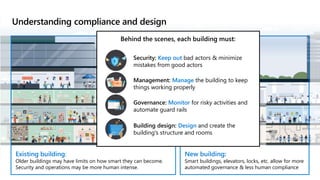
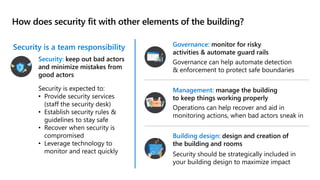
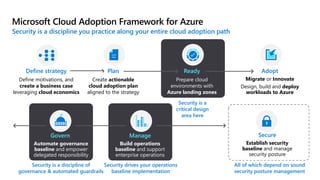
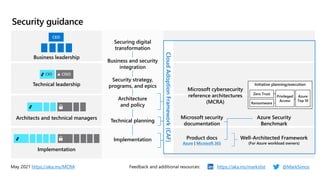
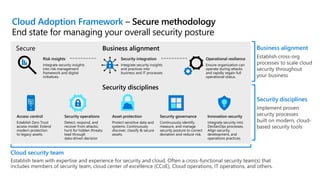
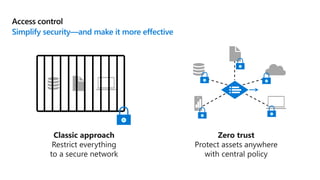
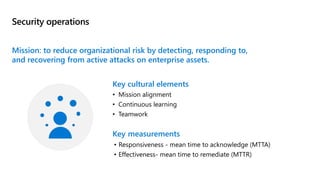
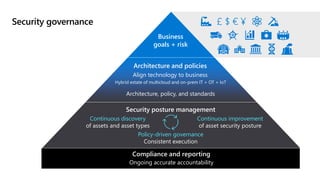
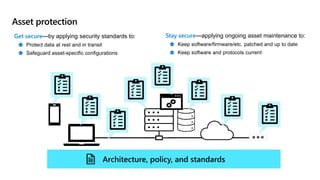
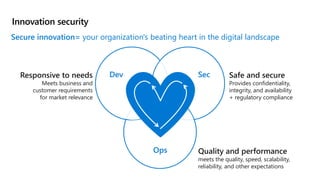
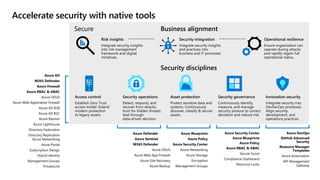
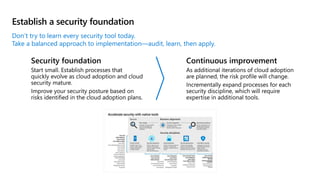
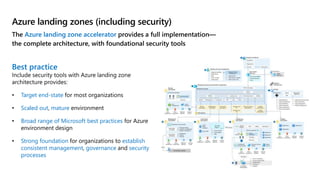
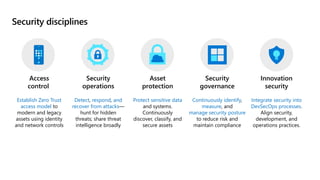
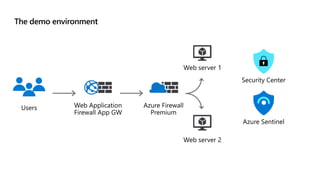
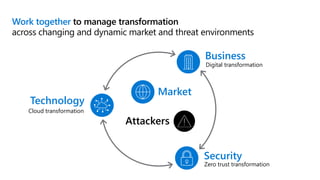
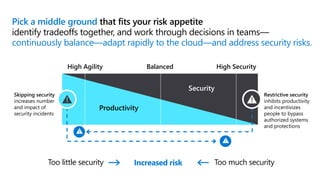
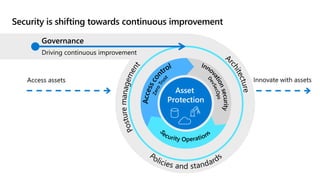
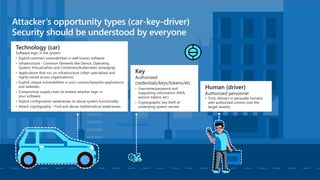
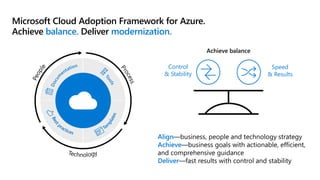
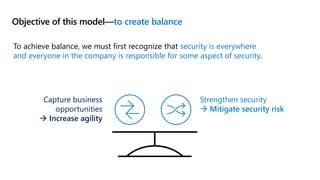
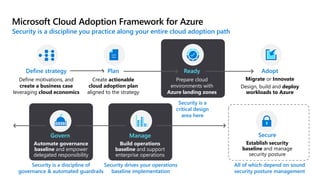
This document provides an overview of security best practices within the Microsoft Cloud Adoption Framework for Azure. It discusses how security is a discipline that should be practiced throughout the entire cloud adoption path, from defining strategy to managing operations. The secure methodology focuses on key security areas like access control, security operations, asset protection, and security governance. It also provides recommendations on using native Azure security tools to establish an initial security foundation and posture.




![A tale of two city [structures]
Existing building:
Business needs are being met, but decisions makers want
to improve compliance and modify the environment
New building:
An entirely new building is required to
meet business and compliance needs](https://image.slidesharecdn.com/cafsecureoverview-240226031726-efa1a5c1/85/Cloud-Adoption-Framework-Secure-Overview-13-320.jpg)