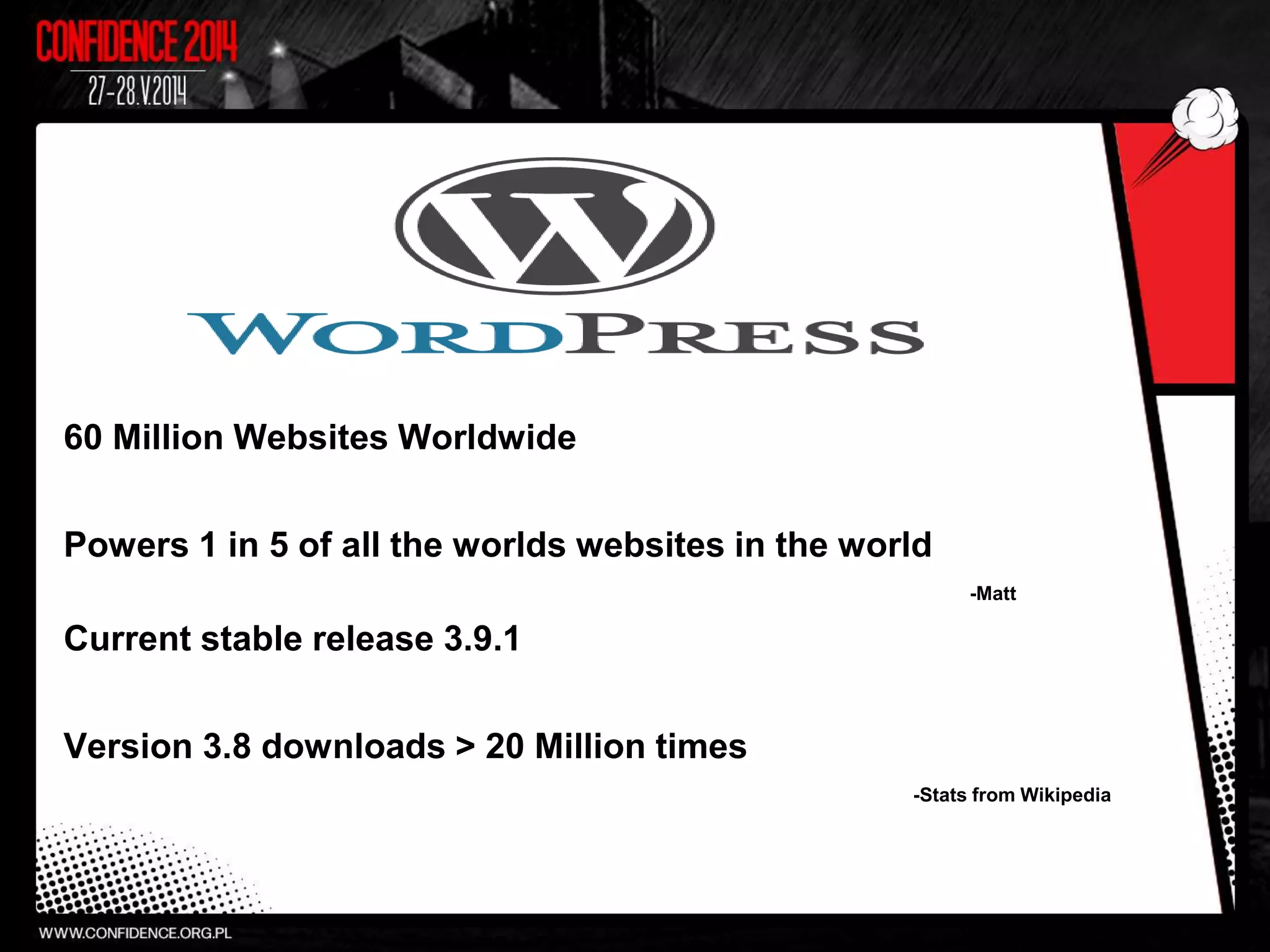
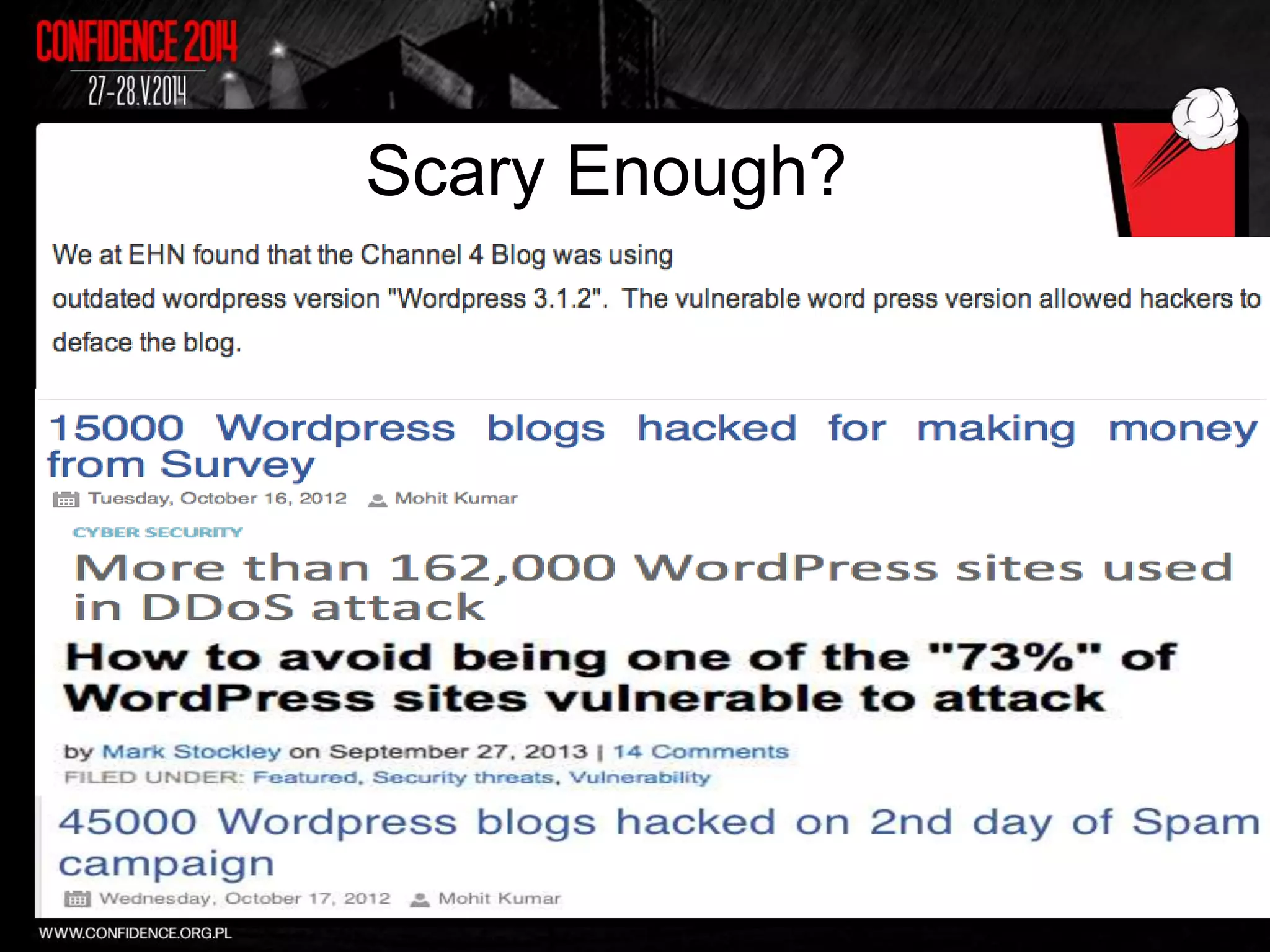
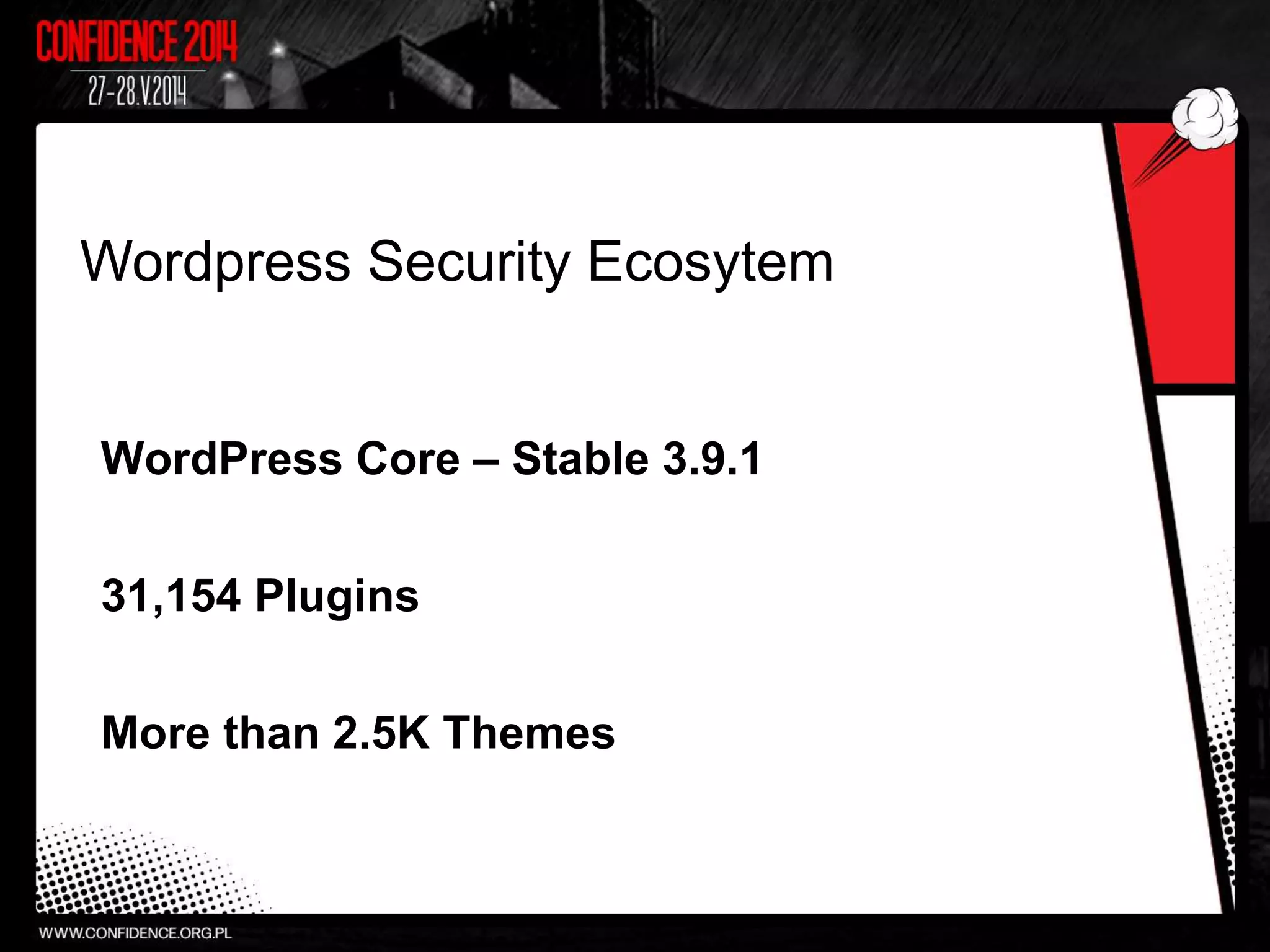
