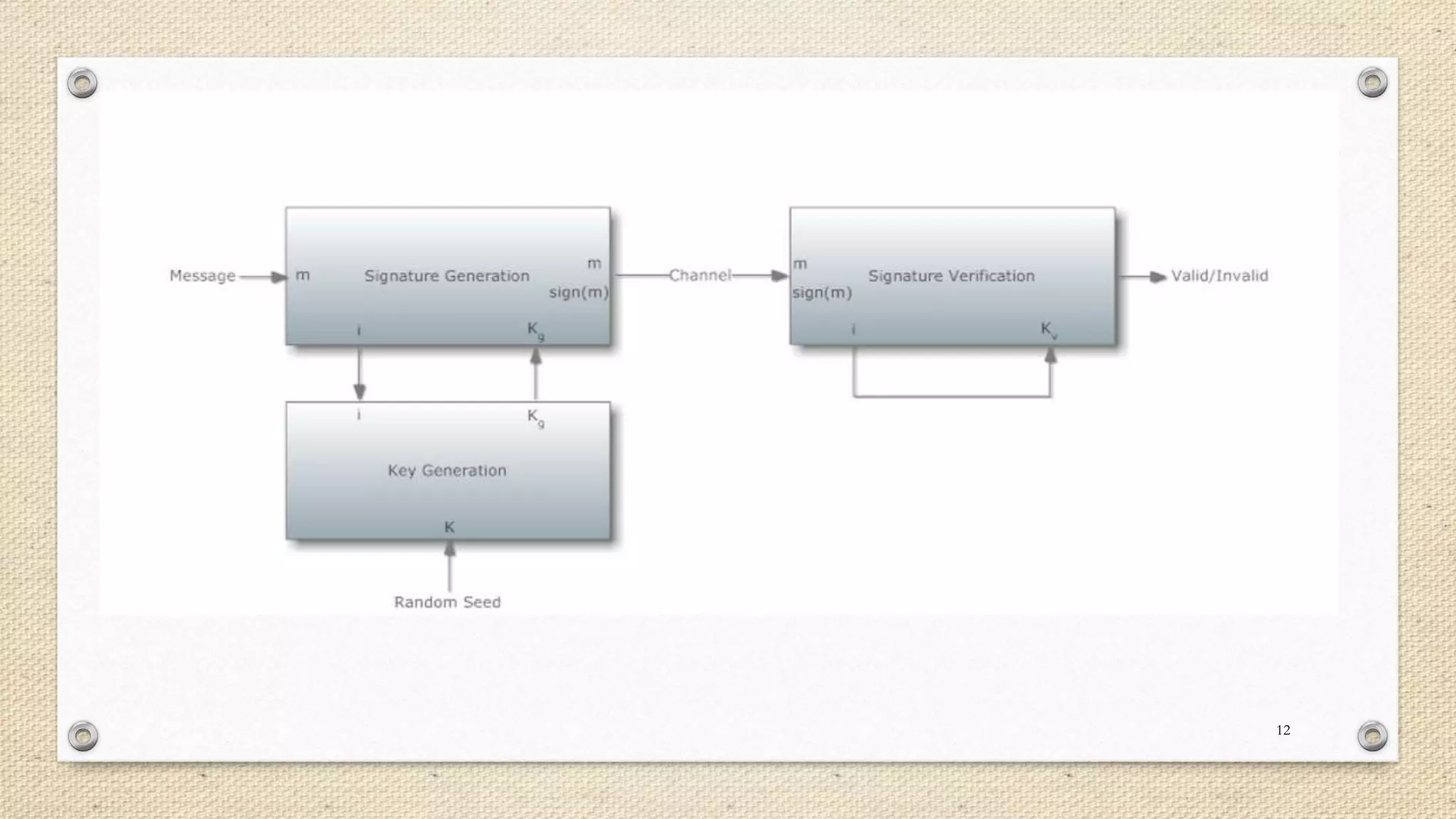
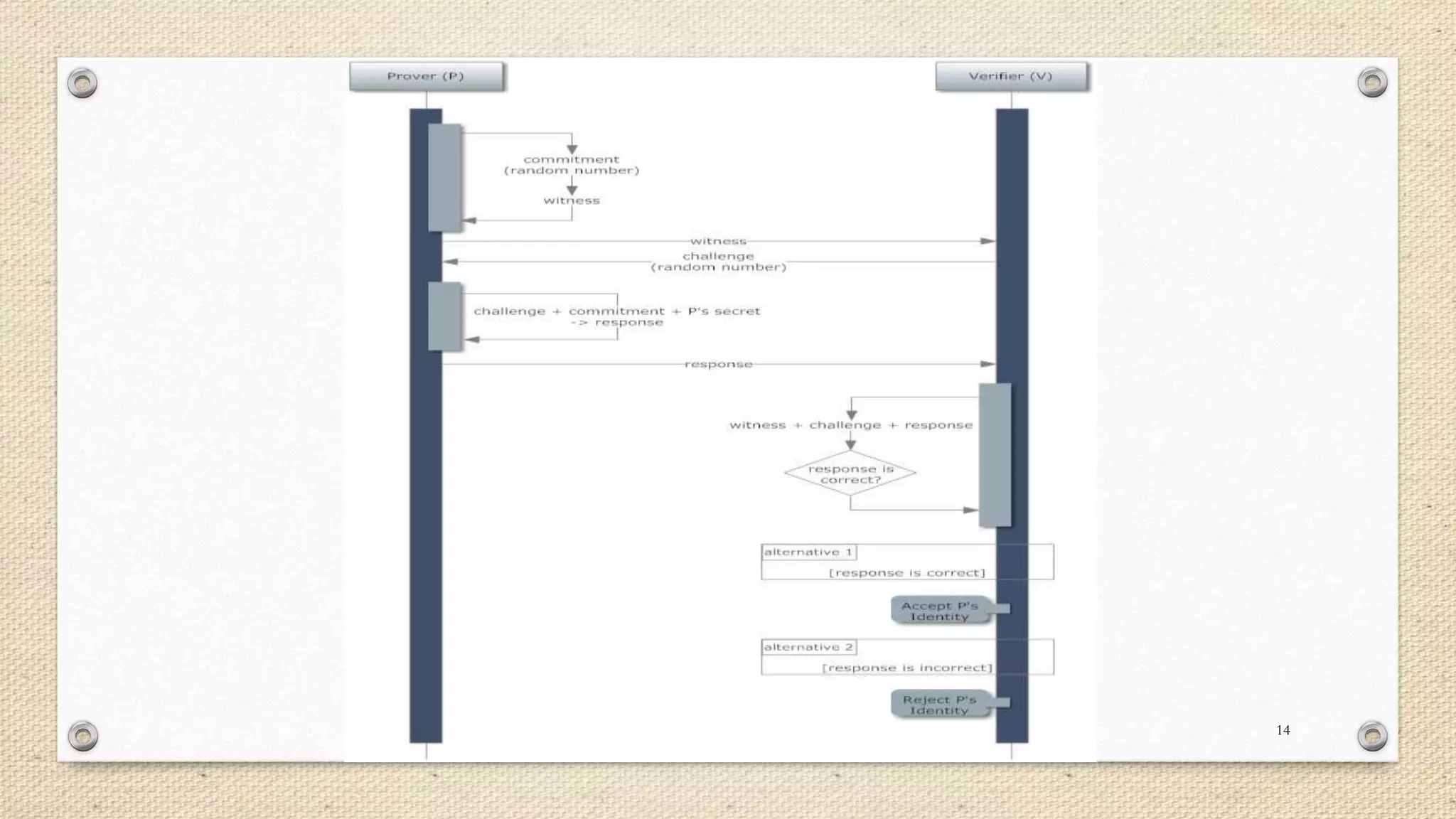
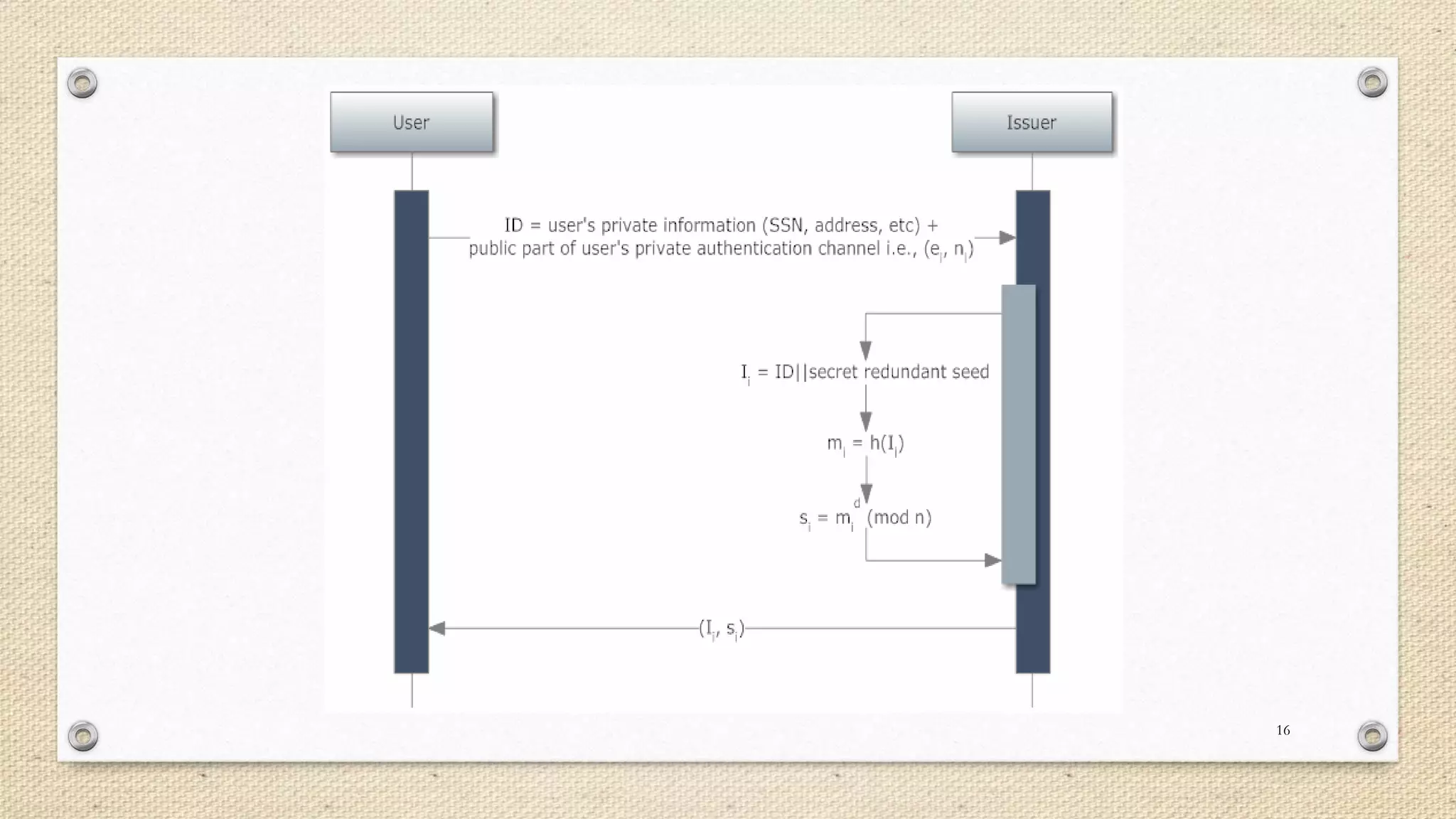
