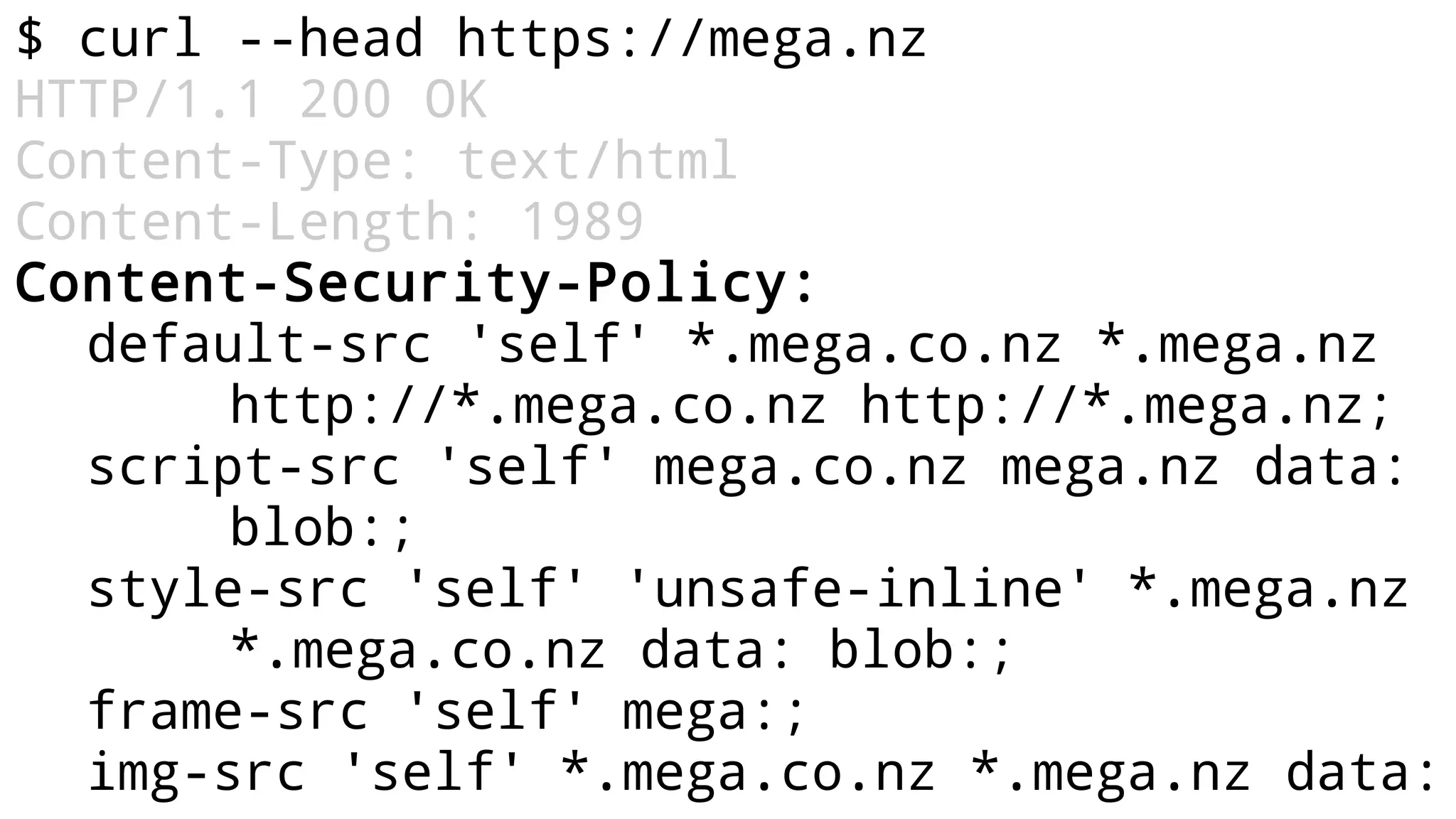
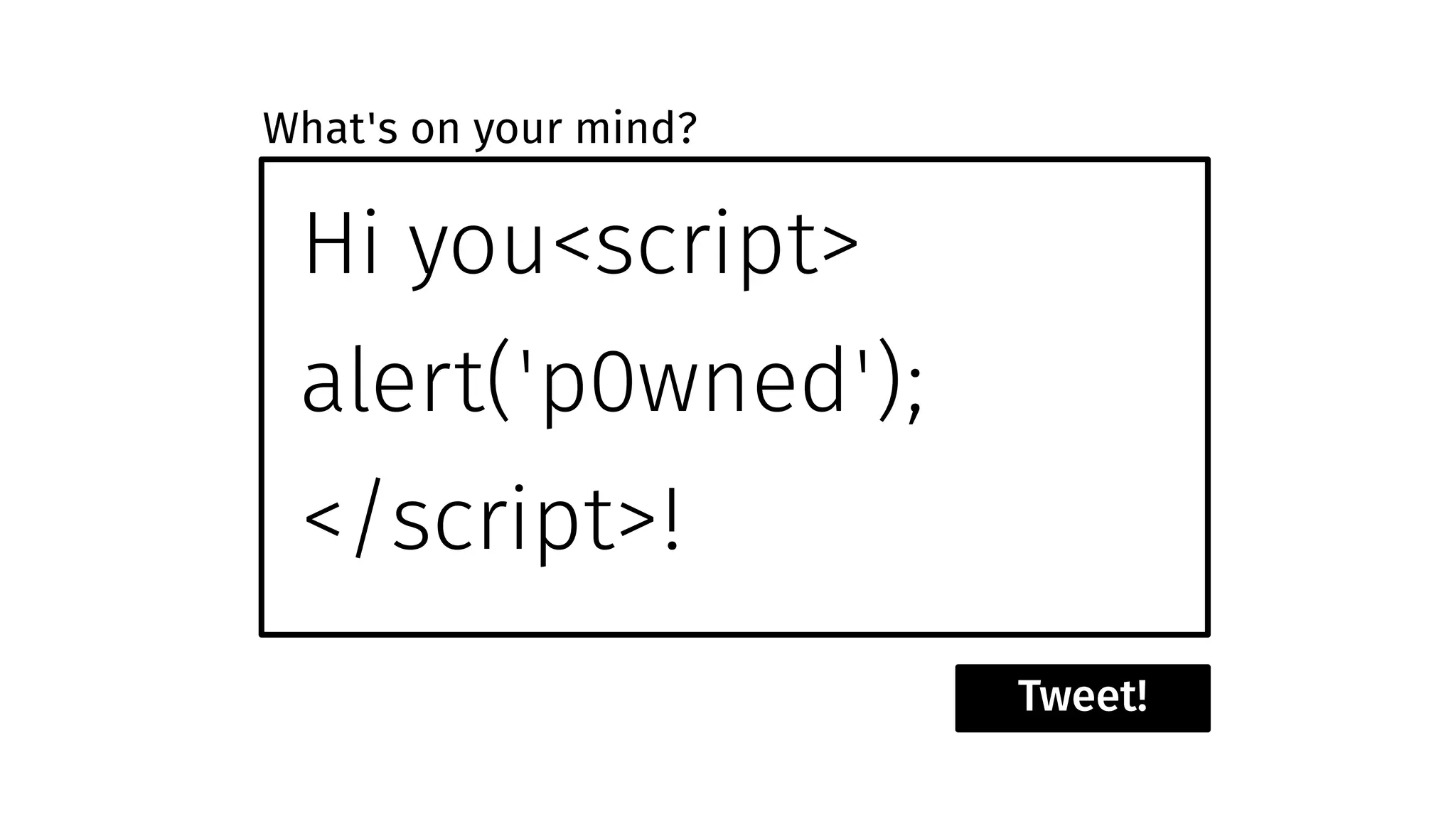
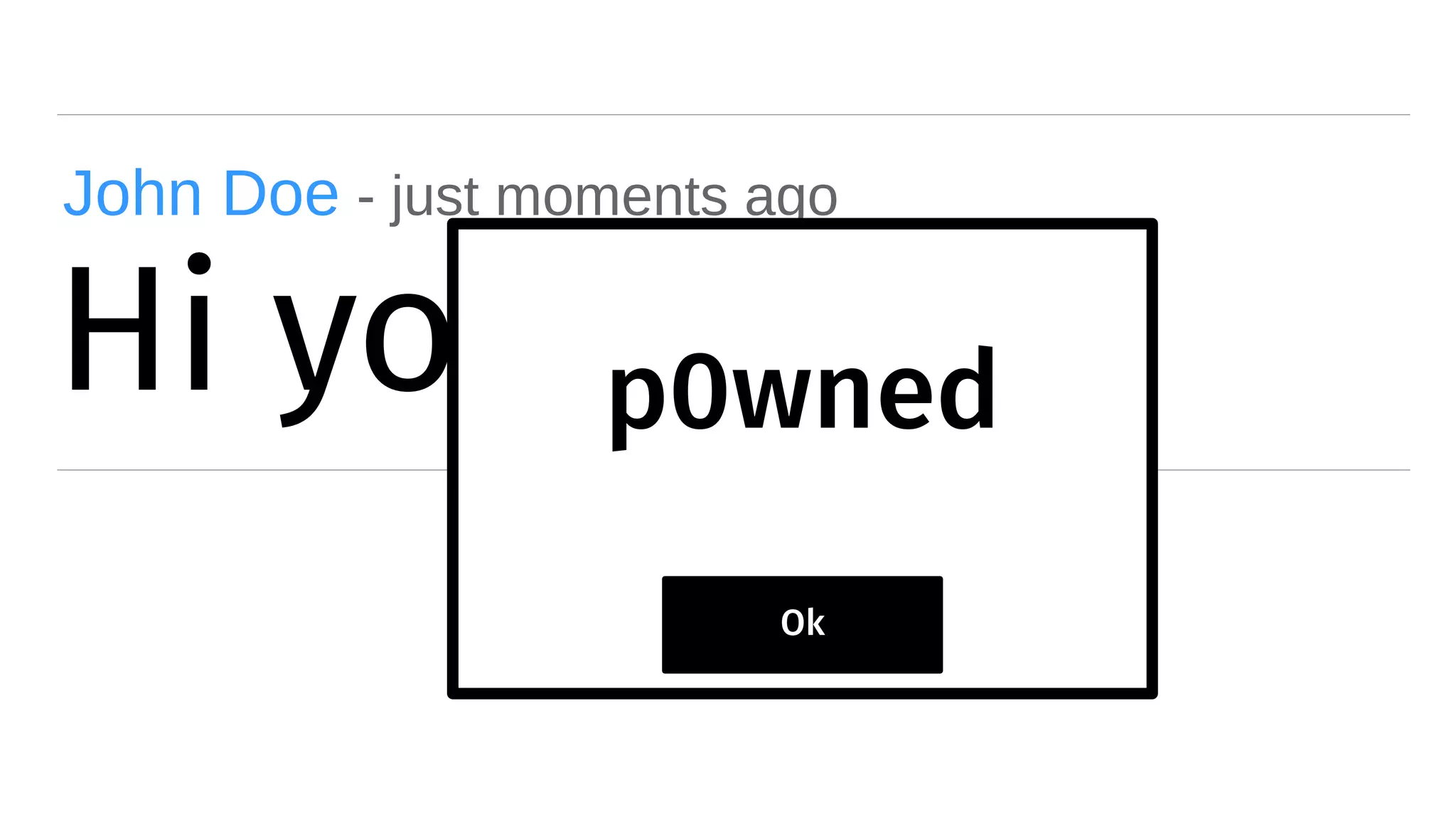
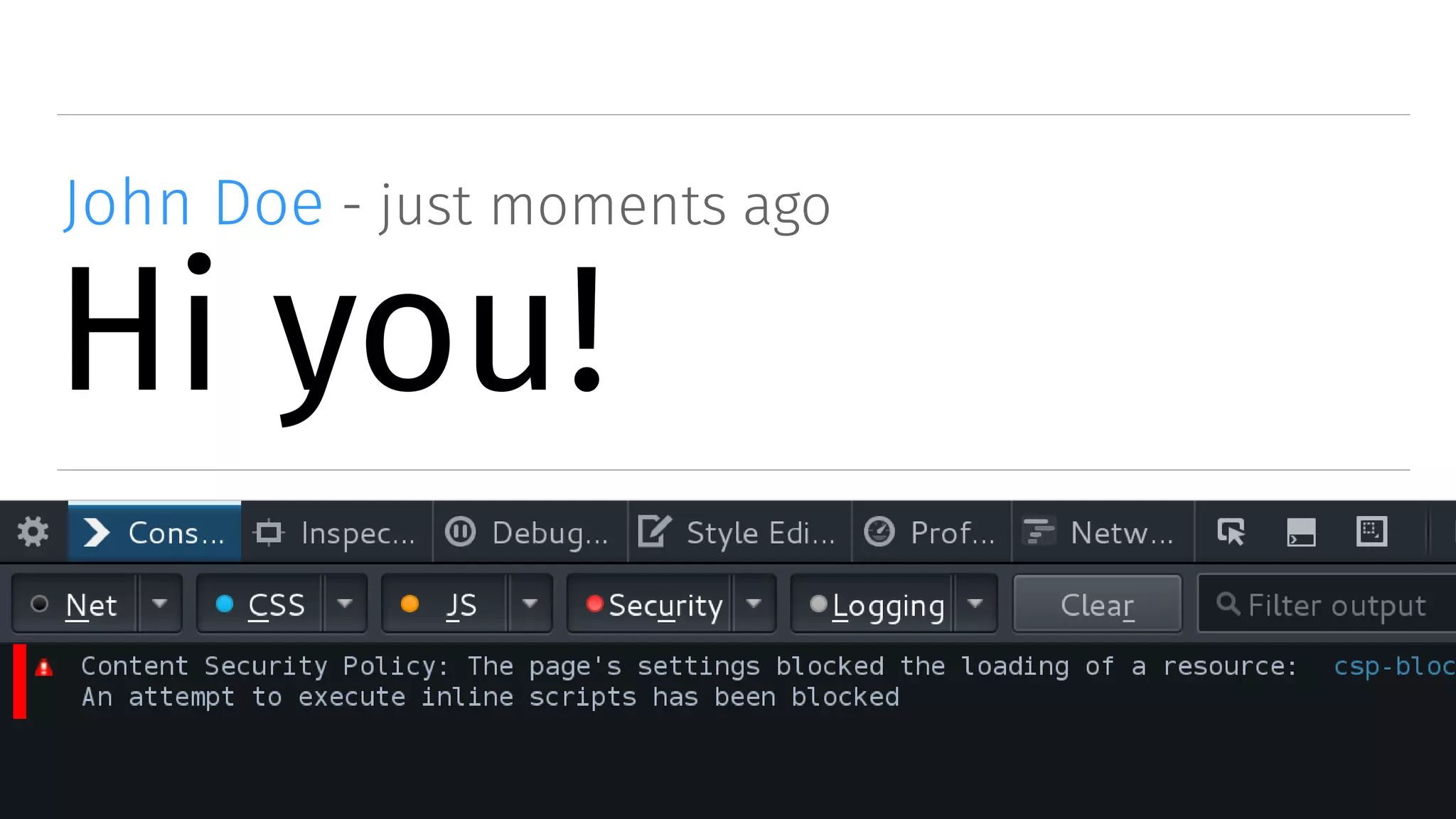
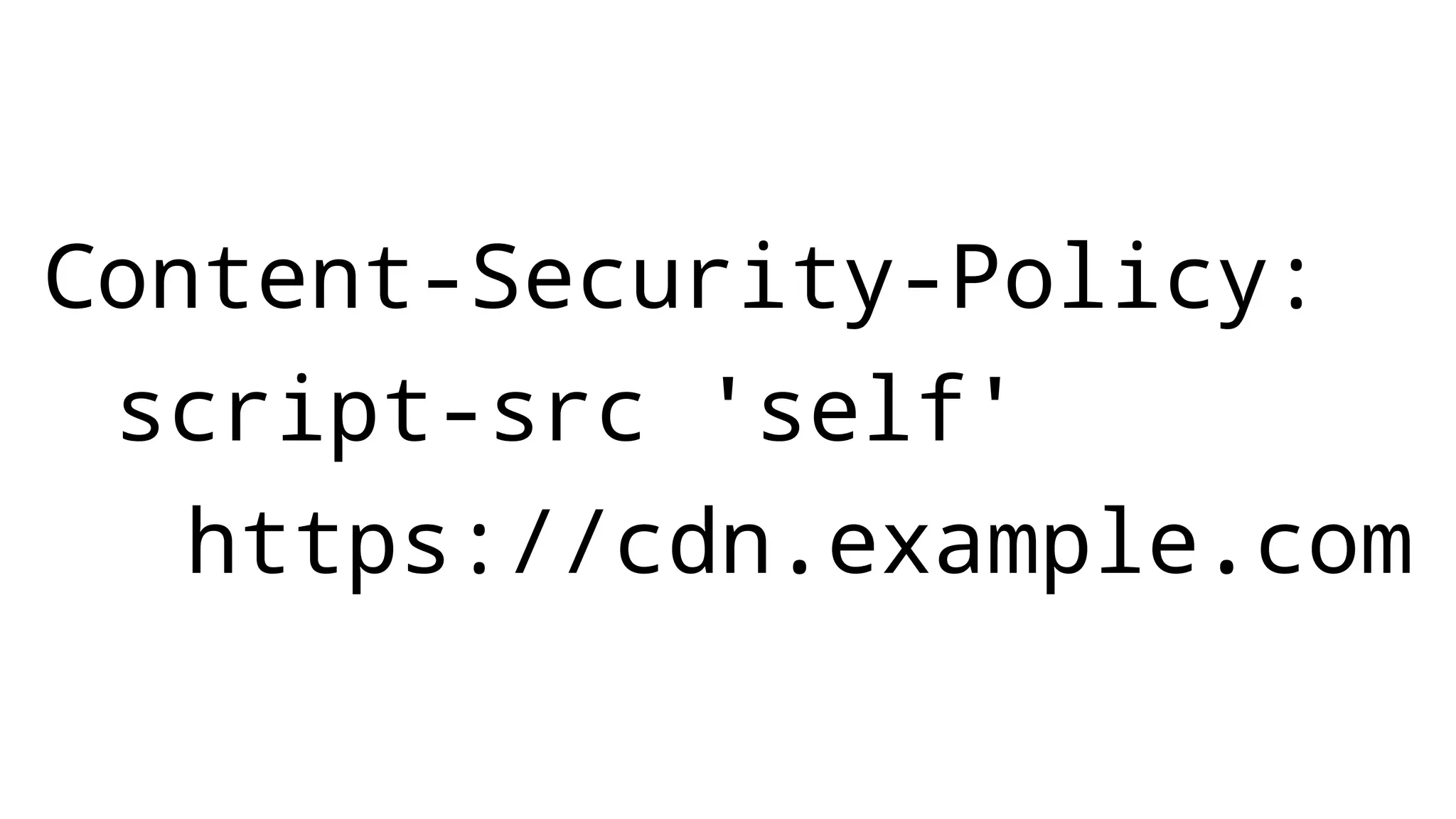
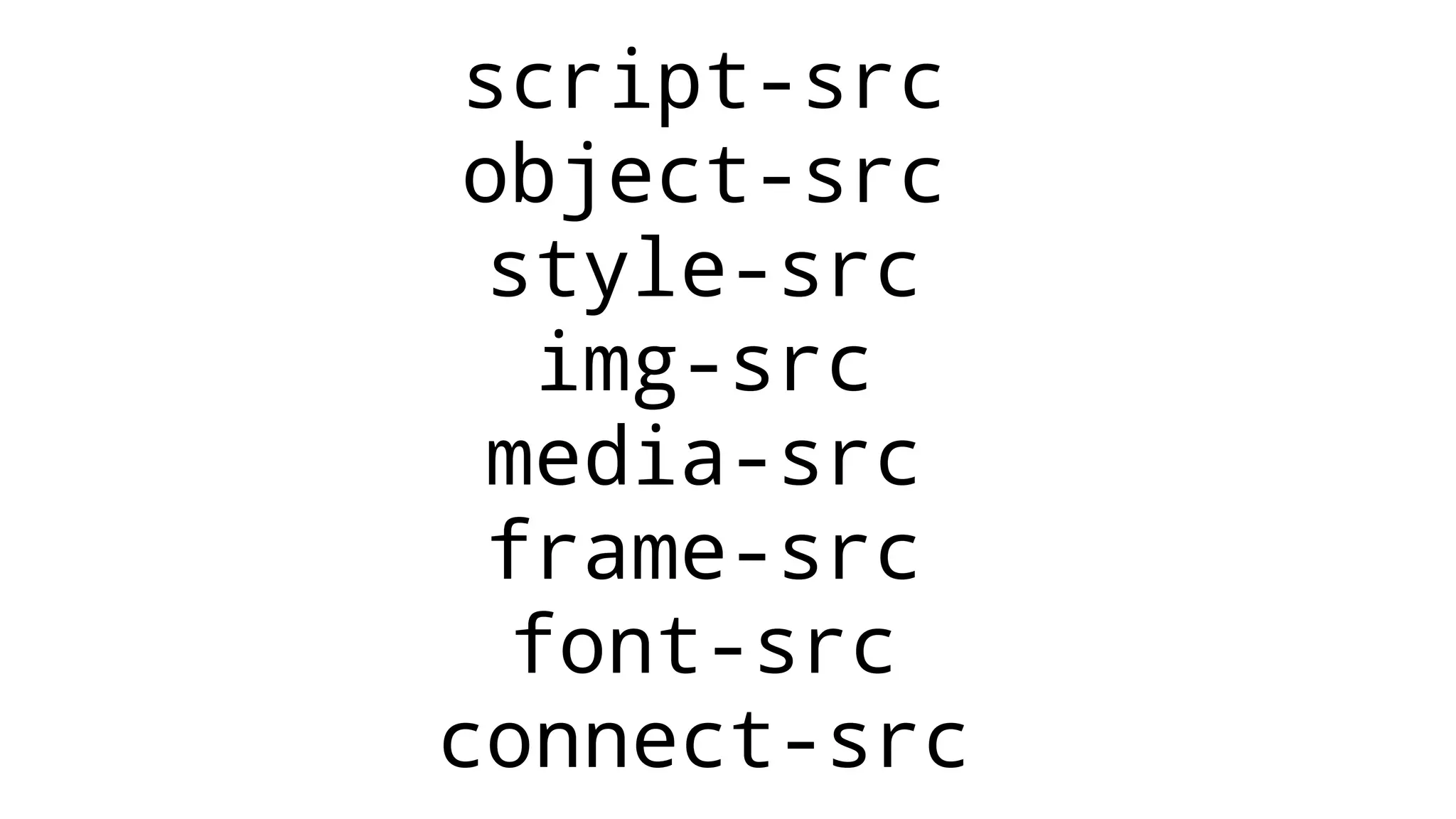
