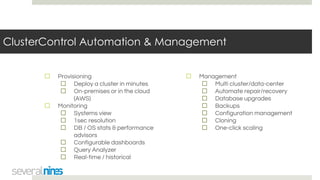
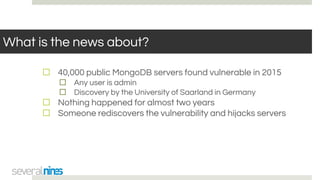
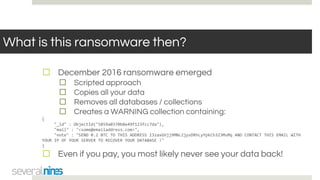
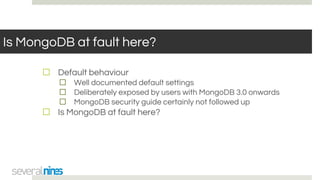
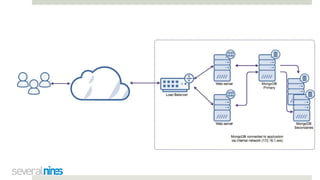
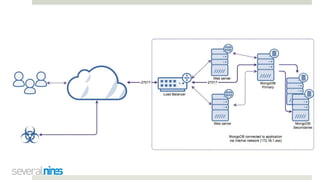
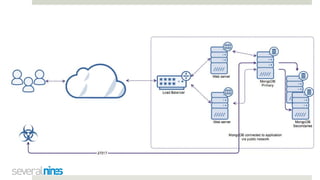
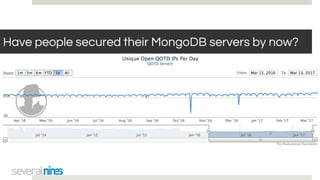
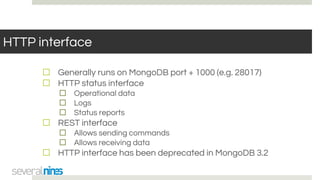
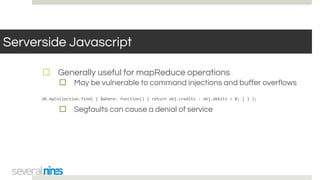
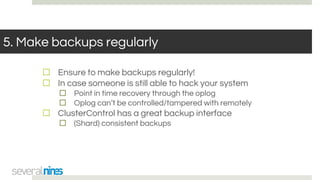
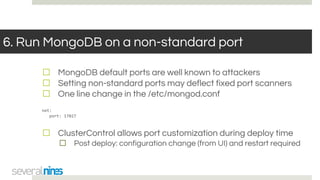
The document outlines a webinar hosted by Severalnines focusing on MongoDB security, specifically discussing ransomware vulnerabilities and how to secure MongoDB databases. Key points include identifying and addressing vulnerabilities, enabling authentication, avoiding weak passwords, and implementing robust security measures such as firewalls and regular backups. The session also covers additional security features provided by ClusterControl to enhance MongoDB deployment management.







![Excessive rights
☐ Roles/users are stored in the database you connect to
☐ Local users with userAdmin role
☐ Able to grant admin role to any database they have rights to
☐ Normally you can’t bypass local authentication
☐ Except when you authenticate command line
[user@server ~]$ mongo -u user -p pass --authenticationDatabase test
☐ Or switch databases after authentication](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-26-320.jpg)
![Excessive rights (2)
[user@server ~]$ mongo -u admin -p admin test
mongodb_0:PRIMARY> db.createUser({ user: "user",
pwd: "pass",
roles: [
{ role: "readWrite", db: "test" },
{ role: "userAdmin", db: "test" }
{ role: "userAdmin", db: "exploited" }
]
})
[user@server ~]$ mongo -u user -p pass --authenticationDatabase test
mongodb_0:PRIMARY> db.createUser({ user: "exploit",
pwd: "pass",
roles: [
{ role: "readWrite", db: "exploited" },
{ role: "dbAdmin", db: "exploited" }
]
})
[user@server ~]$ mongo -u exploit -p pass --authenticationDatabase test exploited
mongodb_0:PRIMARY>](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-27-320.jpg)









![Enable audit logging
☐ Enable the audit log, when possible
☐ MongoDB Enterprise
☐ Percona Server MongoDB
☐ Scan for unexpected behaviour:
auditLog:
destination: file
format: BSON
path: /var/lib/mongodb/auditLog.bson
filter: '{ atype: { $in: [ "dropCollection", "dropDatabase", "dropIndexes", "renameCollection" ] } }'](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-40-320.jpg)
![Check for external connectivity
☐ Use an external box (any AWS box would suffice)
☐ Try to telnet to your host
telnet your.host.com 27017
☐ A response indicates MongoDB ports are open
Trying your.host.com...
Connected to your.host.com.
Escape character is '^]'.](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-42-320.jpg)
![Check for external connectivity (2)
☐ Install nmap and scan
[you@host ~]$ sudo yum install nmap
[you@host ~]$ nmap -p 27017 --script mongodb-databases your.host.com
PORT STATE SERVICE REASON
27017/tcp open unknown syn-ack
| mongodb-databases:
| ok = 1
| databases
| 1
| empty = false
| sizeOnDisk = 83886080
| name = test
...
| 2
| empty = true
| sizeOnDisk = 1
| name = admin
|_ totalSize = 167772160](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-43-320.jpg)

![☐ MongoDB build information:
[you@host ~]$ nmap -p 27017 --script mongodb-info 10.10.22.17
Starting Nmap 6.40 ( http://nmap.org ) at 2017-01-16 14:37 UTC
Nmap scan report for 10.10.22.17
Host is up (0.00078s latency).
PORT STATE SERVICE
27017/tcp open mongodb
| mongodb-info:
| MongoDB Build info
| javascriptEngine = mozjs
| buildEnvironment
| distmod =
| target_arch = x86_64
…
| openssl
| running = OpenSSL 1.0.1e-fips 11 Feb 2013
| compiled = OpenSSL 1.0.1e-fips 11 Feb 2013
| versionArray
| 1 = 2
| 2 = 11
| 3 = -100
| 0 = 3
| version = 3.2.10-3.0
…
| Server status
| errmsg = not authorized on test to execute command { serverStatus: 1.0 }
| code = 13
|_ ok = 0](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-45-320.jpg)
![Check for excessive privileges
☐ MongoDB authenticates against the database you connect to
☐ Additional rights to other databases may be defined
☐ Connect command line with the authenticationDatabase
☐ Also switching databases will not re-authenticate
use mydatastore
db.createUser(
{
user: "user",
pwd: "password",
roles: [ { role: "readWrite", db: "mysdatastore" },
{ role: "readWrite", db: "admin" } ]
}
);
☐ Notice the additional rights on the admin database!](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-46-320.jpg)
![Check for excessive privileges (2)
☐ Review all privileges of all databases
my_mongodb_0:PRIMARY> use mydatastore
switched to db mydatastore
my_mongodb_0:PRIMARY> db.getUsers();
[
{
"_id" : "mysdatastore.user",
"user" : "user",
"db" : "mysdatastore",
"roles" : [
{
"role" : "readWrite",
"db" : "mysdatastore"
},
{
"role" : "readWrite",
"db" : "admin"
}
]
}
]](https://image.slidesharecdn.com/webinar-slides-become-a-mongodb-dba-securing-mongodb-170315091249/85/Webinar-slides-How-to-Secure-MongoDB-with-ClusterControl-47-320.jpg)