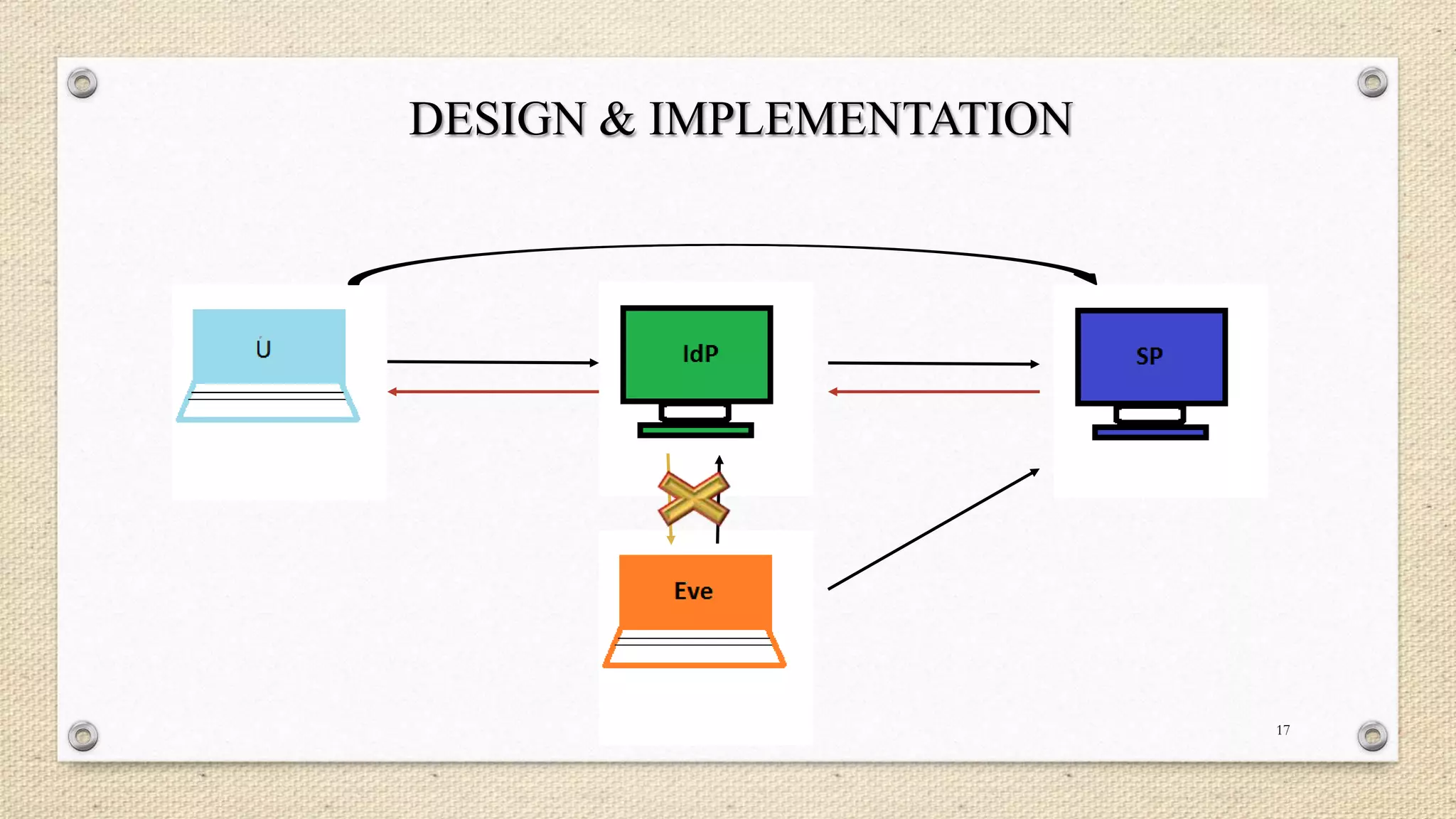
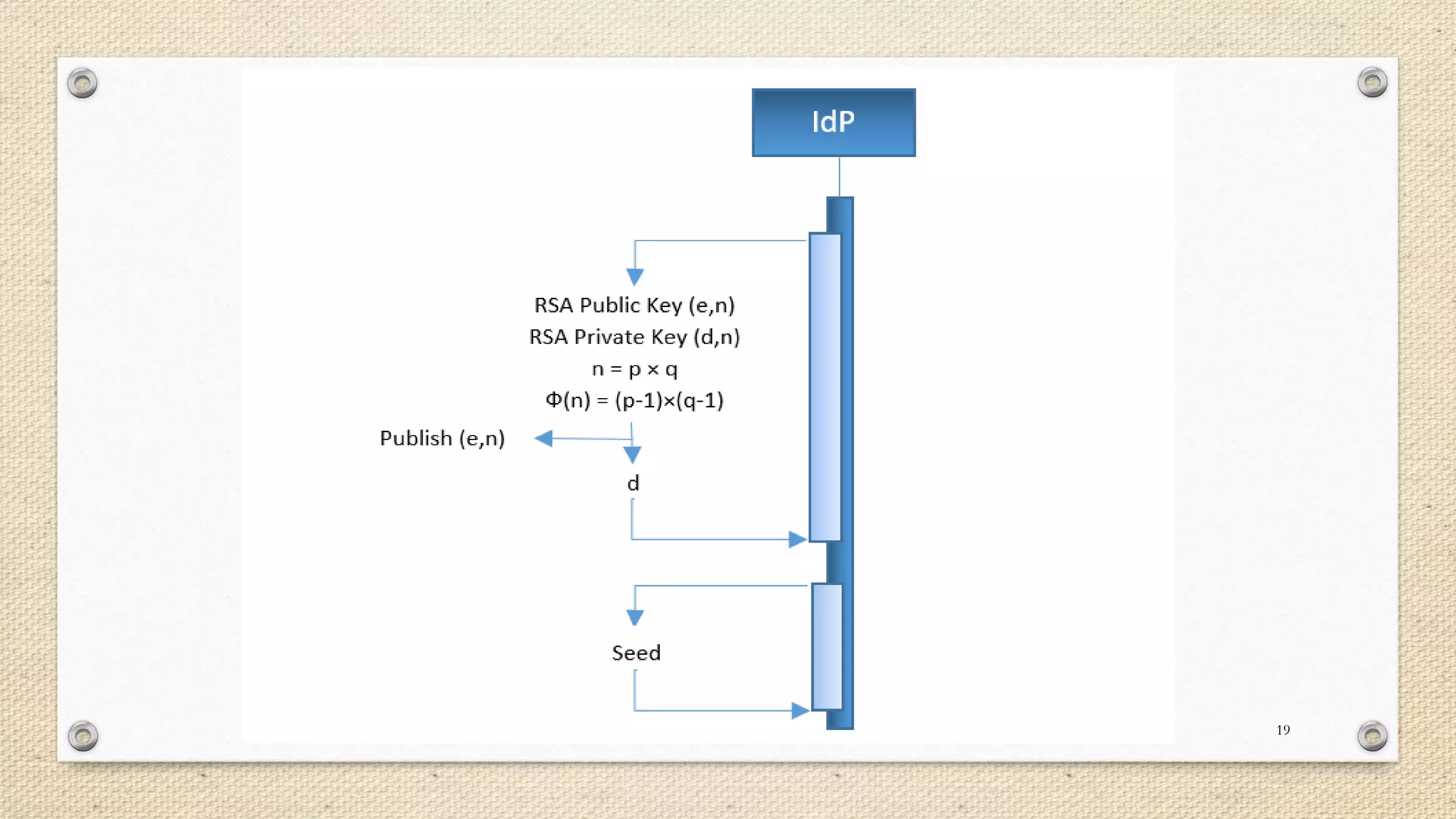
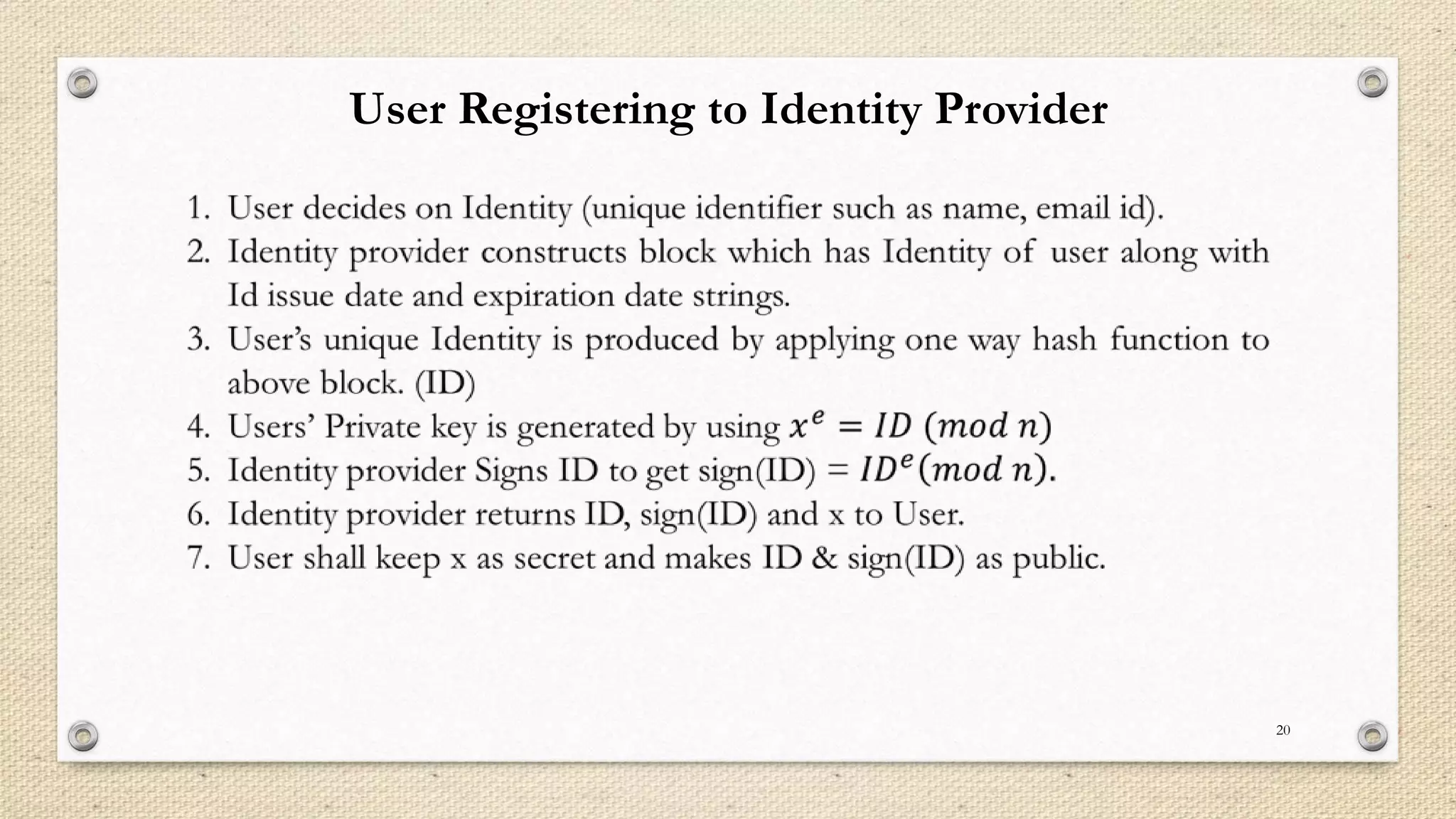
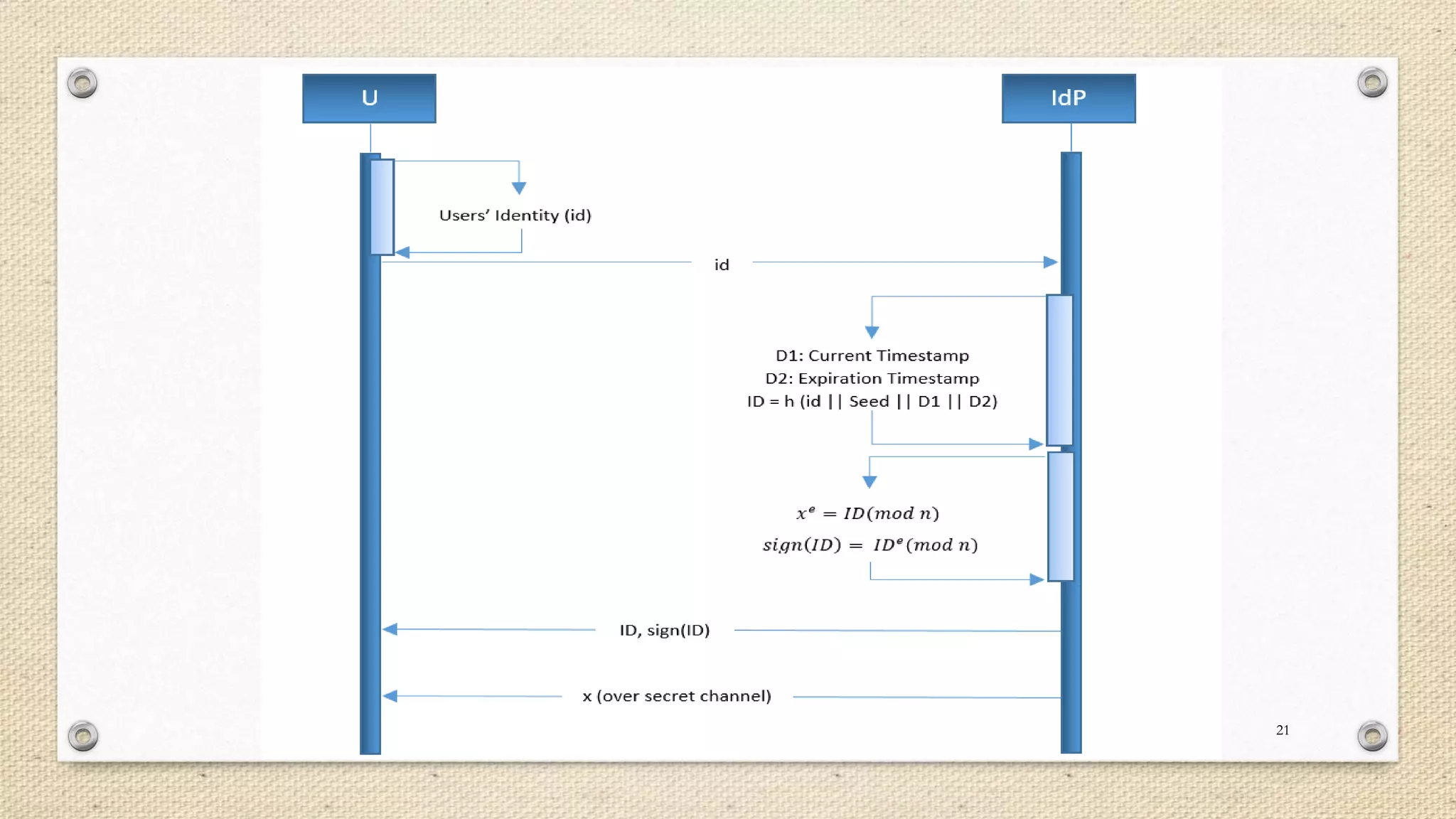