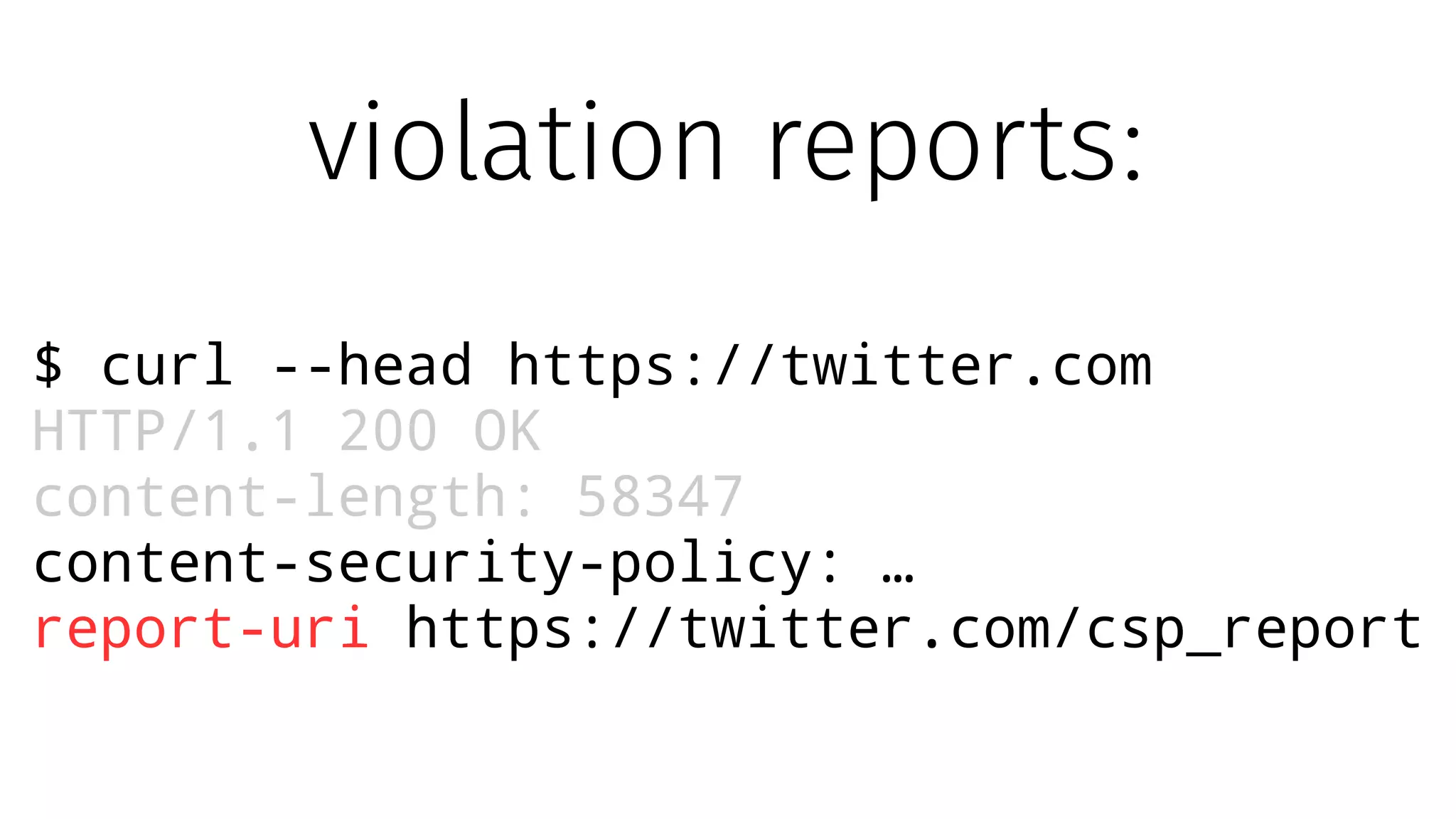
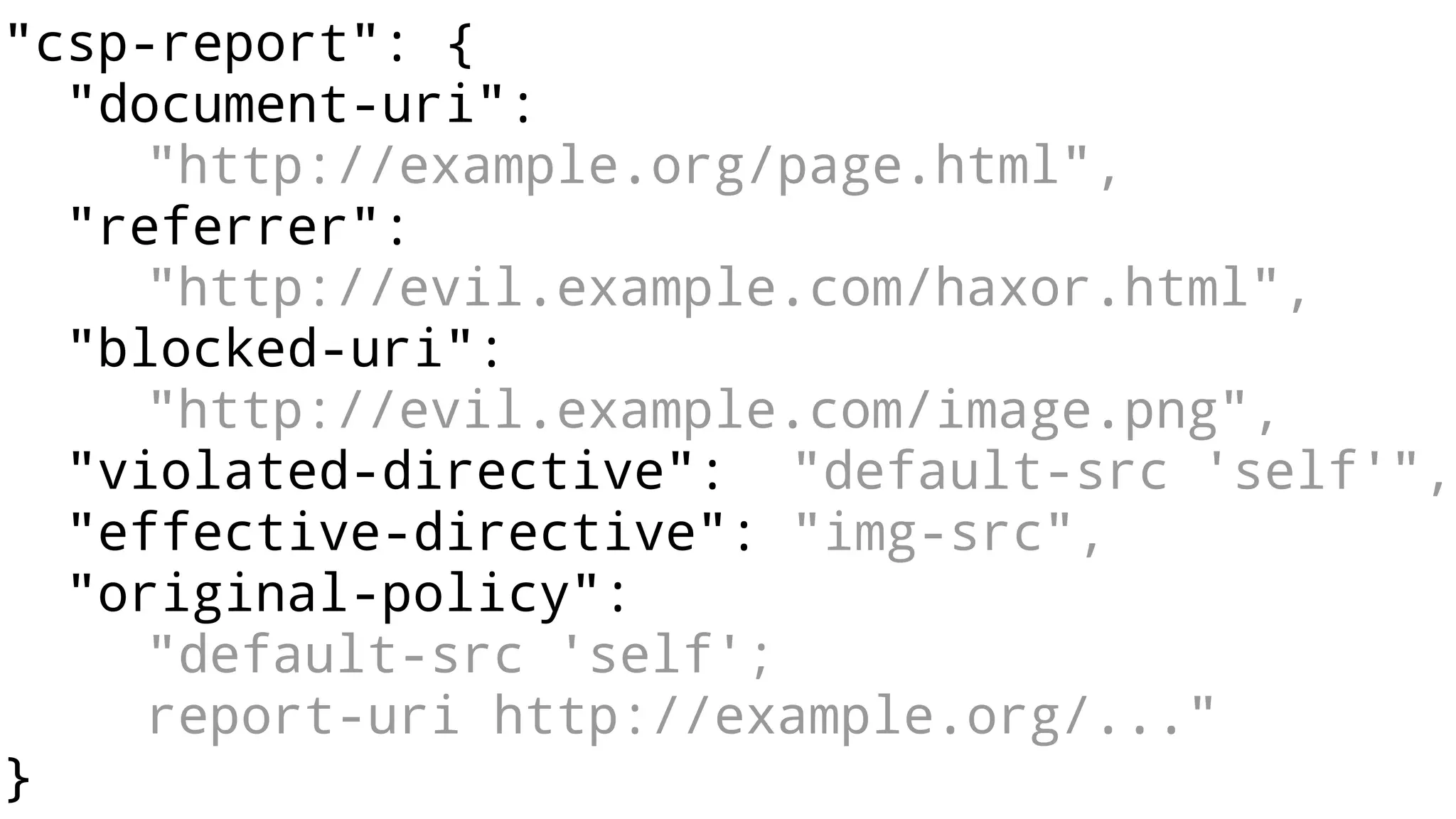
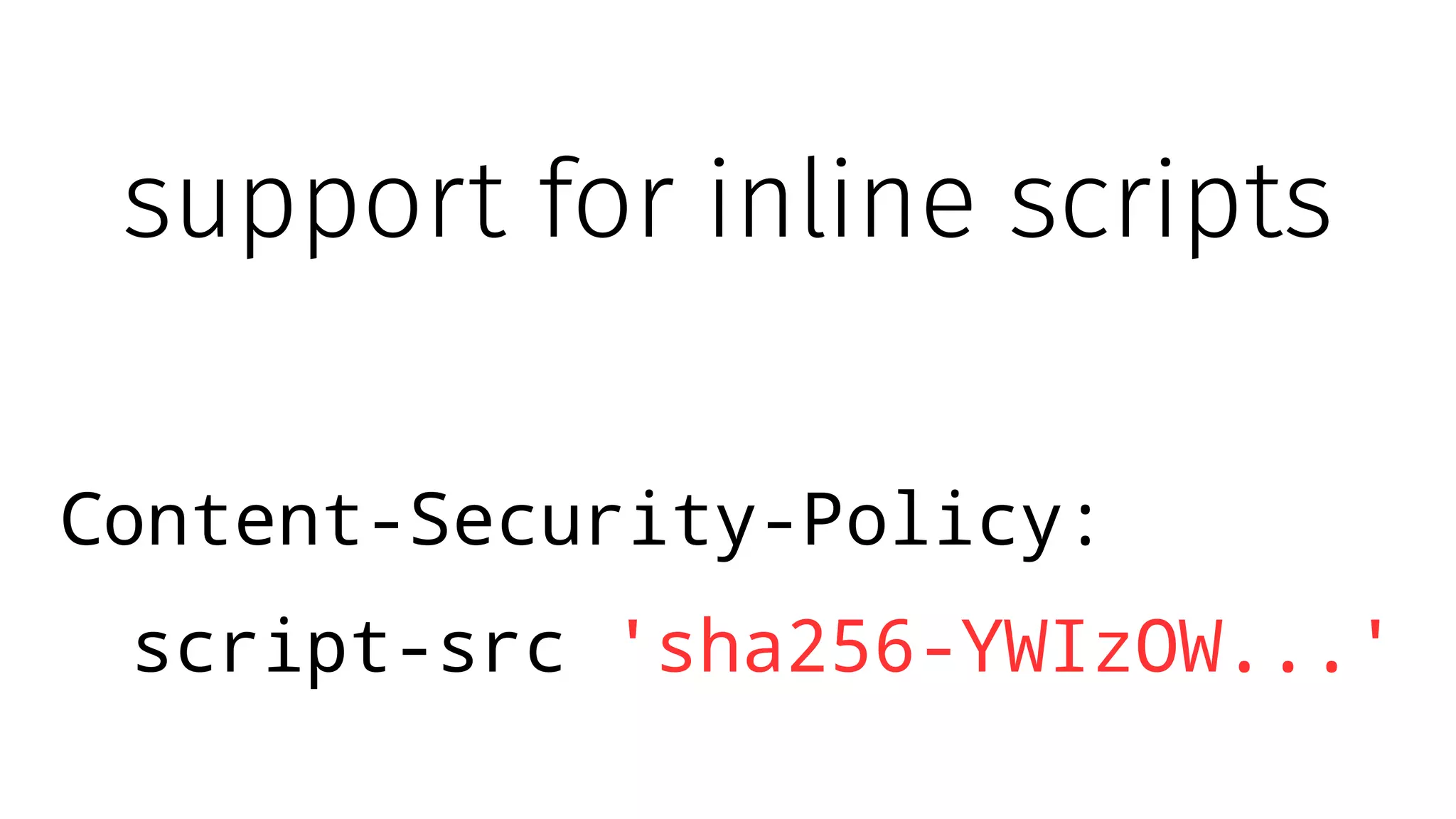
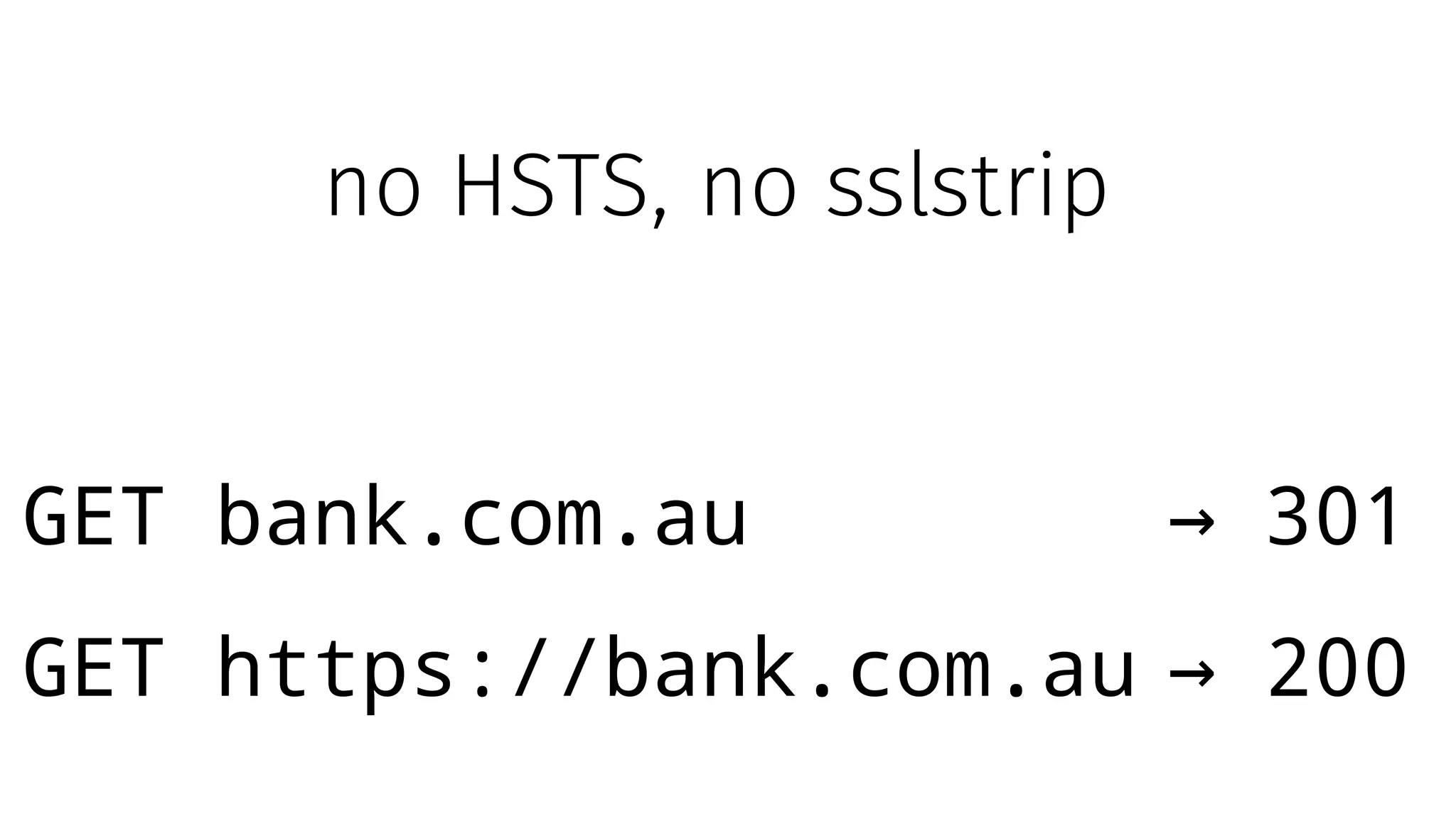
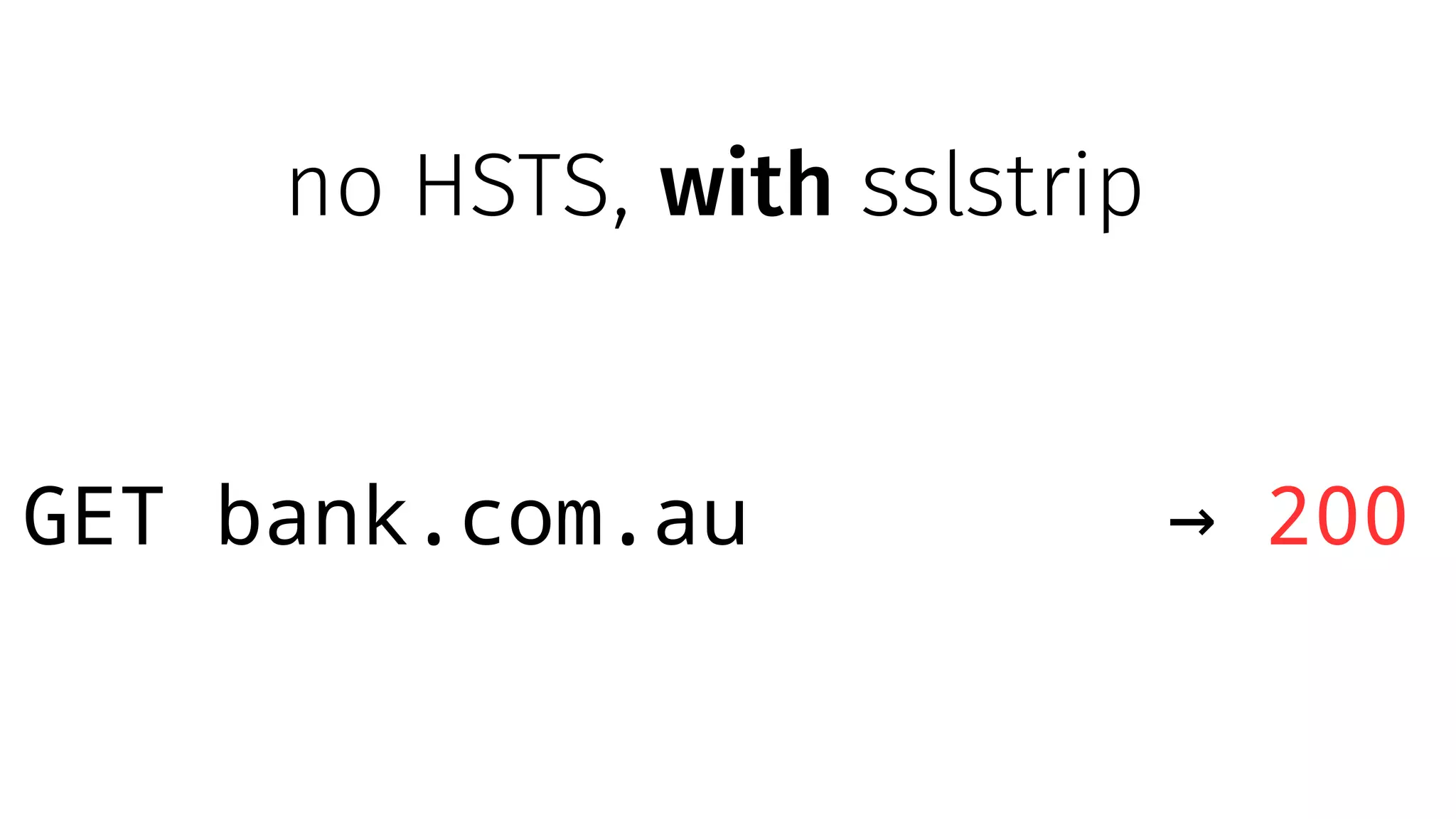
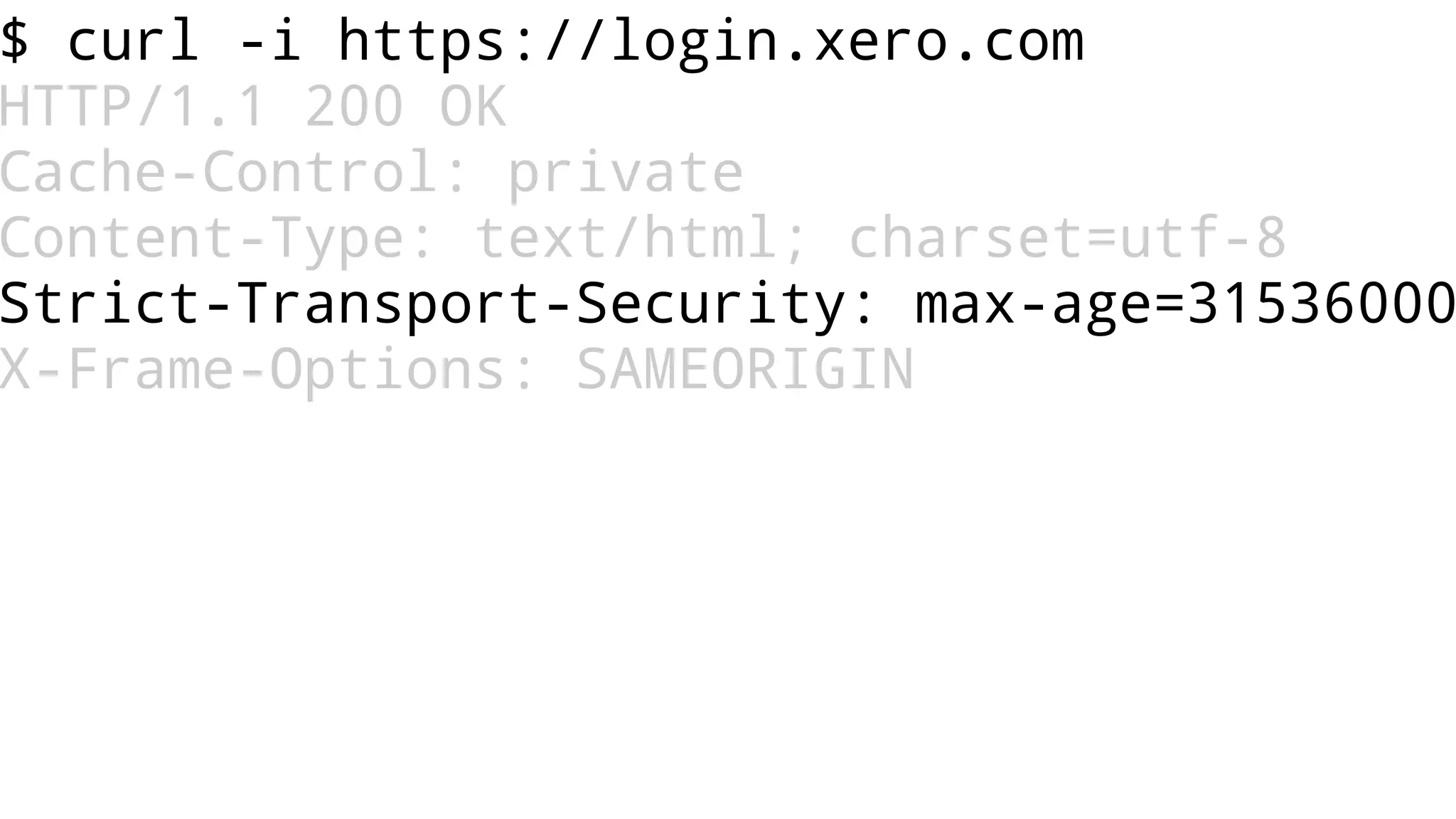
