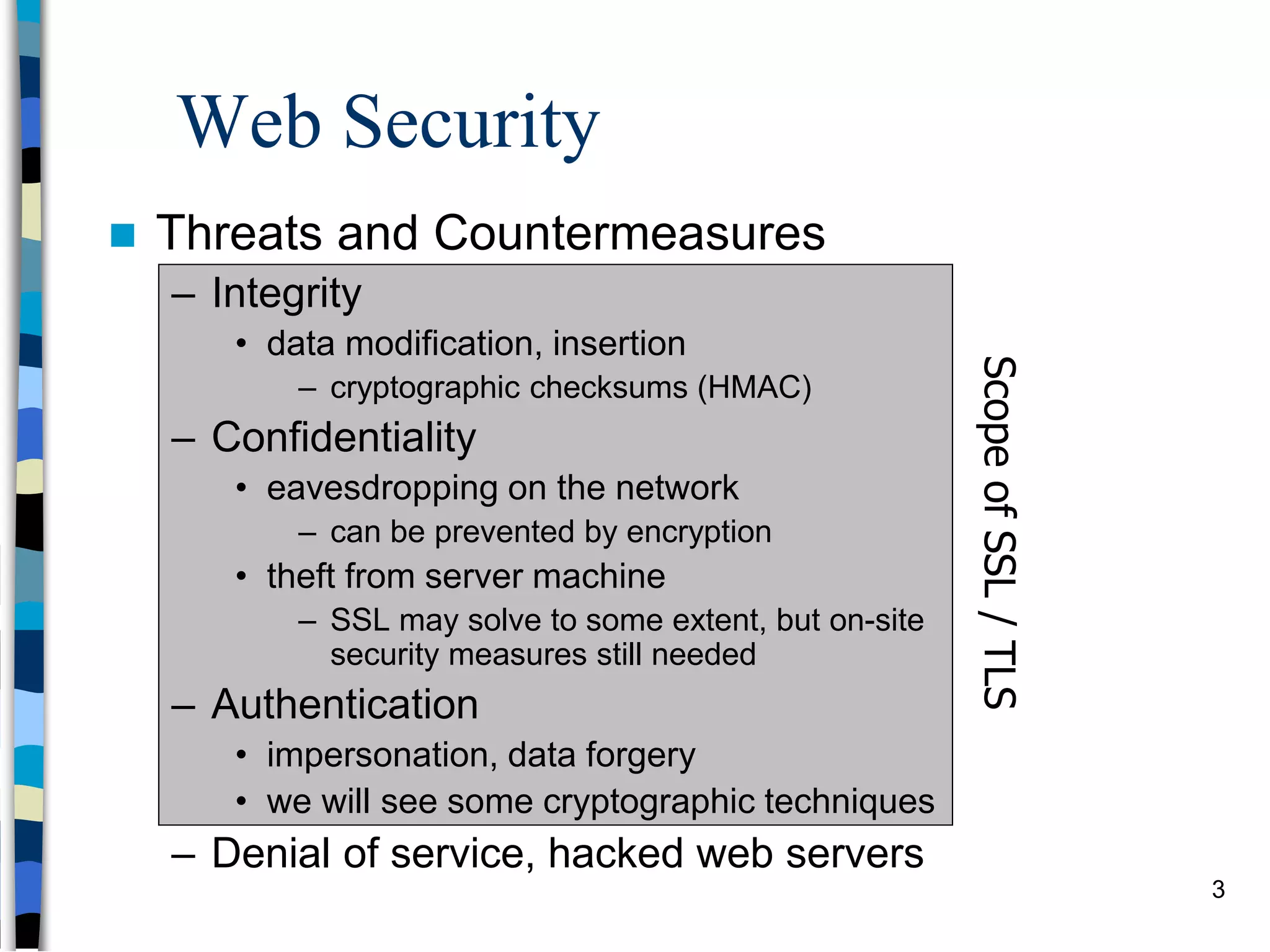