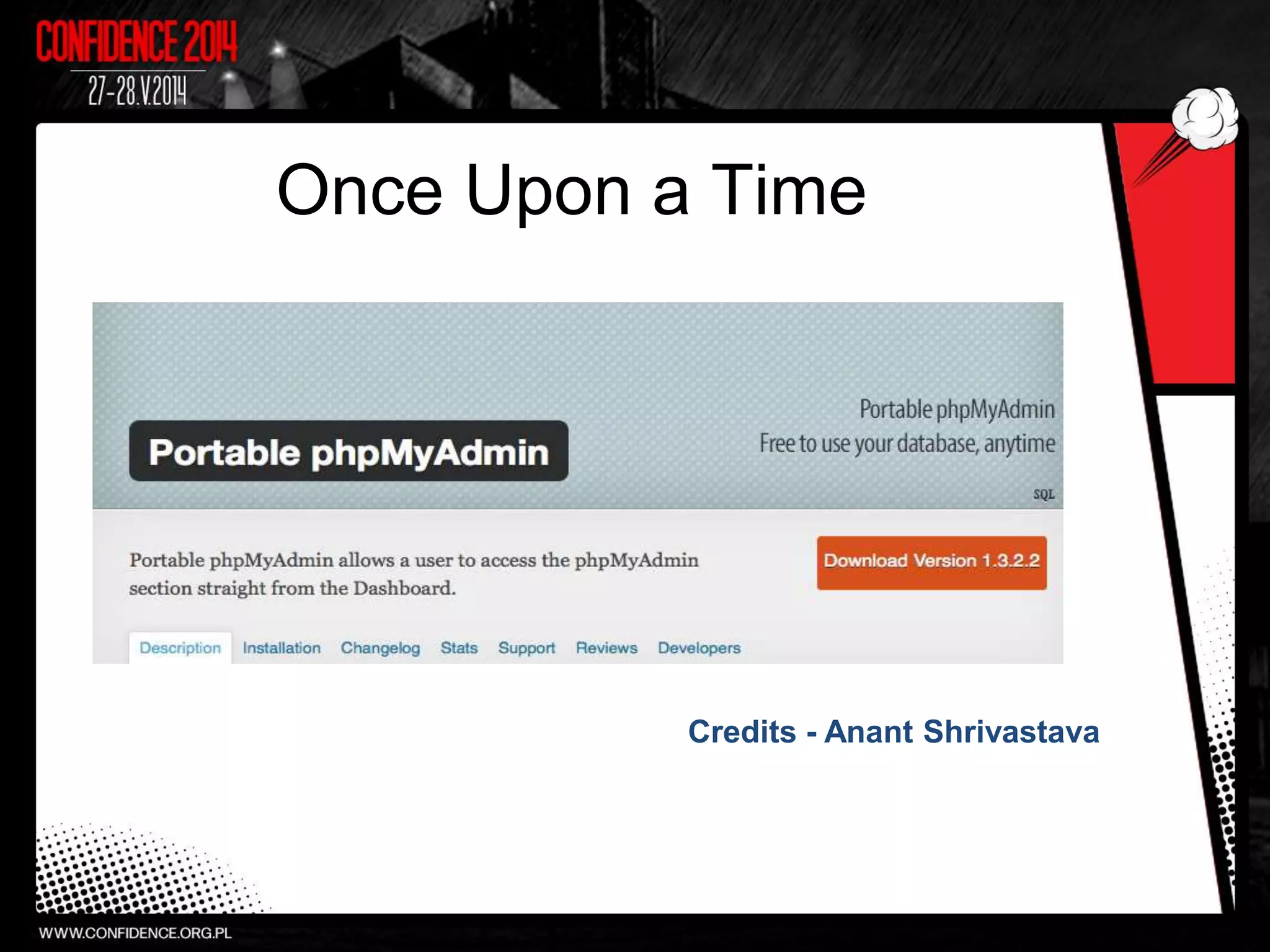
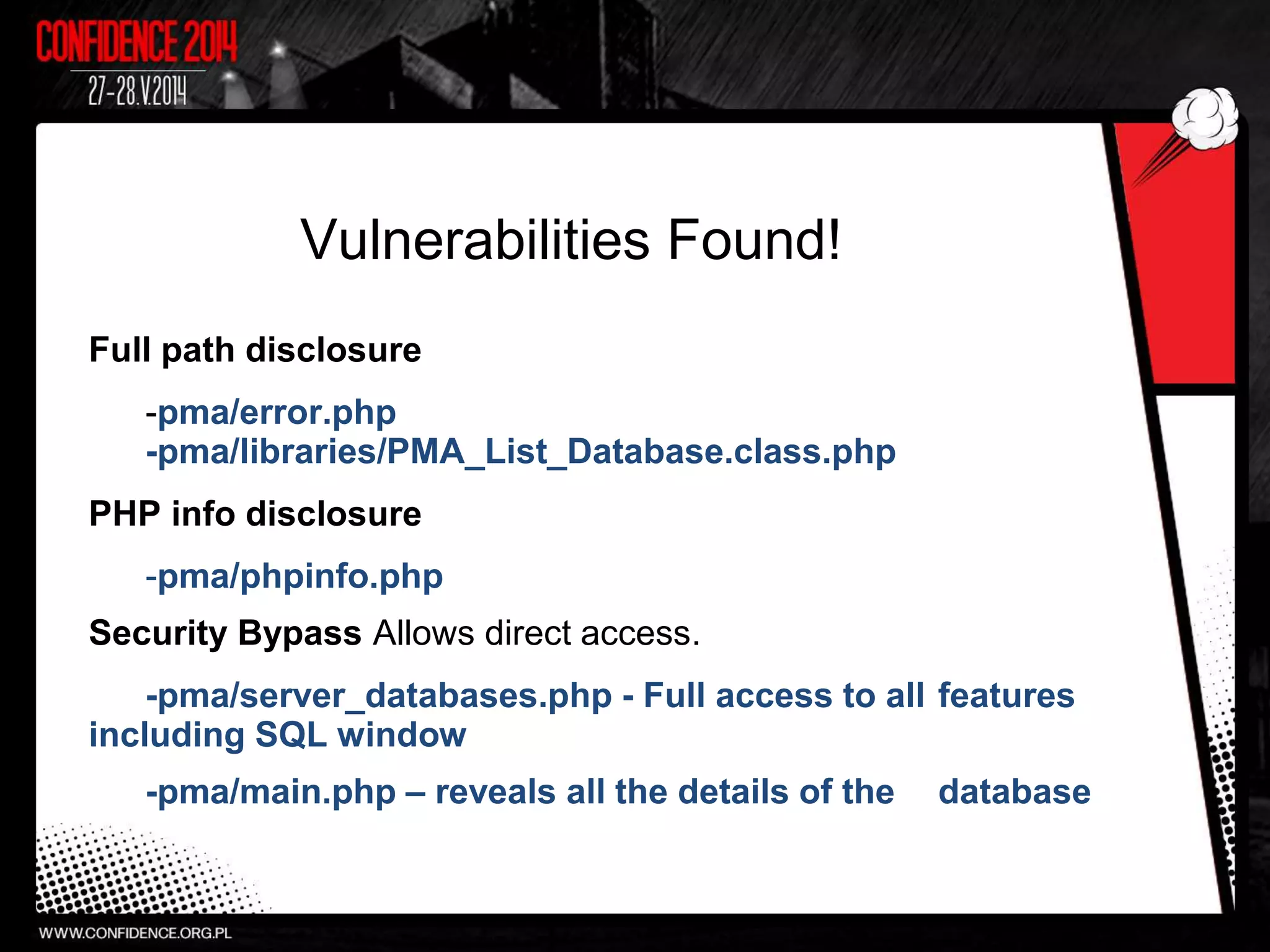
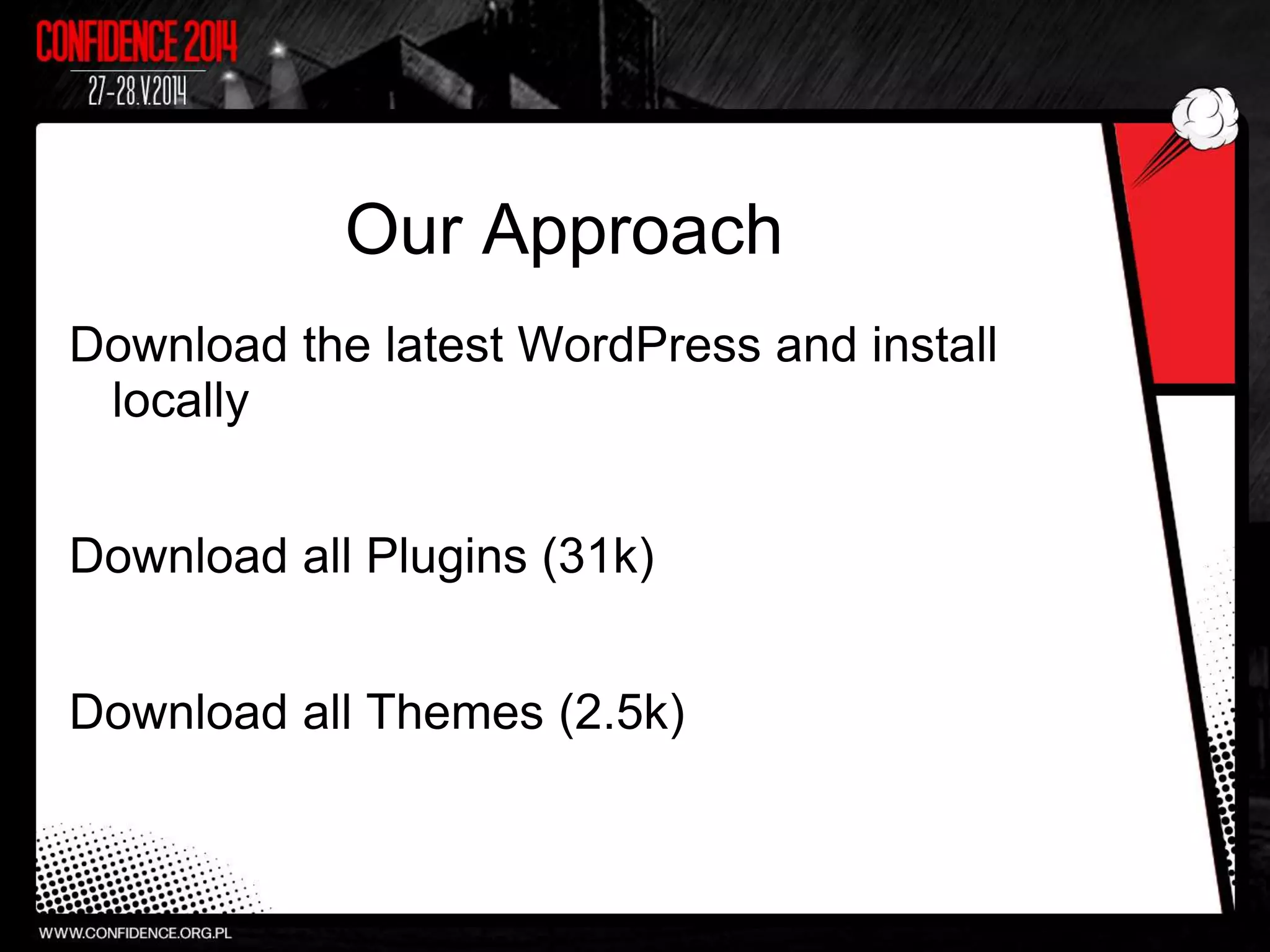
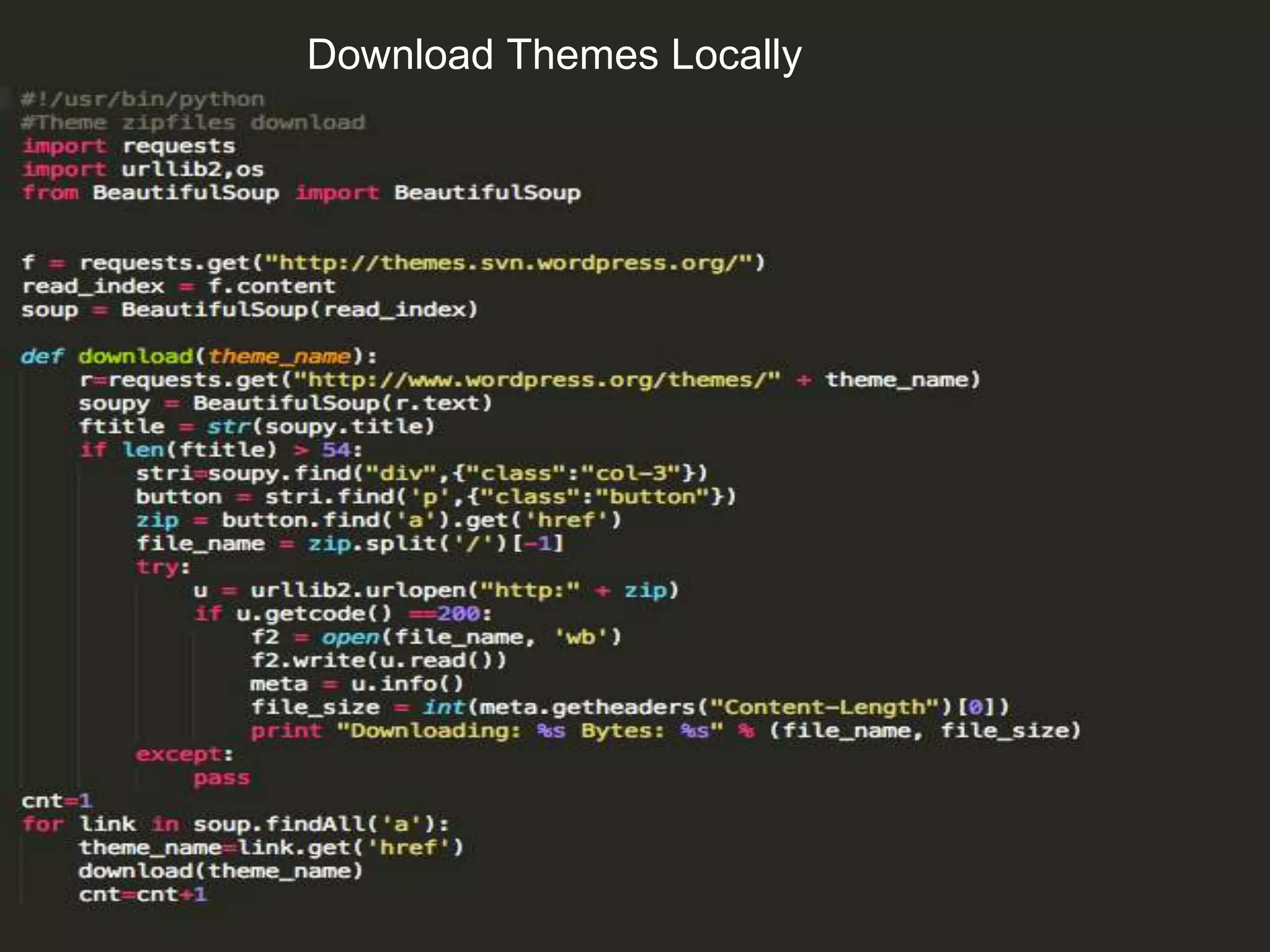
