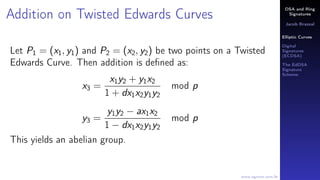
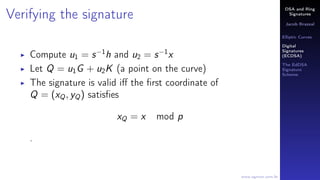
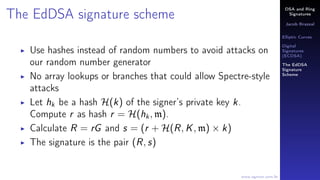
Monero is a cryptocurrency that uses ring signatures to obscure the origin of transactions. It uses twisted Edwards curves to implement elliptic curve cryptography. Ring signatures allow multiple people to sign a transaction at once, making it difficult to determine the true signer. Monero implements ring signatures and uses the Ed25519 elliptic curve for its digital signatures.