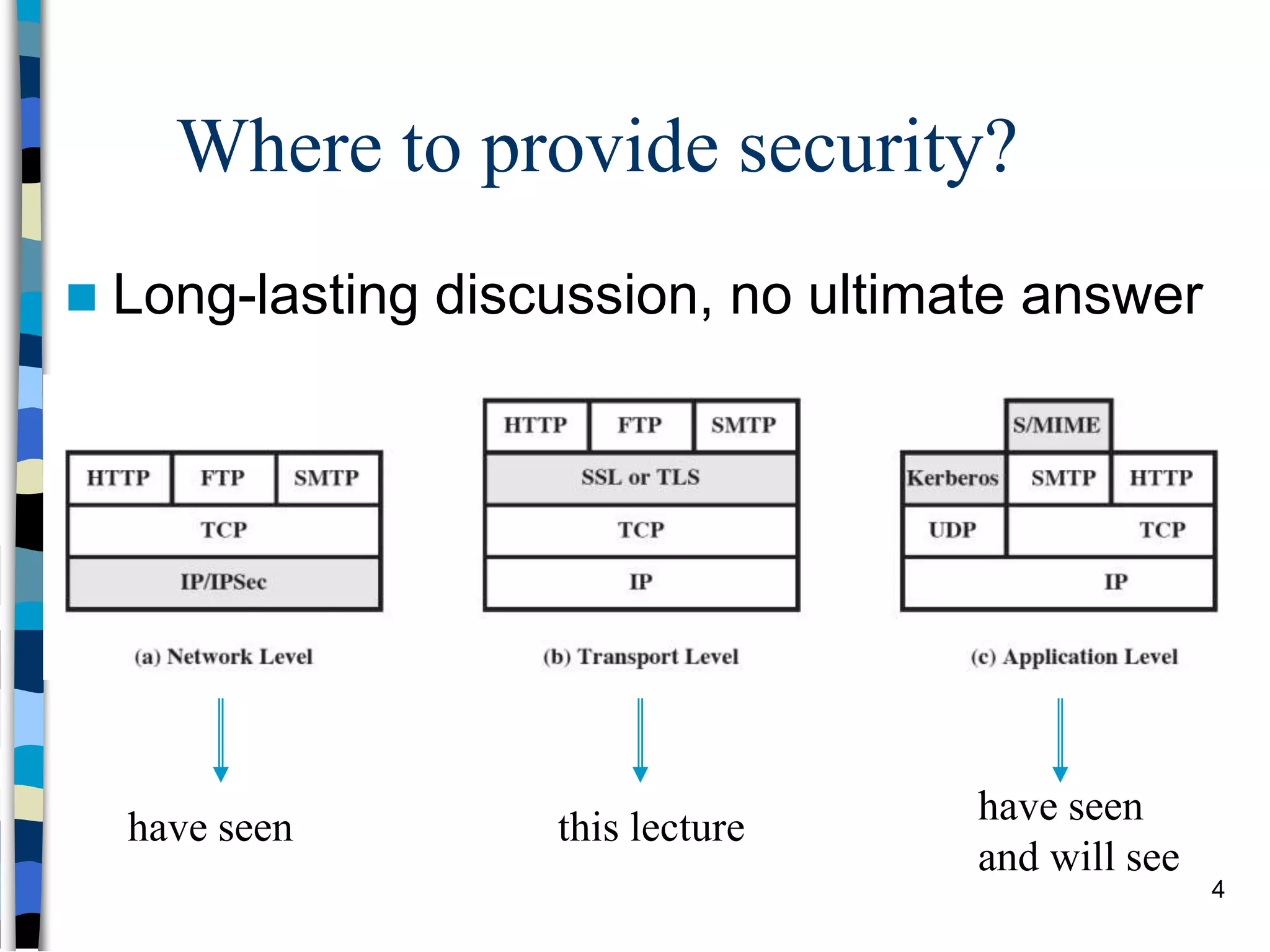
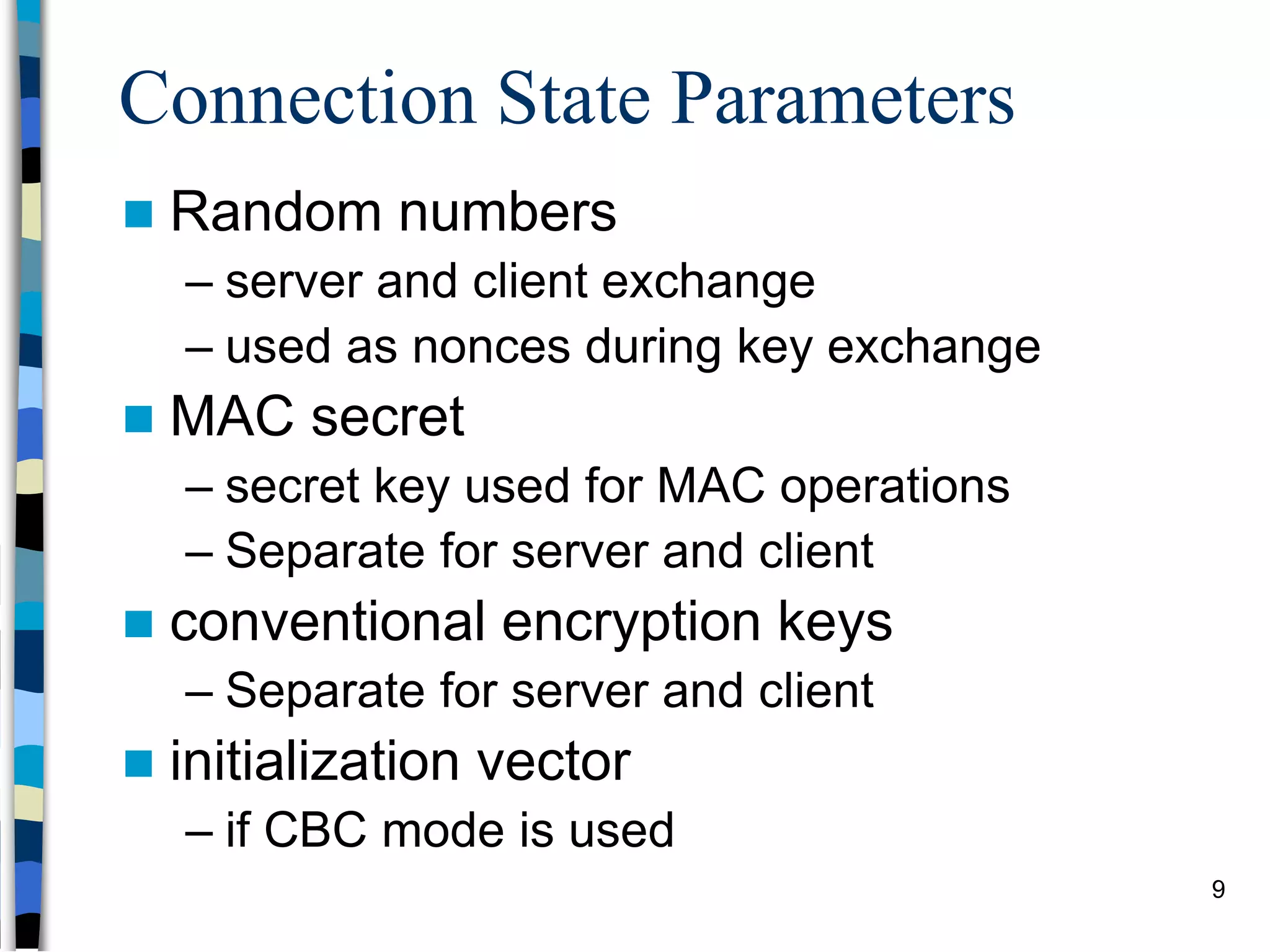
