Malware and the Cost of Inactivity
•
11 likes•8,794 views
This document summarizes cybersecurity statistics from several reports published between 2013-2015. It finds that the average cost of a data breach rose to $5.9 million in 2014, with retail, financial services and healthcare being hit hardest. Mobile malware targeting Android devices increased, with web, network and email as the top infection vectors. The document also reports that 99% of cyberattacks are not detected in a timely manner, with over 2 years sometimes passing before a breach is discovered.
Report
Share
Report
Share
Download to read offline
Recommended
The Cost of Inactivity: Malware Infographic

As the cost and likelihood of a breach grows you can't afford "good enough" protection before, during, AND after an attack. Protect your brand and data with Cisco email and web security.
Learn more: http://cs.co/9003hKu3, http://cs.co/9003hKu9
Verizon Data Breach Investigations Report (DBIR) 2017

The Verizon Data Breach Investigation Report (DBIR) provides useful information related to information security. The information was obtained from a collaboration of many security organizations and vendors. The findings from the report confirm that phishing is a significant threat vector in today's environment. This presentations highlights key points from the DBIR related to phishing.
4 Facts Every Business Should Know About Phishing

This presentation highlights four facts about phishing. These facts prove that phishing is a serious information security risk for businesses.
Infographic - Three steps to stopping advanced email threats

Stop BEC, ransomware and other advanced threats with an advanced email security strategy. Here are three steps to get started.
2013 Threat Report

Cyberthreats broke new ground with mobile devices, while reaching deeper into social media. Online criminals also stepped up attacks via email, web and other traditional vectors.
Your Data Is Under Siege: Fortify Your Endpoints

1 in 5 businesses suffered a security breach in 2016. See the trends and learn how you can stop malware in its tracks.
Recommended
The Cost of Inactivity: Malware Infographic

As the cost and likelihood of a breach grows you can't afford "good enough" protection before, during, AND after an attack. Protect your brand and data with Cisco email and web security.
Learn more: http://cs.co/9003hKu3, http://cs.co/9003hKu9
Verizon Data Breach Investigations Report (DBIR) 2017

The Verizon Data Breach Investigation Report (DBIR) provides useful information related to information security. The information was obtained from a collaboration of many security organizations and vendors. The findings from the report confirm that phishing is a significant threat vector in today's environment. This presentations highlights key points from the DBIR related to phishing.
4 Facts Every Business Should Know About Phishing

This presentation highlights four facts about phishing. These facts prove that phishing is a serious information security risk for businesses.
Infographic - Three steps to stopping advanced email threats

Stop BEC, ransomware and other advanced threats with an advanced email security strategy. Here are three steps to get started.
2013 Threat Report

Cyberthreats broke new ground with mobile devices, while reaching deeper into social media. Online criminals also stepped up attacks via email, web and other traditional vectors.
Your Data Is Under Siege: Fortify Your Endpoints

1 in 5 businesses suffered a security breach in 2016. See the trends and learn how you can stop malware in its tracks.
4 Ways to Respond to Today's Advanced Threats

Knowing how cybercriminals are threatening security is the first step to securing your information—and your company’s goals. From social media vulnerabilities to digital extortion, the 2015 Symantec Internet Security Threat Report leverages an unparalleled amount of data and is the resource you need to quickly uncover digital threats.
Proofpoint Q3 - 2017 Email Fraud Threat Report

Proofpoint has a comprehensive solution to fight email fraud
Email fraud continues to expand its reach and attackers continue to shift in their approach. Proofpoint helps organizations stop all forms of email fraud with a comprehensive multi-layered solution.
To learn more about the email fraud landscape, read the full quarterly threat update here: www.proofpoint.com/us/resources/threat-reports/quarterly-email-fraud-report
For more information about how to stop impostor email attacks before they reach the inbox, please visit: www.proofpoint.com/us/solutions/email-fraud
Cyber attacks in 2021

Cybersecurity experts predict that cyber attacks will be twice as what happened in 2019. In 2021 it is predicted that a cyber attack will be reported every 11 seconds which is twice what it was in 2019 (every 19 seconds).
Petya Ransomware

Once we get beyond the immediate patchwork of solutions and accept that these attacks will continue, we need to think about how to best bolster response. Security orchestration allows for automation and improved capabilities to navigate the full scope of security operations and incident response activities from the initial alert through to remediation. Simply put, context, automation and analyst enablement ensure that the disease is cured, not just the symptoms.
Visit - https://siemplify.co
Presentation on Network Security

The world has seen incredible growth in networks and there is a large amount of information on networking infrastructures. Along with that different types of attacks have come to the picture. Due to all these Network Security is very important and has become a fundamental component in networks.
Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...

