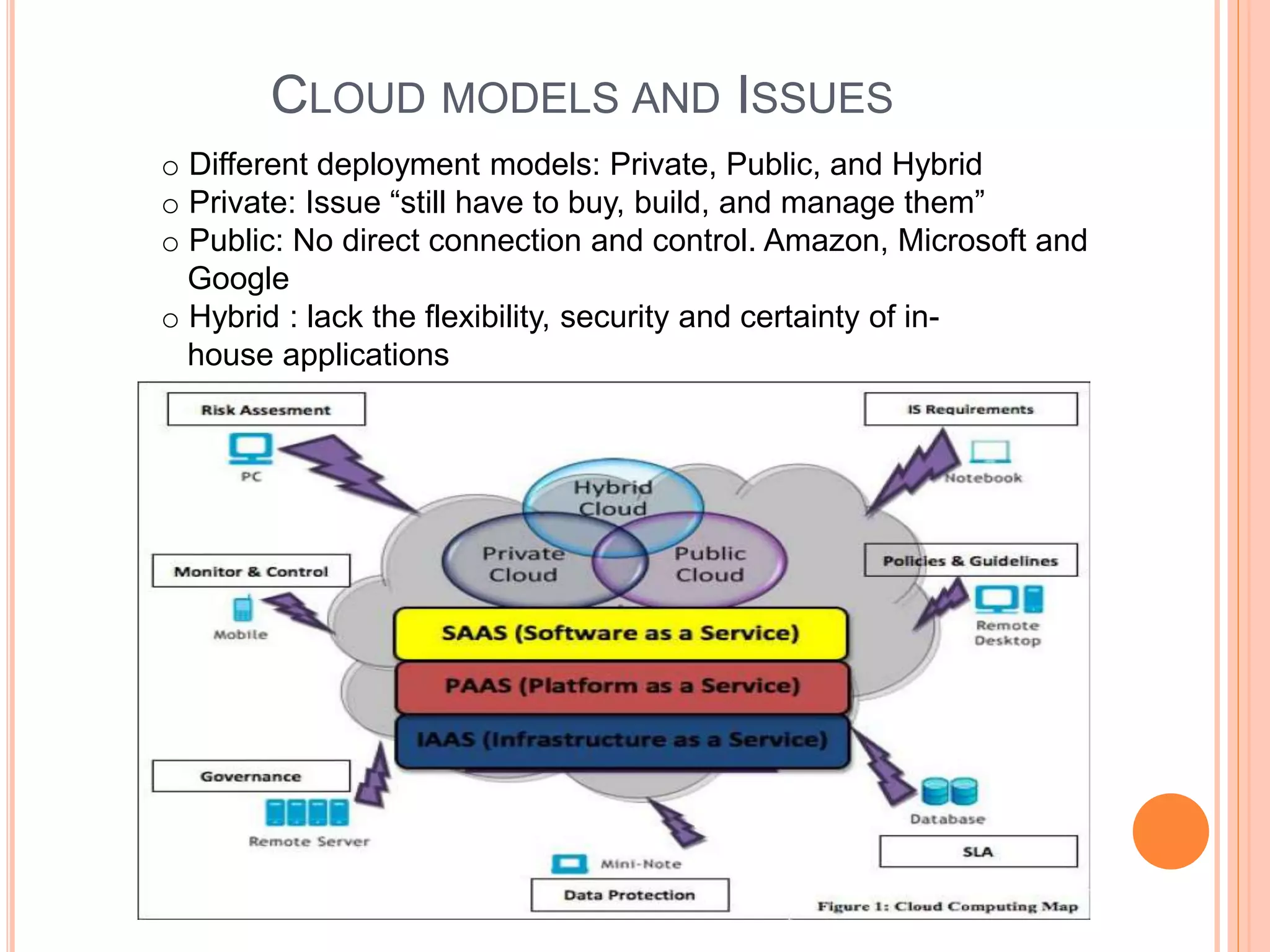
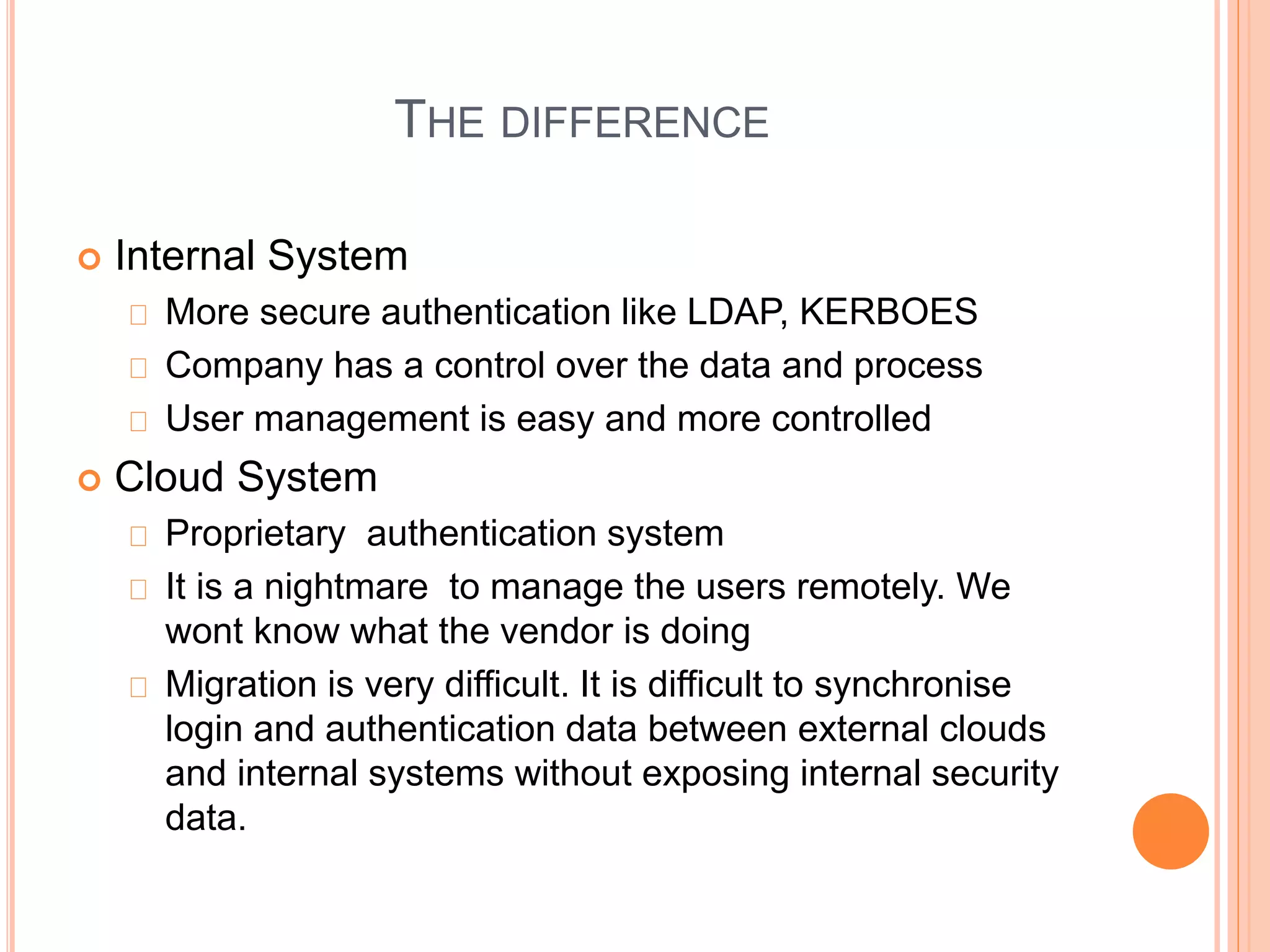
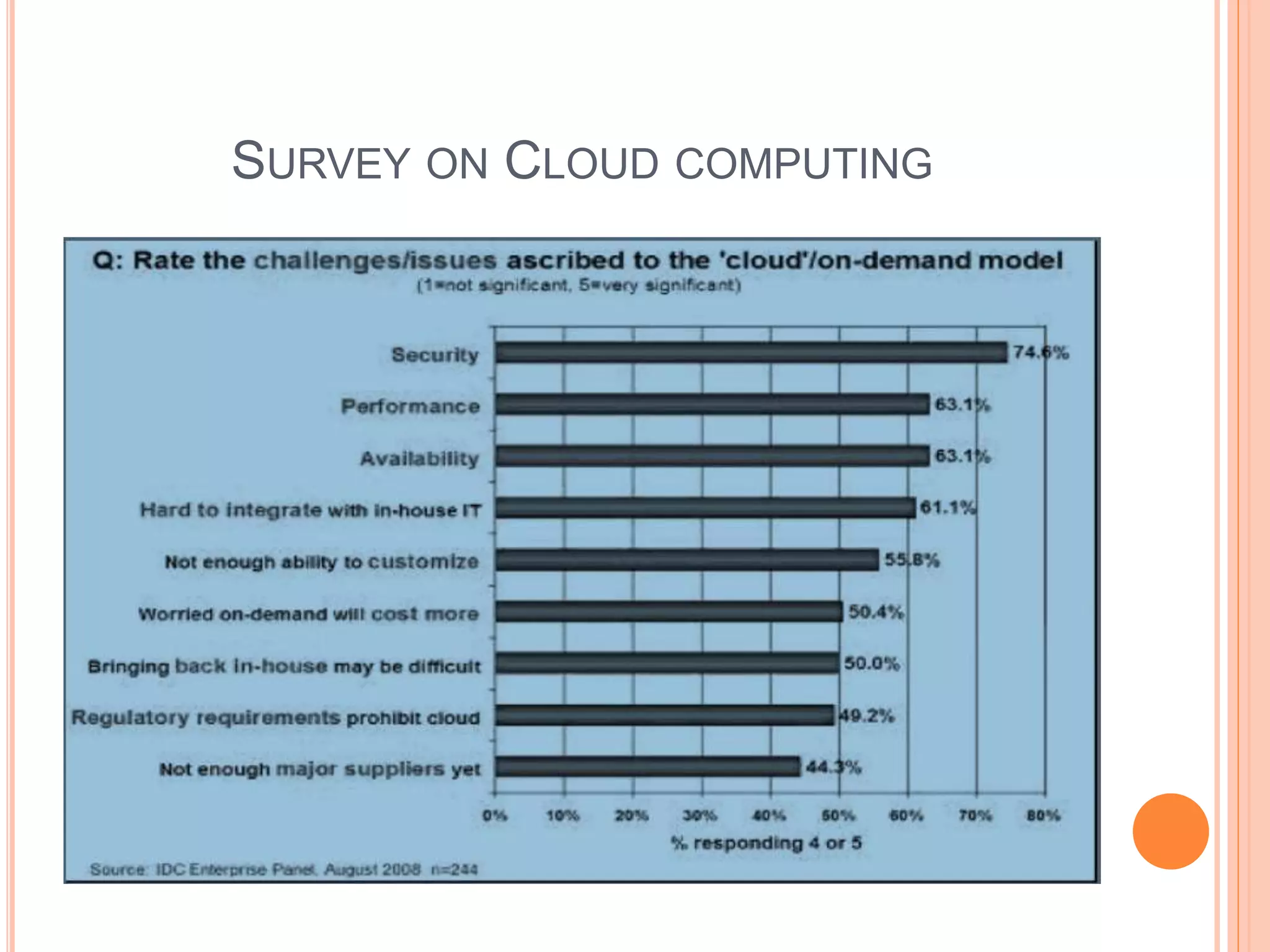
This document discusses authentication issues in cloud computing. It outlines that authentication is the top security concern for businesses migrating to the cloud. The document examines different cloud deployment models and their issues, particularly the lack of control and transparency with public clouds. It also analyzes the challenges of managing users and synchronizing authentication data between internal and external cloud systems. Specific issues covered include privacy risks from cloud providers accessing customer information, and security risks from storing the same passwords across multiple cloud services.