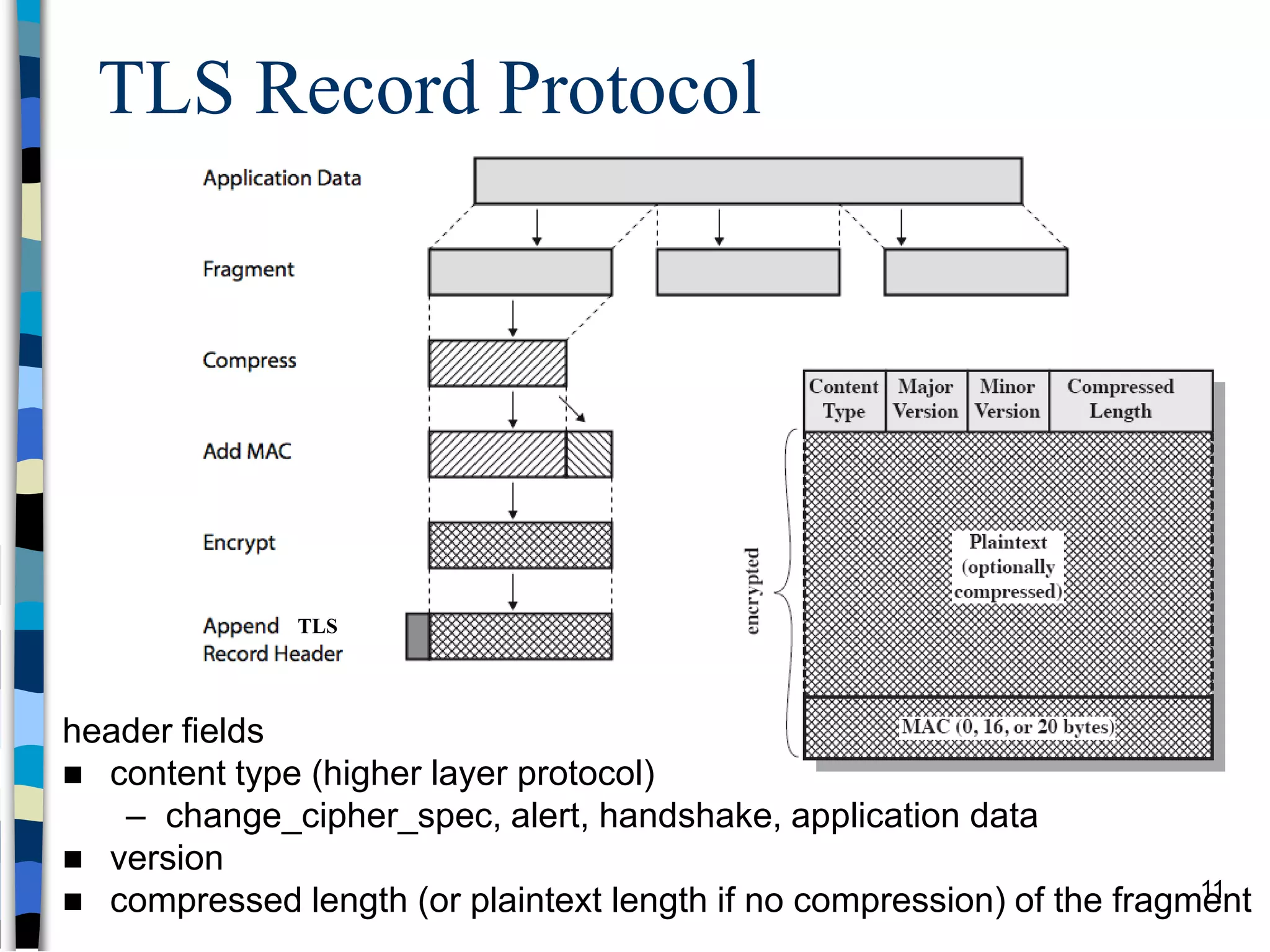
