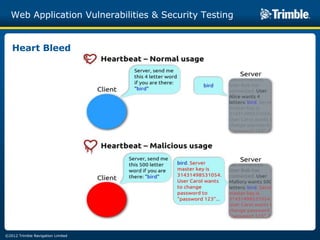
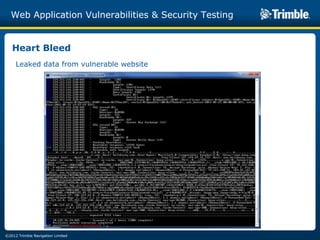
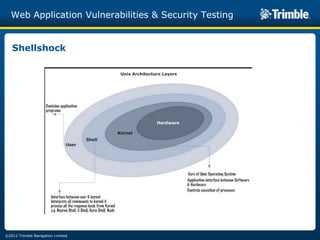
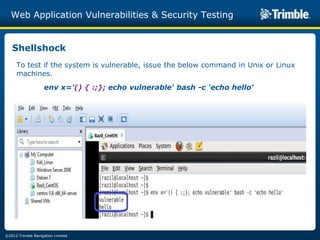
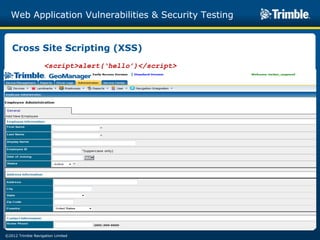
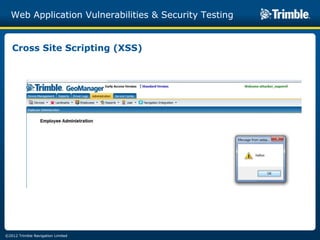
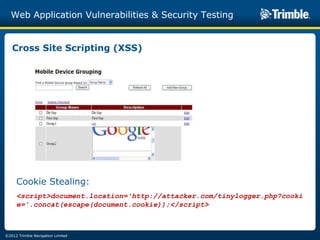
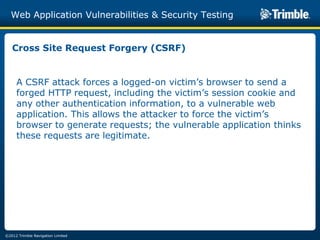
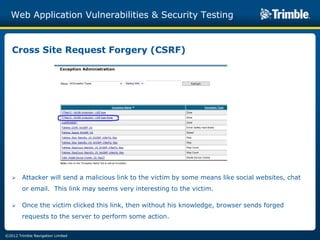
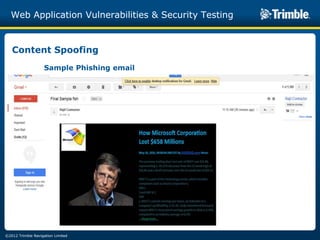
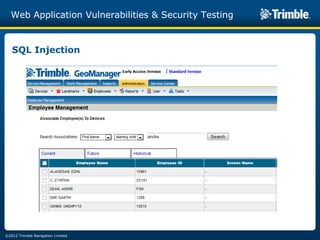
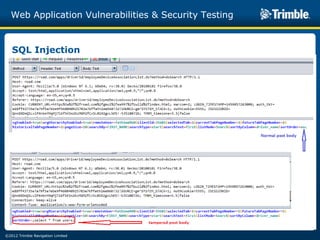
The document discusses various common web application vulnerabilities like Heartbleed, Shellshock, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), SQL injection, denial-of-service attacks, and content spoofing. It provides details on each vulnerability like how it works, the impact, and ways to test for them. The document also demonstrates security testing tools used like Nmap, ZAP, and Metasploit and shows examples of revealing error messages an attacker could use to learn about the system.