Cisco Advanced Malware Protection (AMP) for Endpoints prevents threats at point of entry, then continuously tracks every file it lets onto your endpoints. In this guide, we explore how the features and benefits of Cisco Advanced Malware Protection for Endpoints as well as ways you can get in touch if you would like to know more or put AMP to the test with a free trial.
https://re-solution.co.uk/security
2017 Cybersecurity Predictions

Read our cybersecurity predictions for 2017: http://researchcenter.paloaltonetworks.com/tag/2017-predictions/
These predictions are part of an ongoing blog series examining “Sure Things” (predictions that are almost guaranteed to happen) and “Long Shots” (predictions that are less likely to happen) in cybersecurity in 2017.
2015 Microsoft Vulnerabilities Report 

Avecto's annual report into Microsoft vulnerabilities uncovers how you can mitigate risk by removing admin rights.
Four Network Security Challenges for the Cloud Generation

Users are everywhere and need quick access to data and cloud applications around the clock. Your network protection must balance security, performance, complexity, and cost. Symantec Web Security Services protects you with uncompromised network security, delivered from the cloud.
Pen testing and how does it help strengthen cybersecurity

Penetration testing is designed to assess your security before an attacker does. By exploiting security vulnerabilities, penetration testing helps you determine how to best mitigate and protect your vital business data from future cybersecurity attacks.
A Hacker's perspective on ransomware

Microsoft MVP and pen tester, Paula Januszkiewicz takes a deep dive into ransomware, how it works and how it can be prevented.
180814 cloudsec2018 charles mok1

Understanding and Tackling Emerging Cyber Threats
Aug 14 2018
Trend Micro's CLOUDSEC 2018 "Freedom to Connect"
Containing the outbreak: The healthcare security pandemic

James Maude, Senior Security Engineer at Avecto examines the security state of play in the healthcare industry and why it’s now a prime target for hackers.
Istr number 23 internet security threat repor 2018 symantec

Istr number 23 internet security threat repor 2018 symantec
Proofpoint Understanding Email Fraud in 2018 

Email fraud, also known as business email compromise (BEC), is one of today's greatest cyber threats. These highly targeted attacks, sent in low volumes, target people rather than technologies. As a result, they are difficult for traditional security solutions to detect.
To better understand how email fraud is affecting companies like yours, Proofpoint commissioned a survey of more than 2,250 IT decision makers across the U.S., the U.K., Australia, France, and Germany. This infographic highlights our findings.
A Reality Check on the State of Cybersecurity

In 2015, companies need to challenge the perception of security versus the reality of a connected world of people, process, data and things in the Internet of Everything. Learn more at cisco.com/go/securityservices
Infographic: Security for Mobile Service Providers

This infographic offers an operator's view on mobile security trends, such as the technology innovations driving business gowth and security threats. It also suggests how you can protect customers.
More Related Content
What's hot
4 Ways to Respond to Today's Advanced Threats

Knowing how cybercriminals are threatening security is the first step to securing your information—and your company’s goals. From social media vulnerabilities to digital extortion, the 2015 Symantec Internet Security Threat Report leverages an unparalleled amount of data and is the resource you need to quickly uncover digital threats.
Proofpoint Q3 - 2017 Email Fraud Threat Report

Proofpoint has a comprehensive solution to fight email fraud
Email fraud continues to expand its reach and attackers continue to shift in their approach. Proofpoint helps organizations stop all forms of email fraud with a comprehensive multi-layered solution.
To learn more about the email fraud landscape, read the full quarterly threat update here: www.proofpoint.com/us/resources/threat-reports/quarterly-email-fraud-report
For more information about how to stop impostor email attacks before they reach the inbox, please visit: www.proofpoint.com/us/solutions/email-fraud
Cyber attacks in 2021

Cybersecurity experts predict that cyber attacks will be twice as what happened in 2019. In 2021 it is predicted that a cyber attack will be reported every 11 seconds which is twice what it was in 2019 (every 19 seconds).
Petya Ransomware

Once we get beyond the immediate patchwork of solutions and accept that these attacks will continue, we need to think about how to best bolster response. Security orchestration allows for automation and improved capabilities to navigate the full scope of security operations and incident response activities from the initial alert through to remediation. Simply put, context, automation and analyst enablement ensure that the disease is cured, not just the symptoms.
Visit - https://siemplify.co
Presentation on Network Security

The world has seen incredible growth in networks and there is a large amount of information on networking infrastructures. Along with that different types of attacks have come to the picture. Due to all these Network Security is very important and has become a fundamental component in networks.
Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...