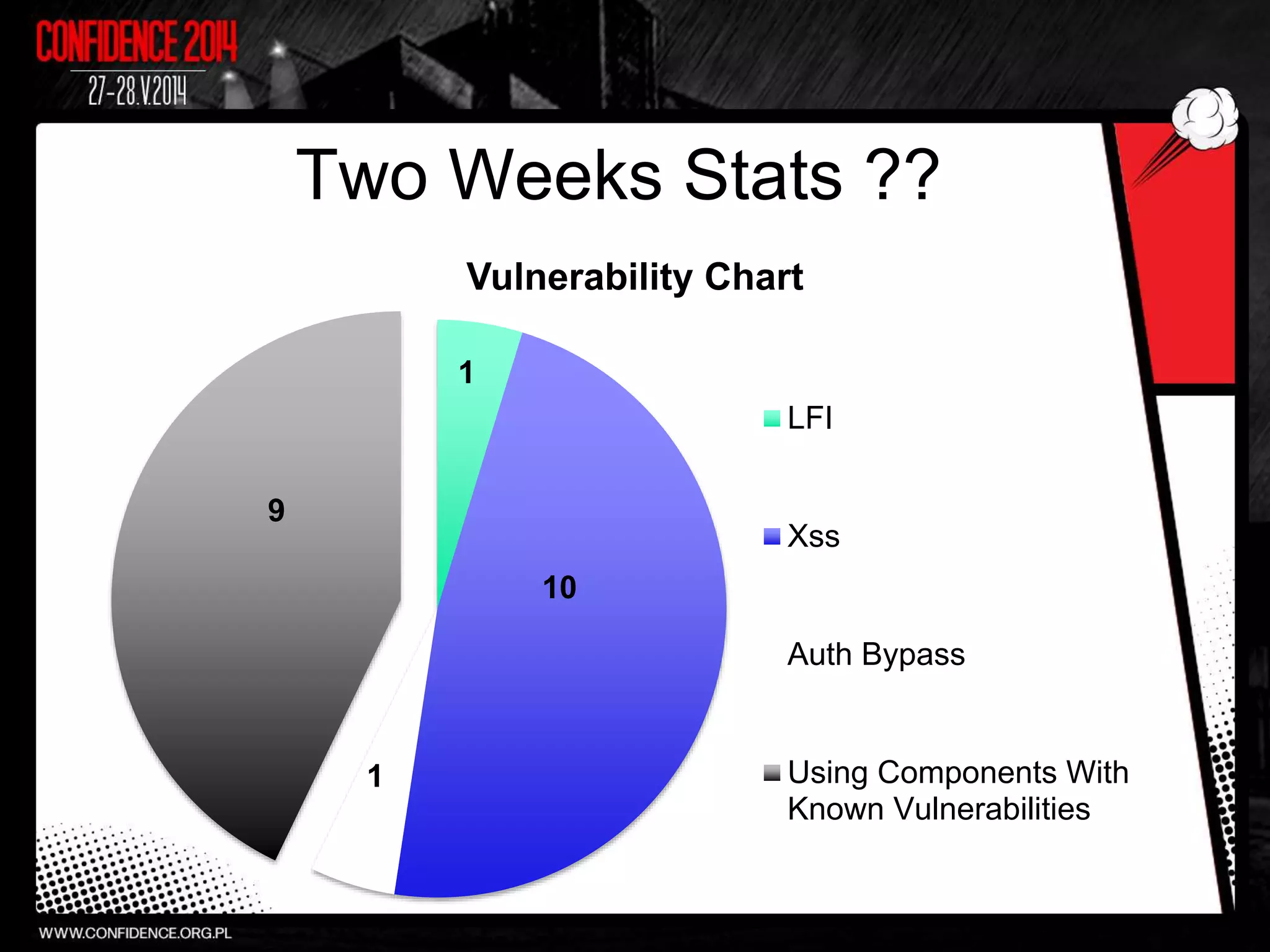
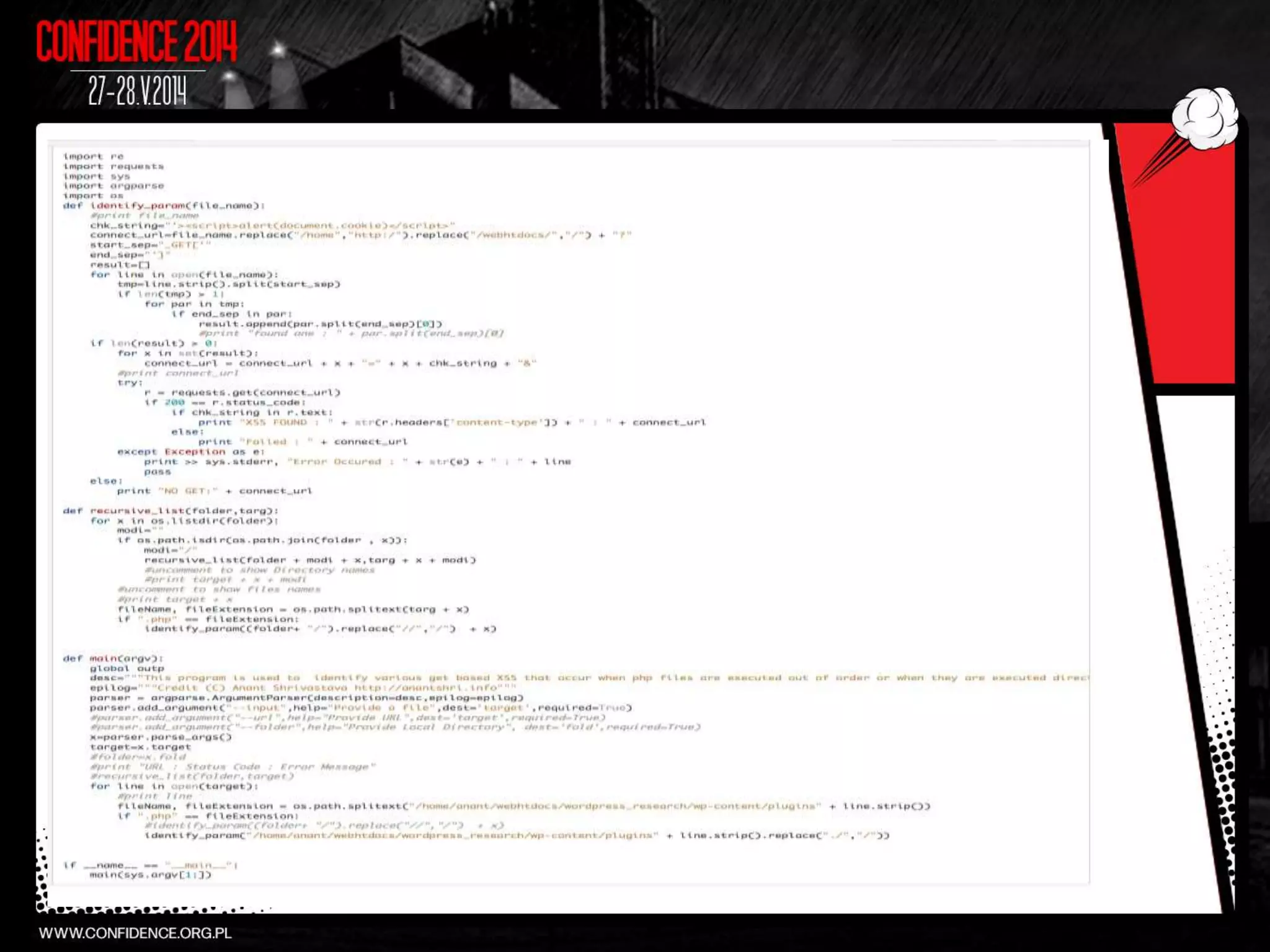
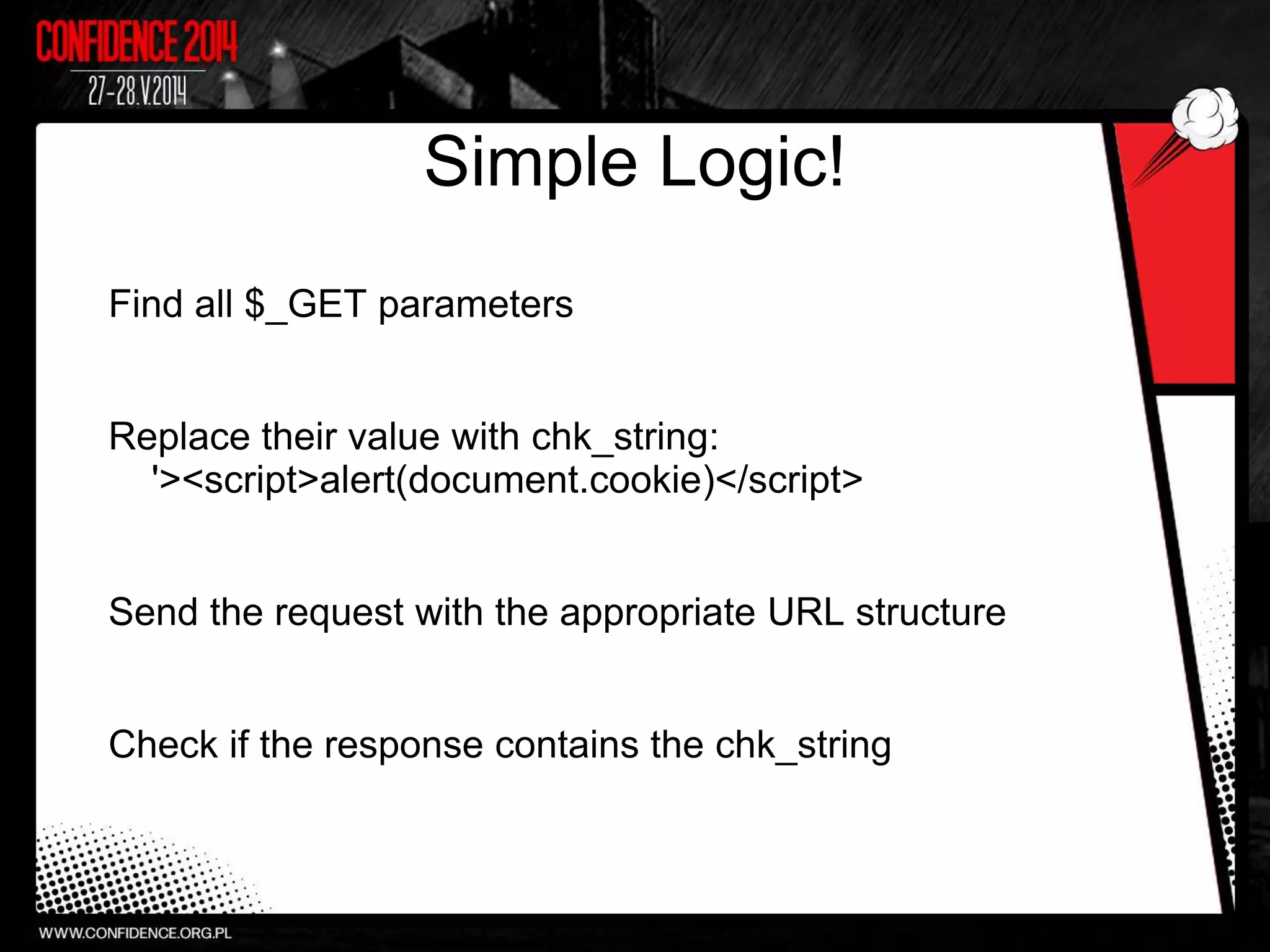
