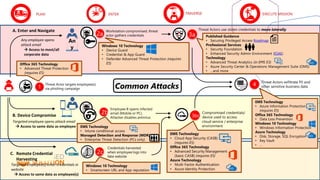
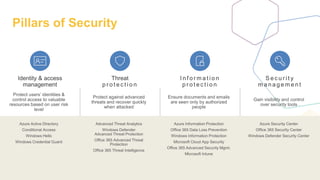
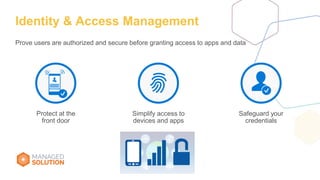
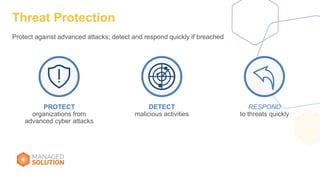
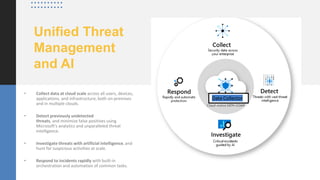
The document discusses strategies and tools for maintaining security while working from home, emphasizing both internal and external measures. It outlines essential tools such as advanced threat protection, identity management, and data loss prevention to safeguard against various threats. The document also raises critical questions for organizations to consider as they develop security policies and practices.