Cisco Advanced Malware Protection (AMP) for Endpoints prevents threats at point of entry, then continuously tracks every file it lets onto your endpoints. In this guide, we explore how the features and benefits of Cisco Advanced Malware Protection for Endpoints as well as ways you can get in touch if you would like to know more or put AMP to the test with a free trial.
https://re-solution.co.uk/security
2017 Cybersecurity Predictions

Read our cybersecurity predictions for 2017: http://researchcenter.paloaltonetworks.com/tag/2017-predictions/
These predictions are part of an ongoing blog series examining “Sure Things” (predictions that are almost guaranteed to happen) and “Long Shots” (predictions that are less likely to happen) in cybersecurity in 2017.
2015 Microsoft Vulnerabilities Report 

Avecto's annual report into Microsoft vulnerabilities uncovers how you can mitigate risk by removing admin rights.
Four Network Security Challenges for the Cloud Generation

Users are everywhere and need quick access to data and cloud applications around the clock. Your network protection must balance security, performance, complexity, and cost. Symantec Web Security Services protects you with uncompromised network security, delivered from the cloud.
Pen testing and how does it help strengthen cybersecurity

Penetration testing is designed to assess your security before an attacker does. By exploiting security vulnerabilities, penetration testing helps you determine how to best mitigate and protect your vital business data from future cybersecurity attacks.
A Hacker's perspective on ransomware

Microsoft MVP and pen tester, Paula Januszkiewicz takes a deep dive into ransomware, how it works and how it can be prevented.
180814 cloudsec2018 charles mok1

Understanding and Tackling Emerging Cyber Threats
Aug 14 2018
Trend Micro's CLOUDSEC 2018 "Freedom to Connect"
Containing the outbreak: The healthcare security pandemic

James Maude, Senior Security Engineer at Avecto examines the security state of play in the healthcare industry and why it’s now a prime target for hackers.
Istr number 23 internet security threat repor 2018 symantec

Istr number 23 internet security threat repor 2018 symantec
Proofpoint Understanding Email Fraud in 2018 

Email fraud, also known as business email compromise (BEC), is one of today's greatest cyber threats. These highly targeted attacks, sent in low volumes, target people rather than technologies. As a result, they are difficult for traditional security solutions to detect.
To better understand how email fraud is affecting companies like yours, Proofpoint commissioned a survey of more than 2,250 IT decision makers across the U.S., the U.K., Australia, France, and Germany. This infographic highlights our findings.
What's hot (20)
Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...

Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...
Four Network Security Challenges for the Cloud Generation

Four Network Security Challenges for the Cloud Generation
Pen testing and how does it help strengthen cybersecurity

Pen testing and how does it help strengthen cybersecurity
Containing the outbreak: The healthcare security pandemic

Containing the outbreak: The healthcare security pandemic
Istr number 23 internet security threat repor 2018 symantec

Istr number 23 internet security threat repor 2018 symantec
Trend micro research covid19 threat brief summary 27 mar

Trend micro research covid19 threat brief summary 27 mar
Viewers also liked
A Reality Check on the State of Cybersecurity

In 2015, companies need to challenge the perception of security versus the reality of a connected world of people, process, data and things in the Internet of Everything. Learn more at cisco.com/go/securityservices
Infographic: Security for Mobile Service Providers

This infographic offers an operator's view on mobile security trends, such as the technology innovations driving business gowth and security threats. It also suggests how you can protect customers.
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE reduces the attack surface by controlling access and preventing unauthorized lateral movement on the network. Learn more at http://cs.co/9007BRFbW
Midsize Business Solutions: Cybersecurity

You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network.
To deal with these challenges, you need a smart, scalable threat-centric security model. This model needs to provide cost-effective threat remediation and support standard security policies and controls.
Cisco can help. We deliver intelligent cybersecurity for the real world. Our threat-centric approach reduces complexity while delivering superior visibility and control—saving you time and reducing costs.
With Cisco, you gain advanced threat protection across the entire attack continuum—before, during, and after an attack. To learn more, visit http://cs.co/mmigvepg
What is Inbound Recruiting?

Finding and hiring amazing people is hard. Build your employer brand and create a personalized candidate experience with inbound recruiting.
Data Center Security Challenges

More than a technology issue - it's a human problem. Learn more at www.cisco.com/go/acisecurity.
Modern Prospecting Techniques for Connecting with Prospects (from Sales Hacke...