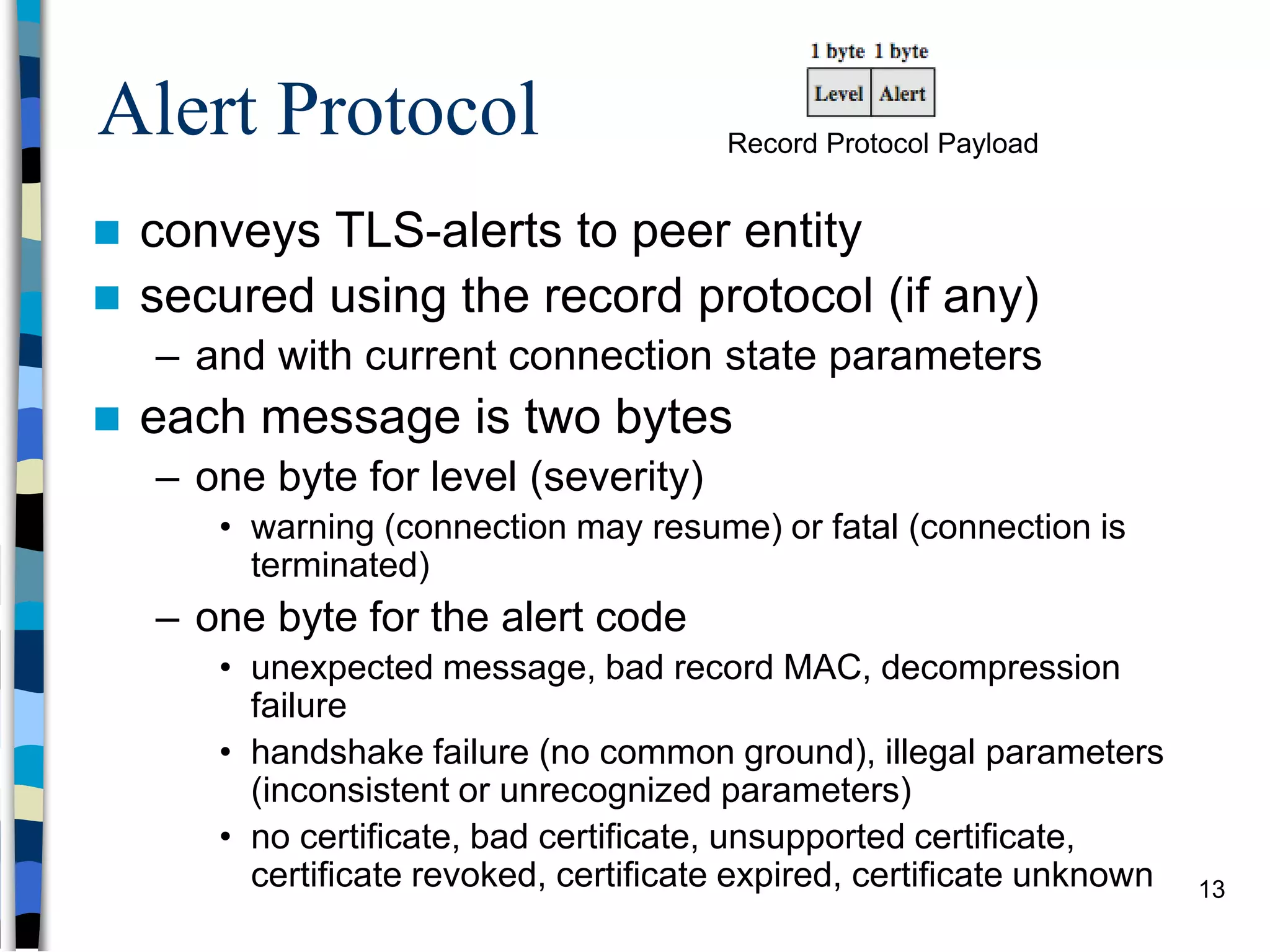
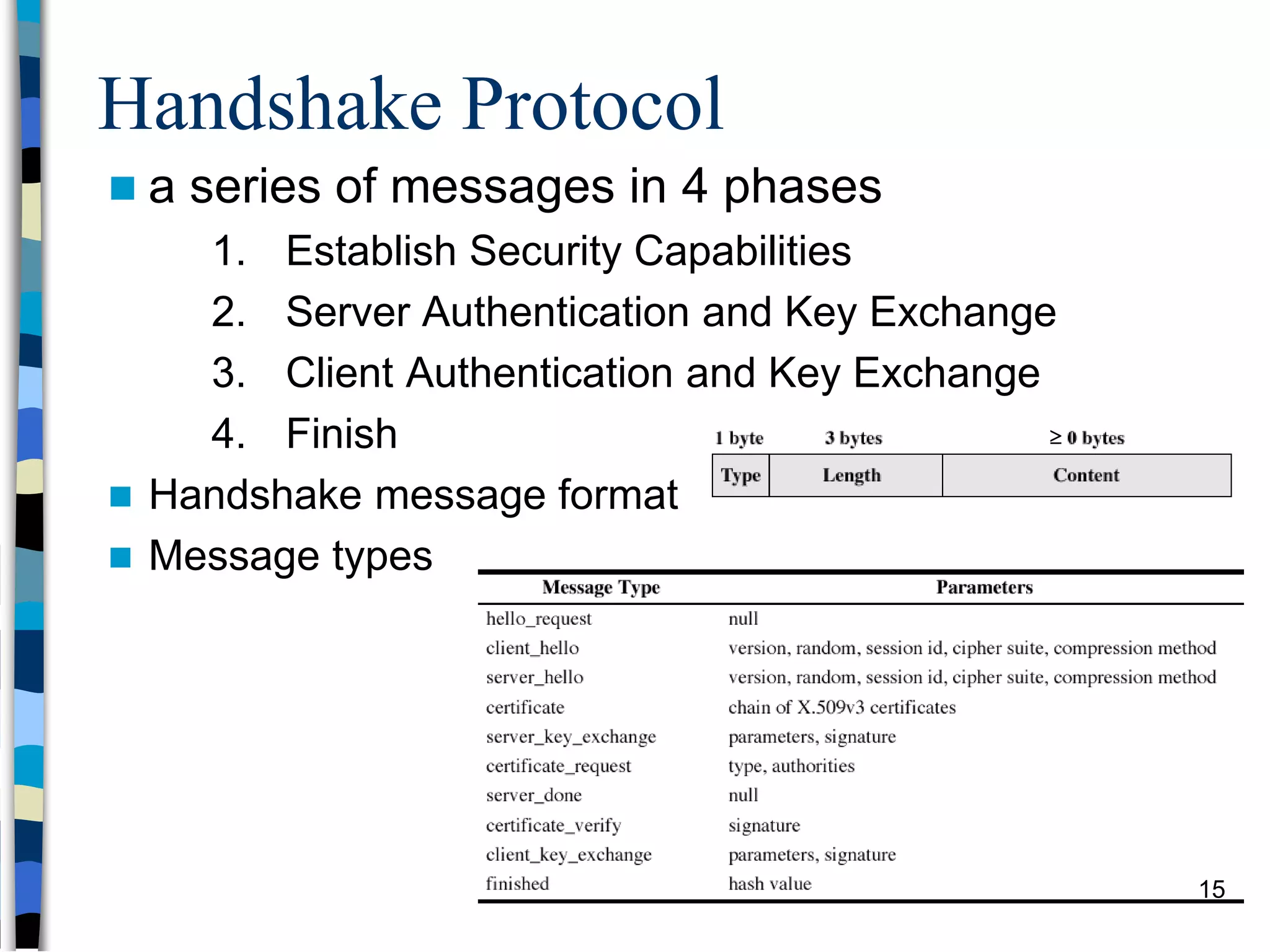
