This document summarizes a research paper that proposes a new block cipher cryptographic symmetric key algorithm called the "TACIT Encryption Technique." The algorithm uses a unique mathematical logic approach along with a new key distribution system. It is implemented in a hardware chip using VHDL programming language on a Network-on-Chip model for secure data transmission. Experimental results show encryption and decryption of 128-bit blocks using an 8-bit key through simulation in Modelsim. The algorithm aims to provide better security, speed and flexibility than existing algorithms like DES, AES and RSA.

![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
34
Keywords: Application Specific Integrated circuits (ASIC), Complex programmable logic
devices (CPLD), Field Programmable Gate Array (FPGA), Network on chip (NOC), System
on chip (SOC), Very Large Scale of Integration (VLSI) , Very High Speed Integrated
Circuit hardware Description language (VHDL).
I. INTRODUCTION
Intellectual property (IP) based networks like the Internet are known for their
scalability and resilience to partial failures. Their reliance on datagram forwarding on a hop-
by-hop basis makes them ideal for the transport of short control messages with little or no
call holding times [22]. Each terminal in the network must have a unique address so
messages or connections can be routed to the correct recipients. Connection-oriented
broadband networks based on asynchronous transfer mode (ATM) technology permit a
much higher degree of predictability to be engineered relatively simply, because of their
inherent resource partitioning capability. They are thus highly suited for transport of streams
with quality of service (QOS) requirements and long call holding times [22]. However, there
is an issue of safe transmission of information when communicating over any untrusted
medium which includes any network particularly the internet (IP based). Cryptography is
being utilized to handle such issues since year. [23] A cryptographic algorithm is considered
to be computationally secured if it cannot be broken with standard resources, either current
or future and apart from the algorithm, distribution of keys is equally important to make an
efficient cryptosystem [23].
Cryptography involves encryption algorithms along with an efficient approach of key
management because there are different algorithms that offer different degree of security [7].
Encryption algorithms are classified according to the type of transformation and keys. In the
broad sense they can be classified as the symmetric and asymmetric approaches. In
symmetric algorithm, the sender and receiver agree on a same (shared) key. In asymmetric
algorithms encryption and decryption of data takes place with two different keys in such a
way that it is difficult to decrypt without the decryption key. Both algorithms were reported
by Tomas and Rene [25] for their application in Third Generation Cellular Networks. Based
upon the algorithm The DES (Data Encryption Standard) and triple DES was implemented in
compliance with the NIST Data Encryption Standard [5, 7]. It processes 64-bit blocks, with
one, two, or three 56-bit keys. However the security and slow processing speed was major
concerns with DES triples respectively. The AES (Advanced Encryption Standard) core
implements Rijndael cipher encoding and decoding in compliance with the NIST Advanced
Encryption Standard [5-6, 11]. AES cipher is specified as a number of repetitions of
transformation rounds that convert the input plaintext into the final output of cipher text.
Each round consists of several processing steps, including one that depends on the encryption
key [7]. Again the processing time was a major concern with AES. Most of today’s
conventional encryption algorithms are implemented in software and their throughputs are
about 10 megabits per second (Mbps) at most if a 128-bit key is used. However, the
explosively growing electronic data transportation often necessitates higher throughput. As a
result, it is desired to implement encryption algorithms into hardware to achieve high-speed
encryption and decryption.
There are many encryption and decryption algorithms which are already proposed. A
comparison [21] of all is shown in table 1 listed below. Table 2 list the comparison of various
encryption algorithms on the basis of Type and Features. It can be seen that from this](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-2-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
35
comparison table that TACIT Encryption Technique has a unique independent approach by
using some suitable mathematical logic along with a new key distribution system which is
being applied on a secure policy based routing [8]. The main advantage of TACIT logic is
that it can processes n-bit blocks and n- bit key size. This approach may be good if the block
size is less than the key size [21]. The algorithm may be implemented in all the languages
support Unicode system facility like Java, C#, .Net, etc.
Table 1 Comparison of various encryption algorithms [21] on the basis of Key size and
Block size.