Sales is a difficult world to be in because buyers aren't putting up with salespeople anymore. Instead of helping and building relationships, sales reps are still focused on closing prospects - even when they aren't ready to buy! So buyers ignore them. Because of that, even great sales reps would be lucky to get on the phone with someone.
While buyers have evolved and become more sophisticated, sales reps and training programs have been slow to adapt to that change.
Learn actionable modern prospecting techniques you can apply immediately from two best selling authors and sales experts: Max Altschuler CEO of Sales Hacker, and Mark Roberge CRO of HubSpot.
Class 1: Email Marketing Certification course: Email Marketing and Your Business

*From HubSpot Academy*
Over the past few decades, people have radically changed the way they live, work and buy. This class will give you an overview of an adaptive, inbound approach to sending emails that provide value and drive growth for your business. It will also teach you about the four big themes of a modern email marketing program: segmentation, personalization, mobile, and optimization.
3 Proven Sales Email Templates Used by Successful Companies

76% of emails never get opened. That makes life for salespeople very difficult. So we've partnered up with Breakthrough Email to bring you email templates that are proven to engage prospects and close more deals. Start using them today and grow your revenue.
Add the Women Back: Wikipedia Edit-a-Thon

The lack of visible female role models is pervasive in the tech industry, particularly on Wikipedia, where just under 17% of Wikipedia biographies were on women. That's why HubSpot wrote fourteen Wikipedia entries for remarkable women in tech to help inspire young women to reach positions at the highest levels of STEM.
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Cognitive Threat Analytics is a technology that analyzes web requests to identify Command & Control traffic, identifying threats that are currently present in a network. It is currently available across the entire Cisco Web Security portfolio, including Cloud Web Security (CWS) and the Web Security Appliance (WSA). To learn more, watch this webinar: http://cs.co/9000BuggO
10 Things You Didn’t Know About Mobile Email from Litmus & HubSpot

Learn how to use email more effectively with 10 new tips you didn't already know about optimizing email for mobile.
25 Discovery Call Questions

Discovery is the most crucial part of a sales process. Here are HubSpot sales director Dan Tyre's 25 tried-and-true must-ask questions.
Behind the Scenes: Launching HubSpot Tokyo

HubSpot officially opened its doors in Japan in September 2016. Check out behind-the-scenes photos of the launch day and get to know the Tokyo team!
Pervasive Security Across Your Extended Network

There are many ways attackers can access your network. Keep yours safe before, during, and after an attack with best-in-class Cisco Security designed to protect your business data. Learn more at http://cs.co/9009BJ8o3
How to Earn the Attention of Today's Buyer

Buyers no longer use voicemails and emails from strangers to learn about products. This information is online, whenever buyers are interested. This SlideShare presentation show sellers how to connect in a meaningful way by starting conversations around the buyer’s plans, goals and challenges.
This presentation is one class in HubSpot Academy's free sales training course. You can enroll here: http://certification.hubspot.com/inbound-sales-certification
Viewers also liked (18)
Infographic: Security for Mobile Service Providers

Infographic: Security for Mobile Service Providers
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE Reduces the Attack Surface by Controlling Access
Modern Prospecting Techniques for Connecting with Prospects (from Sales Hacke...

Modern Prospecting Techniques for Connecting with Prospects (from Sales Hacke...
Class 1: Email Marketing Certification course: Email Marketing and Your Business

Class 1: Email Marketing Certification course: Email Marketing and Your Business
3 Proven Sales Email Templates Used by Successful Companies

3 Proven Sales Email Templates Used by Successful Companies
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...
10 Things You Didn’t Know About Mobile Email from Litmus & HubSpot

10 Things You Didn’t Know About Mobile Email from Litmus & HubSpot
Similar to Malware and the Cost of Inactivity
Symantec's Internet Security Threat Report for the Government Sector

Symantec has established the most comprehensive source of Internet threat data in the world through the Symantec Global Intelligence Network, which is made up of more than 41.5 million attack sensors and records thousands of events per second. This network monitors threat activity in over 157 countries and territories through a combination of Symantec products and services such as Symantec DeepSight Threat Management System, Symantec Managed Security Services, Norton consumer products, and other third-party data sources.
In addition, Symantec maintains one of the world’s most comprehensive vulnerability databases, currently consisting of more than 60,000 recorded vulnerabilities (spanning more than two decades) from over 19,000 vendors representing over 54,000 products.
Spam, phishing, and malware data is captured through a variety of sources including the Symantec Probe Network, a system of more than 5 million decoy accounts, Symantec.cloud, and a number of other Symantec security technologies. Skeptic, the Symantec.cloud proprietary heuristic technology, is able to detect new and sophisticated targeted threats before they reach customers’ networks. Over 8.4 billion email messages are processed each month and more than 1.7 billion web requests filtered each day across 14 data centers. Symantec also gathers phishing information through an extensive anti-fraud community of enterprises, security vendors, and more than 50 million consumers.
Symantec Trust Services provides 100 percent availability and processes over 6 billion Online Certificate Status Protocol (OCSP) look-ups per day, which are used for obtaining the revocation status of X.509 digital certificates around the world. These resources give Symantec analysts unparalleled sources of data with which to identify, analyze, and provide informed commentary on emerging trends in attacks, malicious code activity, phishing, and spam. The result is the annual Symantec Internet Security Threat Report, which gives enterprises, small businesses, and consumers essential information to secure their system effectively now and into the future.
Protect Your Enterprise - Check Point SandBlast Mobile

