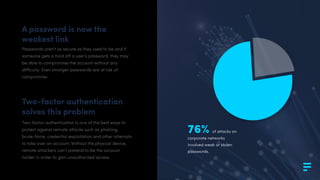
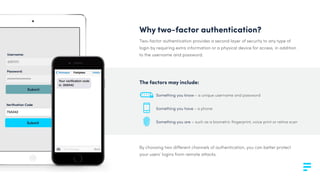
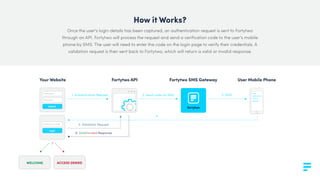
Fortytwo offers a two-factor authentication solution that enhances security by sending a verification code to users' mobile phones, addressing vulnerabilities related to weak or stolen passwords. The process involves an API request for authentication, sending a one-time code via SMS, and requiring this code for successful login validation. Fortytwo's system, backed by a multilingual support team and global messaging networks, is designed to protect against various forms of remote attacks.