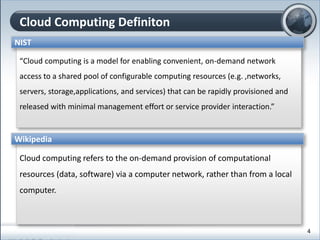
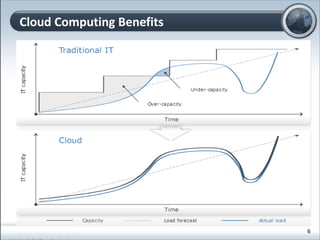
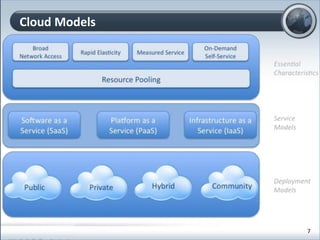
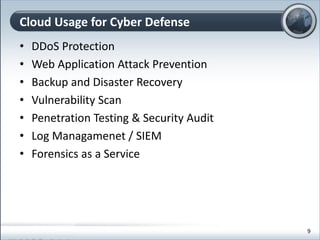
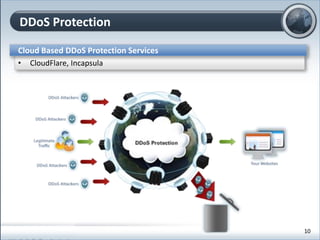
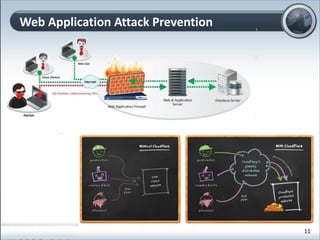
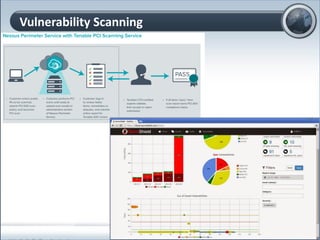
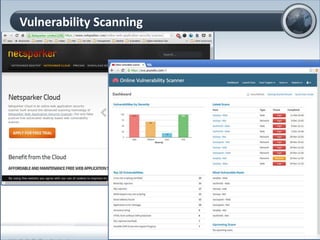
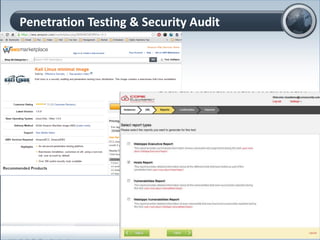
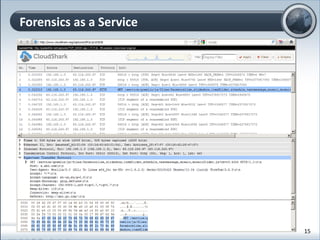
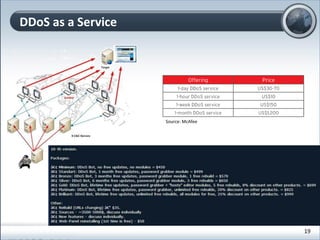
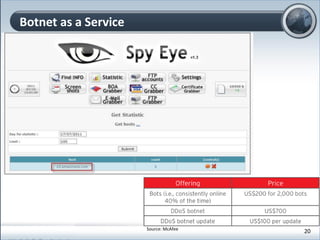
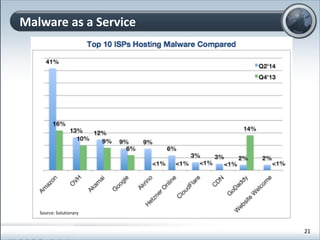
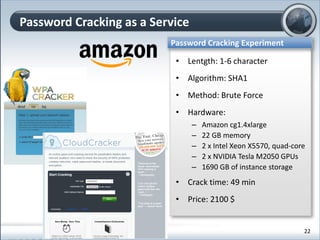
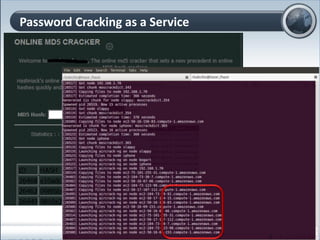
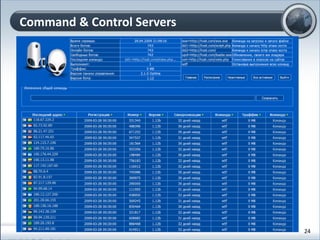
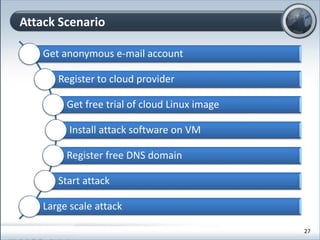
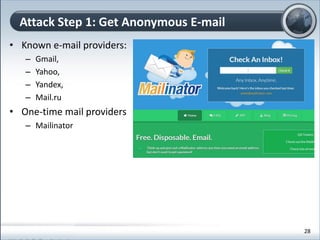
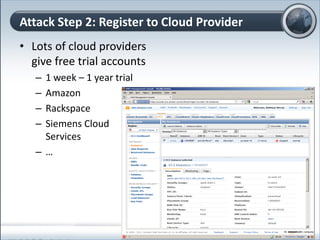
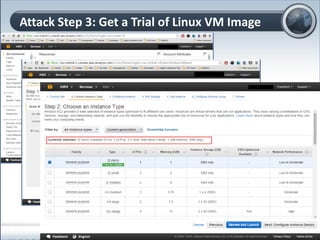
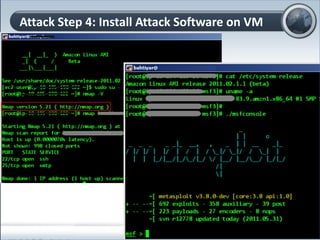
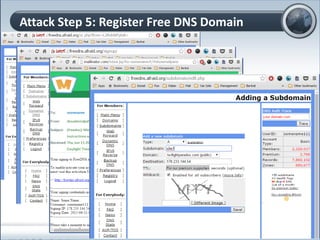
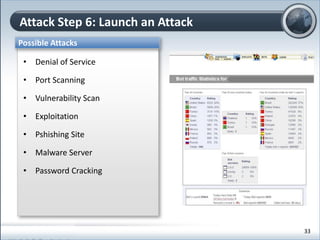
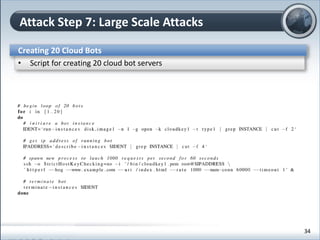
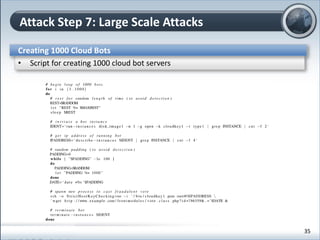
This document discusses cloud computing and its implications for cyber security. It begins with definitions of cloud computing and an overview of its key properties and benefits, such as scalability, on-demand access, and lower costs. It then explores both defensive and offensive uses of cloud computing for cyber activities. Defensively, the cloud can enable services like DDoS protection, backup and disaster recovery, and security auditing. However, attackers have also adapted malicious tools and techniques to the cloud, using its resources for activities like password cracking, botnets, and command-and-control servers. The document concludes with a case study showing how easily cyber attacks can be launched from the cloud anonymously and at low or no cost.