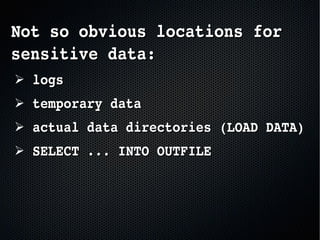
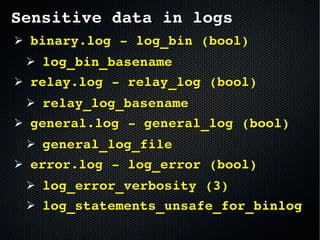
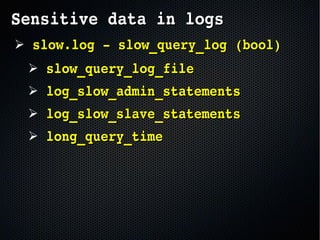
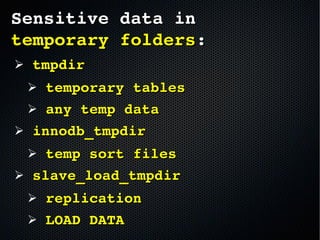
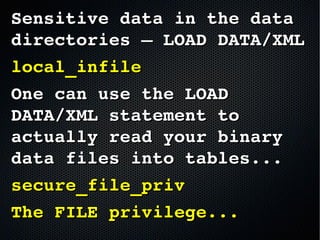
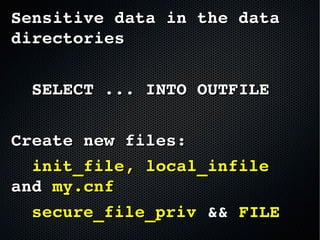
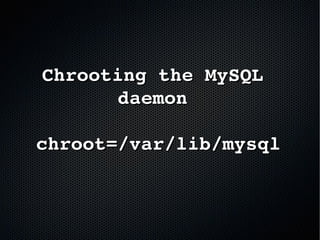
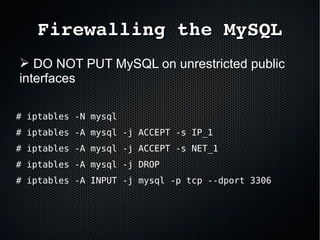
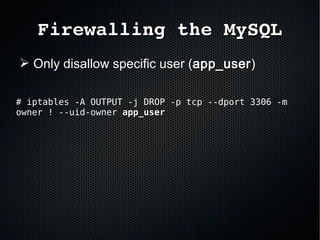
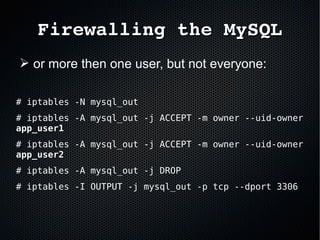
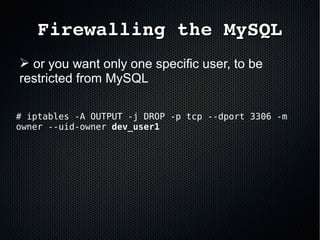
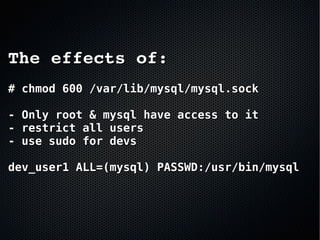
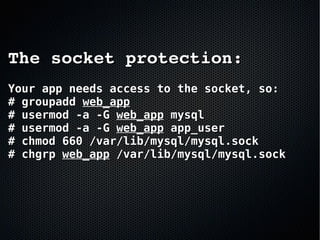
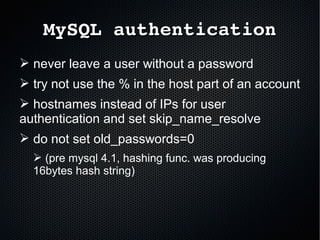
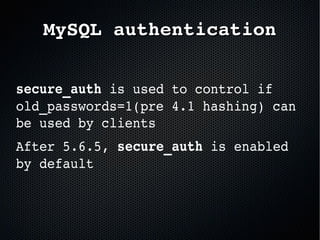
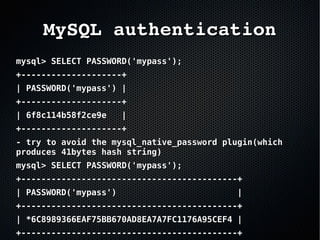
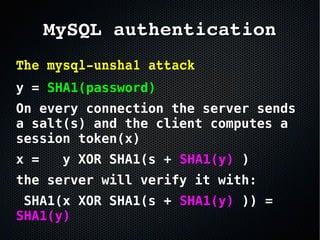
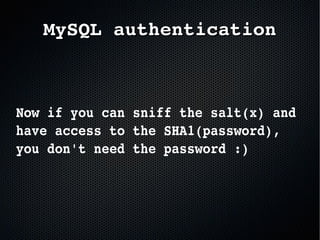
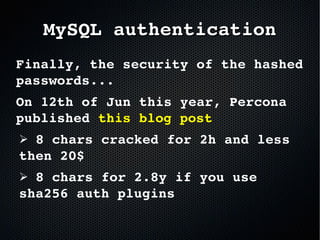
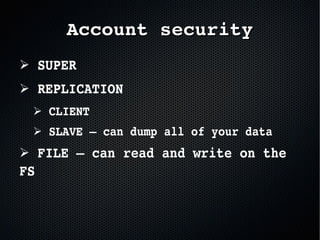
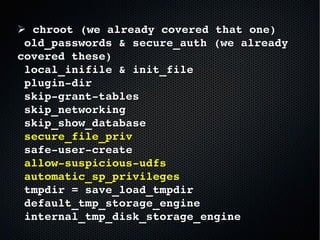
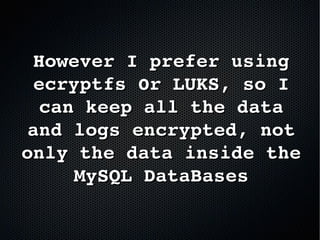
The document discusses the importance of securing MySQL servers, highlighting risks associated with storing sensitive data like passwords in plain text and vulnerabilities in default configurations. It emphasizes best practices like using secure hashing algorithms, encrypting sensitive data, implementing firewalls, and controlling access to MySQL sockets and authentication. Furthermore, it explores data encryption at rest and the limitations of built-in MySQL encryption features, recommending external tools for comprehensive security.