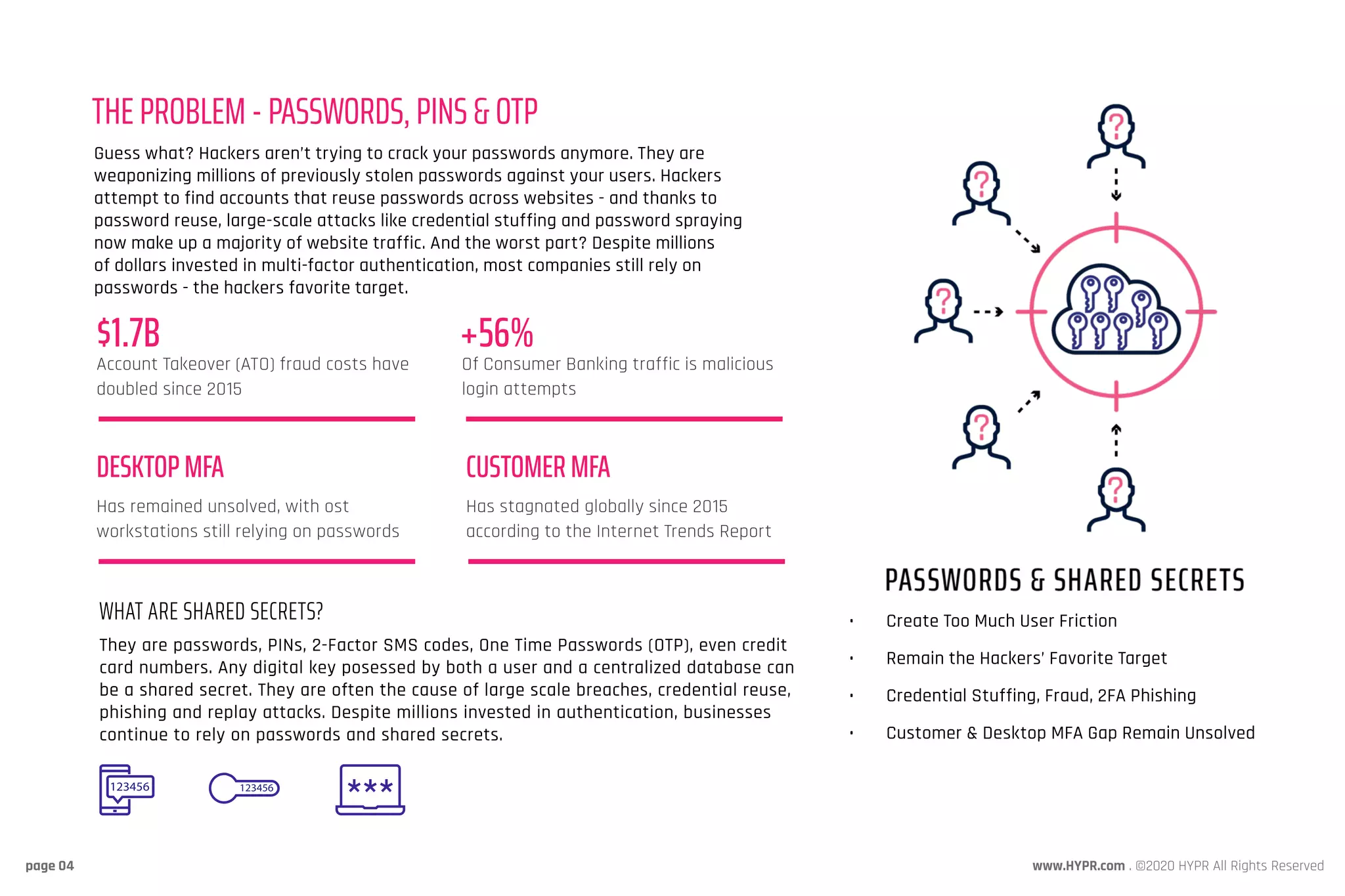
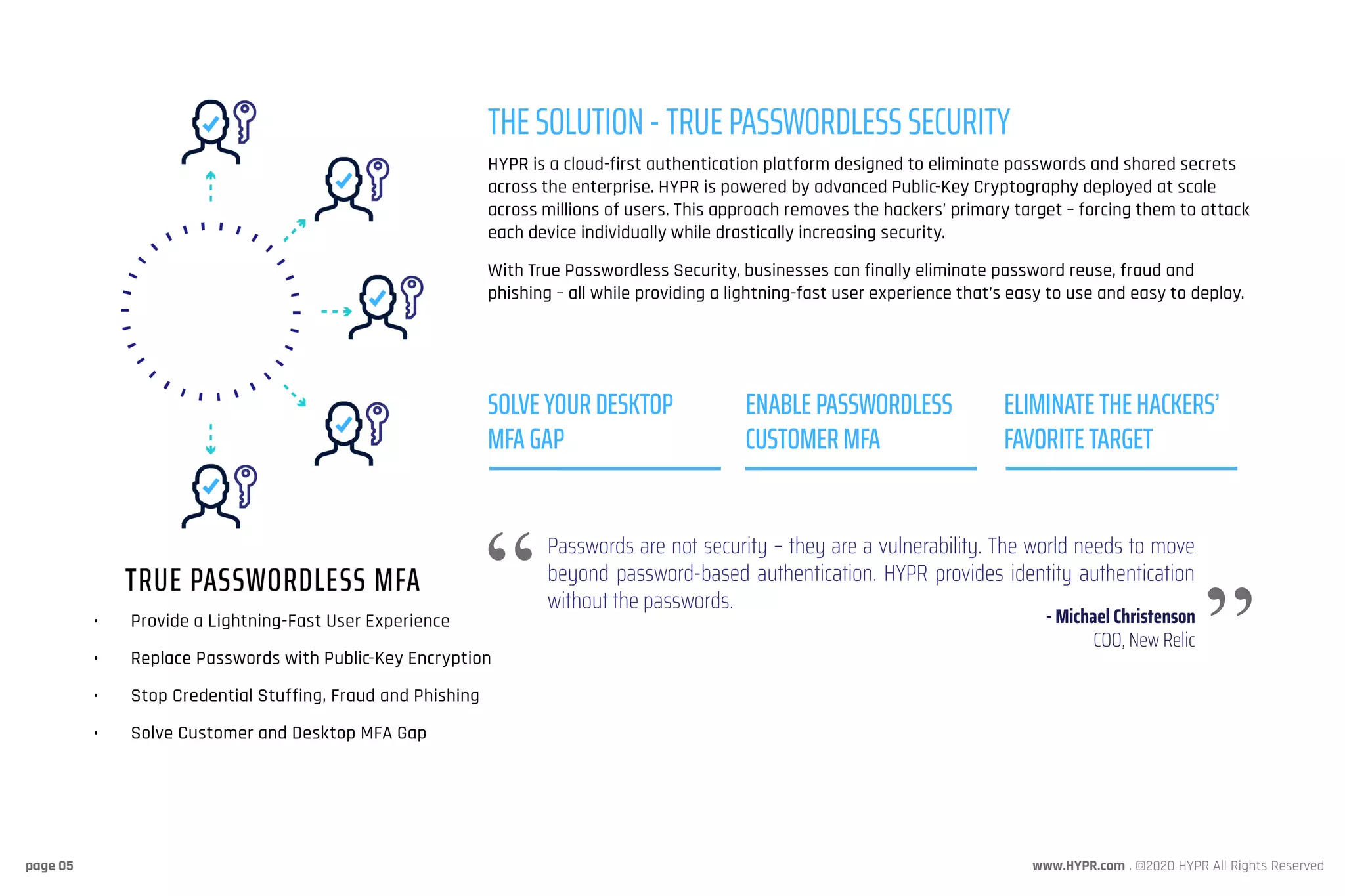
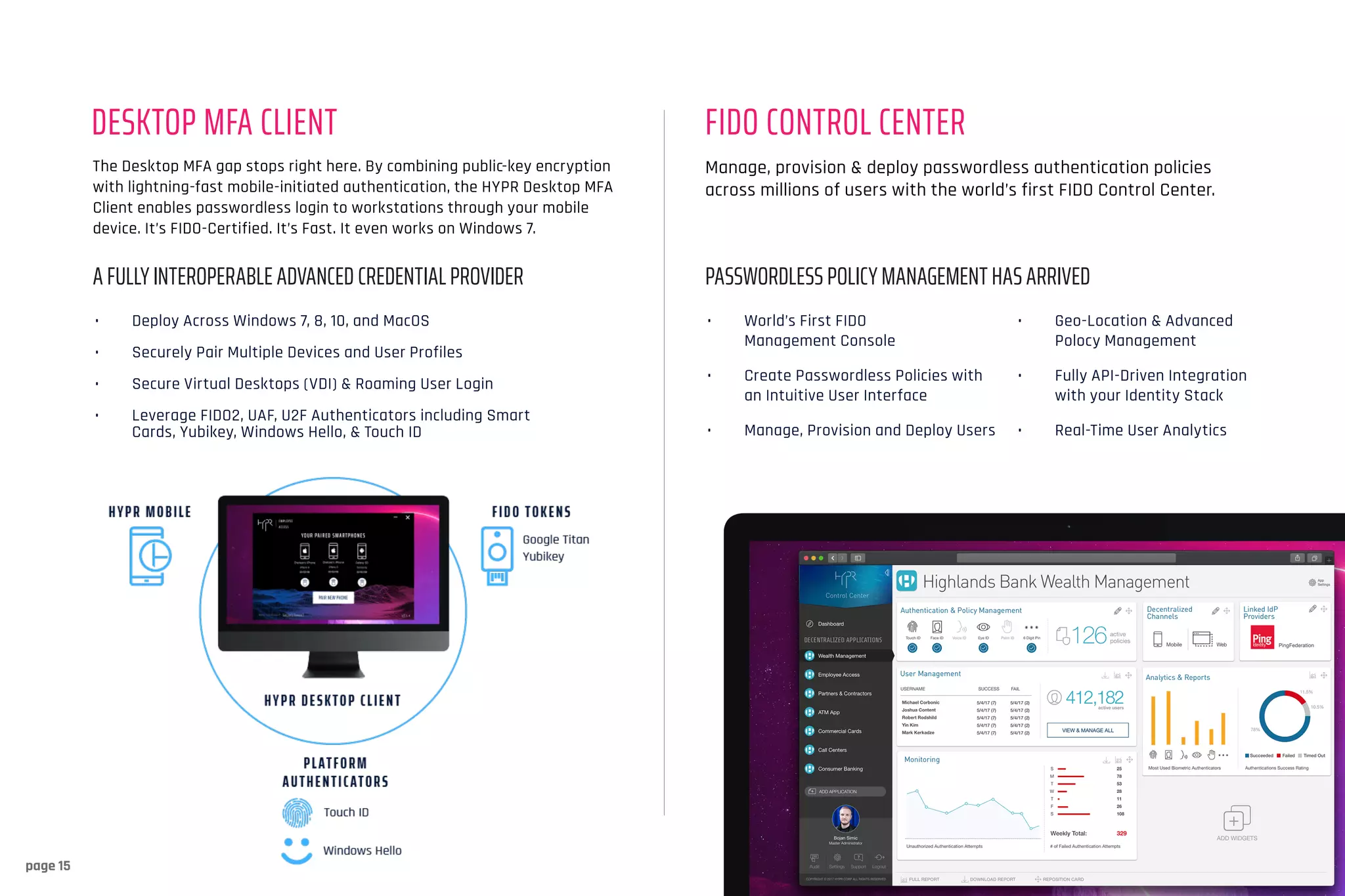
Hypr provides a cloud-based passwordless authentication platform designed to eliminate passwords and shared secrets, addressing security vulnerabilities that lead to breaches. By using public key cryptography, Hypr enhances security while improving user experience and deploying strong multi-factor authentication for millions of users. Trusted by major industry leaders, Hypr seeks to transform authentication practices across enterprises globally.