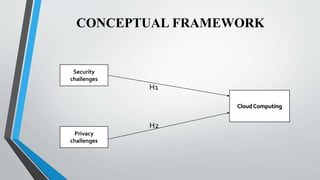
The document addresses security and privacy challenges in cloud computing, highlighting a research gap in existing literature that mainly focuses on technical and performance issues. It outlines the research questions, conceptual framework, and methodology, emphasizing the significance of the study for IT industry users, developers, and academic researchers in Sri Lanka. The findings aim to assist cloud service providers in identifying challenges and educating users on protection strategies.




![OPERATIONALIZATION TABLE
Concept/ Construct Dimension Indicators Sources
Cloud Computing
• Cloud Computing Users
Enrolment • Number of users involve
to Cloud computing
• [Balding08] Craig
Balding, "ITG2008
World Cloud
Computing Summit",
2008
• [Reese09] George
Reese, "Cloud
Application
Architectures",April
2009, O'Reilly Media
• Cloud computing
Challenges
• Types of Challenges
• Parties, who involve in
cloud computing
• Category of parties](https://image.slidesharecdn.com/securityprivacychallengesincloudcomputing-180215071744/85/Security-privacy-challenges-in-cloud-computing-6-320.jpg)