Prezentace ze semináře Check Point CPX Highlights
Praha, 13.6.2017
Securing the Cloud

GGV Managing Partner Glenn Solomon reviews the current state of cybersecurity, the key targets and threats, and how the landscape is evolving.
Symantec Cyber Security Intelligence Report

As reported in the ISTR Volume 19, 2013 saw a 500 percent increase in ransomware in the latter part of the year. Overall ransomware levels remained high through March 2014, and then slowly started to decline, in part due to the disruption of the GameOver Zeus botnet back in late May.
In contrast, crypto-style ransomware has seen a 700 percent-plus increase. These file-encrypting versions of ransomware began the year comprising 1.2 percent of all ransomware detec¬tions, but now make up 31 percent at the end of August. One variant known as Trojan.Cryptodefense began to appear in large numbers in early June. By the end of July, it made up 77 percent of all crypto-style ransomware for the year to date. This follows predictions in the ISTR saying this type of malware would become more common in 2014.
Over 31.5 million identities were reported exposed in August, from 12 incidents. The jump in exposed identities is due to a large breach in South Korea, comprising 27 million identities. In the last 12 months 53 percent of data breaches were caused by hacking and 21 percent were accidentally made public.
The average number of spear-phishing emails blocked each day for August was 20, compared with 54 in July and 88 in June. This is below the year-to-date average of 86, which is slightly higher than the daily average of 84 for all if 2013.
The most frequently used malicious file types in these email-based targeted attacks were .exe and .doc file types, with .exe attachments coming out on top this month at 31.8 percent. 29 percent of spear phishing emails were sent to Manufacturing, returning it to the top of the industries targeted.
One in 1,587 emails was identified as a phishing attempt, compared with one in 1,298 for July and one in 496 in June. While at first glance this looks like a big drop, it is not indica¬tive of a wider trend just yet, resulting in only a 0.01 percentage point decrease in the overall phishing rate.
We hope that you enjoy this month’s report and feel free to contact us with any comments or feedback.
Internet Security Threat Report 2014 :: Volume 19 Appendices - The hardcore n...

Internet Security Threat Report 2014 :: Volume 19 :: Appendices
Hardcore data from Symantec’s Internet Security Threat Report.
Real number crunching on Threat Malicious Code, Fraud & Vulnerability trends including
Threat Activity Trends
• Malicious Activity by Source
• Malicious Web-Based Attack Prevalence
• Analysis of Malicious Web Activity by Attack Toolkits
• Analysis of Web-Based Spyware, Adware, and Potentially Unwanted Programs
• Analysis of Web Policy Risks from Inappropriate Use
• Analysis of Website Categories Exploited to Deliver Malicious Code
• Bot-Infected Computers
• Analysis of Mobile Threats
• Quantified Self – A Path to Self-Enlightenment or Just Another Security Nightmare?
• Data Breaches that could lead to Identity Theft
• Threat of the Insider
• Gaming Attacks
• The New Black Market
Malicious Code Trends
• Top Malicious Code Families
• Analysis of Malicious Code Activity
by Geography, Industry Sector, and Company Size
• Propagation Mechanisms
• Email-Targeted Spear-Phishing Attacks Intelligence
Spam and Fraud Activity Trends
• Analysis of Spam Activity Trends
• Analysis of Spam Activity by Geography, Industry Sector, and Company Size
• Analysis of Spam Delivered by Botnets
• Significant Spam Tactics
• Analysis of Spam by Categorization
• Phishing Activity Trends
• Analysis of Phishing Activity by Geography, Industry Sector, and Company Size
• New Spam Trend: BGP Hijacking
Vulnerability Trends
• Total Number of Vulnerabilities
• Zero-Day Vulnerabilities
• Web Browser Vulnerabilities
• Web Browser Plug-in Vulnerabilities
• Web Attack Toolkits SCADA Vulnerabilities
Symantec Intelligence Report September 2014

