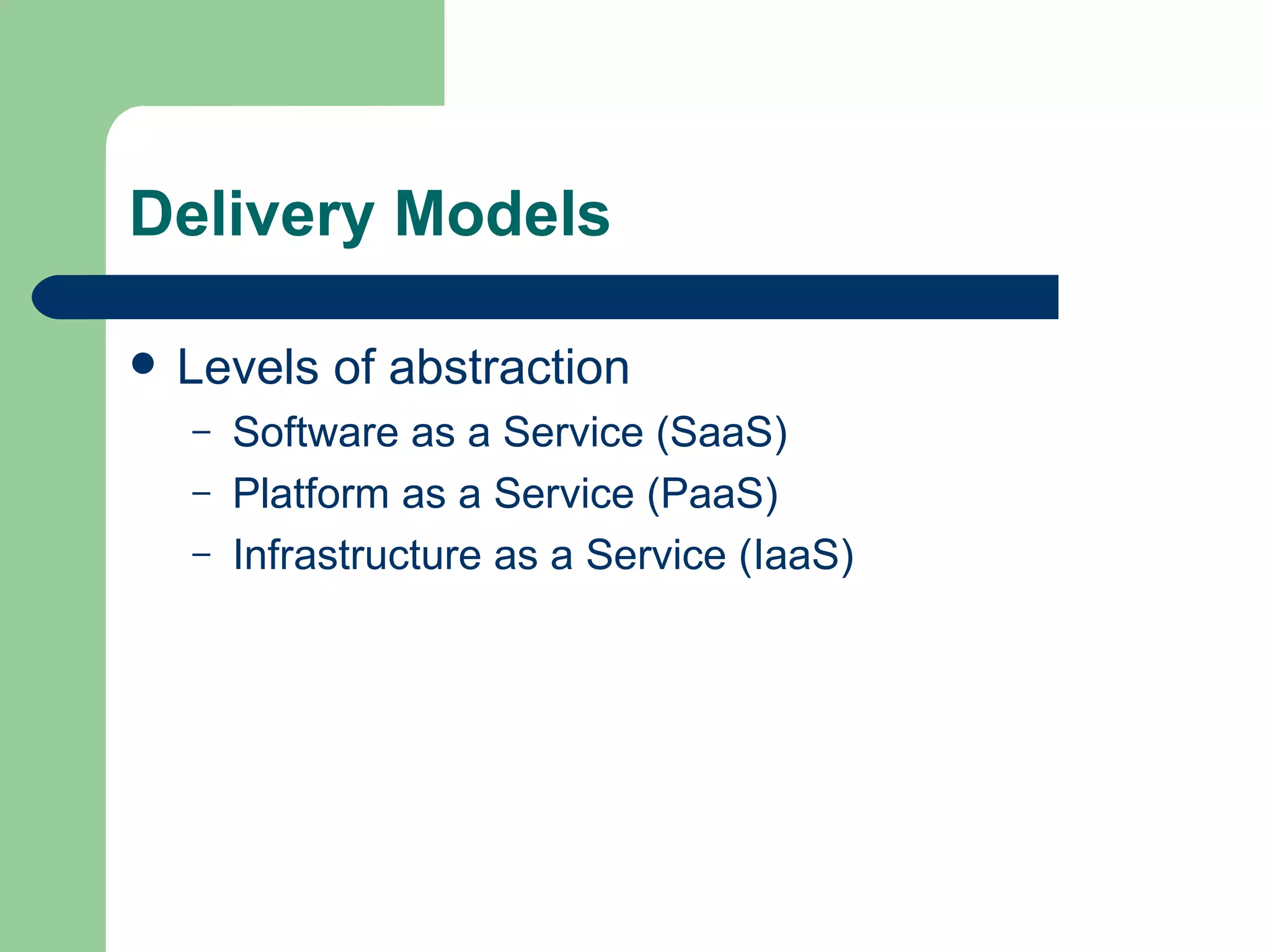
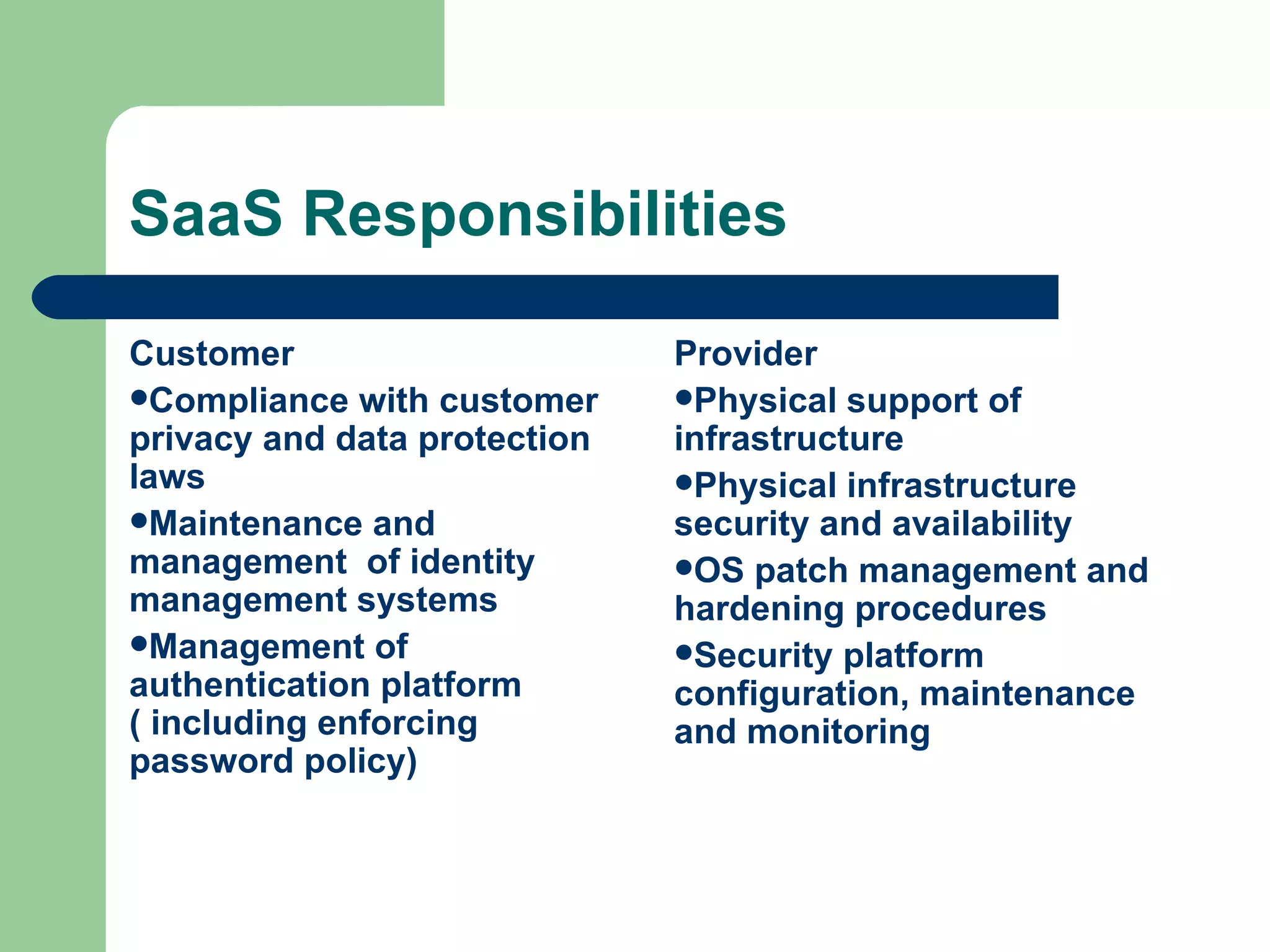
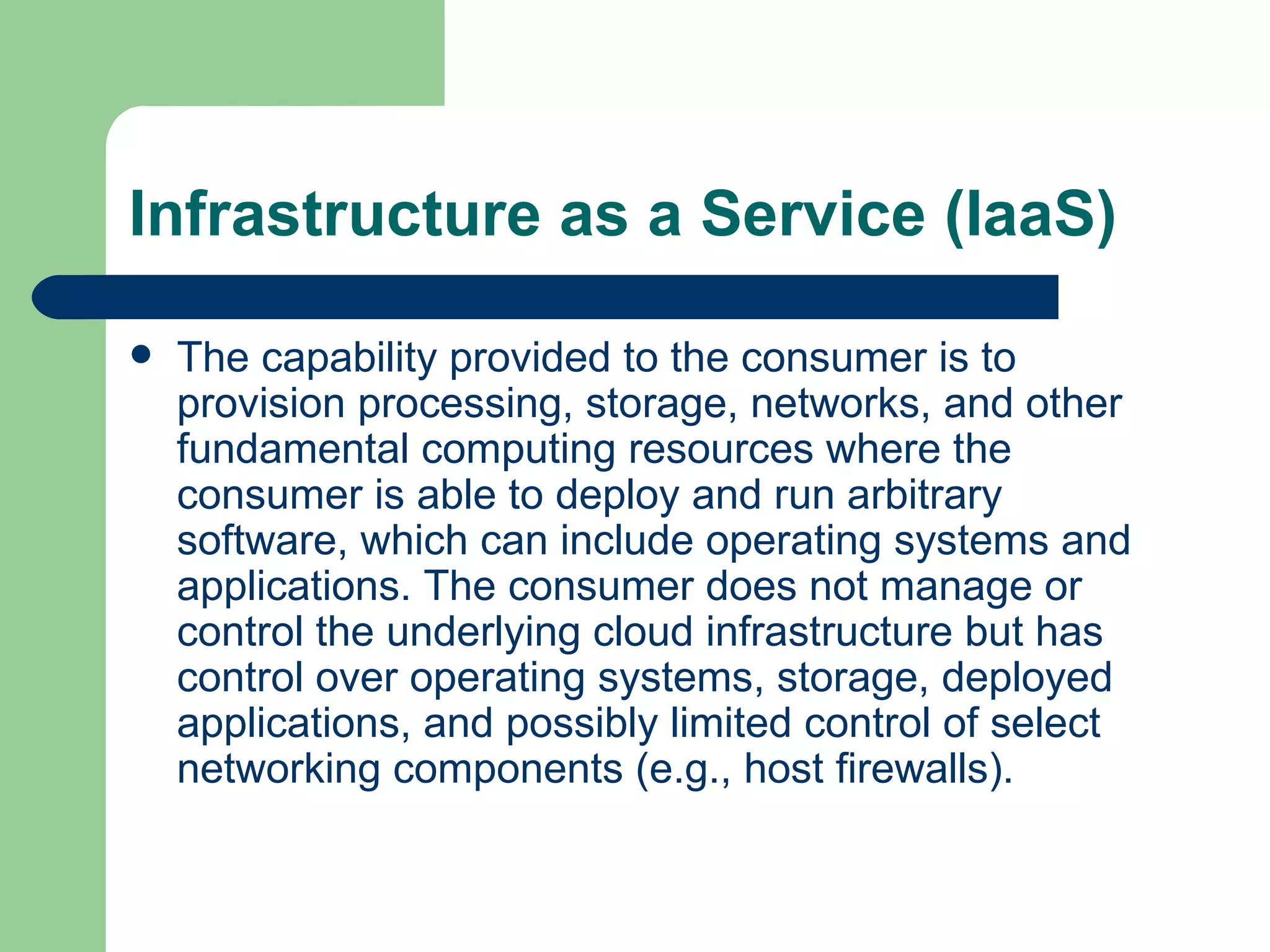
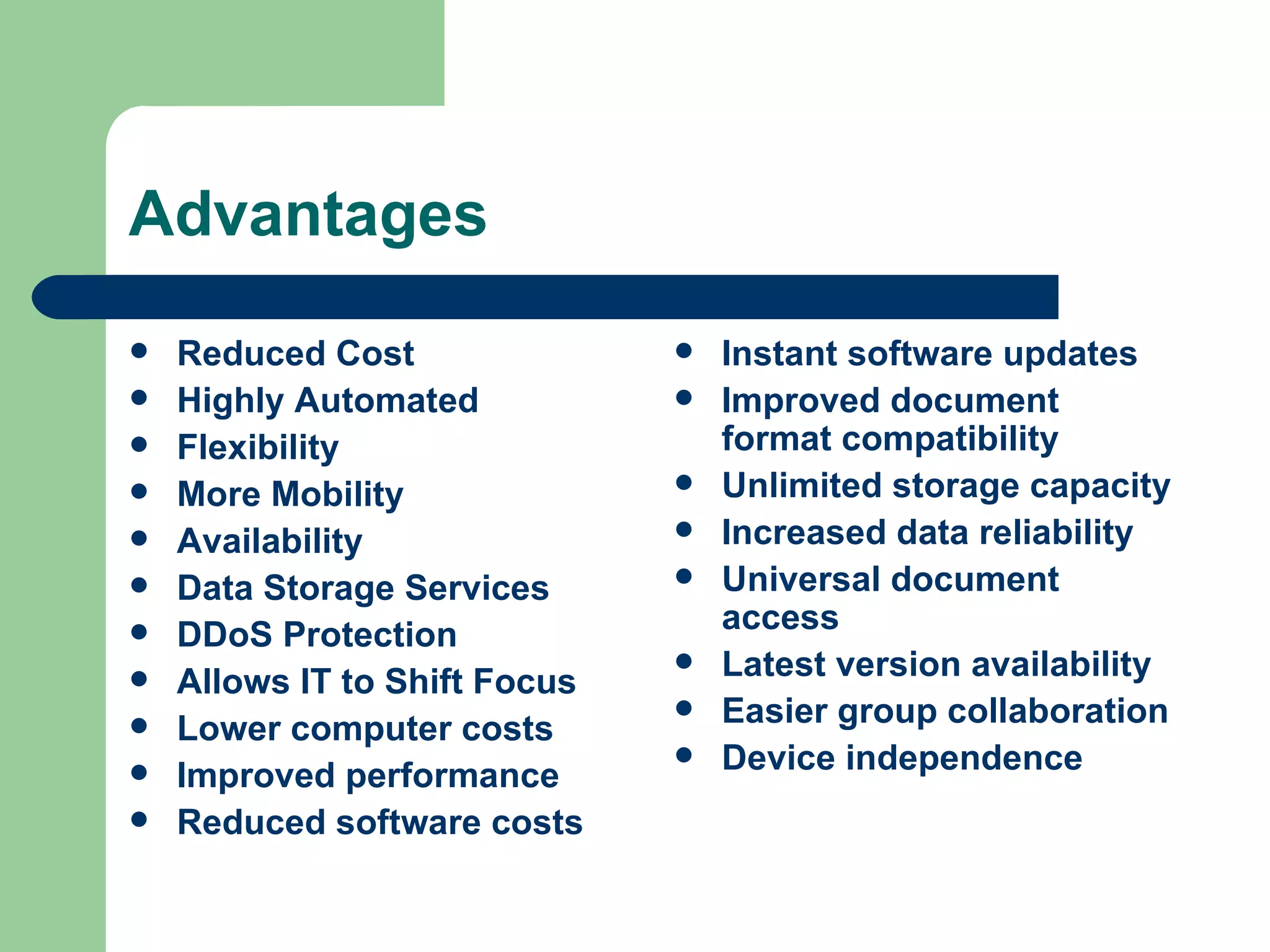
This document discusses cloud computing characteristics, service models, deployment models, risks, and security benefits. It defines cloud computing as on-demand access to configurable computing resources over a network. Key characteristics include rapid elasticity, broad network access, resource pooling, measured service, and self-service. Common models are Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Risks include vendor lock-in, loss of governance, and isolation failures, but cloud security can also be improved through large-scale implementation.


















![Just to be clear…. “ If your security sucks [before the cloud], you will be pleasantly surprised by the lack of change when you move to cloud.” --Christopher Hoff](https://image.slidesharecdn.com/smbcsacloudsecurity-13009807068464-phpapp02/75/Cloud-Computing-Security-Benefits-and-Risks-32-2048.jpg)