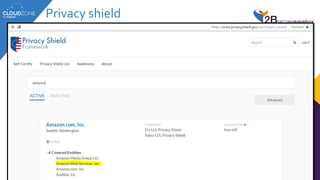
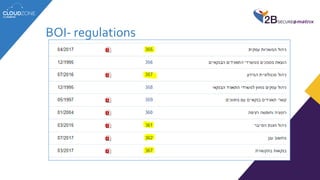
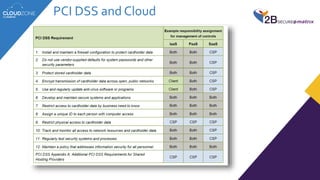
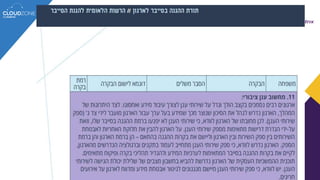
The lecture discusses cloud services' regulatory challenges, including privacy laws such as GDPR and Israeli privacy rules, underscoring the need for compliance in managing personal data. It highlights both the security benefits of cloud services and the risks involved, particularly in relation to data breaches and multi-tenancy concerns. The speaker emphasizes the role of regulatory authorities in guiding organizations through safe cloud adoption while maintaining data protection standards.