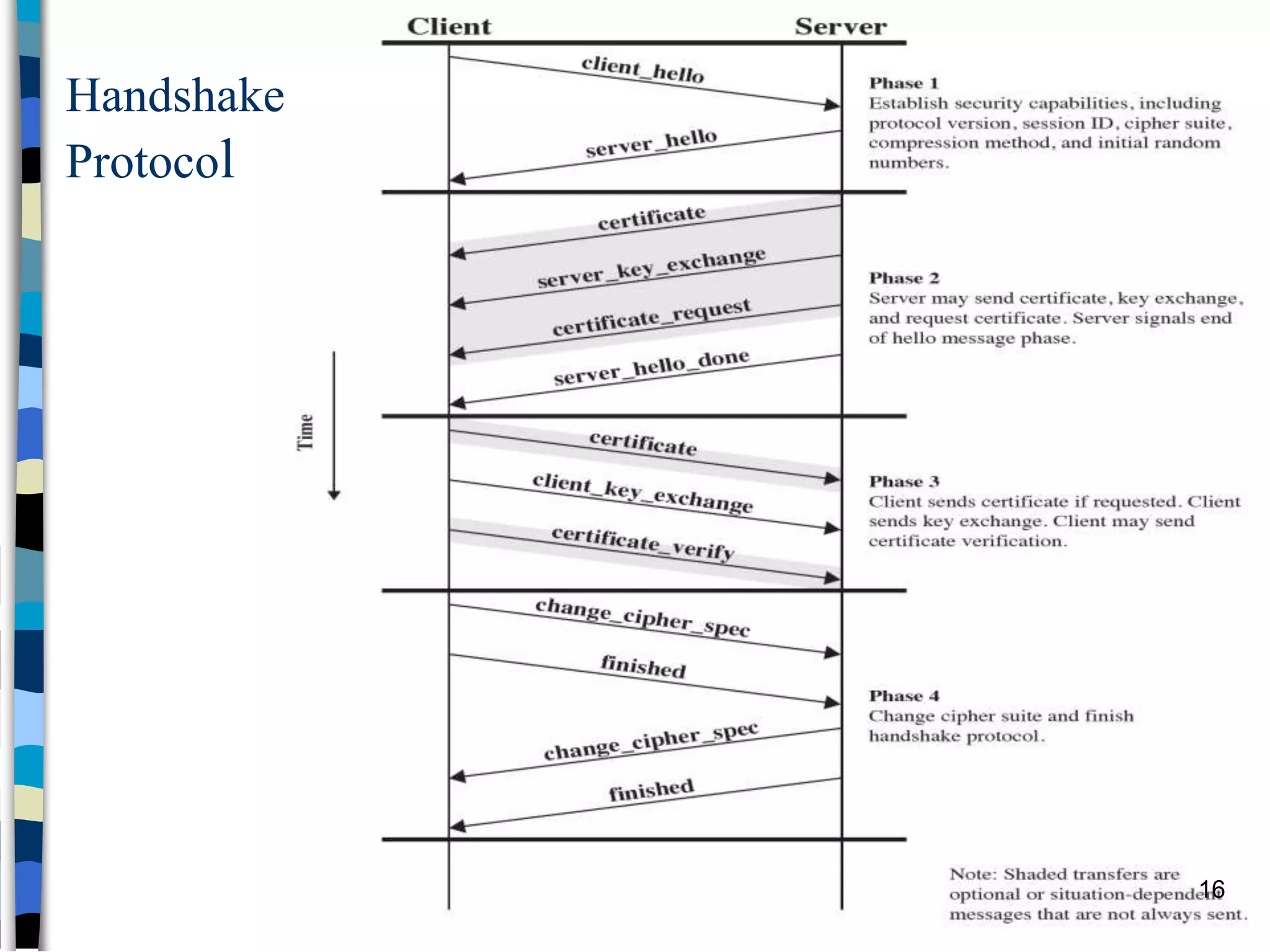
