Embed presentation
Downloaded 12 times
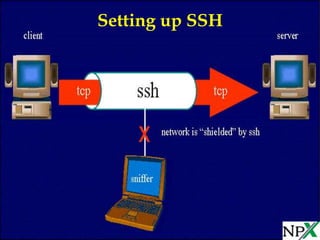


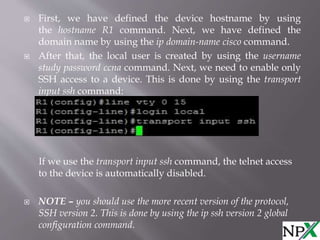

To securely access a Cisco device using SSH, you must first configure a hostname and domain name, create a local username and password, and generate RSA keys. You then allow only SSH access using the "transport input ssh" command, which disables Telnet access. The example configuration shows defining the hostname and domain name, creating a local user, and enabling only SSH access. It is recommended to use SSH version 2 for more secure access.