Symantec Intelligence aims to provide the latest analysis of cyber security threats, trends, and insights concerning malware, spam, and other potentially harmful business risks.
The average number of spear-phishing attacks rose to 53 per day in September, after a 12-month low in August. Spear phishing activity has returned to levels seen earlier in the summer, but is still down from the 12-month average of 85 attacks per day.
The .doc file type was the most common attachment type used in spear-phishing attacks, making up more than 52.9 percent of all attachments in September. At 4.8 percent, last month’s top attachment, .exe file types, dropped to fourth.
There were only four publically disclosed data breaches that took place within the month September, resulting in the exposure of 2.5 million identities. However, there were 14 additional data breaches reported in September that took place earlier in the year. The largest data breach reported in September actually took place in April, and resulted in the exposure of 56 million identities.
Ransomware continues to decline as 2014 progresses. However, crypto-style ransomware remains high, making up 38 percent of all ransomware detected in September.
There were 600 vulnerabilities disclosed in the month of September, the highest number so far in 2014 and second highest in last 12 months.
One in 2,041 emails was identified as a phishing attempt, compared with one in 1,587 for August. While at first glance this looks like a big drop, it results in only a 0.01 percentage point decrease in the overall phishing rate.
Symantec Website Security Threat Report 2014 - RapidSSLOnline

Symantec Website Security Threat Report 2014!
Cybersecurity PowerPoint Presentation

This is the PowerPoint presentation of Cybersecurity for Research Paper or Seminar. For more details go to my YouTube channel and watch this video:-
https://youtu.be/ldrOSxIRW2w
Thank You!!
Key Findings from the 2015 IBM Cyber Security Intelligence Index

View on-demand presentation: http://securityintelligence.com/events/ibm-2015-cyber-security-intelligence-index/
The cyber threat landscape is increasing in complexity and frequency. Organizations that have historically not been the target of cyber attacks now make headline news with large data losses and compromised transactions. Organizations need a clear point of view on how to respond to these threats, and one that incorporates not only the relevant technology but also the organizational changes needed.
Nick Bradley, Practice Leader of the IBM Threat Research Group and the X-Force Threat Analysis Team, and Nick Coleman, Global Head Cyber Security Intelligence Services outline what organizations need to do now and in the future to stay ahead of the growing cyber security threat.
PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018

In 2017, PandaLabs analyzed and neutralized a total of 75 million malware files, about 285,000 new samples a day.
Find out more: http://bit.ly/2mXbIQy
Symantec Intelligence Report December 2014

Welcome to the December edition of the Symantec Intelligence report. Symantec Intelligence aims to provide the latest analysis of cyber security threats, trends, and insights concerning malware, spam, and other potentially harmful business risks.
IT Security and Wire Fraud Awareness Slide Deck

A presentation on IT security, wire fraud and trends in information technology. The information is focused on making the audience aware of the new threats, how to protect against them, and what measures you can take to keep your critical information secure.
Building Human Intelligence – Pun Intended

Presented by: Rohyt Belani, Phishme
Abstract: In the physical world, the human brain has evolved to avoid danger. The threat of physical pain triggers fear – and we have learned to avoid behavior that causes pain. In the electronic world of email, however, this concept doesn’t translate. Clicking on a malicious link or opening an attachment laced with malware doesn’t cause pain, and often a user won’t even notice anything is wrong after doing it. How then, can we teach fear perception in the electronic world? Is it even possible? In this presentation I’ll discuss how immersive training can key on psychological triggers to teach people to become skeptical email users who not only avoid undesired security behavior but can aid intrusion detection by reporting suspicious emails, helping to mitigate one of the most serious problems in security: slow incident detection times. According to reports from Mandiant and Verizon, average detection time for an incident is in the hundreds of days. A properly trained workforce is not only resilient to phishing attacks, but can improve detection times as well.
5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016

1 - Today's challenges.
2- IBM Security Intelligent strategy
3- IBM Security Q-Radar
5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016

View ondemand webinar: https://securityintelligence.com/events/qradar-investment-2016/
Helping you stay ahead of cybercriminals means our work at IBM Security is never done. With data coming from every direction to collect, you need real time and historical analytics to discover anomalistic conditions that often provide the early warning signs of an attacker’s presence. Join us to hear about new features in IBM Security QRadar that can provide you with better visibility into what’s happening on your network and new integrations that will help you multiply your investment and help speed your remediation efforts.
Best practices for_implementing_security_awareness_training

Best practices for_implementing_security_awareness_training
Similar to Malware and the Cost of Inactivity (20)
Symantec's Internet Security Threat Report for the Government Sector

Symantec's Internet Security Threat Report for the Government Sector
Protect Your Enterprise - Check Point SandBlast Mobile

Protect Your Enterprise - Check Point SandBlast Mobile
Internet Security Threat Report 2014 :: Volume 19 Appendices - The hardcore n...