Algorithm Key size(Bits) Block size(Bits)
DES 64 64
Triple DES 192 64
AES Variable (192 or 256) 128
Kasumi Encryption core 128 64
Blowfish 448 64
RSA 1024 128
RC4 Variable(40 or 128) Variable (32,64,128)
X-MODES 32 32
TACIT Encryption n-bit ( n can vary) n-bit
Table 2 Comparison of various encryption algorithms based on Type and Features [21]
Algorithm Type Features
DES Block cipher Most common, Not strong enough
Triple DES Block cipher Modification of DES, Adequate security
AES Block cipher Replacement of DES, Excellent security, limited key
size
Kasumi
Encryption core
Block cipher Designed for Third Generation Partnership
Project(3GPP), used in Universal Mobile
Telecommunication System UMTS, limited to 64-bit
word size
Blowfish Block cipher Excellent security, No. of bits are variable ranging
from 16-448 bits.
RSA Block cipher Asymmetric algorithm, speed is low
RC4 Stream cipher Fast stream chipper in Secured Socket Layer (SSL),
more memory is required since they work on large
chunk of data (stream) instead of block cipher.
X-MODES Block cipher Enhanced security level & faster.
TACIT
Encryption
Block cipher Good for small size of packets
Tools Utilized: Design and FPGA implementation includes the following software
development tools: Project Navigator Application ISE 13.2 of Xilinx Company is a tool to
design the IC and to view their RTL (Register Transfer Logic) schematic. Model SimEE
10.1b students edition of Mentor Graphics Company is used for simulation and debugging the
functionality. The hardware chip implementation is done using VHDL programming
language.
The paper is organized as follows: Section I presents the introduction and the tools
utilized. Section II discusses the NOC Model for the data transfer. Section III presents the](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-3-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
36
data encryption for TACIT logic, section IV presents data decryption for TACIT logic.
Section V describes result and performance evolution and Conclusion is presented in Section
VI.
II. NOC MODEL
Network-on-Chip (NOC) is an approach for designing the telecommunication
subsystem between IP cores in a System-on-a-Chip (SOC). The software and application
layer is a very critical aspect on the NOC communication stack [24]. We mostly focused on
the physical and network layers. Secured transmission among nodes is possible if it is
following the NOC layer protocol. All networked layers follow the pipeline and parallel
processing with coprocessors. This leads to validate the hardware parameters on chip
development: Synthesis Options Summary, VHDL Compilation, VHDL Analysis, Device
utilization summary, Timing report, delay time calculation are the core parameters to design
the chip. A NOC template consists of continuous areas of the chip called regions. Regions are
physically isolated from each other but have special mechanism for communication among
each other. In order to achieve simplicity of interconnections, short cycle time and scalability,
a region of NOC consists of a two dimensional mesh of switches. The computing and other
