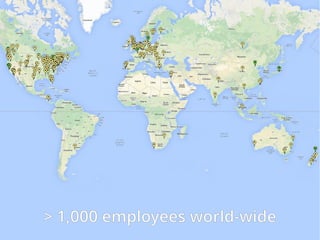
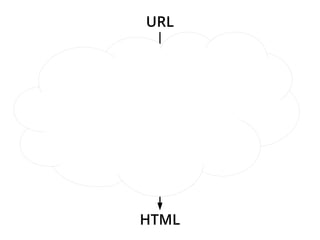
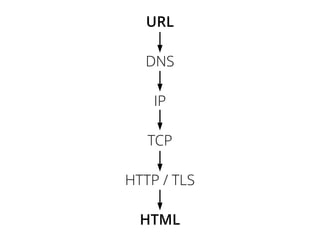
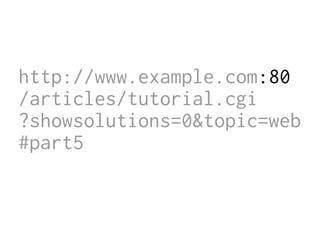
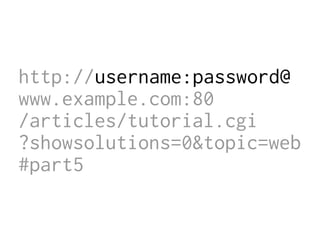
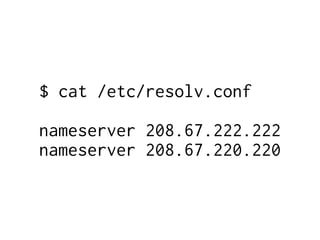
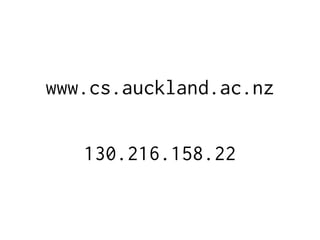
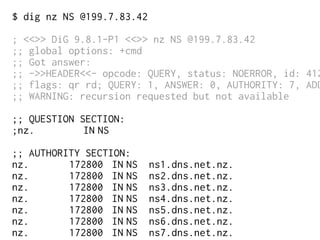
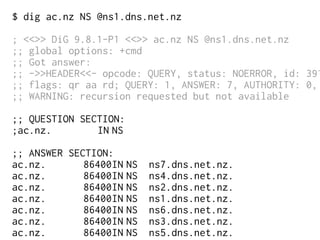
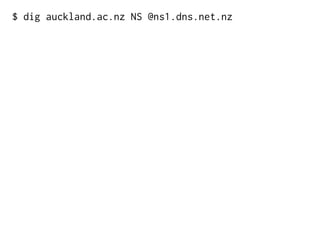
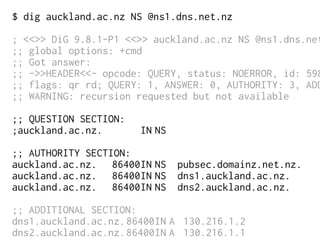
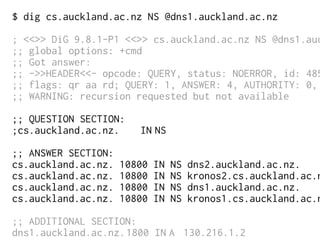
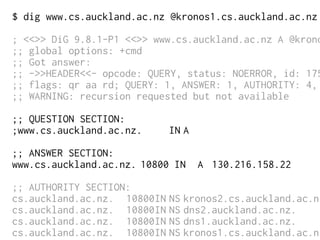
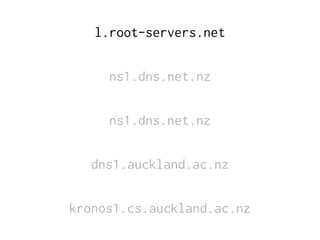
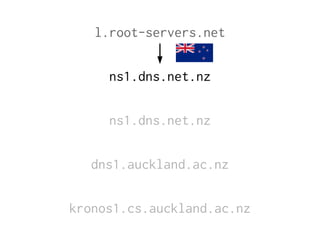
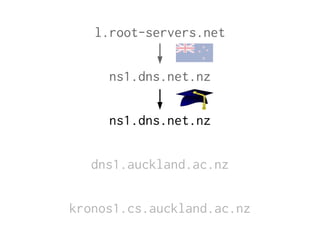
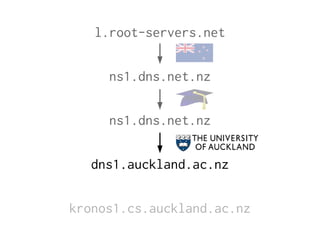