Internet Security Threat Report 2014 :: Volume 19 Appendices - The hardcore n...
Symantec Website Security Threat Report 2014 - RapidSSLOnline

Symantec Website Security Threat Report 2014 - RapidSSLOnline
Key Findings from the 2015 IBM Cyber Security Intelligence Index

Key Findings from the 2015 IBM Cyber Security Intelligence Index
PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018

PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018
5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016

5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016
5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016

5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016
Best practices for_implementing_security_awareness_training

Best practices for_implementing_security_awareness_training
More from Cisco Security
Incident Response Services Template - Cisco Security

When responding to a security incident, communication is perhaps one of the most important, and yet, most overlooked aspects. This Cisco Security Incident Response Services Template has been used and refined for a number of years now in both Fortune 100 companies as well as with all of our Cisco Security Incident Response Services customers.
Learn more about incident response communications here: https://blogs.cisco.com/security/incident-response-fundamentals-communication
Cisco Web and Email Security Overview

The top two attack vectors for malware are email and web browsers. Watering-hole attacks conceal malware on member-based sites and phishing scams can target individuals with personal details. This PPT describes a different security approach to protect against these threats while achieving business growth, efficiency and lowered expenses. The presentation features Cisco Email, Web and Cloud Web Security and covers basic features, offers, benefits, newest features and product integrations. Watch the webinar: http://cs.co/9004BGqvy
Cisco 2015 Midyear Security Report Slide Deck

Download the full Midyear Security Report >> http://cs.co/MSR15SL
Cisco has released its Midyear Security Report. In this report, Cisco provides industry insights and key findings taken from threat intelligence and cybersecurity trends for the first half of 2015.
3 Tips for Choosing a Next Generation Firewall

Discover the top three tips when choosing a NGFW to protect your business from attacks. Learn more: http://cs.co/9001BD8k1
AMP Helps Cisco IT Catch 50% More Malware threats

These statistics show how the Email Security Appliance with Advanced Malware Protection allows Cisco IT to realize its comprehensive threat-centric email security strategy. Learn more: http://cs.co/9000BD620
Balance Data Center Security and Performance

Today's data centers require an approach to security that does not compromise performance or functionality. Identify where you may have gaps in your data center security, and learn what solutions are available to close or mitigate those gaps. Take action to secure your data center. Download our white paper >> http://cs.co/9000BBV22
Enterprise Strategy Group: Security Survey

Understand what your organization is up against and where security is needed.
Cisco Addresses the Full Attack Continuum

Learn key capabilities to improve protection from advanced attacks. Featuring research from Gartner.
Infonetics Network and Content Security Vendor Scorecard

Profiles, analyzes and ranks the 8 largest global vendors of network and content security solutions.
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner report on Cisco TrustSec assessing technical components, interoperability considerations, Cisco’s progress in implementing support across product lines and customer deployment experiences.
Cisco 2014 Midyear Security Report

Download now to learn the latest industry trends and how to identify weak links in the security chain.
String of Paerls Infographic

String of Paerls –> Learn how an integrated threat defense can both detect and protect against socially engineered exploits. https://communities.cisco.com/docs/DOC-54686
Midyear Security Report Infographic

Get more details from the Cisco Midyear Security Report >> http://cs.co/MSR14_S
Cisco Annual Security Report Infographic

Growing Attacks Against the Internet Infrastructure. Learn more from the Cisco Annual Security Report: http://cs.co/CASR14_L
City of Tomorrow Builds in Next-Generation Security

City of El Paso relies on Cisco ASA 5585-X Series to secure network to best deliver municipality’s services.
Laser Pioneer Secures Network End-to-End to Protect Assets

Coherent mitigates against global cyber threats with Cisco Cloud Web Security.
McAllen Intermediate School District

Migrated to Cisco Identity Services Engine (ISE) 1.2 as best solution to level academic environment with secure network access: Transforming Learning in Campus, Classroom & Community.
Leveraging Context-Aware Security to Safeguard Patient Data

Texas Heart Institute controls network access to meet regulatory compliance needs for its locations located in the world’s largest medical complex.
William Paterson University

Transitioned to Cisco Identity Services Engine (ISE) 1.2 to facilitate consistent, secure wireless network access by students bringing range of devices on campus, broadening reach of bring- your-own-device (BYOD) policy.
More from Cisco Security (20)
Incident Response Services Template - Cisco Security

Incident Response Services Template - Cisco Security
Infonetics Network and Content Security Vendor Scorecard

Infonetics Network and Content Security Vendor Scorecard
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...
The Evolution of and Need for Secure Network Access