resources are embedded in the slots within the switches.
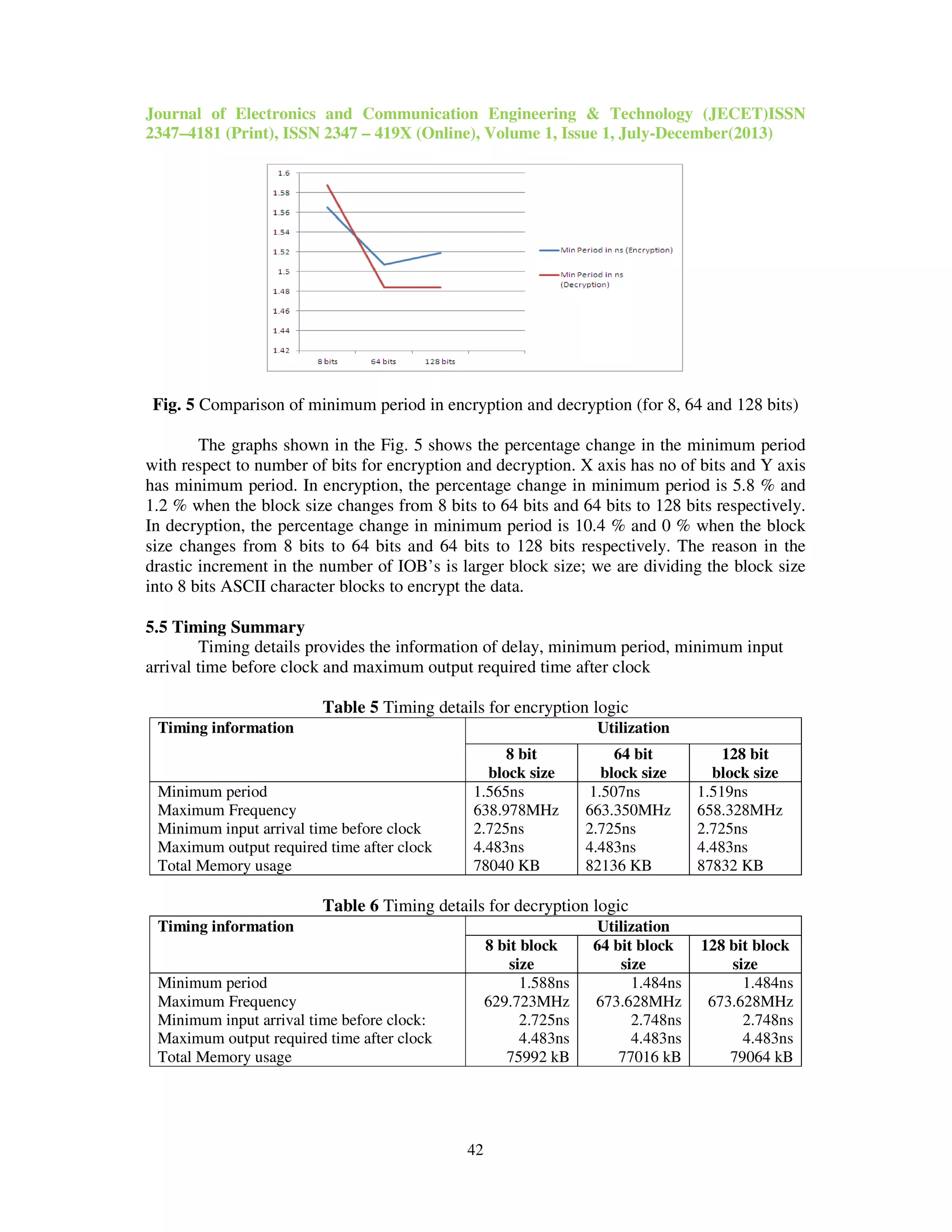
Fig. 1 Layered NOC structure for data transmission [24]](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-4-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
37
Fig. 2 Example of NOC architecture [26]
A switch is connected to four other switches. A scalable communication infrastructure
that better supports the trend of SOC integration consists of an on chip packet-switched
micro-network of interconnects generally known as Network-on-Chip (NOC) architecture
[26]. The basic idea is borrowed from tradition a large-scale multi-processors and the wide-
area networks domain, and envisions on-chip router (or switch)-based networks on which
packetized communication takes place, as depicted in Fig. 2 Cores access the network by
means of proper interfaces, and have their packets forwarded to destination through a multi
hop routing path. The scalable and modular nature of NOCs and their support for efficient on-
chip communication [26] potentially leads to NOC-based multi-processor systems
characterized by high structural complexity and functional diversity.
III. DATA ENCRYPTION ALGORITHM FOR TACIT LOGIC
To implement the TACIT Logic for data communication between two nodes of NOC
the following algorithm has been used. The corresponding VHDL coding has been developed
and results are presented in section V.
Step 1: Text file content is read and position of the character is shuffled by using initial
permutation approach using key value.
Step 2: Read the character from the text file corresponding to the text and get the ASCII
value of that character.
Step 3: Perform XOR operation with the specific n-bit key value.
Step 4: A secure tacit logic has been introduced (i.e. nk
xor kk
along with some specific
operations; where n is the value computed from step 3).
Step 5: Convert the value into binary one.
Step 6: Perform reverse operation on the binary string.
Step 7: Corresponding decimal value is found.
Step 8: The Unicode character corresponds to the decimal value is formed which is none
other than the cipher text.
Step 9: Continue step 1 to 7 for the next characters of the file until End of File (EOF) is
reached.](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-5-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
38
IV. DATA DECRYPTION ALGORITHM FOR TACIT LOGIC
The decryption algorithm at the receiving end follows the following steps.
Step 1: Read the first character from the cipher text and get the corresponding decimal value
of it.
Step 2: The corresponding binary value is evaluated and make the reverse of it.
Step 3: Inverse of the tacit logic is applied.
Step 4: Perform XOR with n-bit key value.
Step 5: The character corresponds to it is determined.
Step 6: Now reshuffling is done using key value.
Step 7: Repeat the steps (1 to 6) till the end.
4.1 Functional Description
4.1.1 Input value
a. Inputs: Keyboard Enter data into system.
Clock: This is the clock used for the core operations.
b. Reset: Asynchronous reset, that sets the device to a known state.