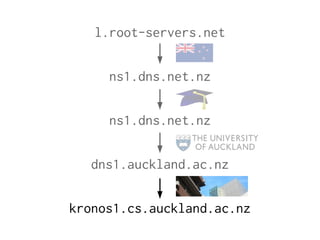
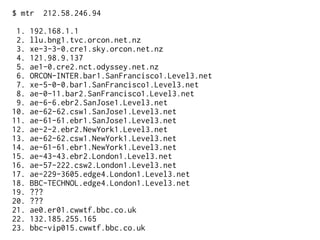
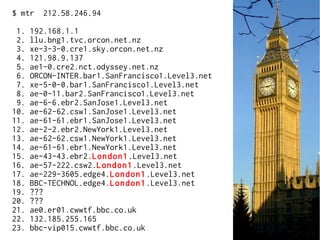
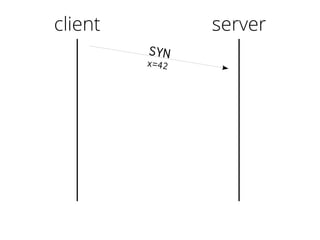
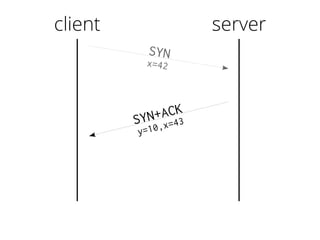
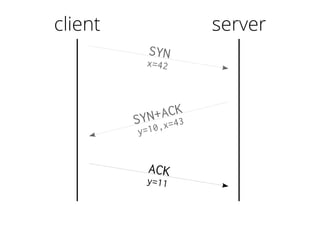
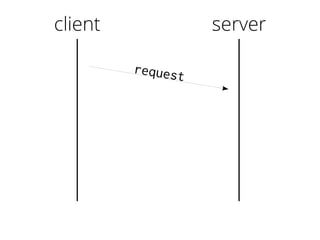
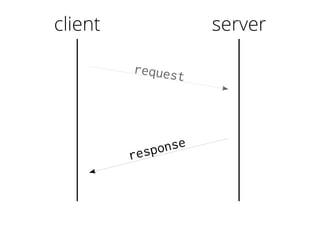
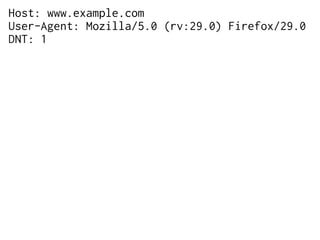
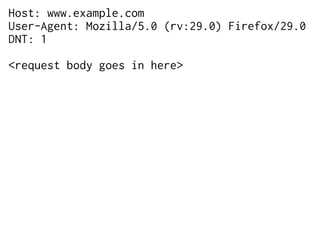
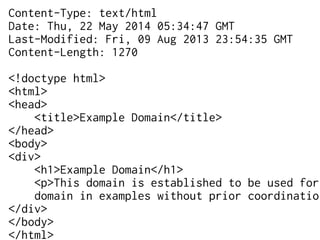
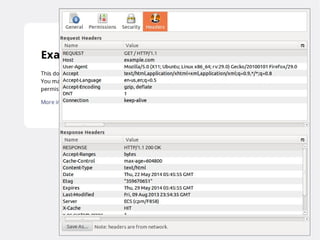
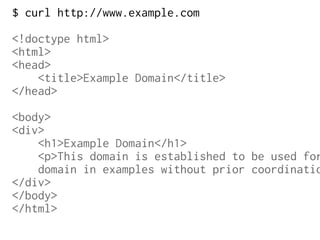
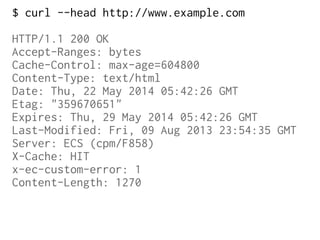
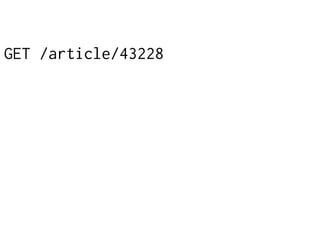
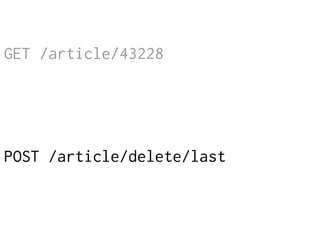