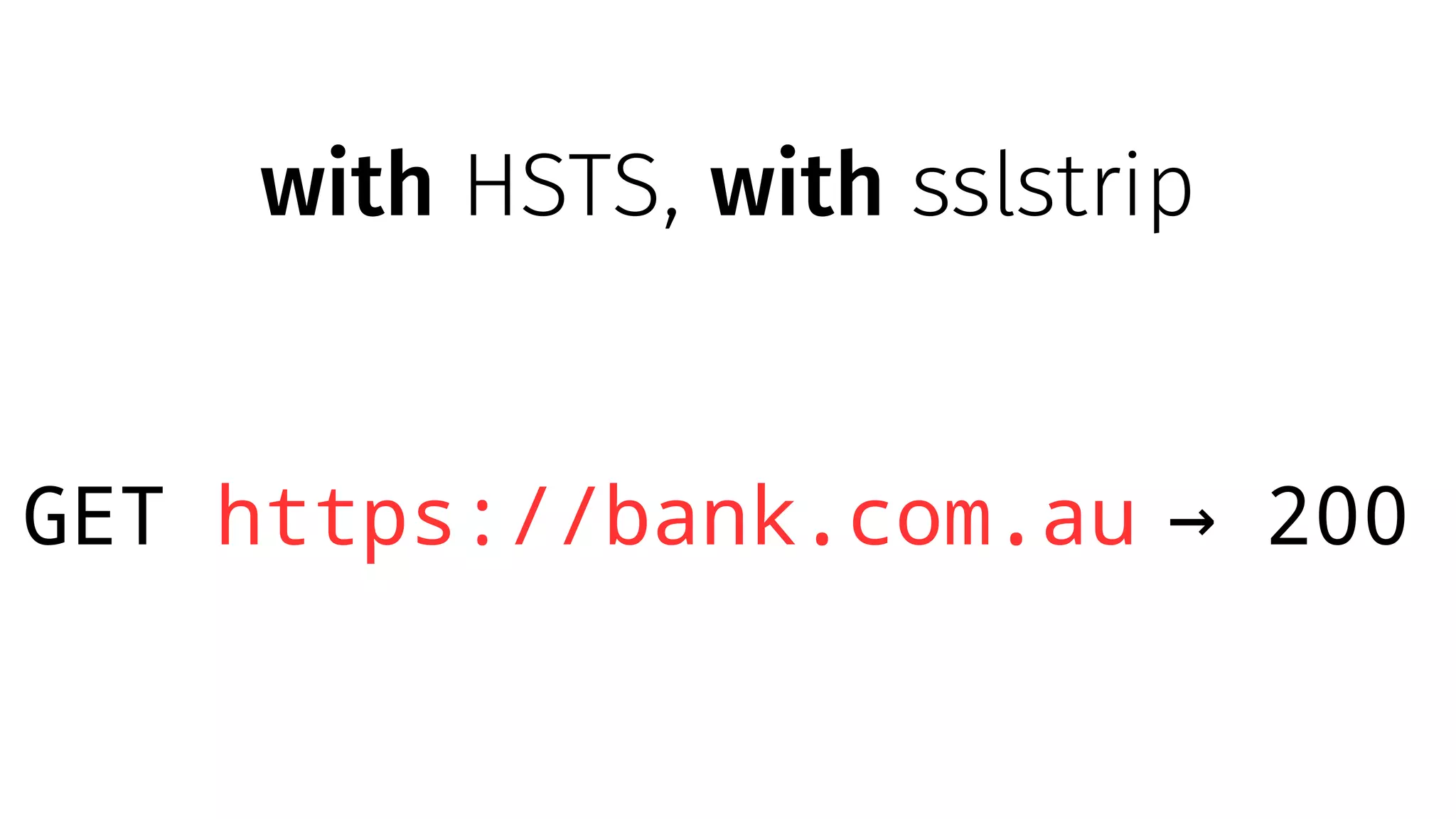
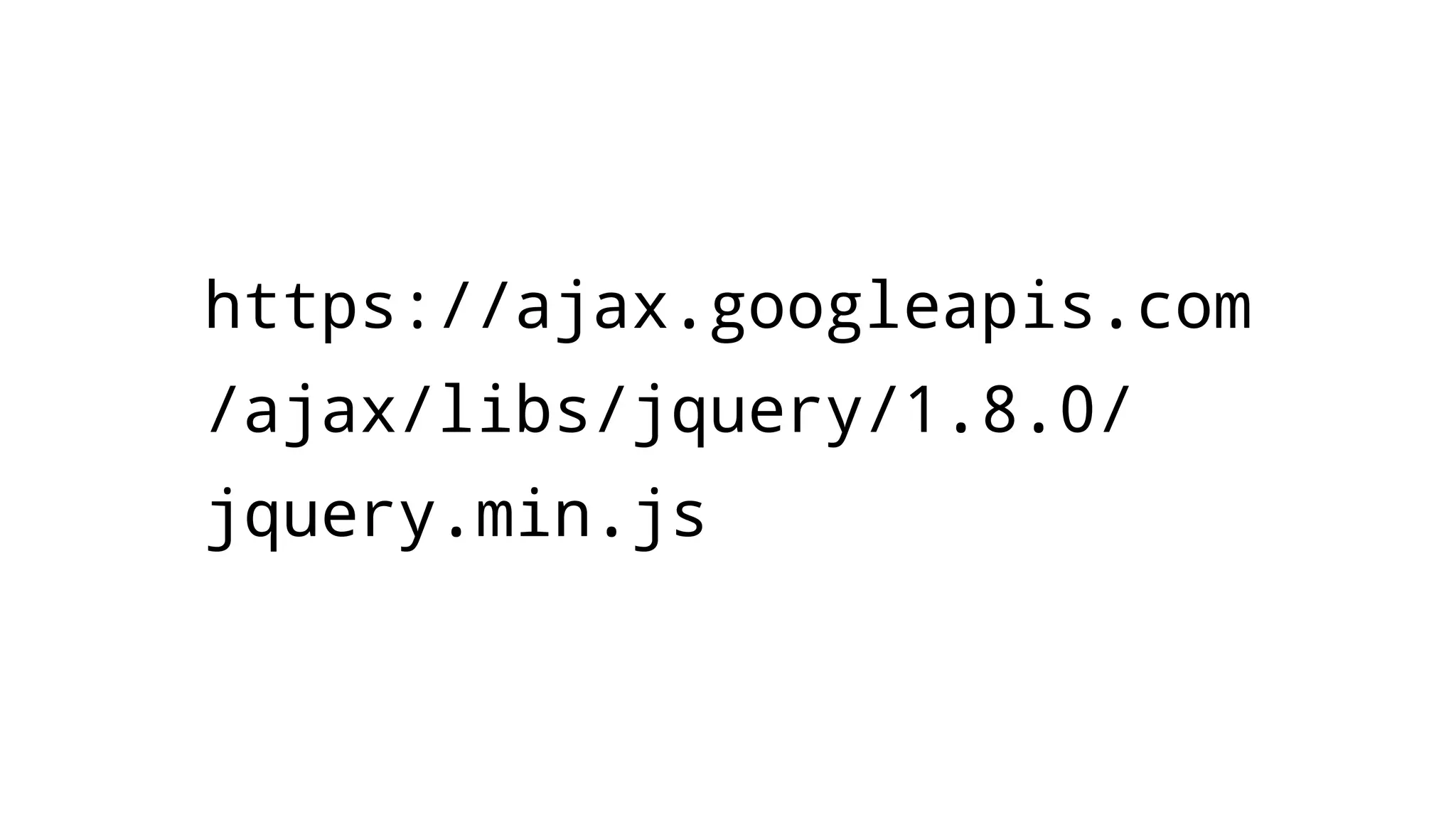
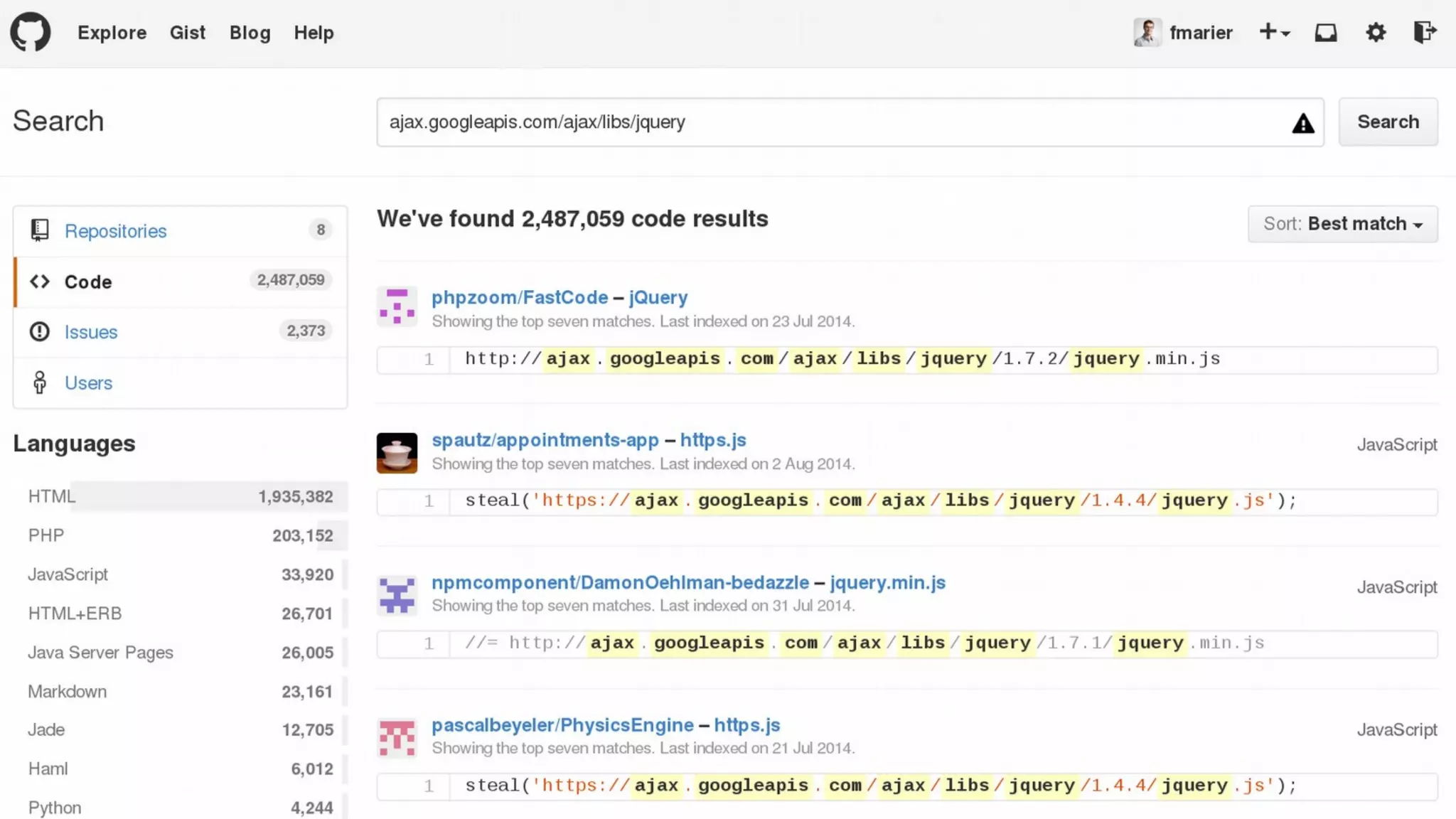
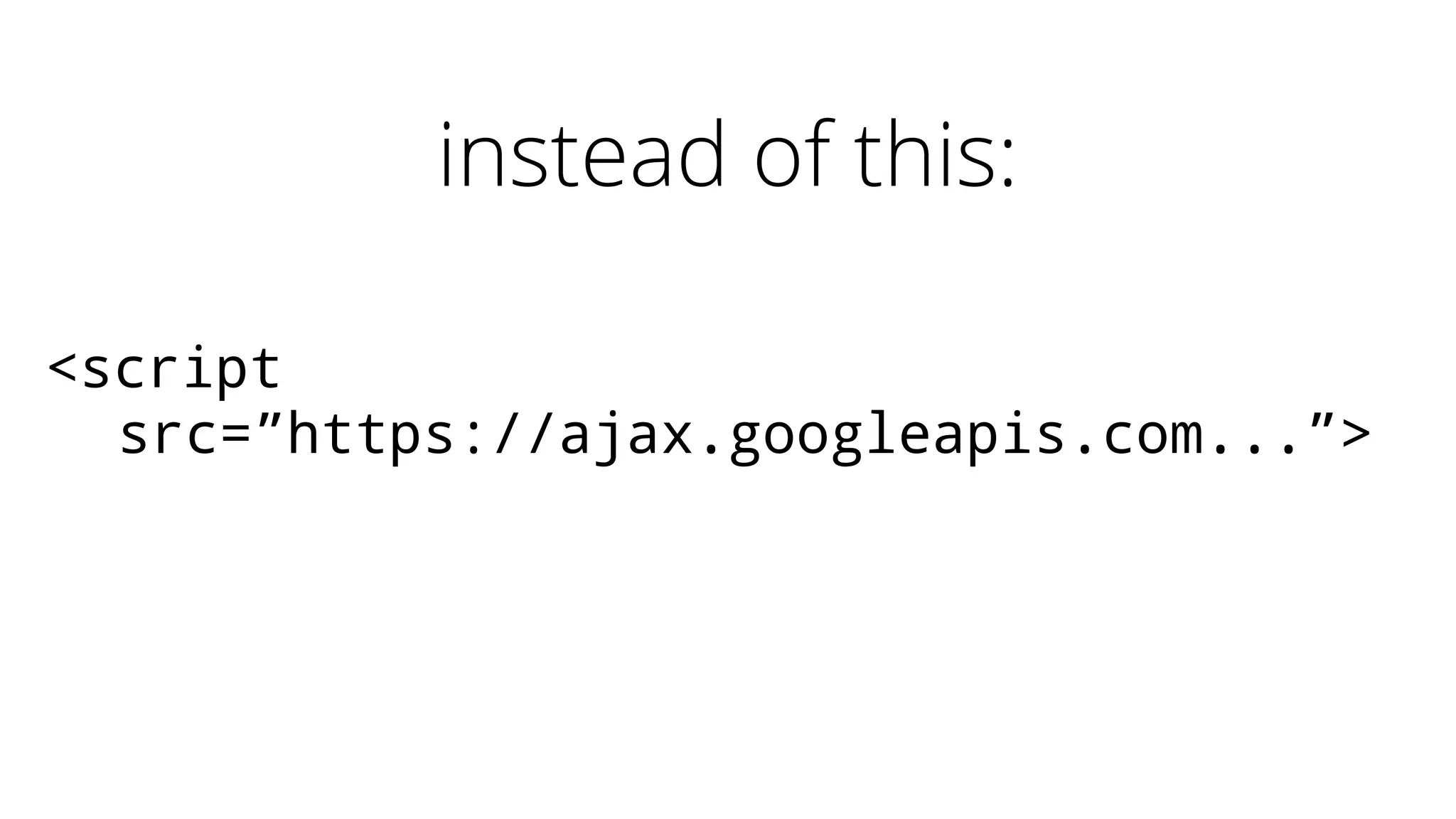
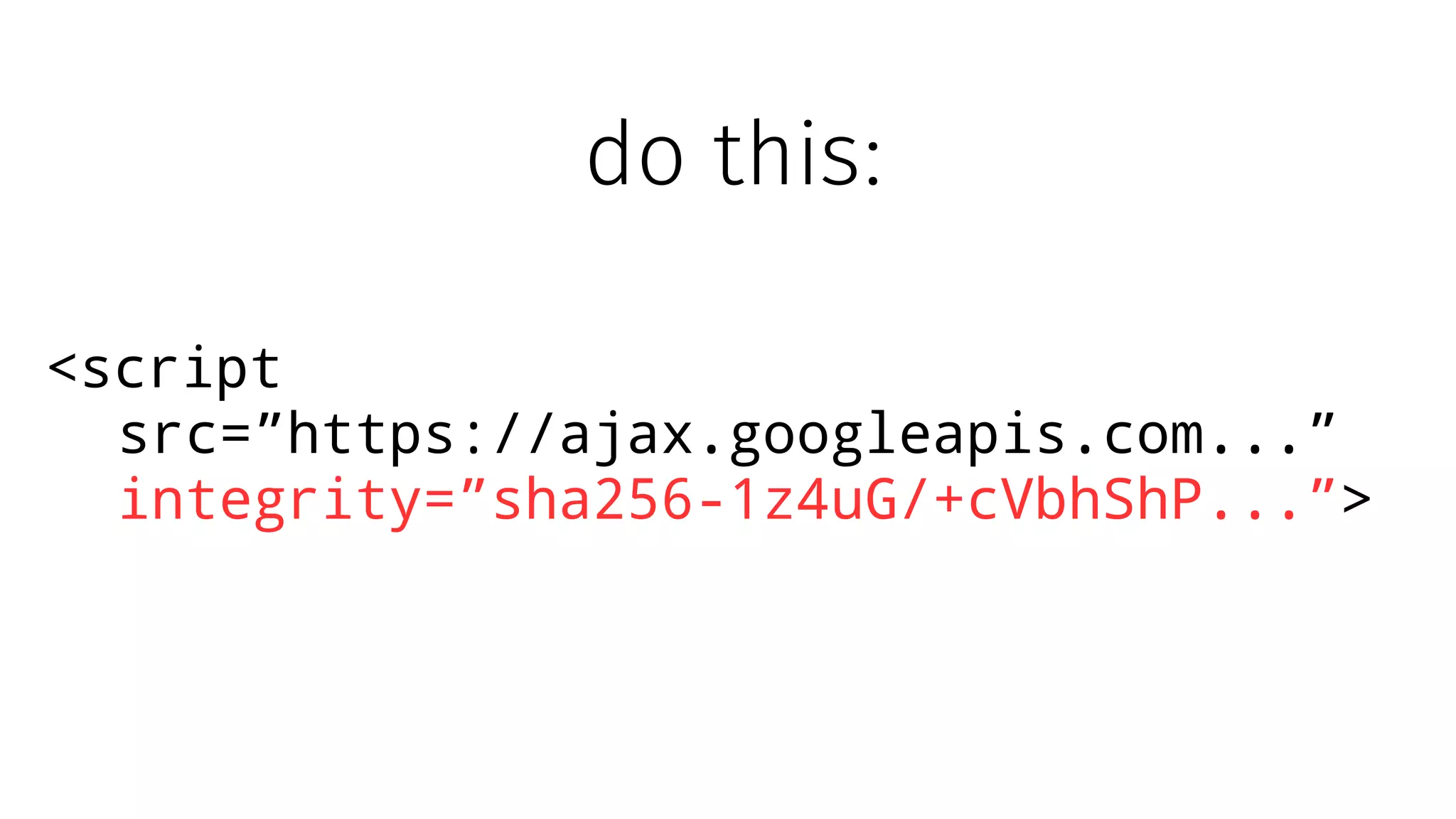
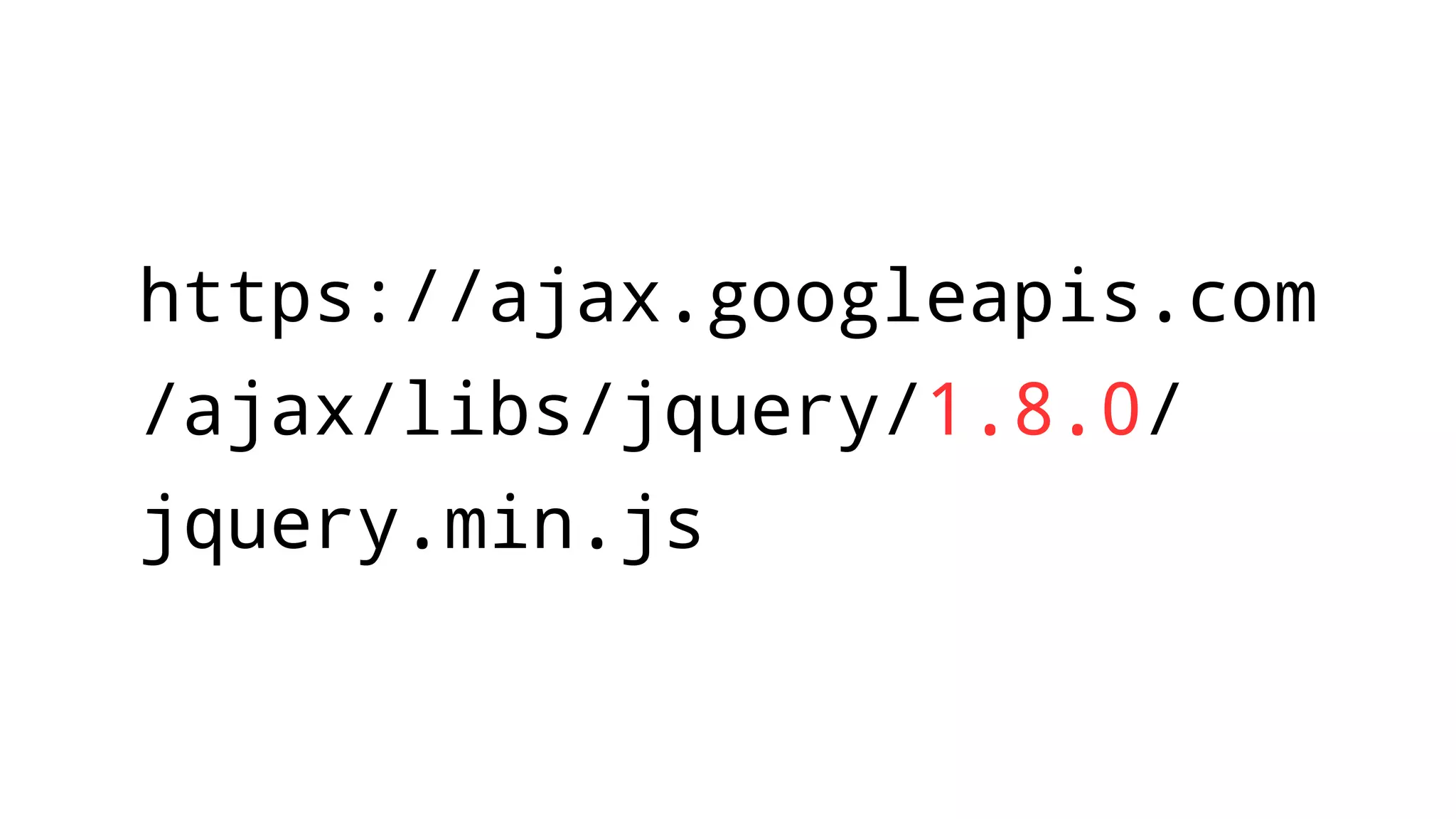
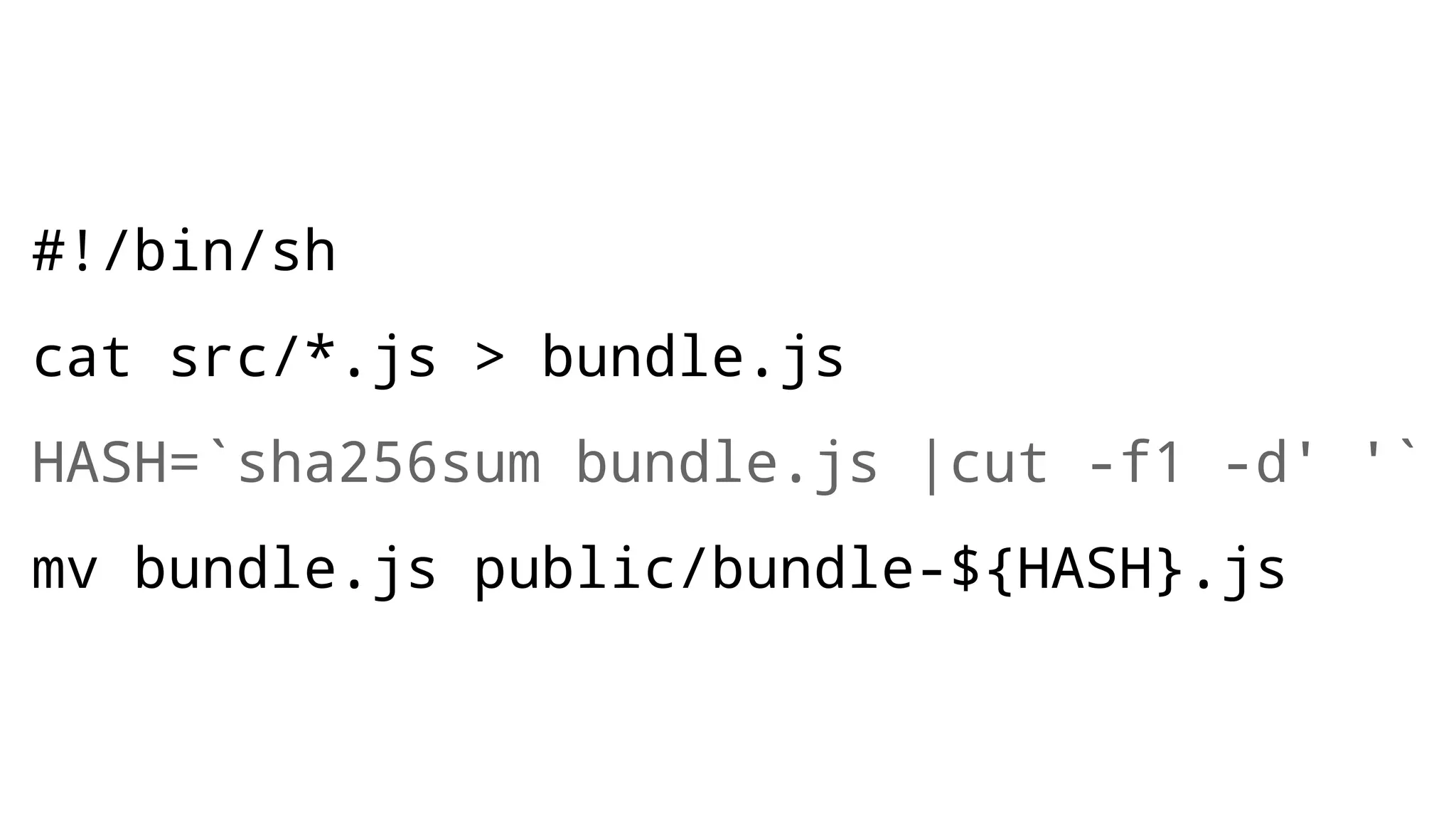
