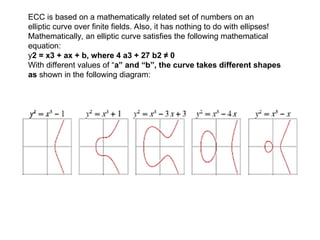
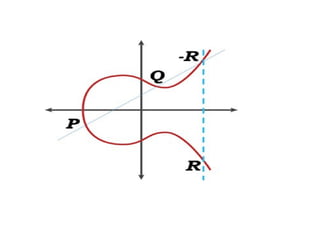
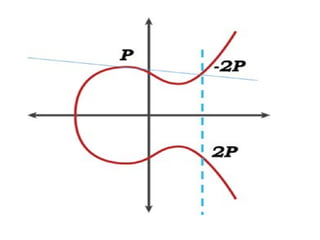
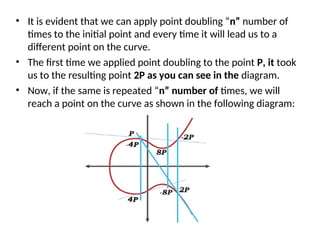
The document discusses elliptic curve cryptography (ECC) and its application in digital signatures, specifically through the Elliptic Curve Digital Signature Algorithm (ECDSA). It explains the mathematical properties of elliptic curves, the process of key generation, signature generation, and verification, and emphasizes the advantages of ECC over traditional methods like RSA in terms of security and efficiency. Additionally, it highlights various applications of ECC in securing communications and transactions.









![Key Generation
Since the domain parameters (P, a, b, G, n, h) are preestablished, the curve
and the base point are known by both parties.
Also, the prime P that makes it a finite field is also known (P is usually 160
bits and can be greater as well).
So, the sender, say, Alice does the following to generate the keys:
• Select a random integer d in the interval [1, n − 1]
• Compute Q = d G
• Declare Q is the public key and keep d as the private key.](https://image.slidesharecdn.com/ecdsagood-250208151750-52b3e804/85/Elliptic-Curve-Digital-Signature-Algorithm-ECDSA-ppt-14-320.jpg)
![Signature Generation
Once the keys are generated, Alice, the sender, would use the private
key “d” to sign the message (m). So, she would perform the
following steps in
the order specified to generate the signature:
• Select a random number k in the interval [1, n − 1]
• Compute k.G and find the new coordinates (x1, y1) and
find r = x1 mod n
If r = 0, then start all over again
• Compute e = SHA-1 (m)
• Compute s = k −1 (e + d . r) mod n
If s = 0, then start all over again from the first step
• Alice’s signature for the message (m) would now be (r, s)](https://image.slidesharecdn.com/ecdsagood-250208151750-52b3e804/85/Elliptic-Curve-Digital-Signature-Algorithm-ECDSA-ppt-15-320.jpg)
![Signature Verification
Let us say Bob is the receiver here and has access to the domain
parameters and the public key Q of the sender Alice.
As a security measure, Bob should first verify that the data he has, which is
the domain parameters, the signature, and Alice’s public key Q are all valid.
To verify Alice’s signature on the message (m), Bob would perform the
following operations in the order specified:
• Verify that r and s are integers in the interval [1, n − 1]
• Compute e = SHA-1 (m)
• Compute w = s −1 mod n
• Compute u1 = e w mod n, and u2 = r w mod n
• Compute X = u1 G + u2 G, where X represents the coordinates, say (x2,
y2)
Compute v = x1 mod n
• Accept the signature if r = v, otherwise reject it](https://image.slidesharecdn.com/ecdsagood-250208151750-52b3e804/85/Elliptic-Curve-Digital-Signature-Algorithm-ECDSA-ppt-16-320.jpg)