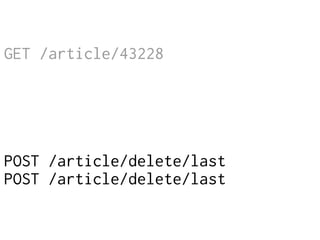
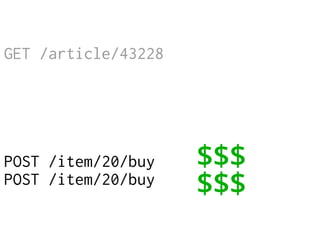
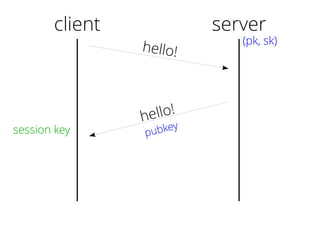
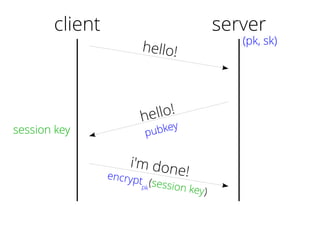
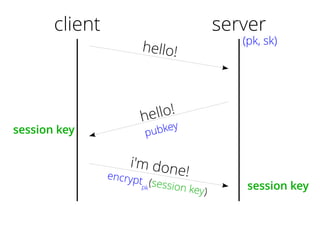
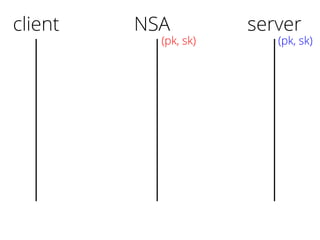
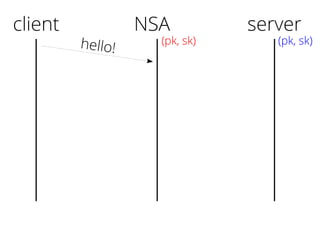
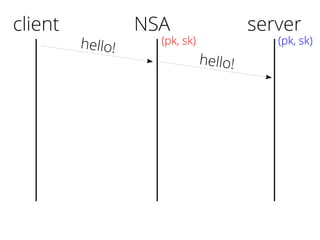
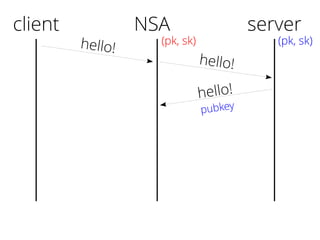
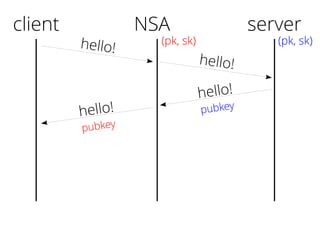
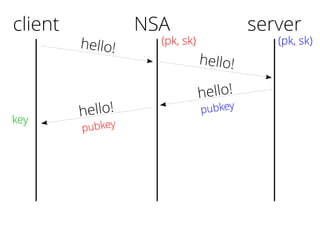
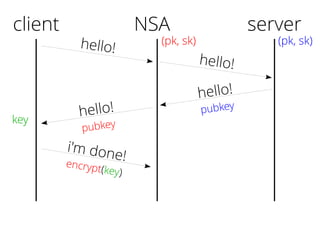
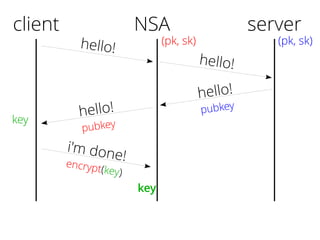
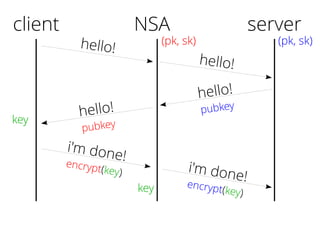
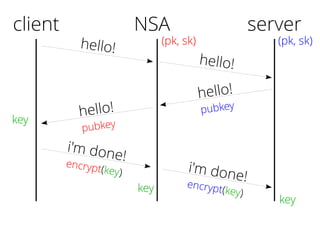
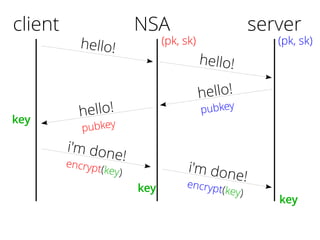
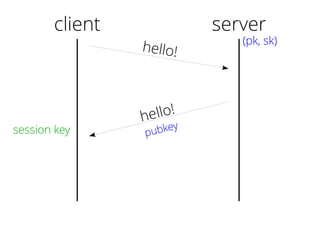