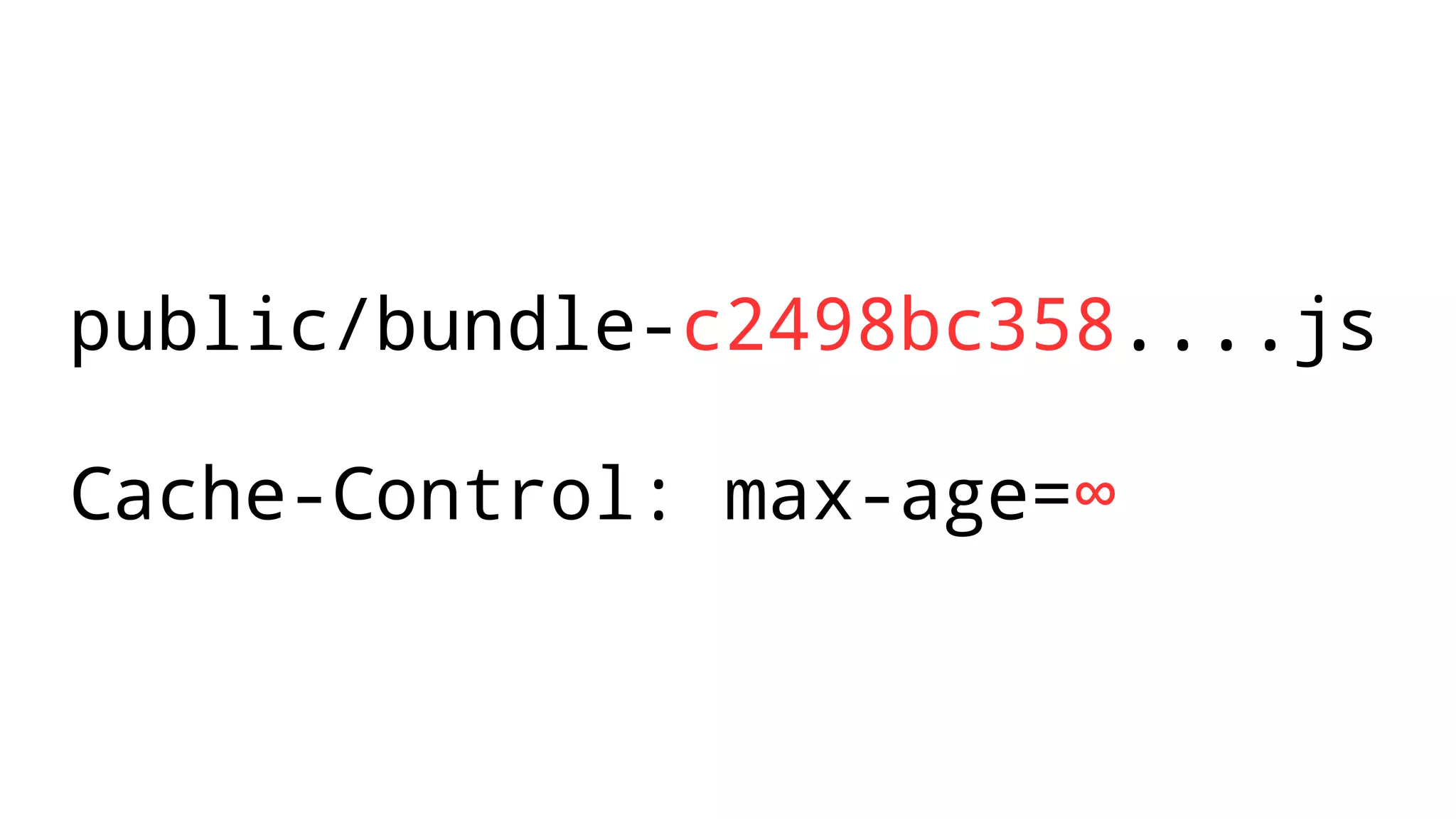
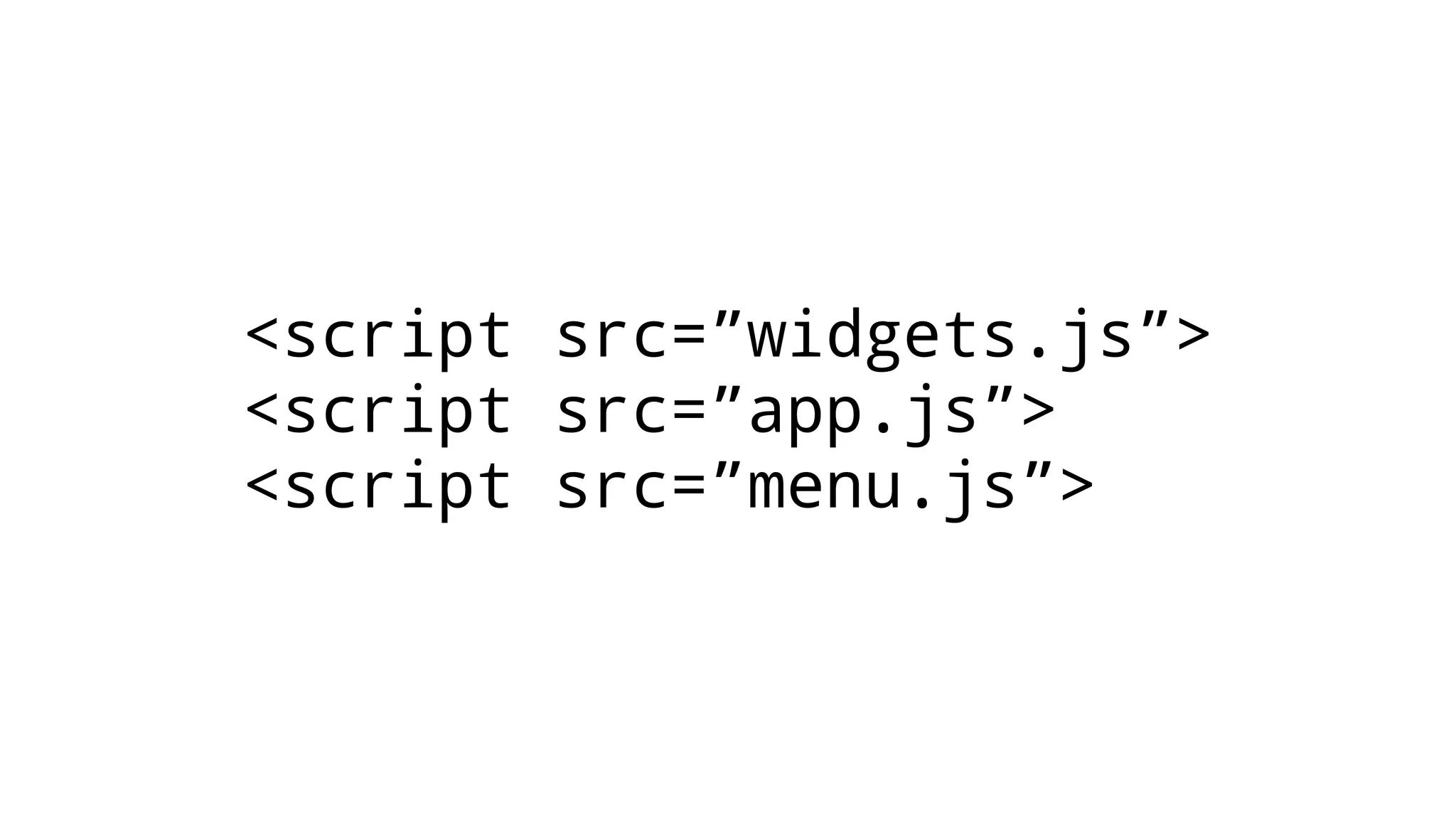
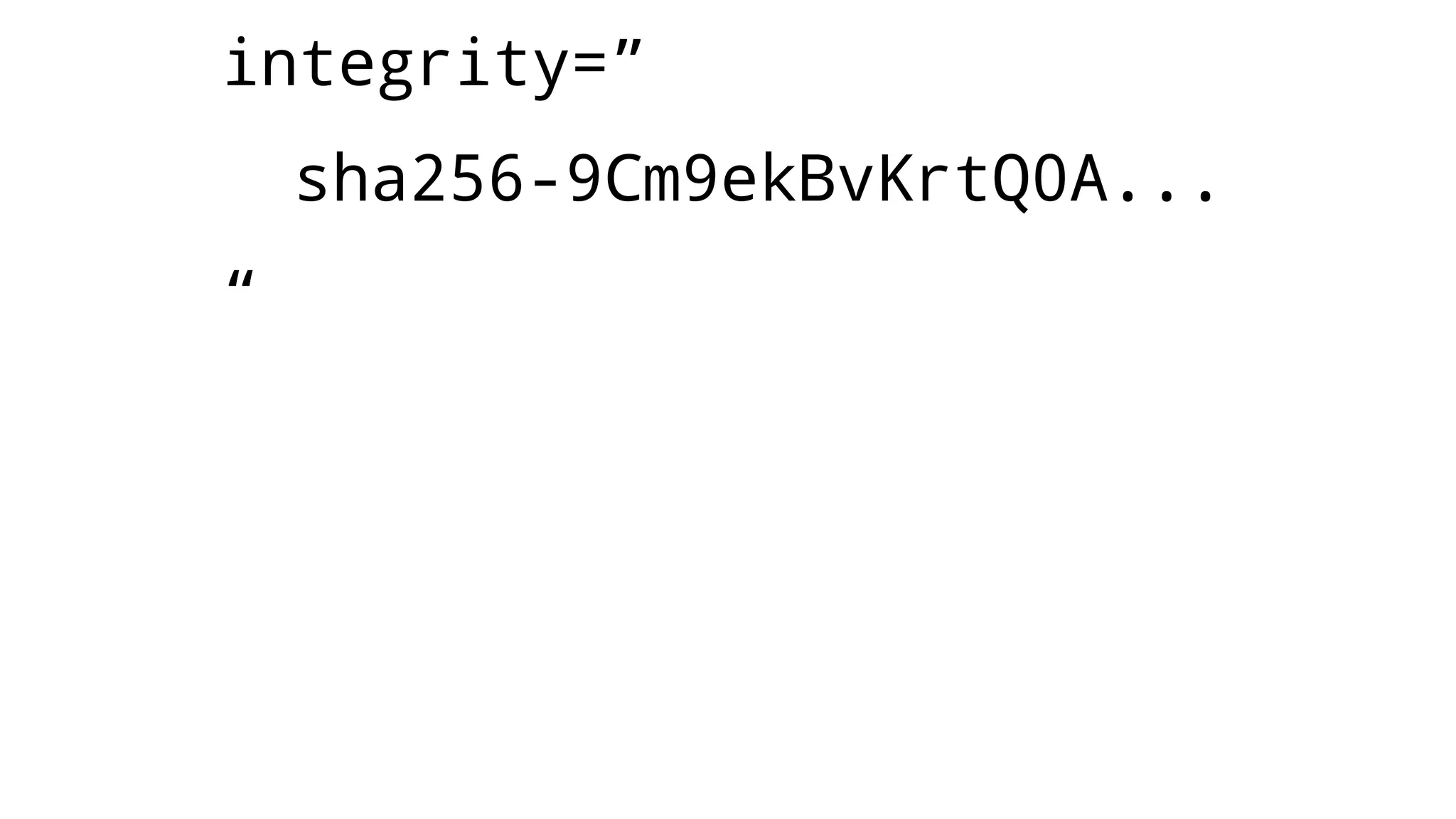
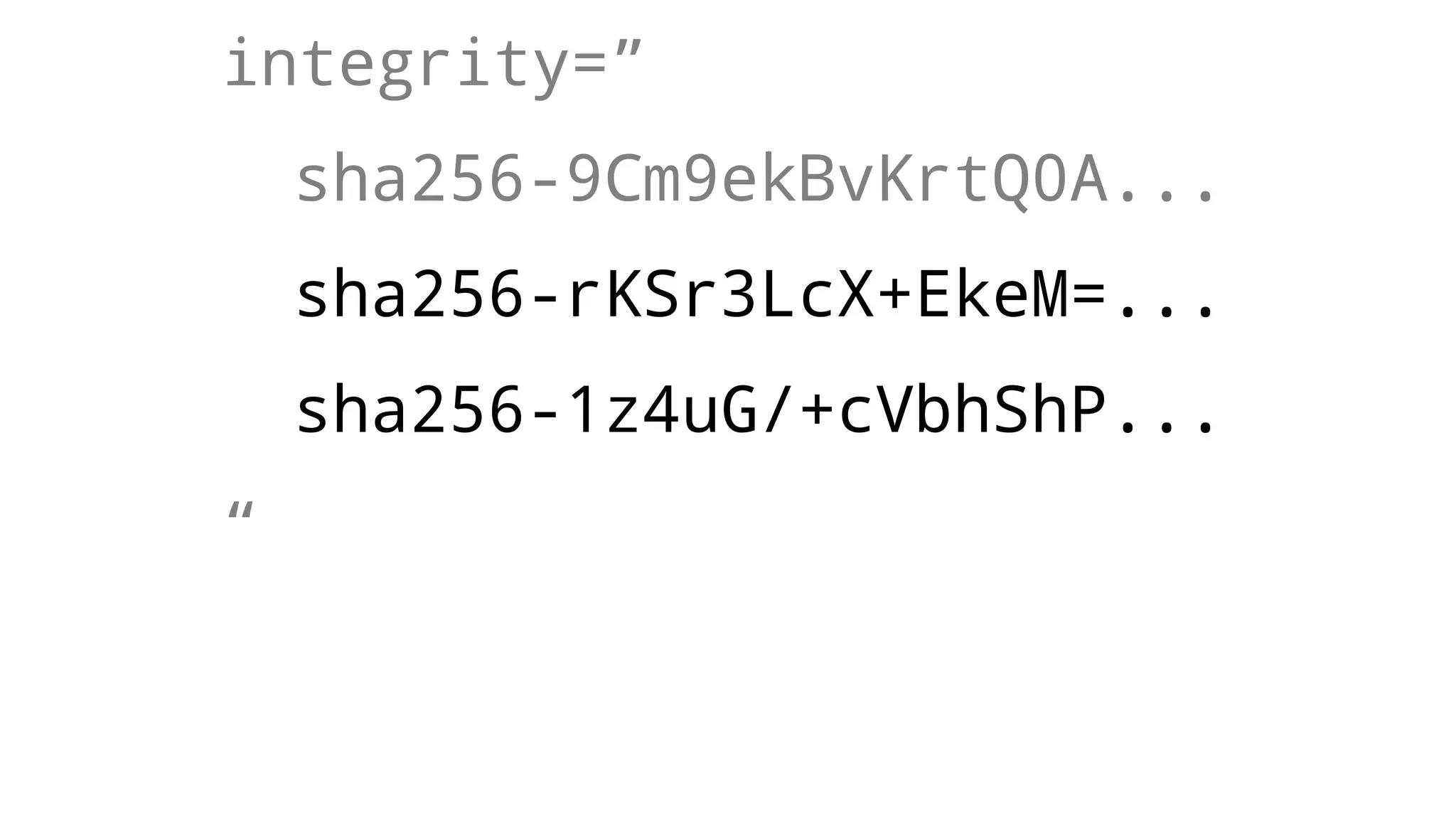
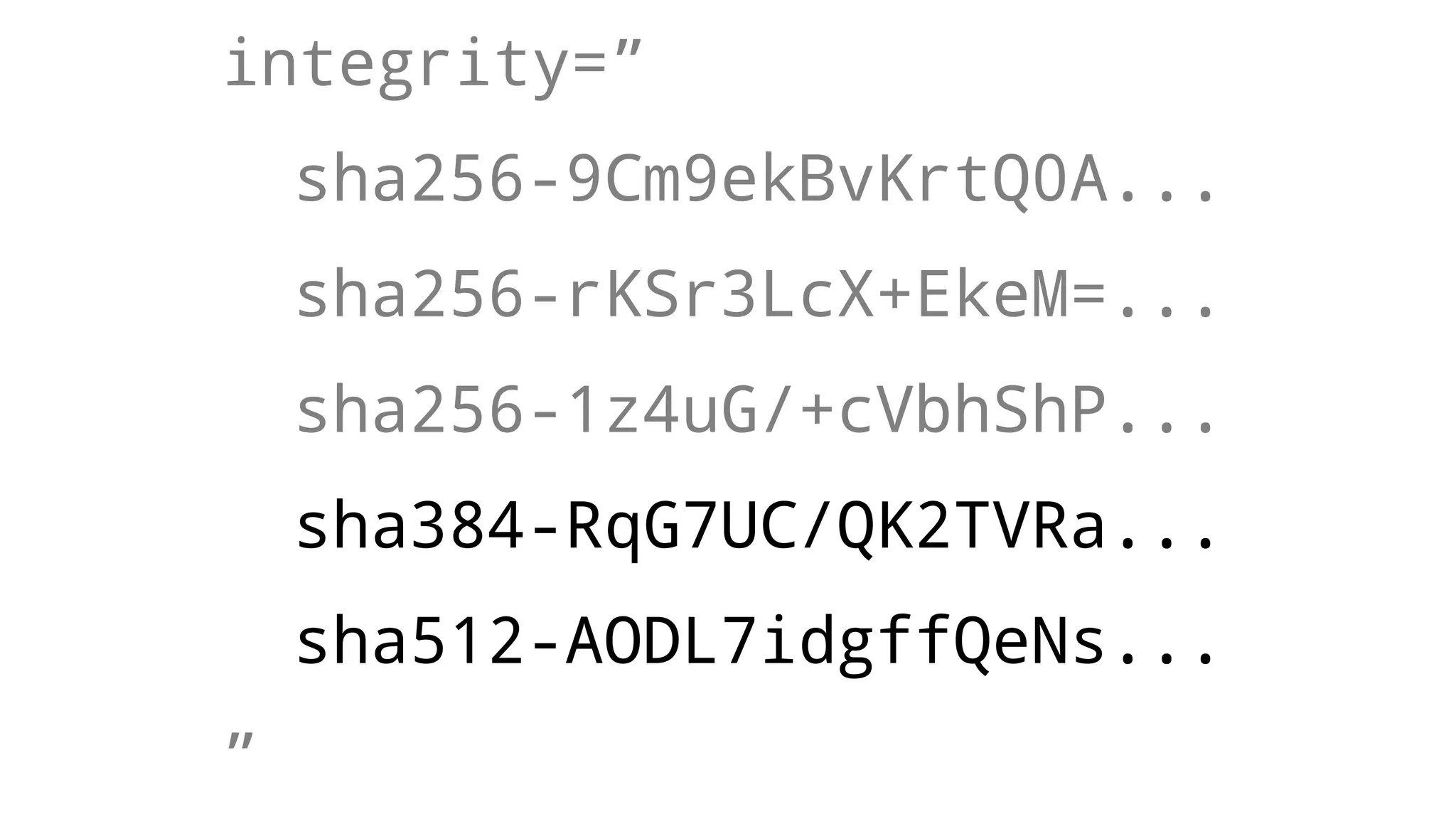
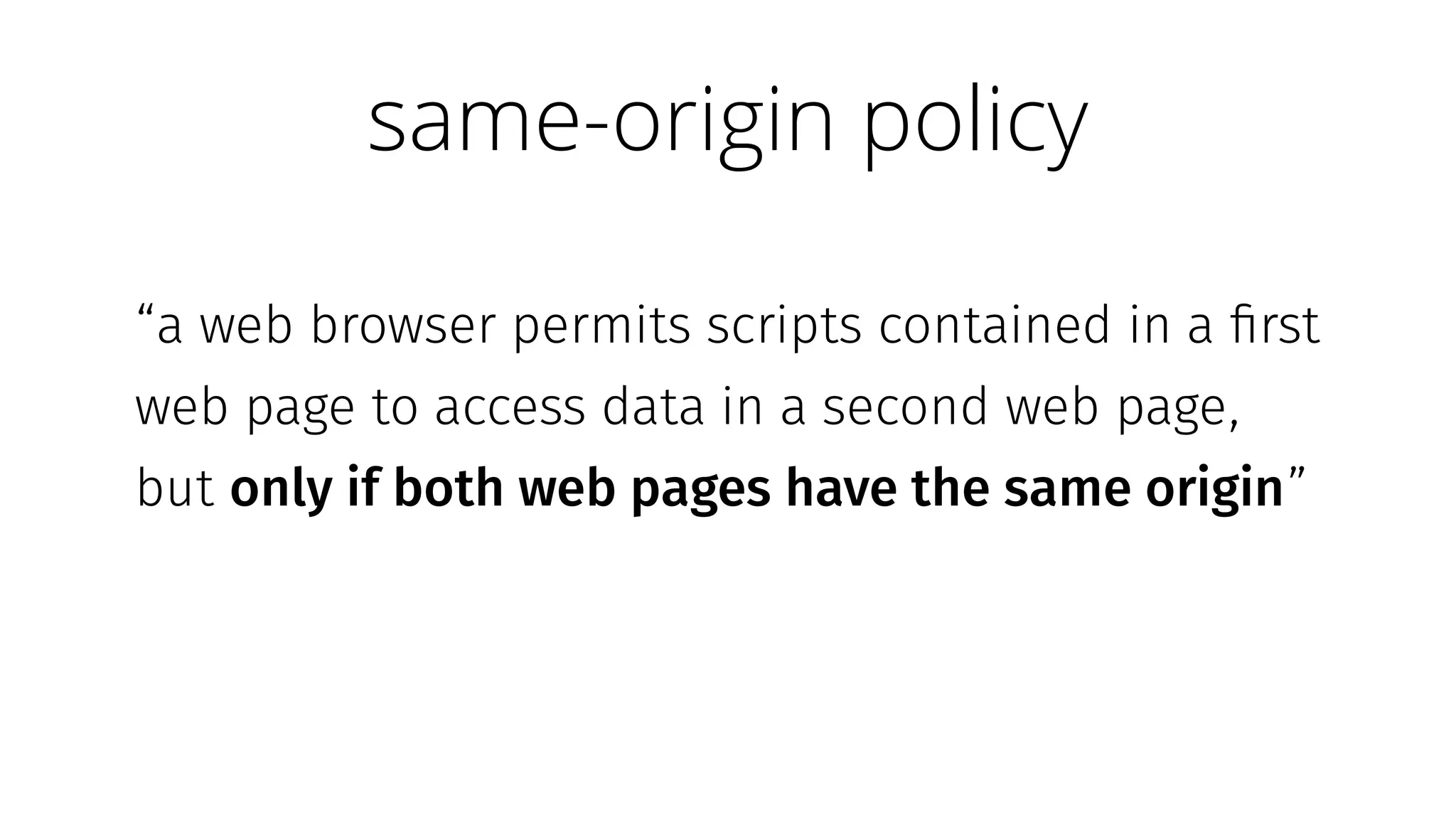