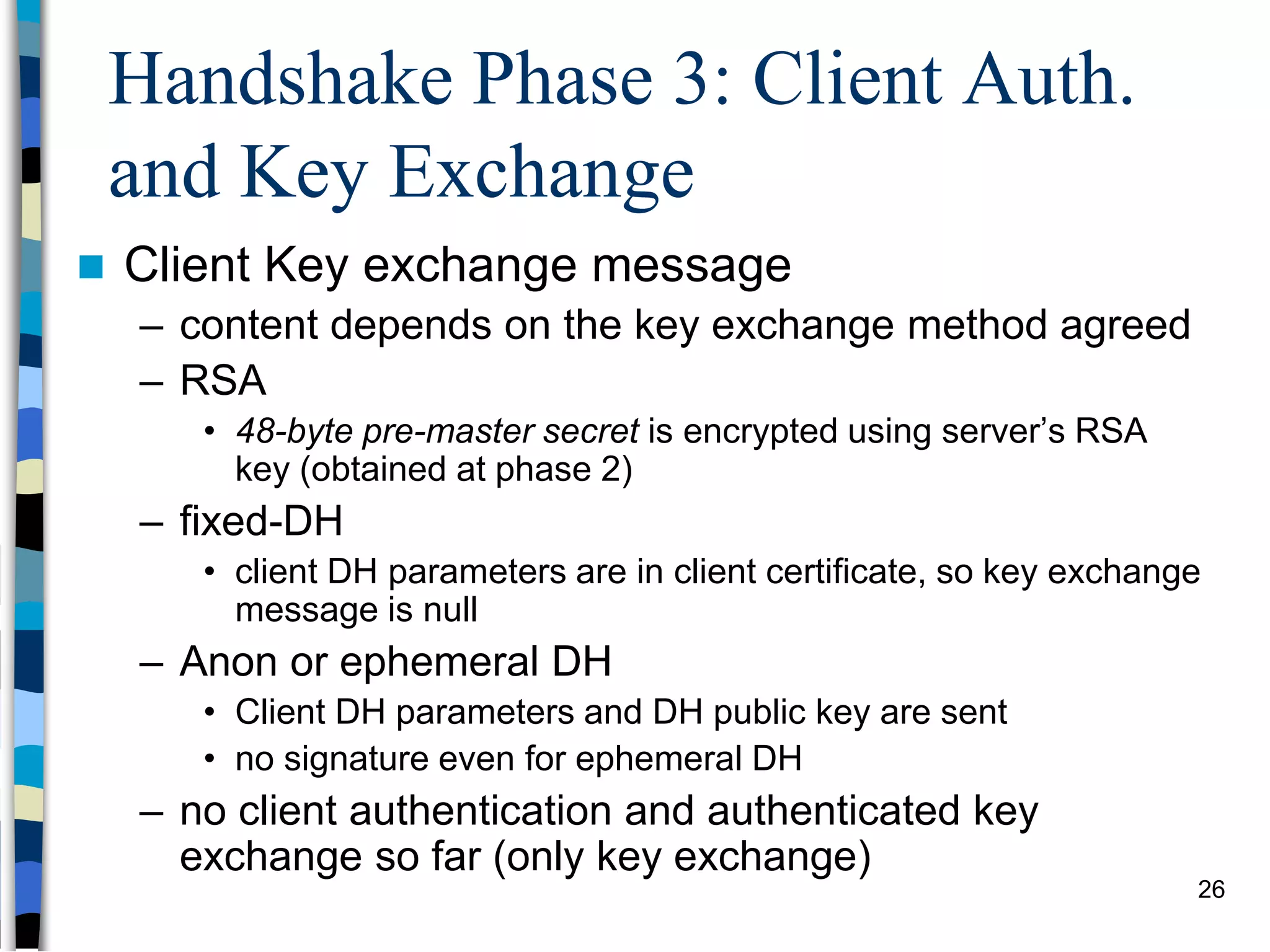