4.1.2. Modes of Operation:
a. ASCII Input Mode: The input from the keyboard is considered to be encoded in
ASCII.
b. Hexadecimal Mode: The input from the keyboard is considered to be encoded in
Hexadecimal, thus the only valid characters are 0-9, A-F.
c. Encryption Mode: Device is configured to receive data and output cipher text.
d. Decryption Mode: Device is configured to receive cipher text and output data.
V. RESULTS & PERFORMANCE EVALUTION
5.1 Data Encryption
In the screenshots of Fig. 3 text is the input text [0-127] which is encrypted in ASCII
format for each character. Key size is considered as 8 bits and each character is encoded with
key size individually. Key is in integer form and key_value is 8 bits binary value of Key.
Xor_value is the result after XOR of text and key_value. tacit_logic_1 is the value of TACIT
operation nk
( n= no of bits in each character and k= key size). In our case n value is fixed, n
= 8 and k value is variable 0 to 255 in decimal. tacit_logic_2 is the value of TACIT operation
kk
. tacit_logic is the actual value of TACIT logic nk
XOR kk
, reverse value is the value of
reverse operation on tacit_value. After it the corresponding decimal value is kept by
intermediate signal decimal_value. ciper_text is the intermediate value of cipher text in
encryption logic and ctext represents the actual cipher text.](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-6-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
39
Fig. 3 Modelsim Simulation (Data Encryption of 128 bits block size
Encryption of plaintext text [ ]= [127 : 0] by the external key k[ ] = [7 : 0] will produce a
cipher text ctext[ ] = [ 127 : 0]. For encryption, RESET is set to high at first but low for the
rest of time RESET is low. Positive clock pulse clk is applied for the synchronization.
Step input 1: reset = 1, positive clock pulse clk ia applied and tenn run in Modelsim
simulator.
Step input 2: reset = 0, positive clock pulse clk , n = 8, Key = input in decimal, text = [127 :
0] block size and run in modelsim simulator. Fig. 3 shows the simulation results of data
Encryption, for a word length of 128 bits.](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-7-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
40
5.2 Data Decryption
Fig. 4: Modelsim Simulation (Data Decryption for 128 bits block size)
In the screen shot of decryption logic Fig.4, ctext is the input cipher text to decryption
logic ctext[0-127] which is decrypted in ASCII format for each character. Key size is
considered same as 8 bit and each character is encoded with key size individually. Key is in
integer form and key_value is 8 bit binary value of Key. Xor_value is the result after XOR of
text and key_value. tacit_logic_1 is the value of TACIT operation nk
( n= no of bits in each
character and k= key size). In our case n value is fixed, n = 8 and k value is variable 0 to 255
in decimal. tacit_logic_2 is the value of TACIT operation kk
. tacit_logic is the actual value of
TACIT logic nk
XOR kk
, reverse value is the value of reverse operation on tacit_value. After
it the corresponding decimal value is kept by intermediate signal decimal_value. ciper_text is
the intermediate value of cipher text in encryption logic and ctext represents the actual cipher
text.
The decryption of cipher text ctext[127: 0][F823AB657CED ..1894] using the same
key k [7:0] produces the original plaintext text[127:0] = [F413579ABCDE2468..] For
decryption, RESET is set to high at first but low for the rest of time RESET is low. Positive
clock pulse clk is applied for the synchronization.](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-8-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
41
Step input 1: reset = 1, positive clock pulse clk ia applied and tenn run in Modelsim
simulator.
Step input 2: reset = 0, positive clock pulse clk, n = 8, Key = input in decimal, ctext = [127:
0] block size and run in modelsim simulator. Fig. 4 shows the simulation results of data
decryption, for a word length of 128 bits.