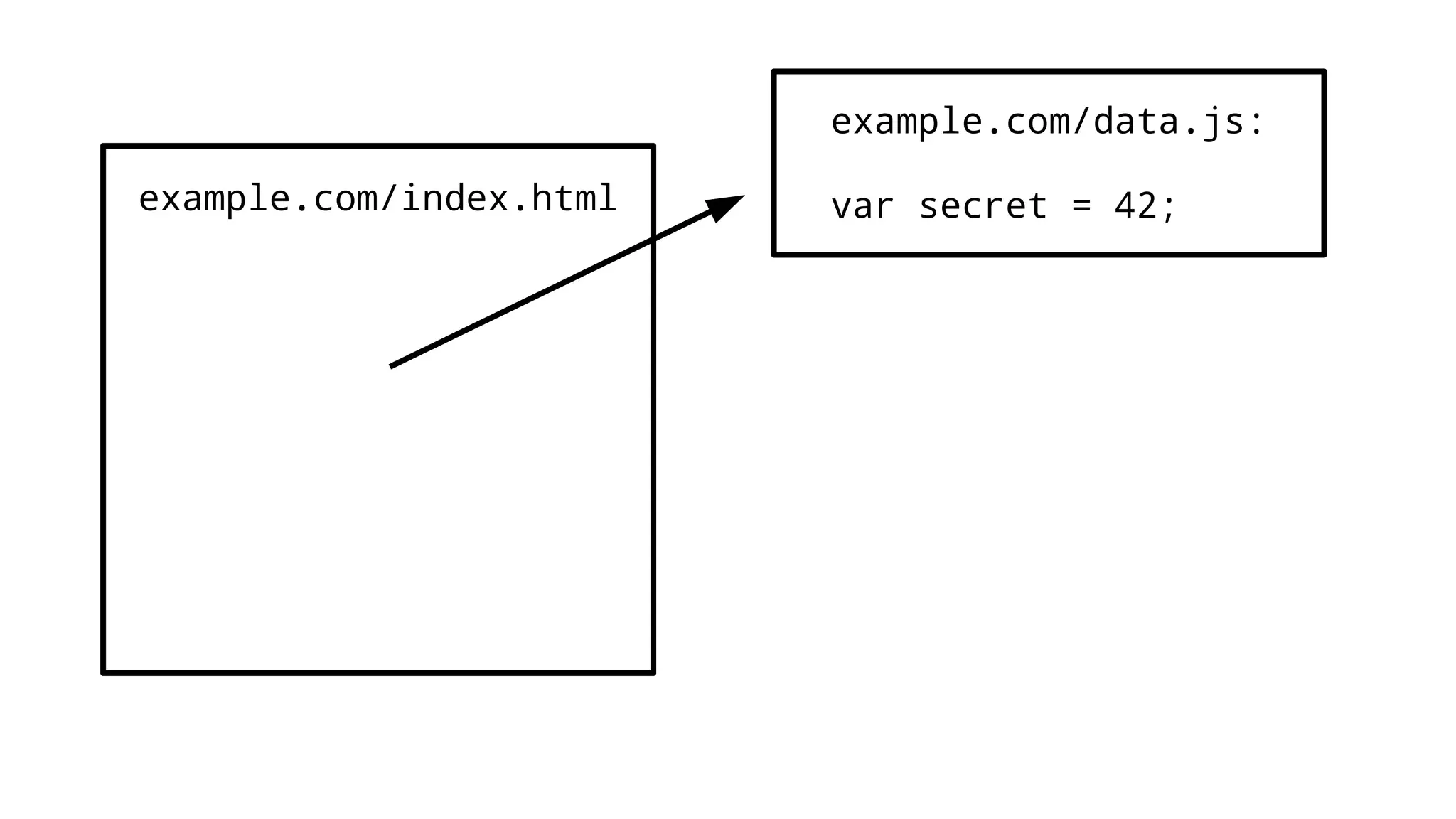
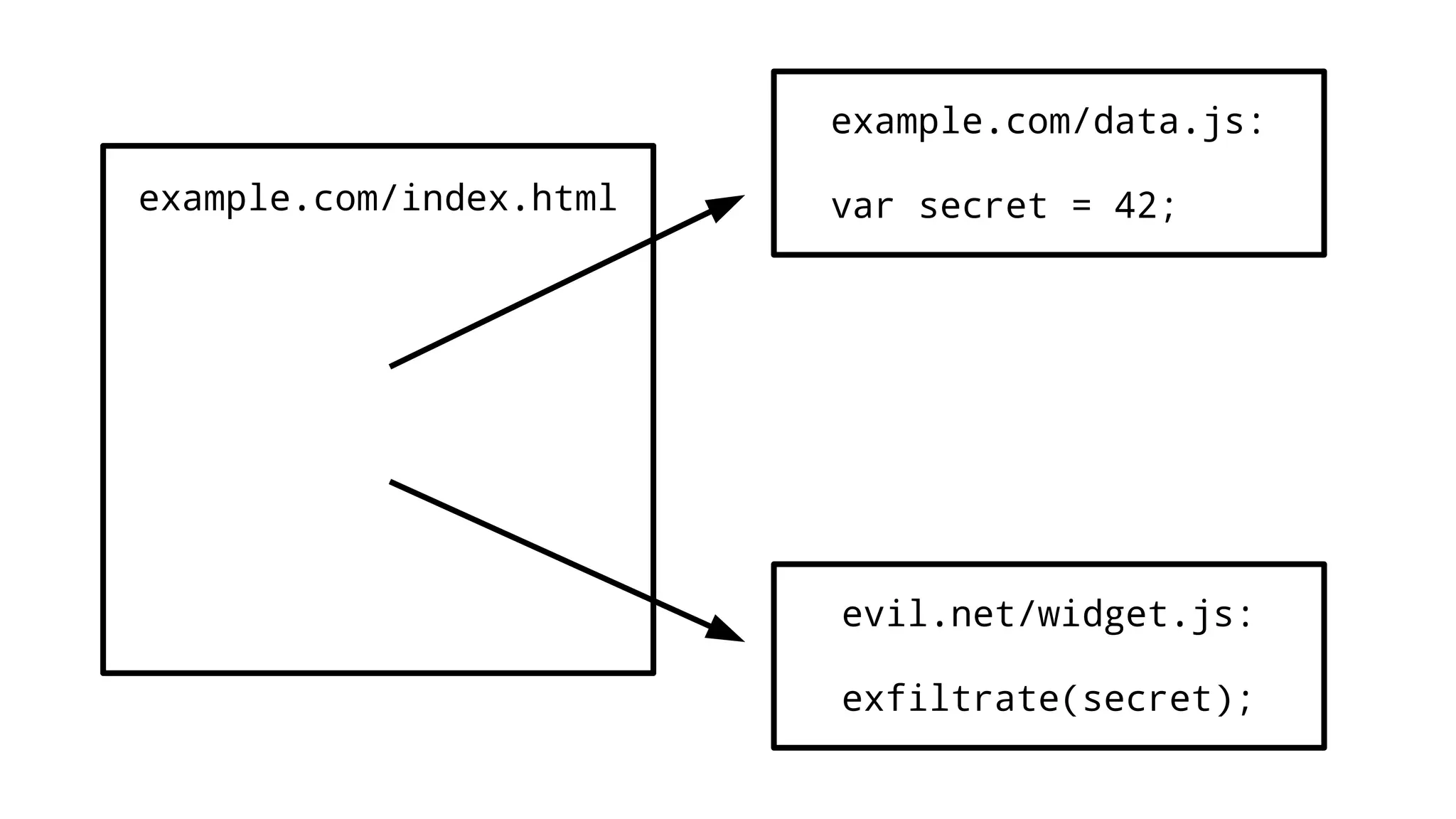
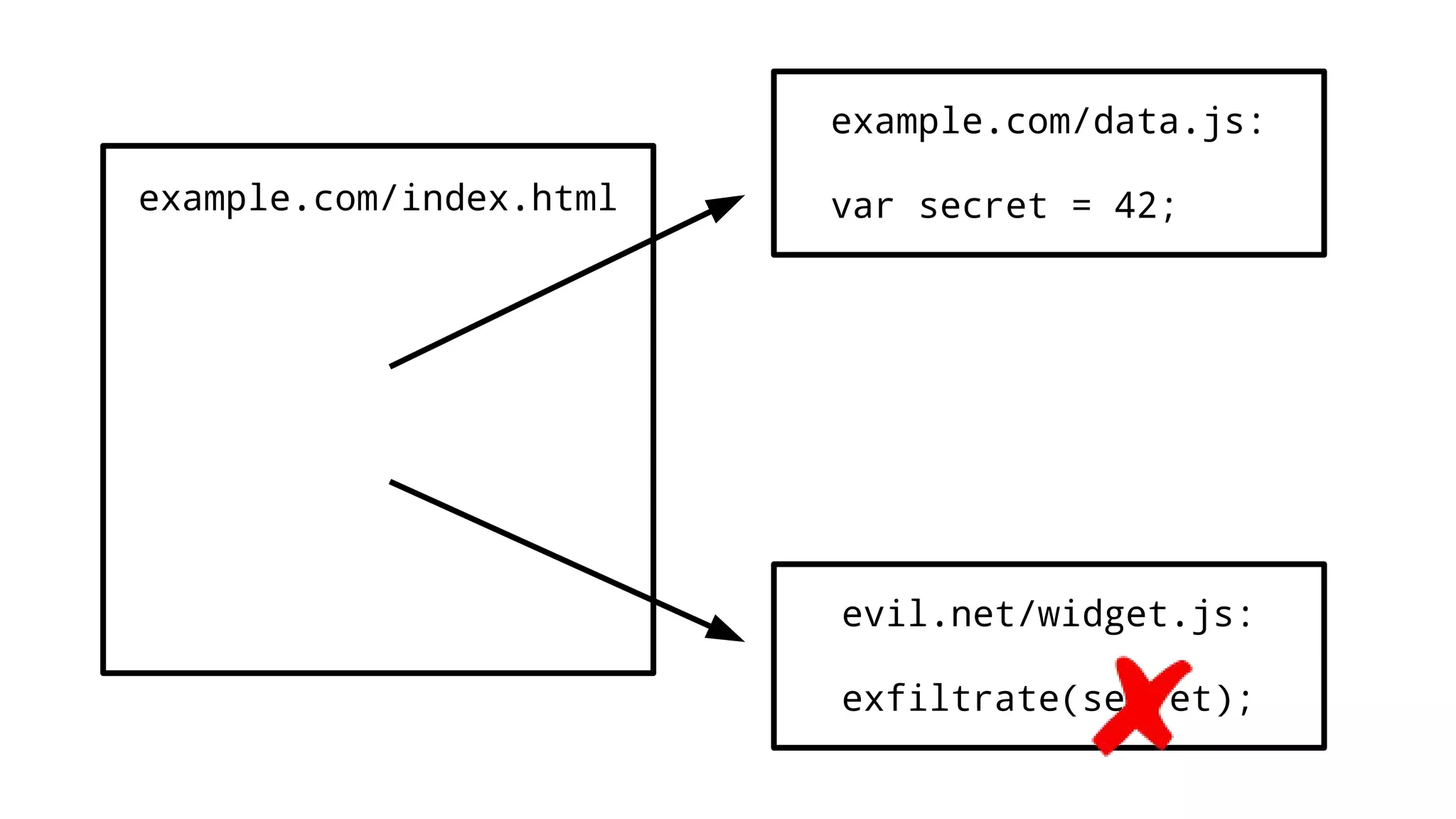
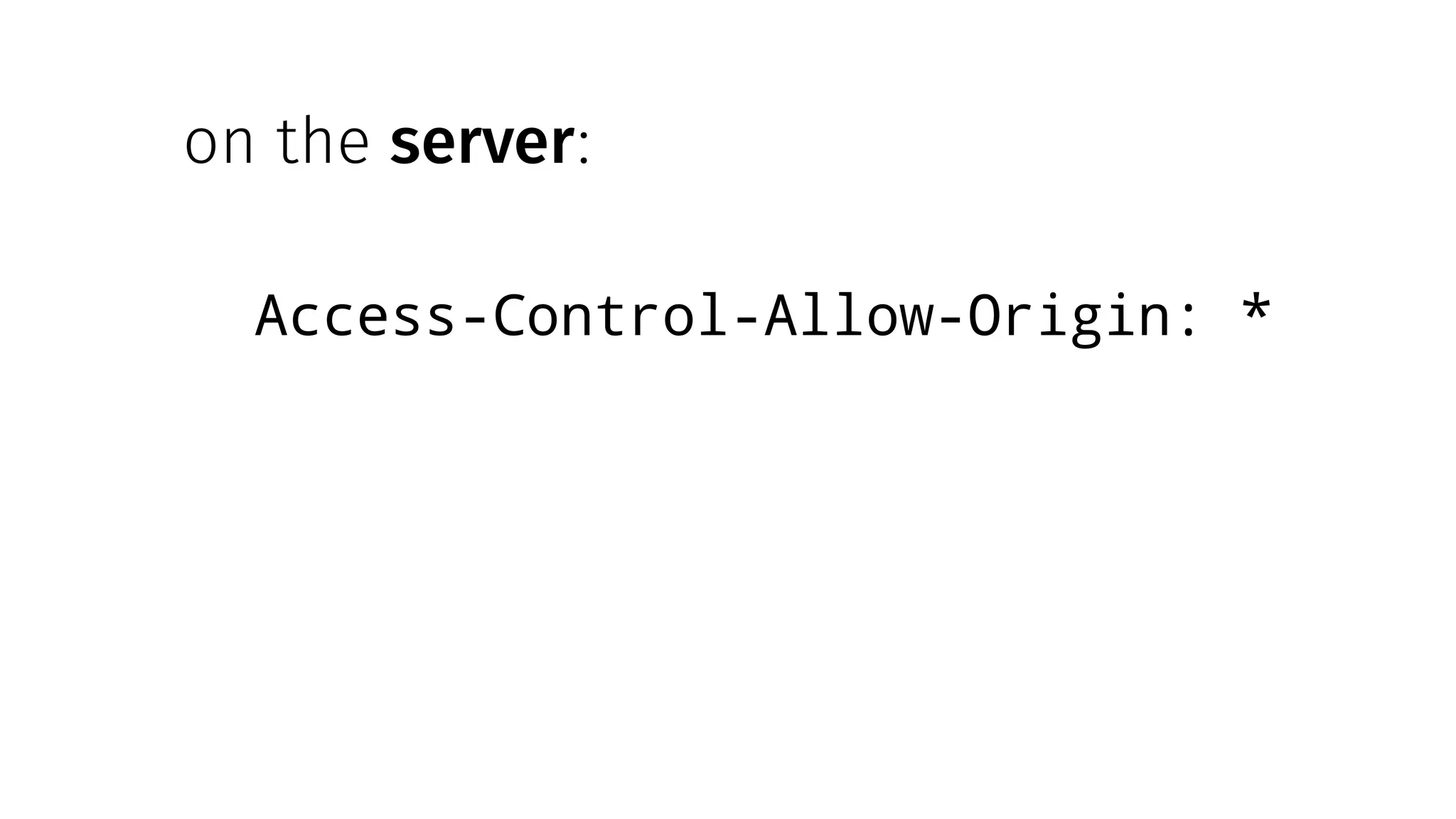
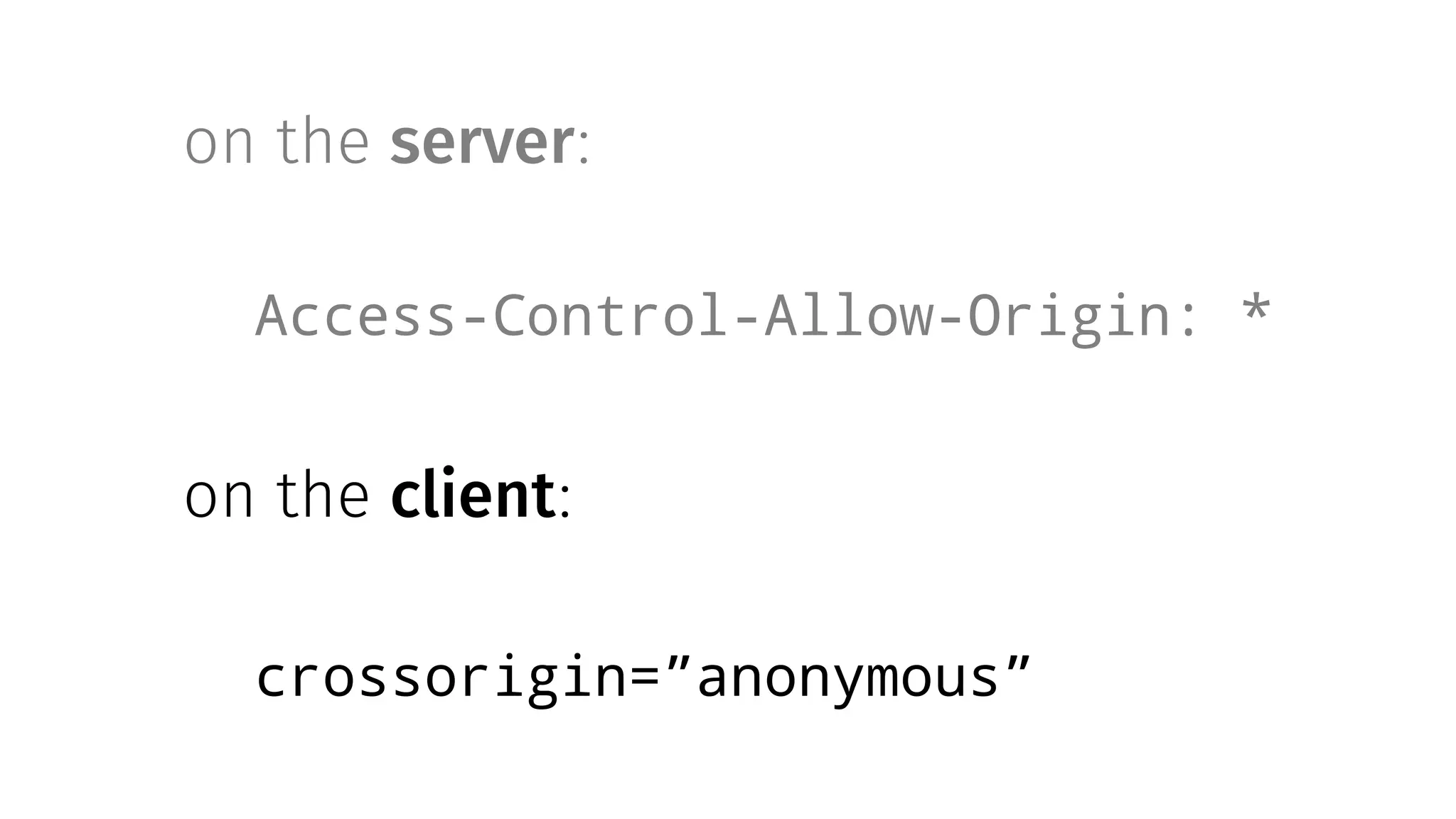
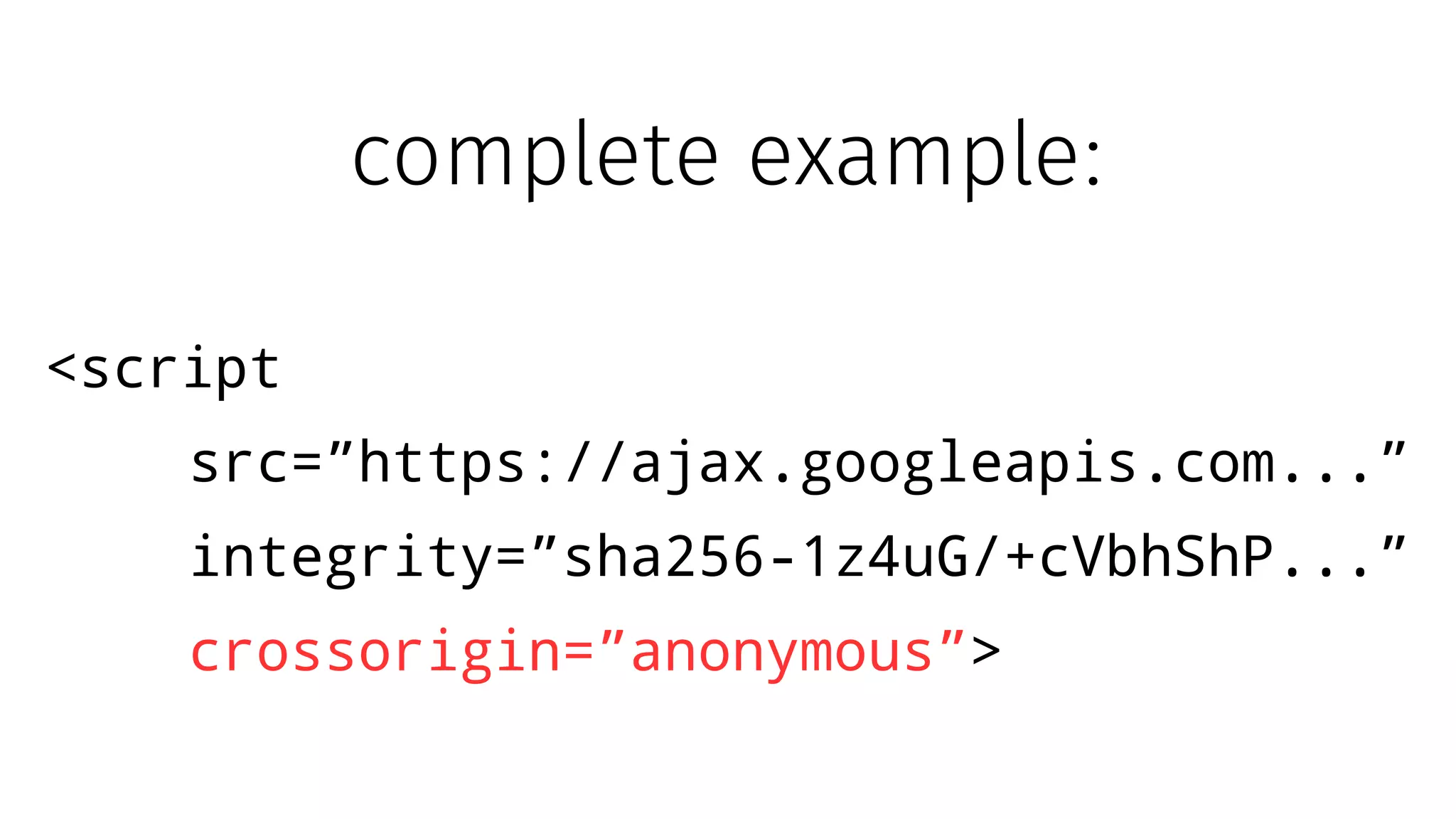