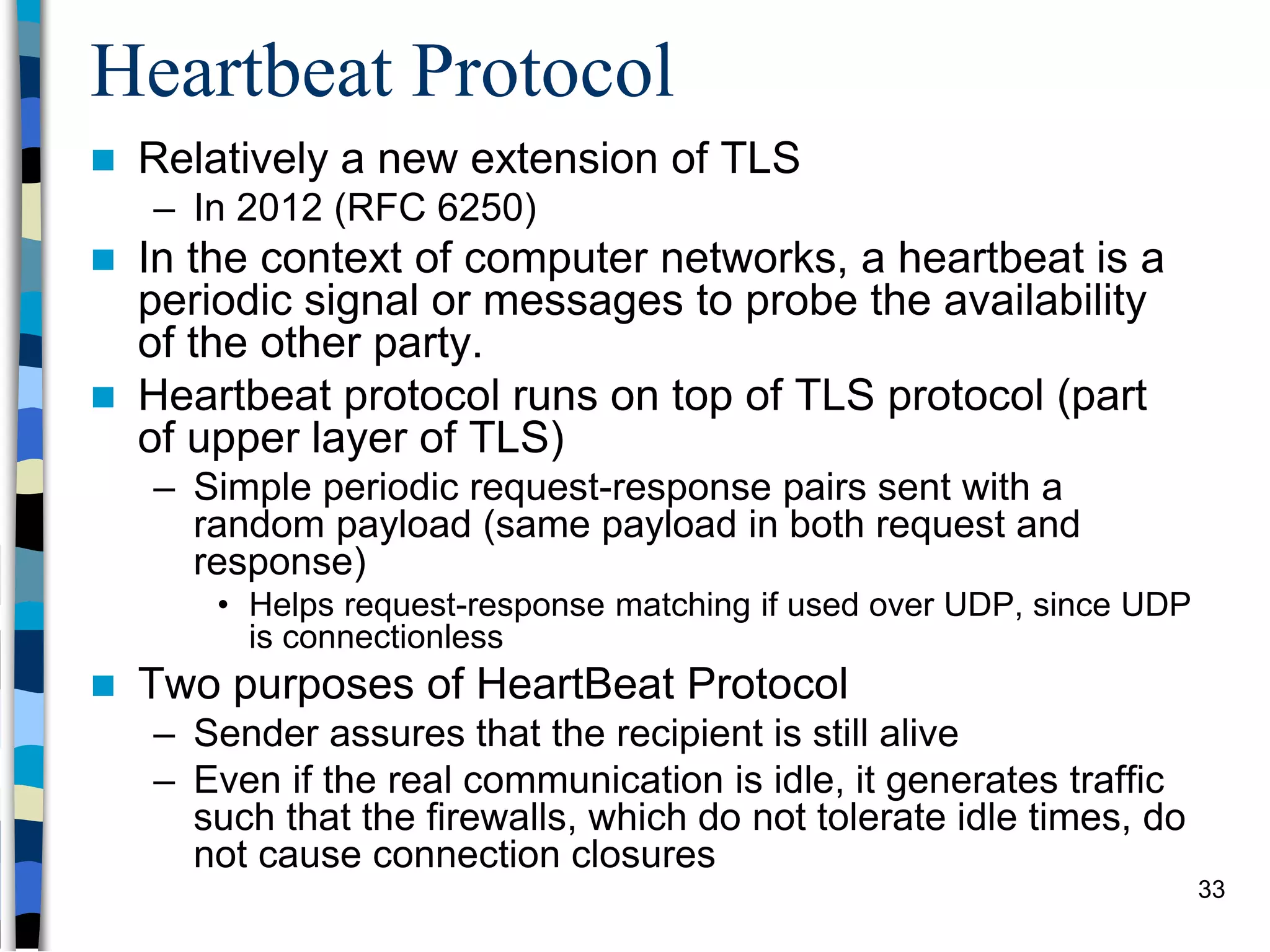
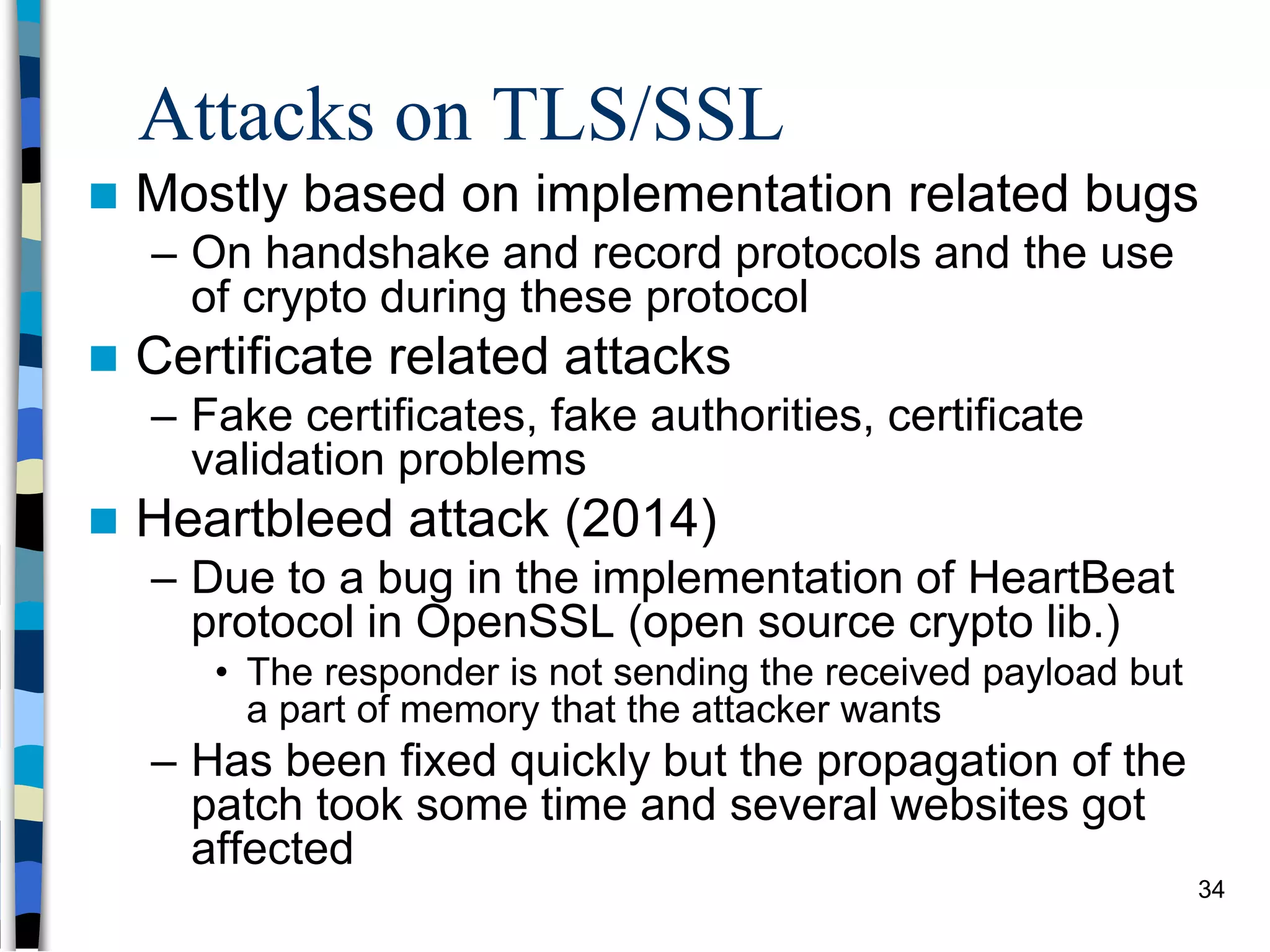
