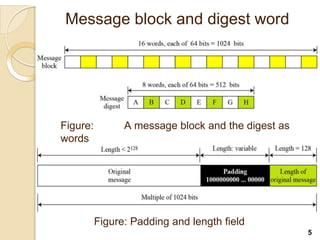
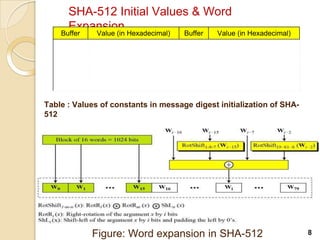
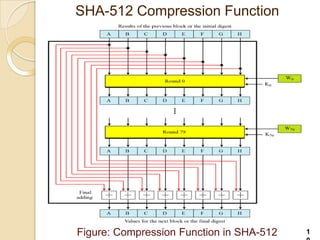
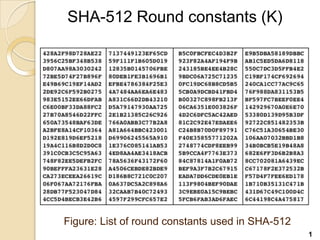
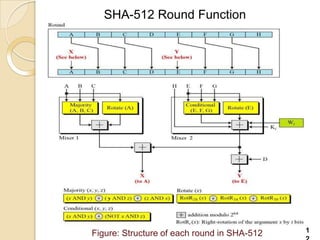
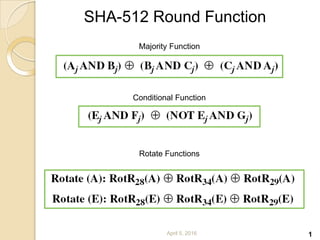
SHA-512 is a cryptographic hash function that produces a 512-bit hash value. It is part of the SHA-2 family and was developed by the National Institute of Standards and Technology. SHA-512 operates by processing message blocks through 80 rounds of computations that include word expansion, compression, and round functions to update digest values. It is commonly used to authenticate files and for password hashing.