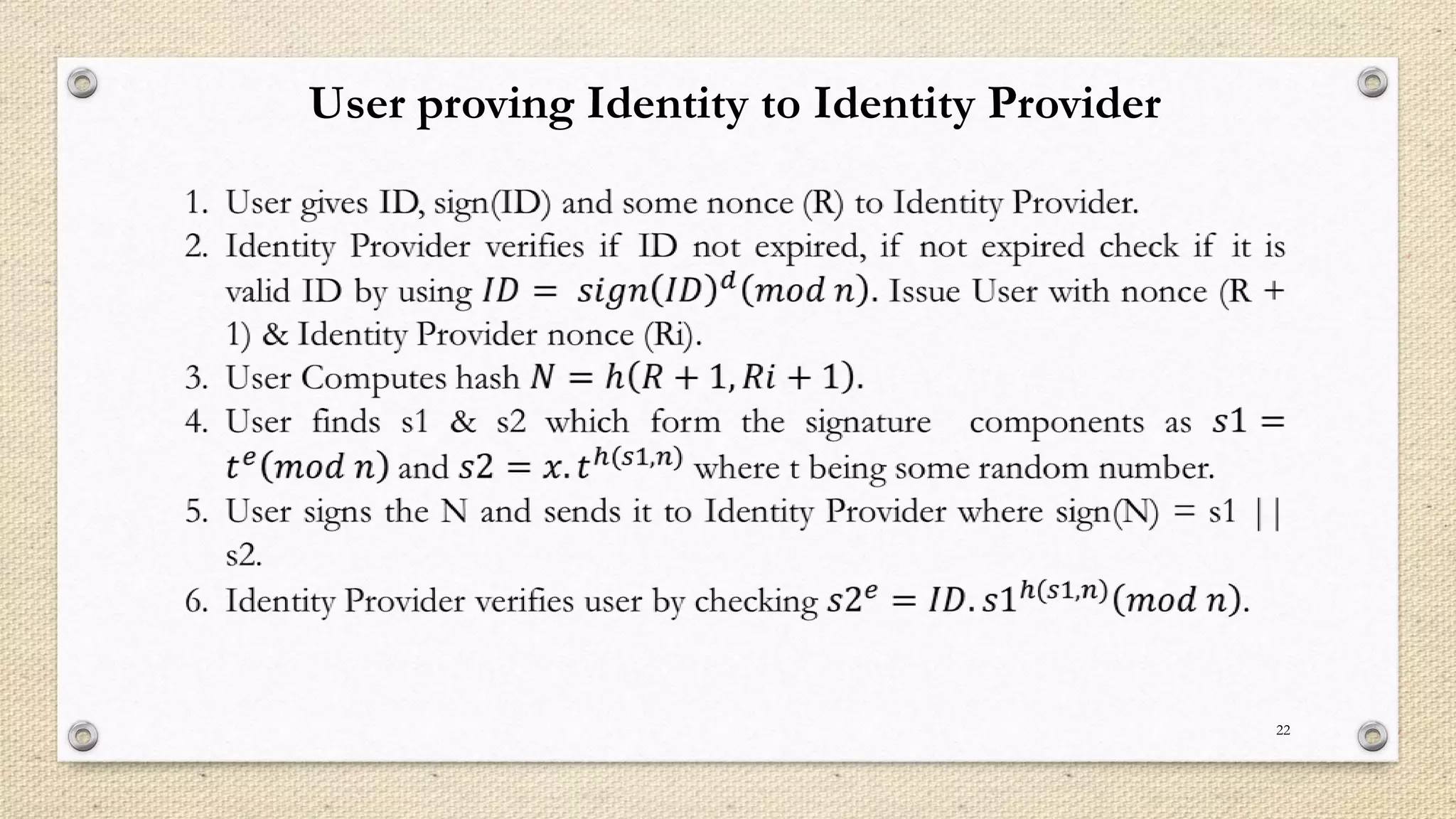
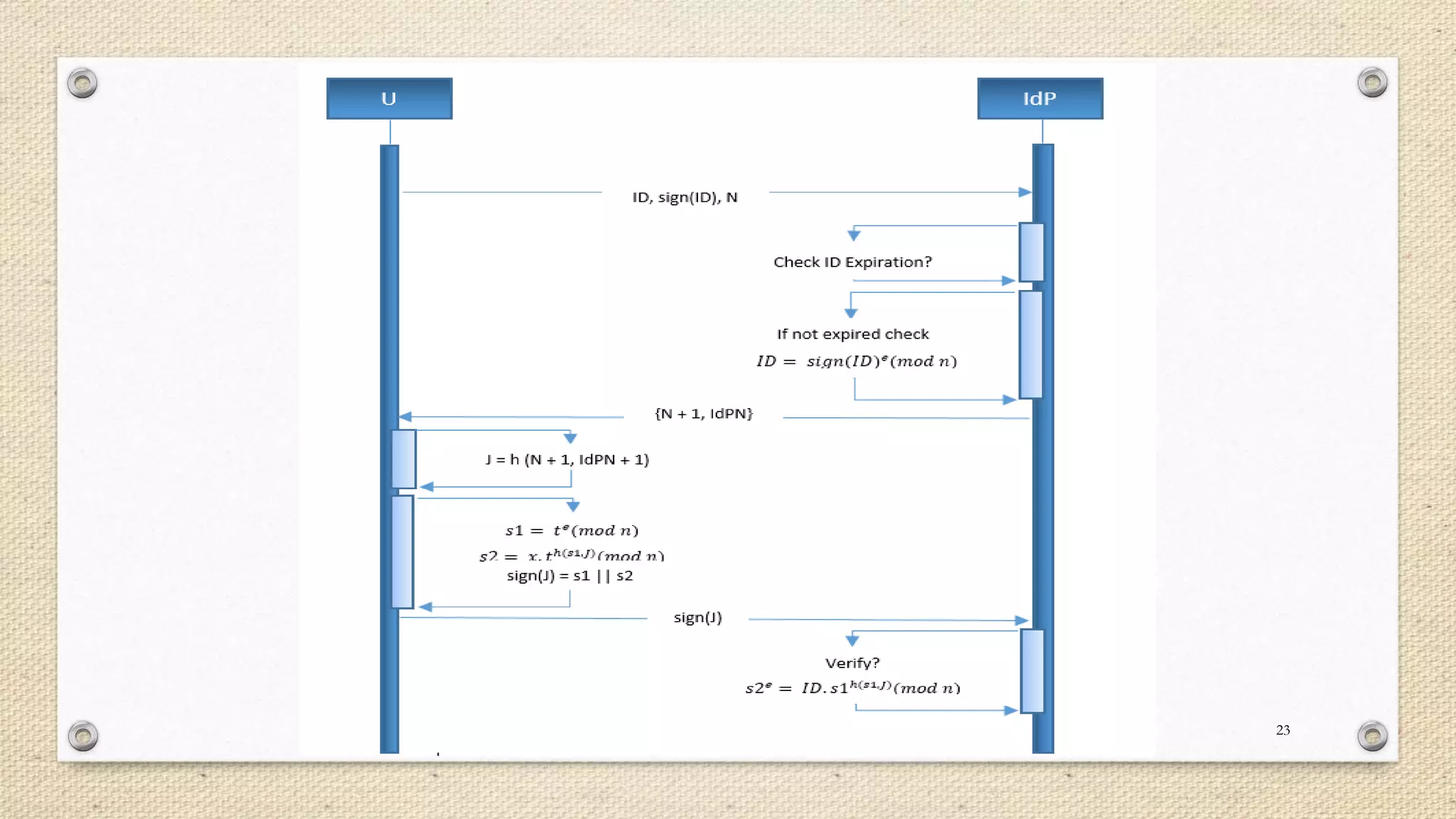
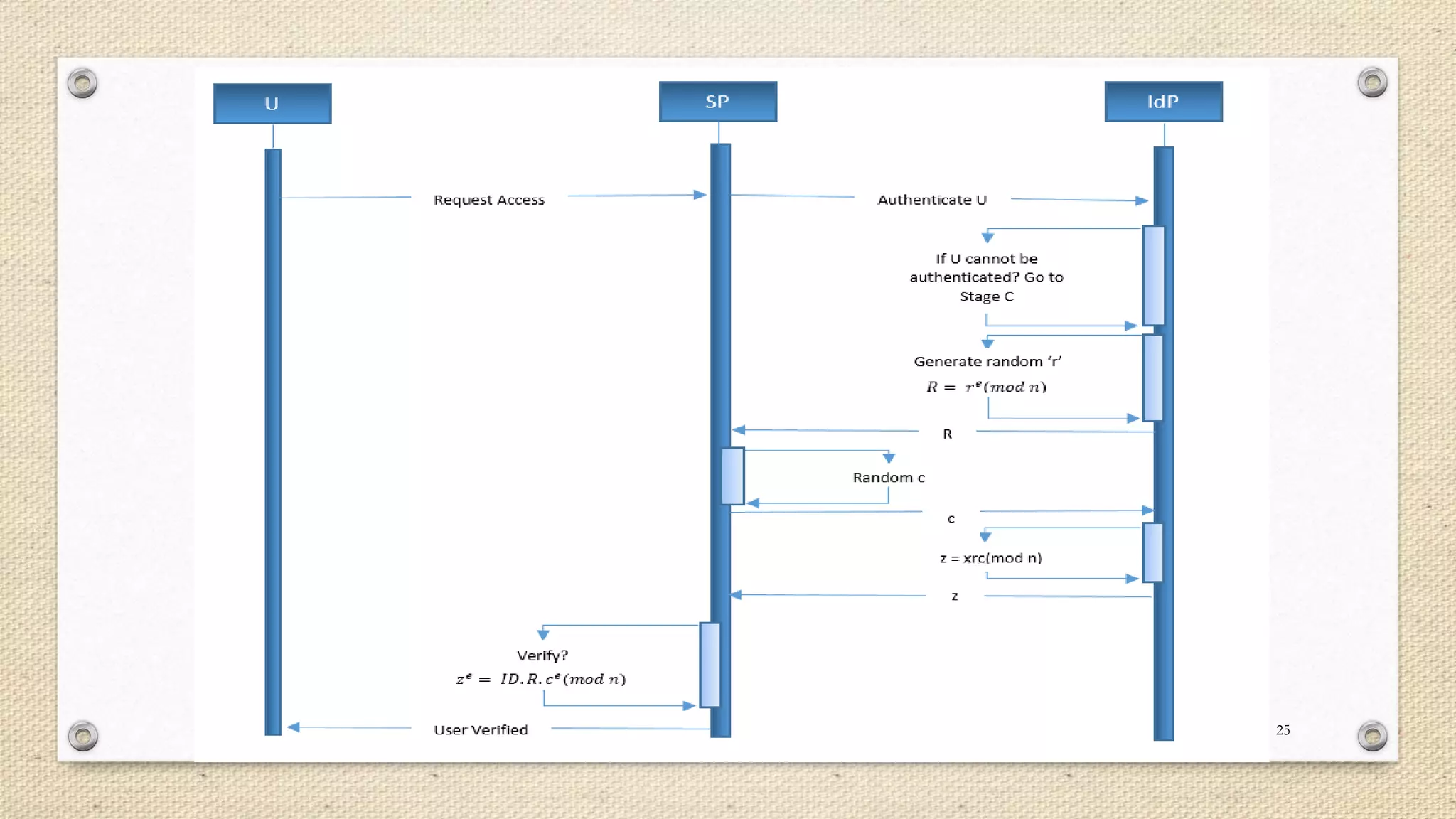
The document describes a double single sign-on (SSO) system for secure network establishment. It discusses the need for strong authentication and outlines the key components of the proposed system. The system separates user authorization from identification to enable asynchronous authorization. It employs Shamir's identity-based signature scheme, a zero-knowledge identification protocol, and Simmons' impersonation-proof identity verification scheme. The design establishes identity providers to generate and validate user credentials, allowing users to prove their identity to service providers. The system aims to reduce costs while improving security over existing SSO solutions.