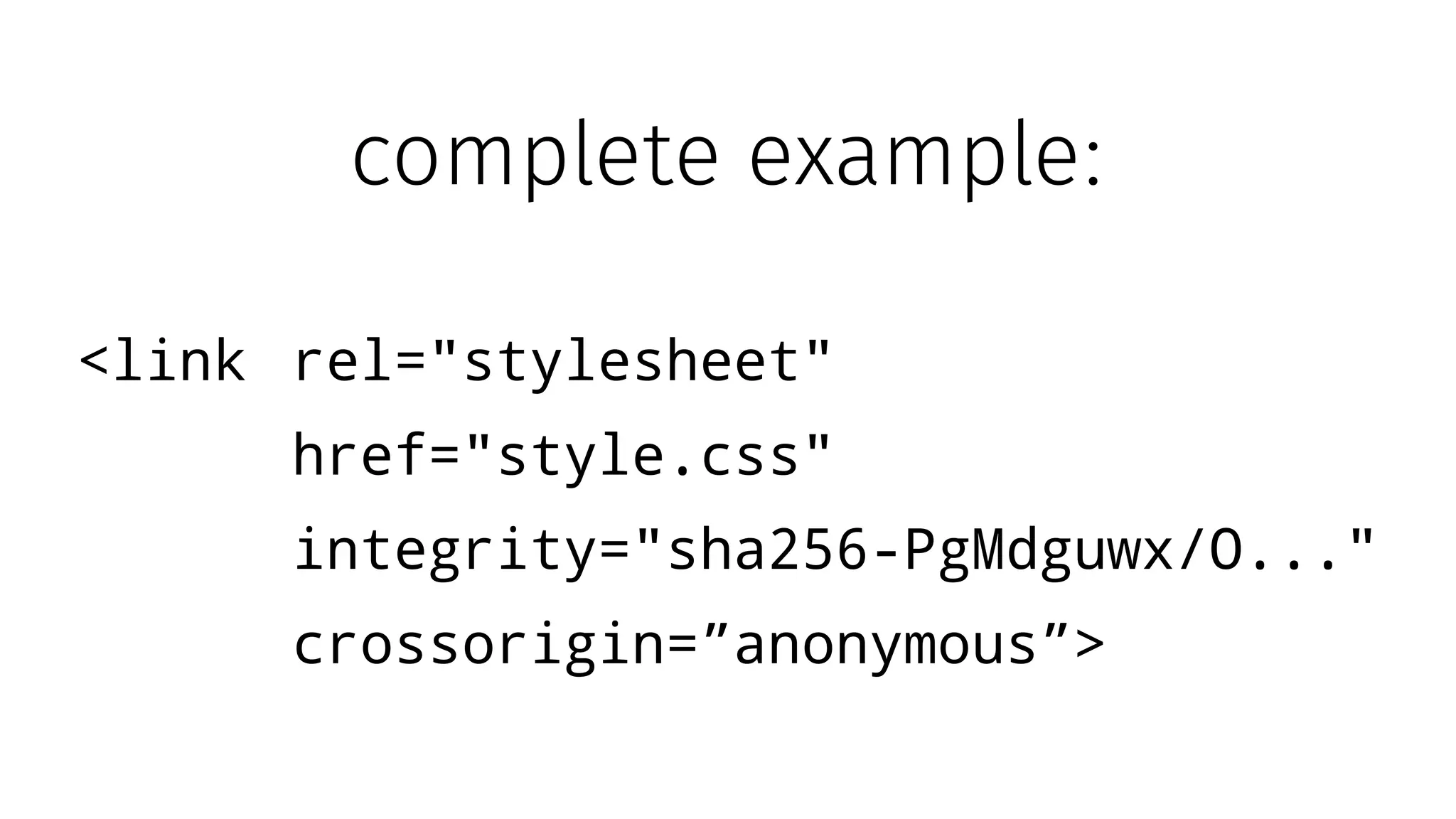
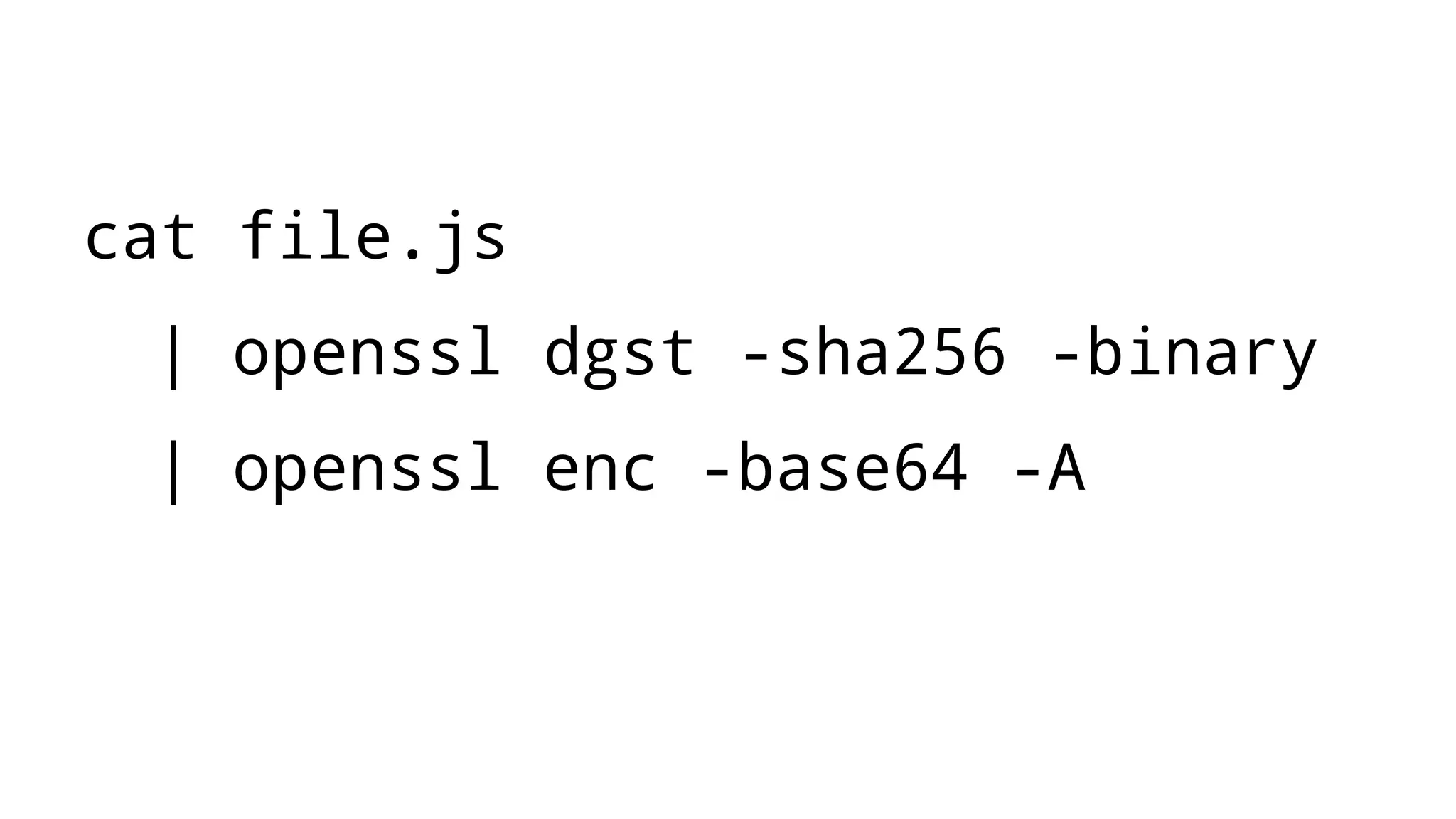
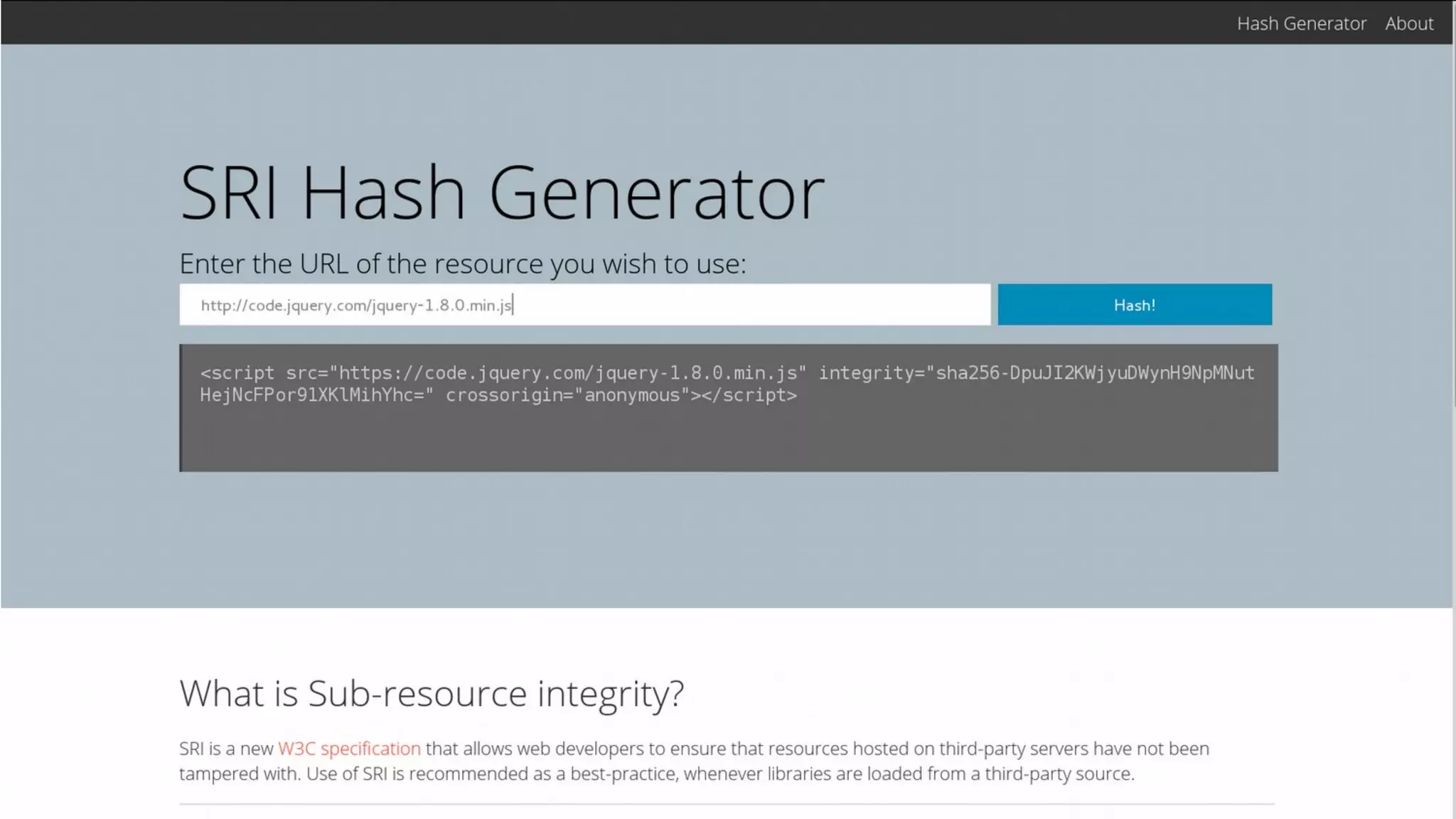
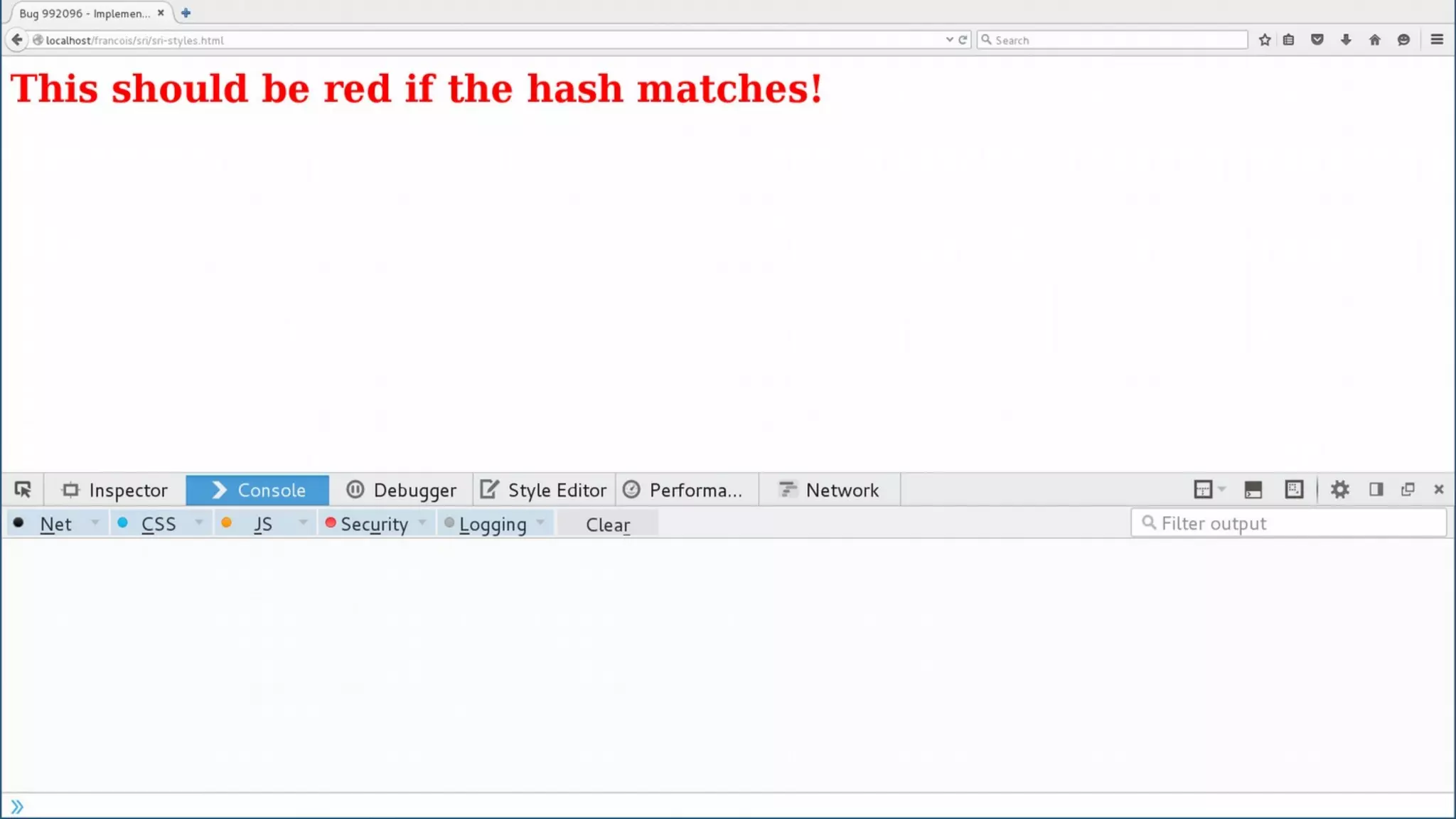
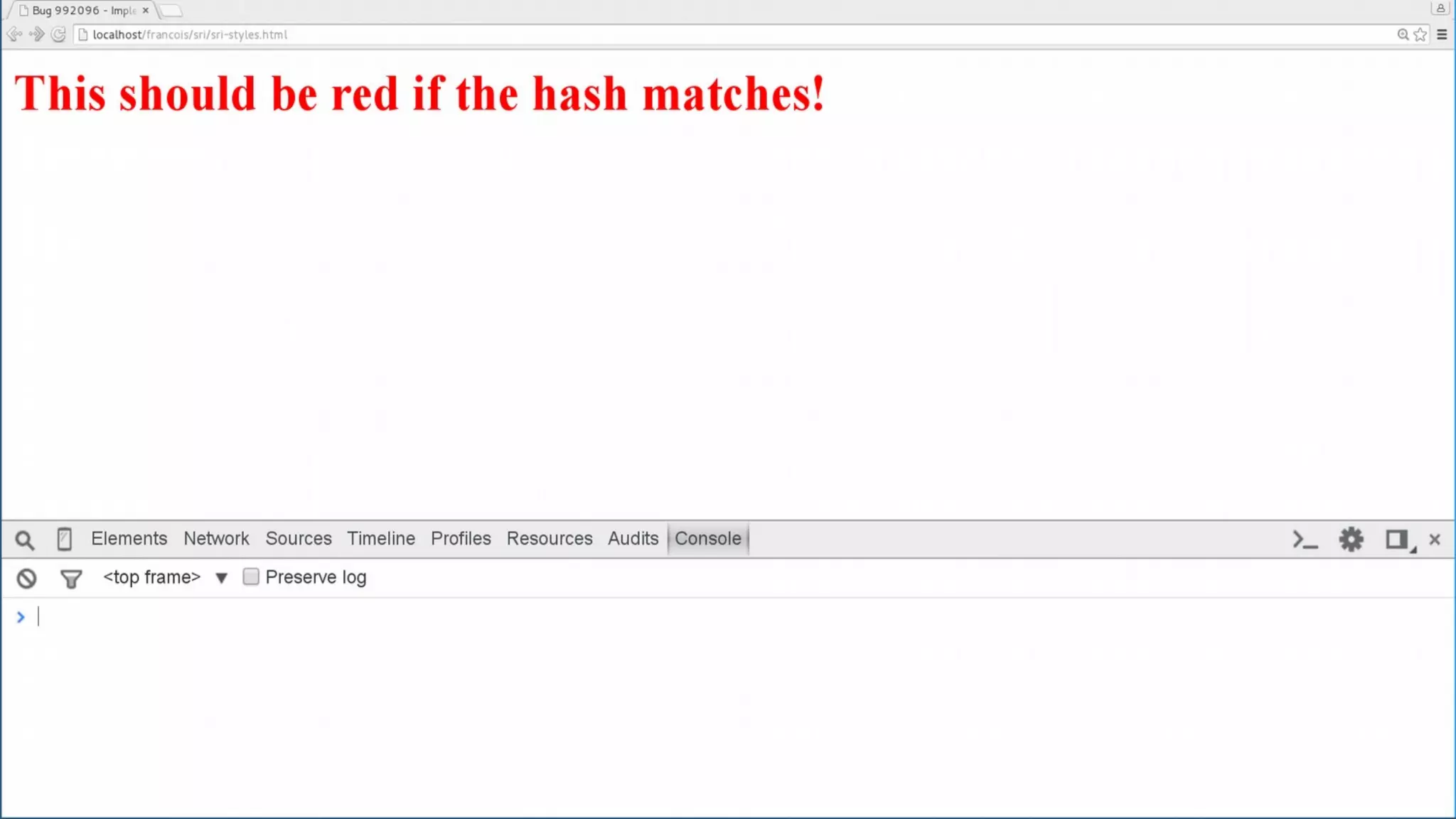
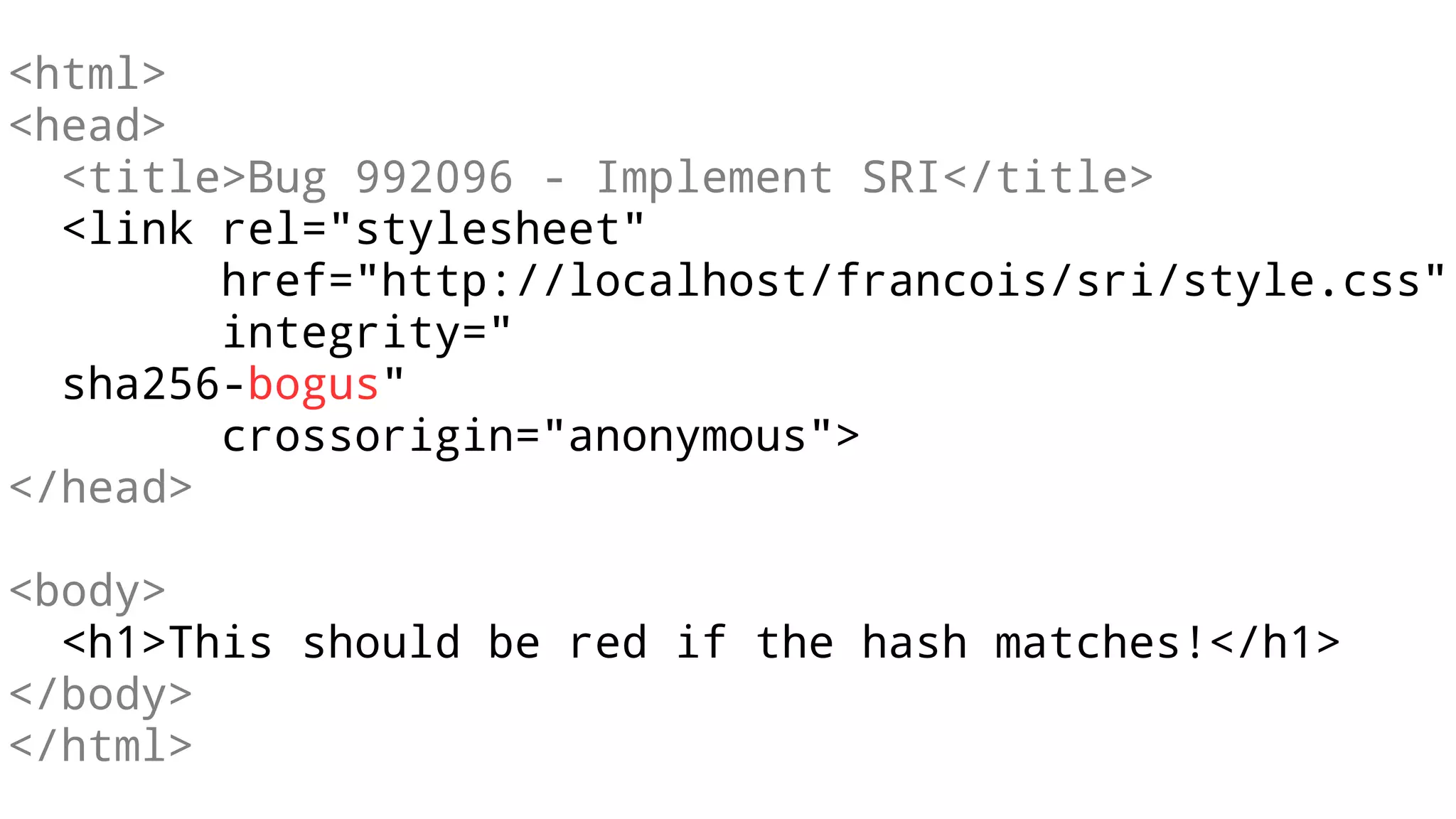