5.3 Device Utilization and timing Summary for encryption
Device utilization is the hardware and logic circuitry required to implement the
design. It consist of no. of slices, flip flops, gates, combinational logic circuitry and
input/output blocks. Selected Device: 2vp2fg256-6, this is the device for targeting FPGA
with Speed Grade: - 6
Table 3 Device utilization in encryption logic
Device part Device Utilization
8 bit block size 64 bit block size 128 bit block
size
Number of Slices 16 out of 1408 1% 32 out of 1408 2% 72 out of
1408 5%
Number of Slice Flip
Flops
19 out of 2816 0% 55 out of 2816 1% 124 out of
2816 4%
Number of 4 input
LUTs
23 out of 2816 0% 27 out of 2816 0% 32 out of
2816 1%
Number of bonded
IOBs
9 out of 140 6% 65 out of 140 46% 129 out of
140 92%
Number of GCLKs 1 out of 16 6% 1 out of 16 6% 1 out of
16 6%
5.4 Device Utilization and timing Summary for decryption
Selected Device: 2vp2fg256-6, this is the device for targeting FPGA with Speed
Grade: -6
Table 4 Device utilization in decryption logic
Device part Device Utilization
8 bit block size 64 bit block size 128 bit block size
Number of Slices 10 out of 1408
0%
43 out of 1408
3%
79 out of 1408
5%
Number of Slice Flip
Flops
17 out of 2816
0%
74 out of 2816
2%
138 out of 2816
4%
Number of 4 input
LUTs
13 out of 2816
0%
70 out of 2816
2%
134 out of 2816
4%
Number of bonded
IOBs
17 out of 140
12%
129 out of 140
92%
137 out of 140
97%
Number of GCLKs 1 out of 16
6%
1 out of 16
6%
1 out of 16
6%](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-9-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
43
The graph shown in the Fig. 6 shows the percentage change in the total memory with
respect to number of bits for encryption and decryption. X axis has no of bits and Y axis has
total memory. In encryption, the percentage change in total memory is 5.8 % and 56.96 %
when the block size changes from 8 bits to 64 bits and 64 bits to 128 bits respectively. In
decryption, the percentage change in total memory is 40.96 % and 20.48 % when the block
size changes from 8 bits to 64 bits and 64 bits to 128 bits respectively. The reason in greater
change in the memory is increment in the number of IOB’s. We are dividing the block size
into 8 bits ASCII character blocks to encrypt/ decrypt the data. Separate memory allocation
and IOBs for each character consumes more memory but it increases the speed due to
pipelining.
Fig. 6 Comparison of total memory in encryption and decryption (for 8, 64 and 128 bits)
VI.CONCLUSION
The hardware chip implementation of TACIT logic for encryption and decryption is
implemented in Xilinx 13.2 and functional simulated in Modelsim 10.1 b. We have
implemented for one character (8 bits), 64 bits, 128 bits and key size was taken 8 bits, and it
means sender and receiver both can enjoy with key range 0 to 255 in (decimal). The main
advantage of the TACIT logic is that we can enhance the block size and key size both. In
future, we can implement the encryption and decryption for larger size of text and key.
Compression techniques could be implemented along with encryption procedure.
REFERENCES
[1] J. Montalvo, Member, IEEE, Ronald S. Gyurcsik, Member, IEEE, and John J. Paulos,
Senior Member, IEEE, An Analog VLSI Neural Network with On-Chip Perturbation
Learning Antonio IEEE JOURNAL OF SOLID-STATE CIRCUITS, VOL.32, NO.4,
APRIL1997 535: (page 8-9)
[2] Naveen Choudhary, Bursty Communication Performance Analysis of Network-on-Chip
with Diverse Traffic Permutations, International Journal of Soft Computing and Engineering
(IJSCE) ISSN: 2231-2307, Volume-1, Issue-6, January 2012 (page 1)
70000
72000
74000
76000
78000
80000
82000
84000
86000
88000
90000
8 bits 64 bits 128 bits
Total Memory(KB),
Encryption
Total Memory(KB),
decryption](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-11-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
44
[3] Yuhui Huang, and Bo Yuan Computer Science Department University of California, Los
Angeles Los Angeles, USA A Tree-Based Topology Synthesis for On-Chip Network Jason
Cong9, page 5-8
[4] The IEEE Research Bulletin of Jordan ACM, ISSN: 2078-7952, Volume II (II) Page 2-3,
a Quadrant-XYZ Routing Algorithm for 3-D Asymmetric Torus Network-on-Chip (page 8-
20).
[5] Wei Zhong, Song Chen, Fei Ma,Takeshi Yoshimura, and Satoshi Goto, Floor planning
Driven Network-on-Chip Synthesis for 3-D SoCs Graduate School of Information Production
and Systems, Waseda University Kitakyushu 808-0135,Japan Page (1-3)
[6] WeiZhong, BeiYu, SongChen, Graduate School of Information Production and Systems,
Waseda University, Kitakyushu, Japan Application-Specific Network-on-Chip Synthesis:
Cluster Generation and Network Component Insertion (page 3-9)
[7] Krishnan Srinivasan, Sonics Inc. Zhonghai Lu, Royal Institute of Technology, December
2010, OCP-IP Network-on-chip benchmarking workgroup Erno Salminen, Tampere
University of Technology (pp 1,4-7)
[8] Muhammad Ali, Awais Adnan, Institute of Management Sciences, Peshawar, Pakistan.