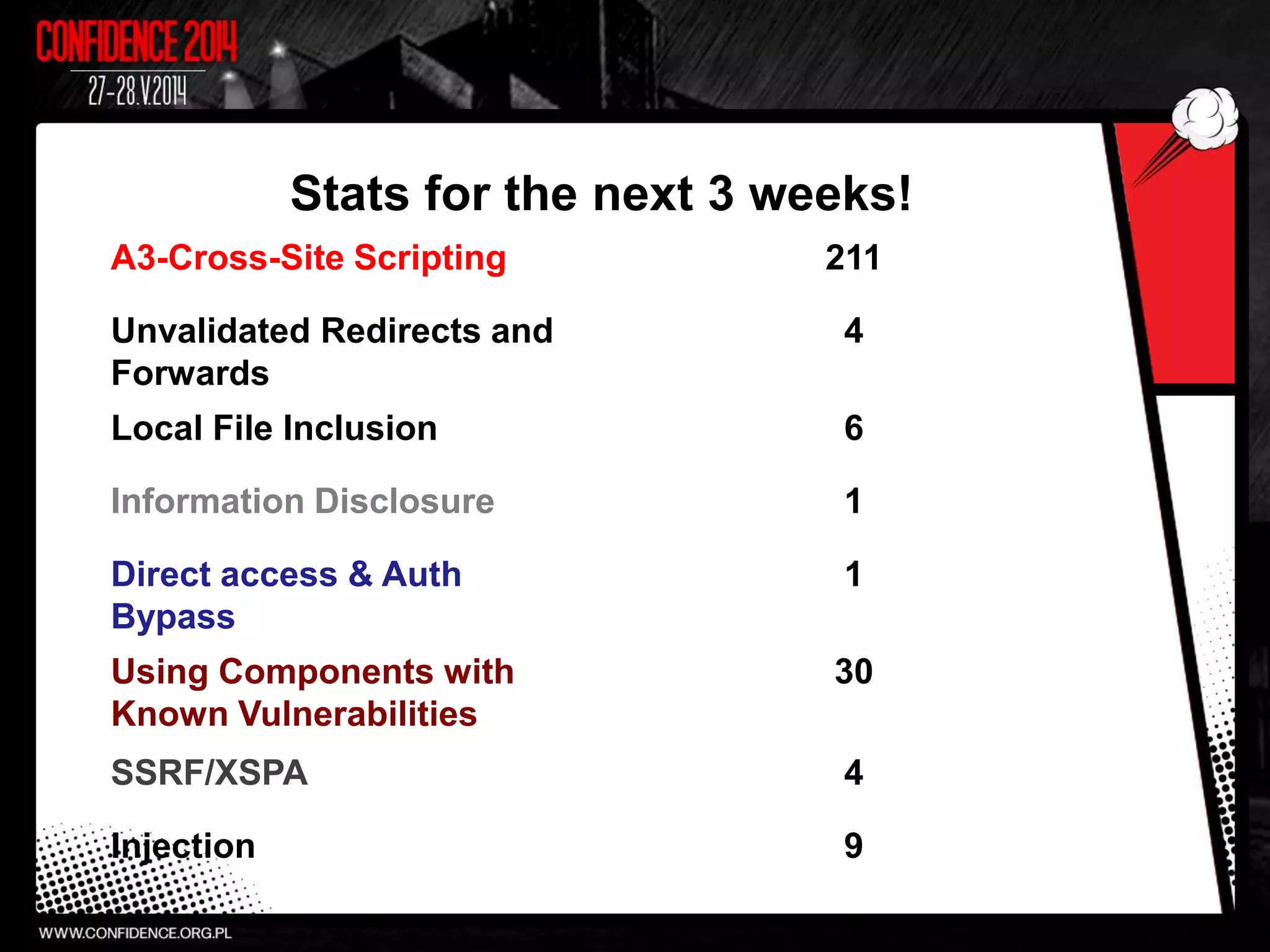
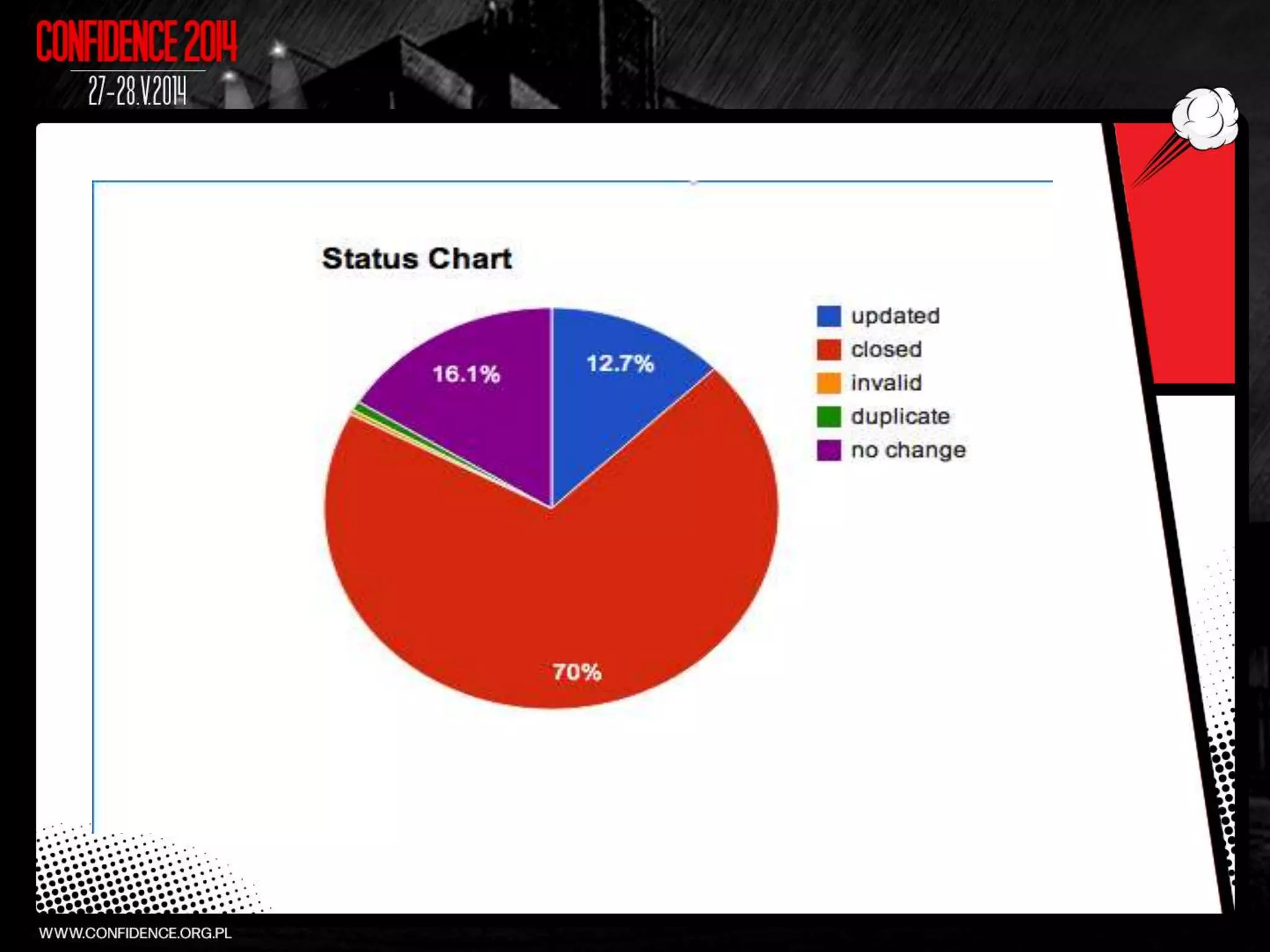
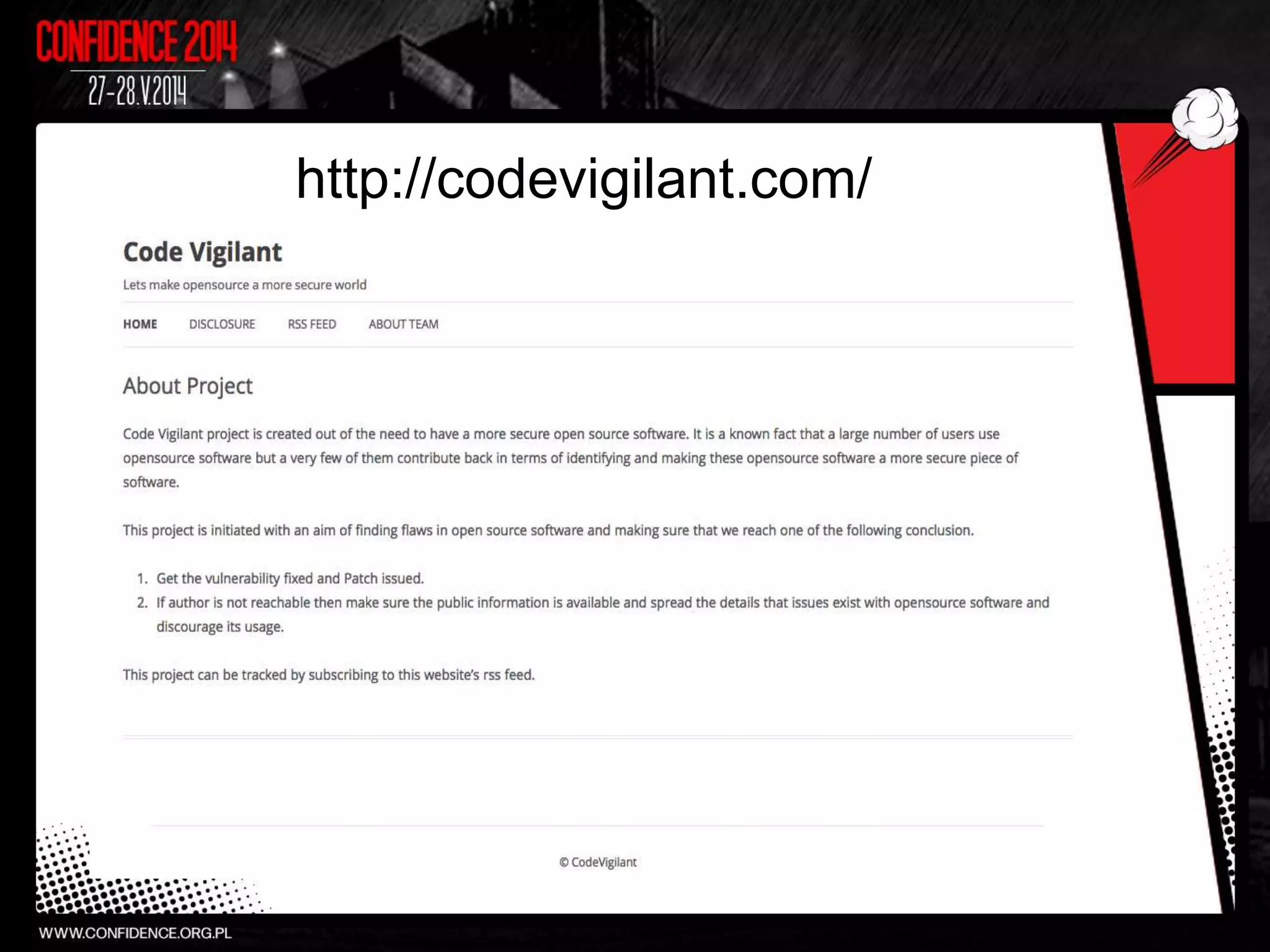
The document summarizes Prajal Kulkarni's project to find security vulnerabilities in the WordPress ecosystem. Over a period of a few months, they found over 100 Common Vulnerabilities and Exposures (CVEs) using both manual and automated techniques. Their automated scanning uncovered many cross-site scripting and file inclusion issues. They reported vulnerabilities to developers and plugin maintainers to get issues patched or plugins removed from repositories. Their goal is to improve WordPress security through their CodeVigilant project.