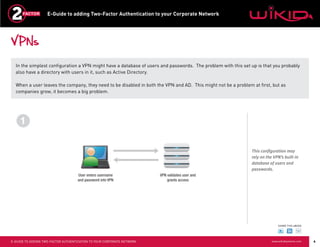
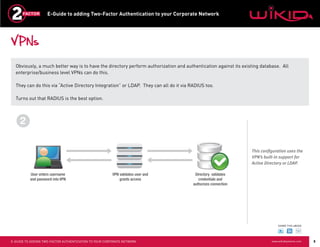
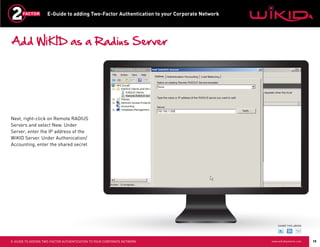
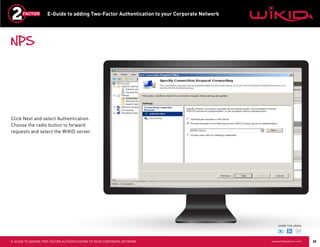
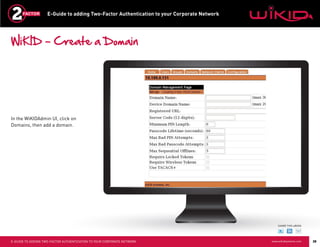
This document provides instructions for adding two-factor authentication to a corporate network using WiKID as the authentication server. It discusses configuring Radius clients like VPNs from Cisco and Juniper to communicate with an Active Directory server through a Radius server. The Active Directory server would authorize users while the WiKID server authenticates users with two-factor authentication. It provides step-by-step examples of configuring Network Policy Server and WiKID to enable two-factor authentication for remote access to a corporate network.