The Evolution of and Need for Secure Network Access
City of Tomorrow Builds in Next-Generation Security

City of Tomorrow Builds in Next-Generation Security
Laser Pioneer Secures Network End-to-End to Protect Assets

Laser Pioneer Secures Network End-to-End to Protect Assets
Leveraging Context-Aware Security to Safeguard Patient Data

Leveraging Context-Aware Security to Safeguard Patient Data
Recently uploaded
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

In this insightful webinar, Inflectra explores how artificial intelligence (AI) is transforming software development and testing. Discover how AI-powered tools are revolutionizing every stage of the software development lifecycle (SDLC), from design and prototyping to testing, deployment, and monitoring.
Learn about:
• The Future of Testing: How AI is shifting testing towards verification, analysis, and higher-level skills, while reducing repetitive tasks.
• Test Automation: How AI-powered test case generation, optimization, and self-healing tests are making testing more efficient and effective.
• Visual Testing: Explore the emerging capabilities of AI in visual testing and how it's set to revolutionize UI verification.
• Inflectra's AI Solutions: See demonstrations of Inflectra's cutting-edge AI tools like the ChatGPT plugin and Azure Open AI platform, designed to streamline your testing process.
Whether you're a developer, tester, or QA professional, this webinar will give you valuable insights into how AI is shaping the future of software delivery.
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Recently uploaded (20)
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
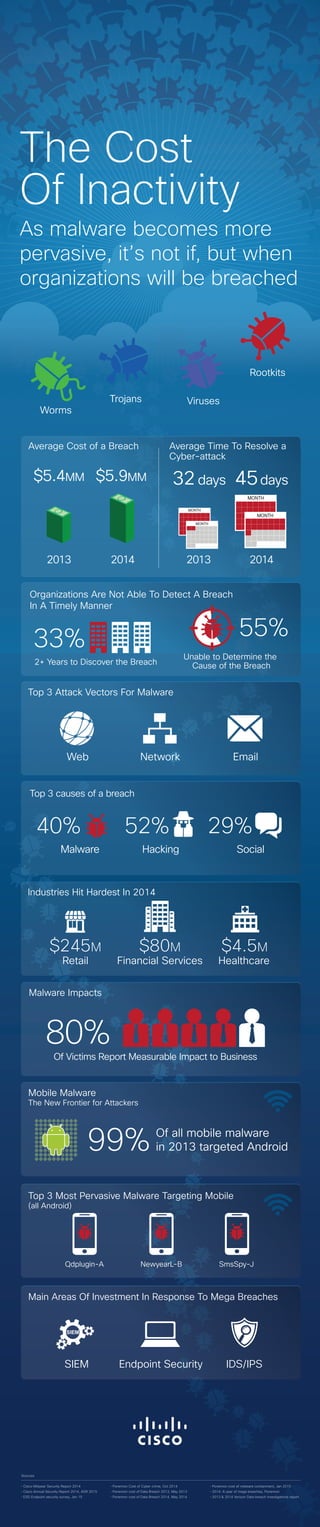
Malware and the Cost of Inactivity
- 1. Sources • Cisco Midyear Security Report 2014 • Cisco Annual Security Report 2014, ASR 2015 • ESG Endpoint security survey, Jan 15 • Ponemon Cost of Cyber crime, Oct 2014 • Ponemon cost of Data Breach 2013, May 2013 • Ponemon cost of Data Breach 2014, May 2014 • Ponemon cost of malware containment, Jan 2015 • 2014: A year of mega breaches, Ponemon • 2013 & 2014 Verizon Data breach investigations report Mobile Malware The New Frontier for Attackers 20142013 20142013 $5.9MM$5.4MM 32days Worms Trojans Viruses Rootkits Top 3 Attack Vectors For Malware Web Network Email Qdplugin-A NewyearL-B SmsSpy-J Top 3 Most Pervasive Malware Targeting Mobile (all Android) Industries Hit Hardest In 2014 Retail $245M $80M $4.5M Financial Services Healthcare Main Areas Of Investment In Response To Mega Breaches SIEM Endpoint Security IDS/IPS Average Cost of a Breach Average Time To Resolve a Cyber-attack 99% MONTH MONTH MONTH MONTH 45days Organizations Are Not Able To Detect A Breach In A Timely Manner 2+ Years to Discover the Breach 33% 55% Unable to Determine the Cause of the Breach Of all mobile malware in 2013 targeted Android Malware Impacts Of Victims Report Measurable Impact to Business 80% The Cost Of Inactivity As malware becomes more pervasive, it’s not if, but when organizations will be breached Top 3 causes of a breach Malware Hacking Social 40% 52% 29%