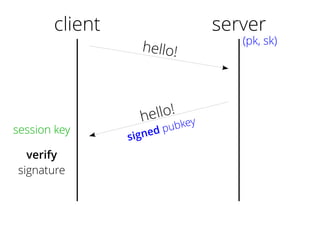
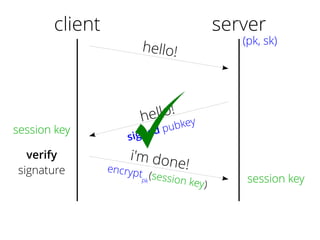
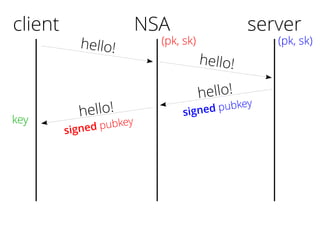
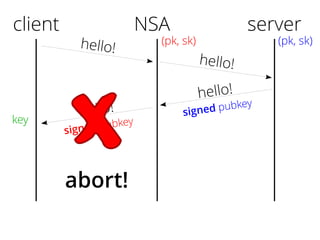
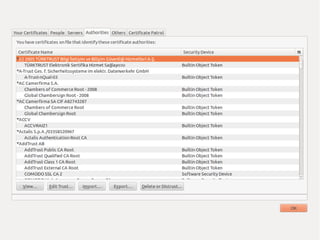
The document provides insights into the technical aspects of web performance, detailing how data is transmitted and rendered in a web environment, particularly focusing on protocols such as DNS and HTTP. It discusses abstractions in programming and performance implications, emphasizing the importance of understanding underlying layers for troubleshooting. Various commands and methods for querying DNS records are illustrated to showcase practical applications in network troubleshooting.