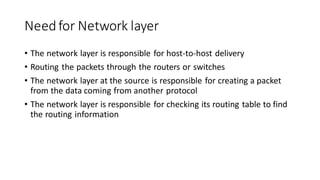
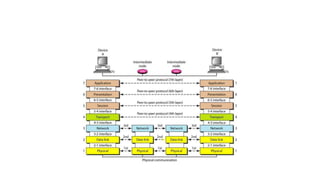
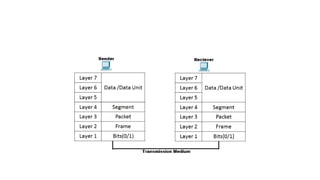
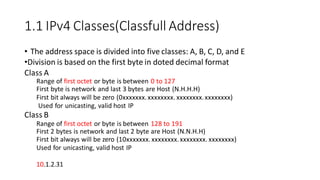
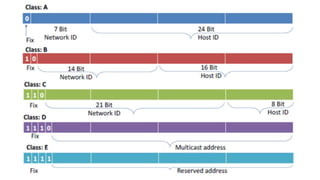
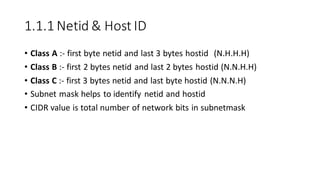
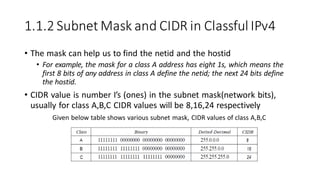
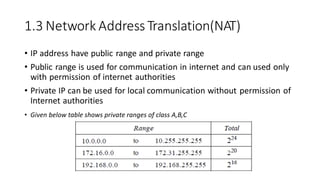
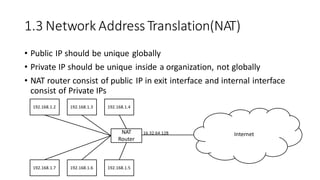
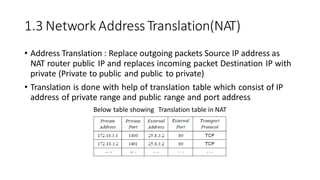
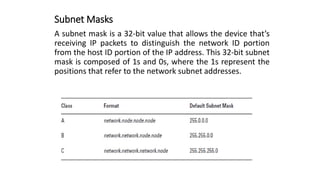
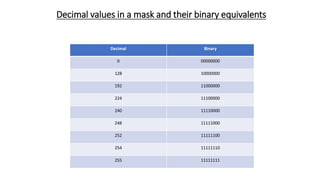
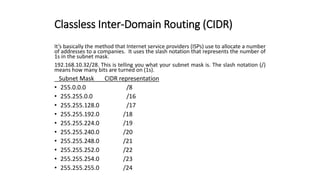
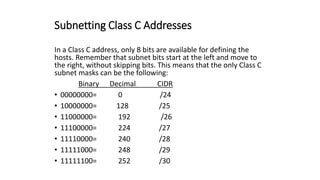
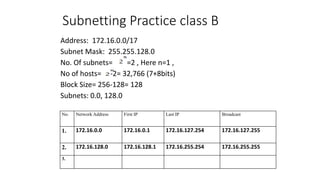
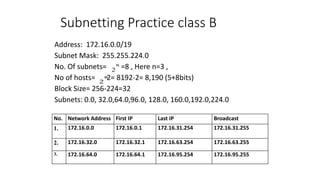
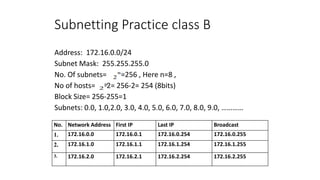
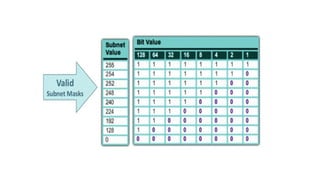
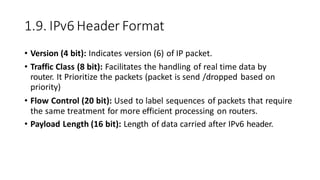
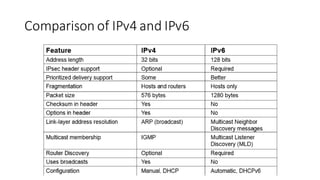
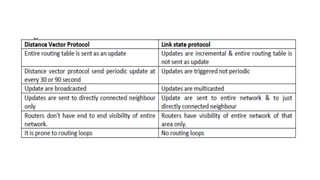
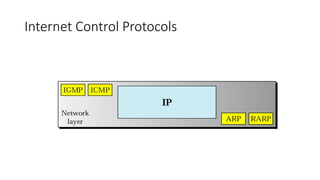
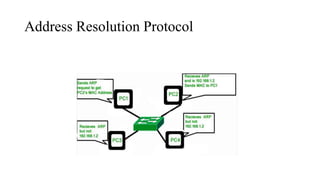
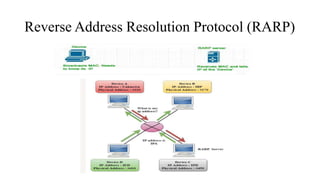
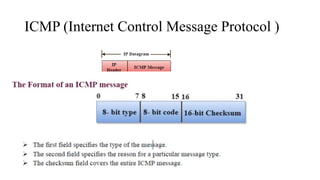
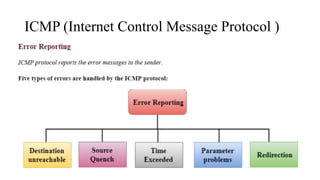
The document discusses IPv4 addressing and subnetting. It begins by explaining the need for a network layer and describing IPv4 addressing fundamentals like address classes and notations. It then covers topics like subnet masks, CIDR notation, private IP ranges for NAT, and address depletion issues in IPv4. The document provides examples of subnetting Class C addresses using different subnet mask values. It also gives practice examples of subnetting Class B addresses.









































![broadcasting
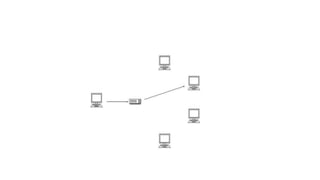
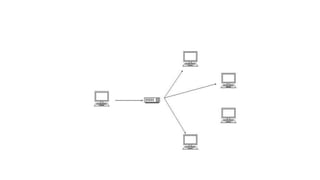
• In computer networking, telecommunication and information
theory, broadcasting is a method of transferring a message to
all recipients simultaneously. Broadcasting can be performed as
a high-level operation in a program, for example, broadcasting
in Message Passing Interface, or it may be a low-level
networking operation, for example broadcasting on Ethernet.
• All-to-all communication is a computer
communication method in which each sender transmits
messages to all receivers within a group.[1] In networking this
can be accomplished using broadcast or multicast. This is in
contrast with the point-to-point method in which each sender
communicates with one receiver.](https://image.slidesharecdn.com/chapter4-240130112113-b9519ed2/85/chapter-4-pptx-75-320.jpg)