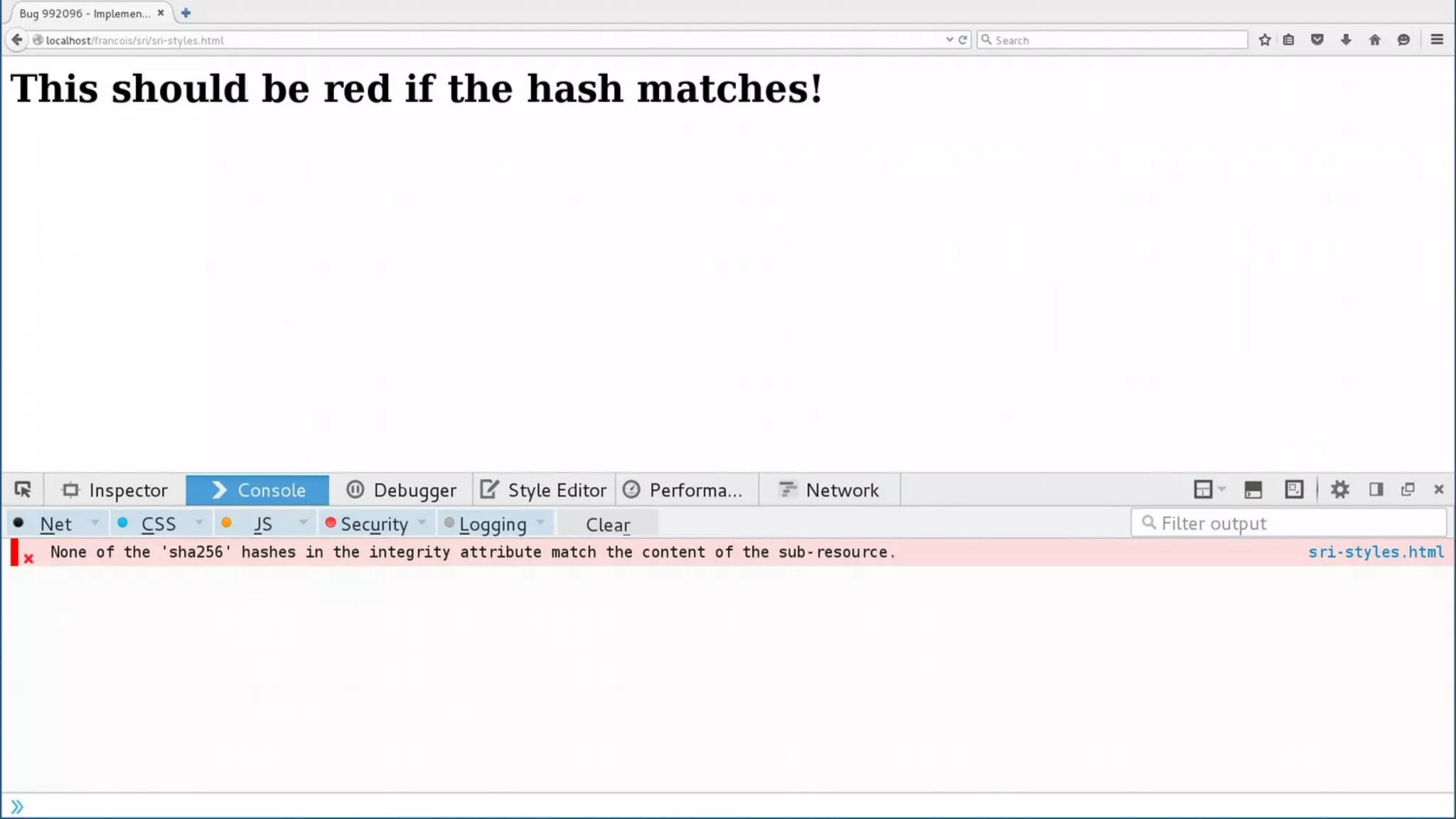
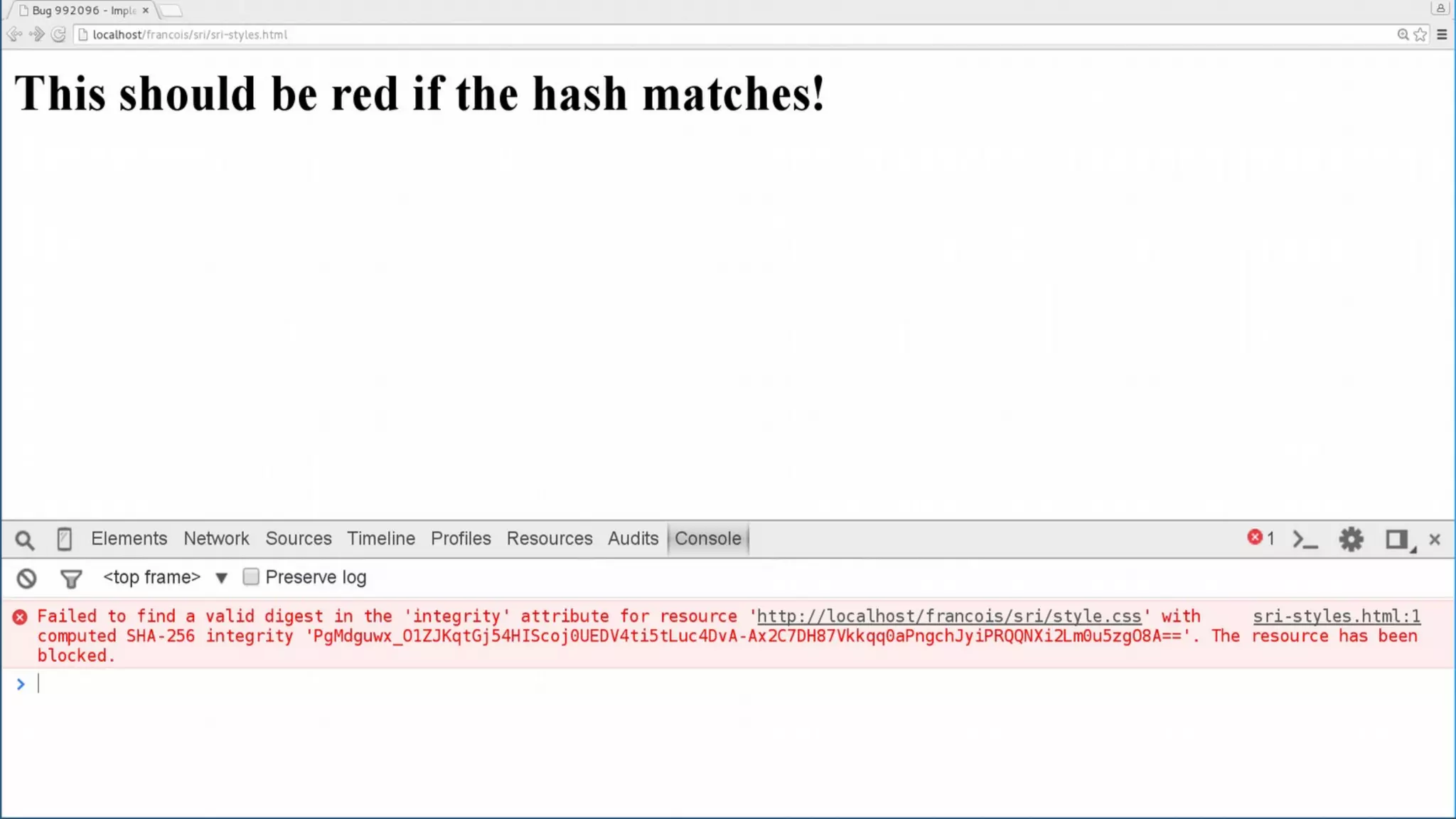
The document discusses web security measures including Content Security Policy (CSP) and Strict Transport Security (HSTS) to prevent XSS attacks and HTTPS downgrade attacks. It emphasizes the importance of using integrity attributes to ensure script integrity and highlights the challenges of dynamically-generated scripts. It also mentions cross-origin requests and provides examples of implementing these security features.