Comparative analysis of transient-fault tolerant schemes for Network on Chips (page 12-16)
[9] Ilya Issenin University of California, Nikil Dutt, University of California Data Reuse
Driven Memory and Network-on-Chip Co-Synthesis page (4-9)
[10] White paper on A Network on Chip Architecture and Design Methodology Laboratory
of Electronics and Computer Systems, Department of Microelectronics and Information
Technology, Royal Institute of Technology, Kista, Stockholm, Sweden VTT Electronics, Box
1100, Oulu, FIN-90571, Finland
[11] Soung c. Liew, Member, IEEE. and Kevin w. Lu, Member, IEEE, Comparison of
Buffering Strategies for Asymmetric Packet Switch Modules IEEE JOURNAL ON
SELECTED AREAS IN COMMUNICATIONS. VOL. 9. NO. 3. APRIL (pp-2-3)
[12] Syed Riffat Ali, “Implementation of Firmware on SPC Switching Systems”, IEEE
Journal on Selected Areas Communications, Vol. 6, No. 8, PP. 1401-1404, 1988.
[13] Semiconductor Complex Limited, Internet PDF: Data sheets of XC 95 series CPLD
[Online]. Available: http://sclindia.com,
[14] K. Asanovi, R. Bodik, B. Catanzaro, J. Gebis, P. Husbands, K. Keutzer, D .Patterson, W.
Plishker, J. Shalf, S. Williams, and K. Yelick, The landscape of parallel computing research :
A view from berkeley," University of California at Berkeley, December 2006. [Online] .
Available: http: // parlab. eecs. berkeley. edu/ pubs/ EECS- 2006-183 .pdf
[15] S. Borkar, design challenges of technology scaling." IEEE Micro, no.4, p. 2329, July-
August 1999.
[16] V. Agarwal, M. Hrishikesh, S.Keckler, and D.Burger, Clock rate versus ipc: the end of
the road for conventional microarchitechtures, "in Proceeding of the 27th
annual International
Symposium on Computer Architrecture (ISCA'00'), vol.28, no.2, May2000, pp. 248 {259.
[17] N. Kirman, M. Kirman, R. Dokania, J. Martnez, A. Apsel, M. Watkins, and D. Albonesi,
Leveraging optical technology in future bus-based chip multiprocessors, "in Proceedings of
the 39th International Symposium on Micro architecture, December 2006, pp .492 -503.
[18] J Bhaskar, VHDL Primer, Second edition BPB publication
[19] M. Morris Mano Digital Design, Second Edition by Pearson Education
[20] N. Weste, CMOS VLSI Design, Third edition A Circuits and Systems Perspective by
Pearson Education Pub.](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-12-2048.jpg)
![Journal of Electronics and Communication Engineering & Technology (JECET)ISSN
2347–4181 (Print), ISSN 2347 – 419X (Online), Volume 1, Issue 1, July-December(2013)
45
[21] Manmeet Kaur, Manjit Kaur,Gurmohan Singh, C-DAC Mohali India, Comparison of
TACIT Encryption Algorithm with Various Encryption Algorithms, International Journal of
Electronics and Computer Science Engineering, page (1-10)
[22] Aurel A. Lazar, Columbia University, Programming Telecommunication Networks,
IEEE Network • September/October 1997 Page (1 and 2)
[23] Prosanta Gope, Ajit Singh, Nikhil Pawha, Ashwani Sharma, An Efficient Cryptographic
Approach for Secure Policy Based Routing (TACIT Encryption Technique), 978-1-4244-
8679-3/11/©2011 IEEE Page (1-4)
[24] M.Coppola, S.Curaba, M.Grammatikakis, R.Locatelli, G.Maruccia, F.Papariello,
L.Pieralisi, White paper on OCCN: A Network-On-Chip Modeling and Simulation
Framework, ISD Integrated system developments, page 8
[25] Thomas Eisen barth, “Cryptography and Cryptanalysis for embedded” Dissertation Ph.D
Faculty of Electrical Engineering and Information Technology Ruhr University Bochum,
Germany July 2009.
[26] Davide Bertozzi and Luca Benini, A Network-on-Chip Architecture for Gigascale
Systems-on-Chip, IEEE Circuits and systems magazine, second quarter 2004, page (18,19
and 20).](https://image.slidesharecdn.com/40520130101005-131011025138-phpapp02/75/40520130101005-13-2048.jpg)