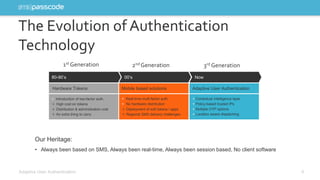
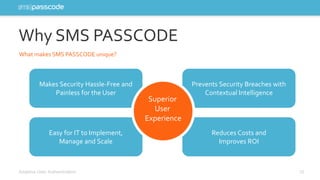
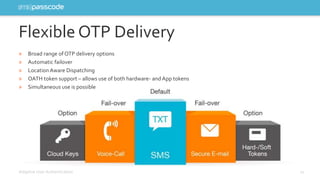
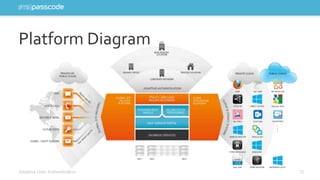
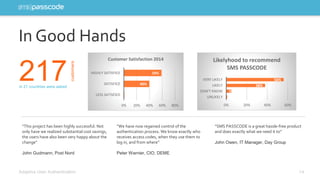
The document highlights the need for stronger authentication methods, emphasizing that traditional passwords are frequently compromised, leading to significant security breaches. It presents SMS passcode technology as an effective multi-factor authentication solution that improves security while being user-friendly and easy to implement for organizations. Additionally, it outlines the evolution of authentication technologies and the benefits of contextual intelligence in enhancing security measures.