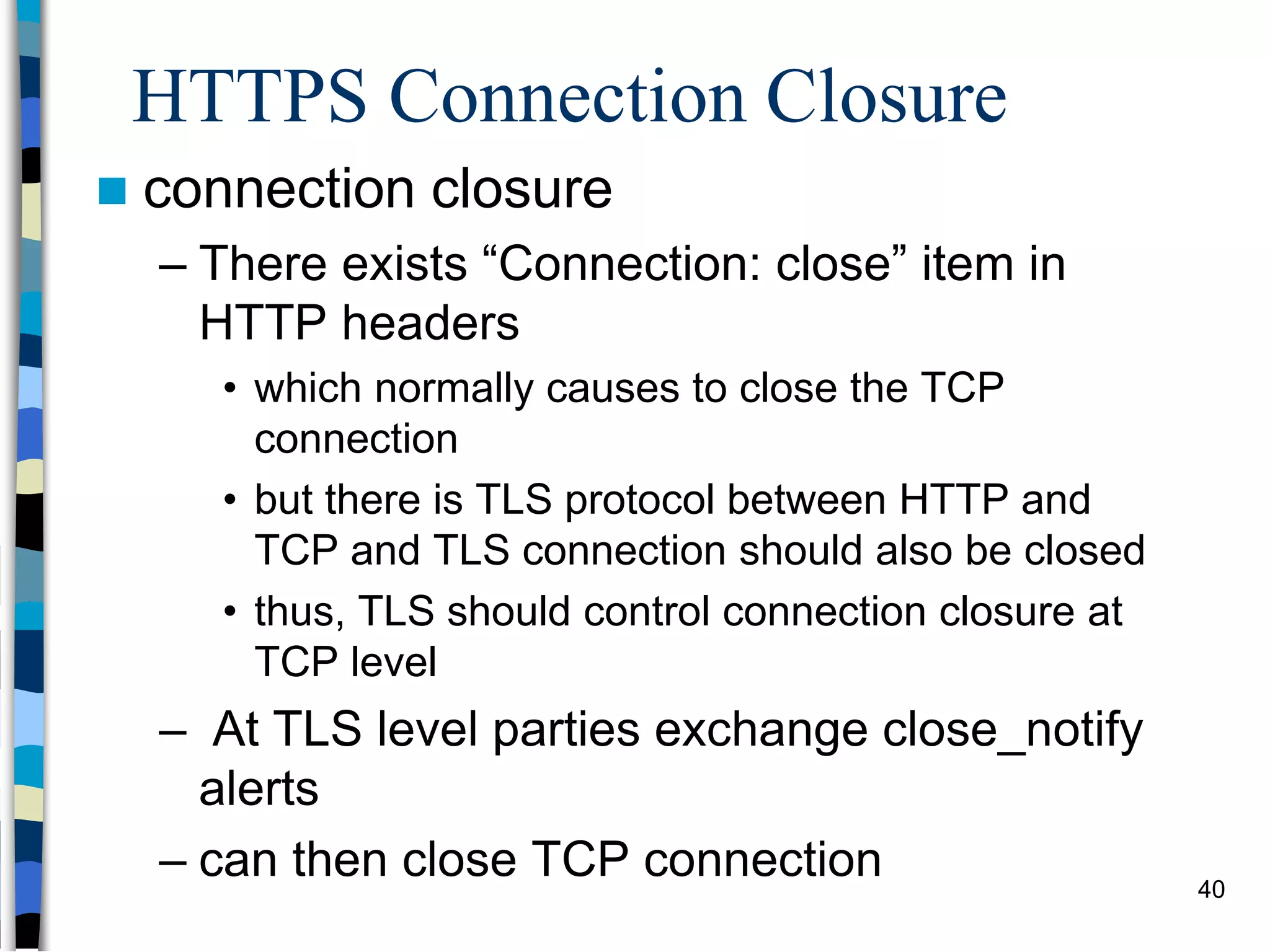
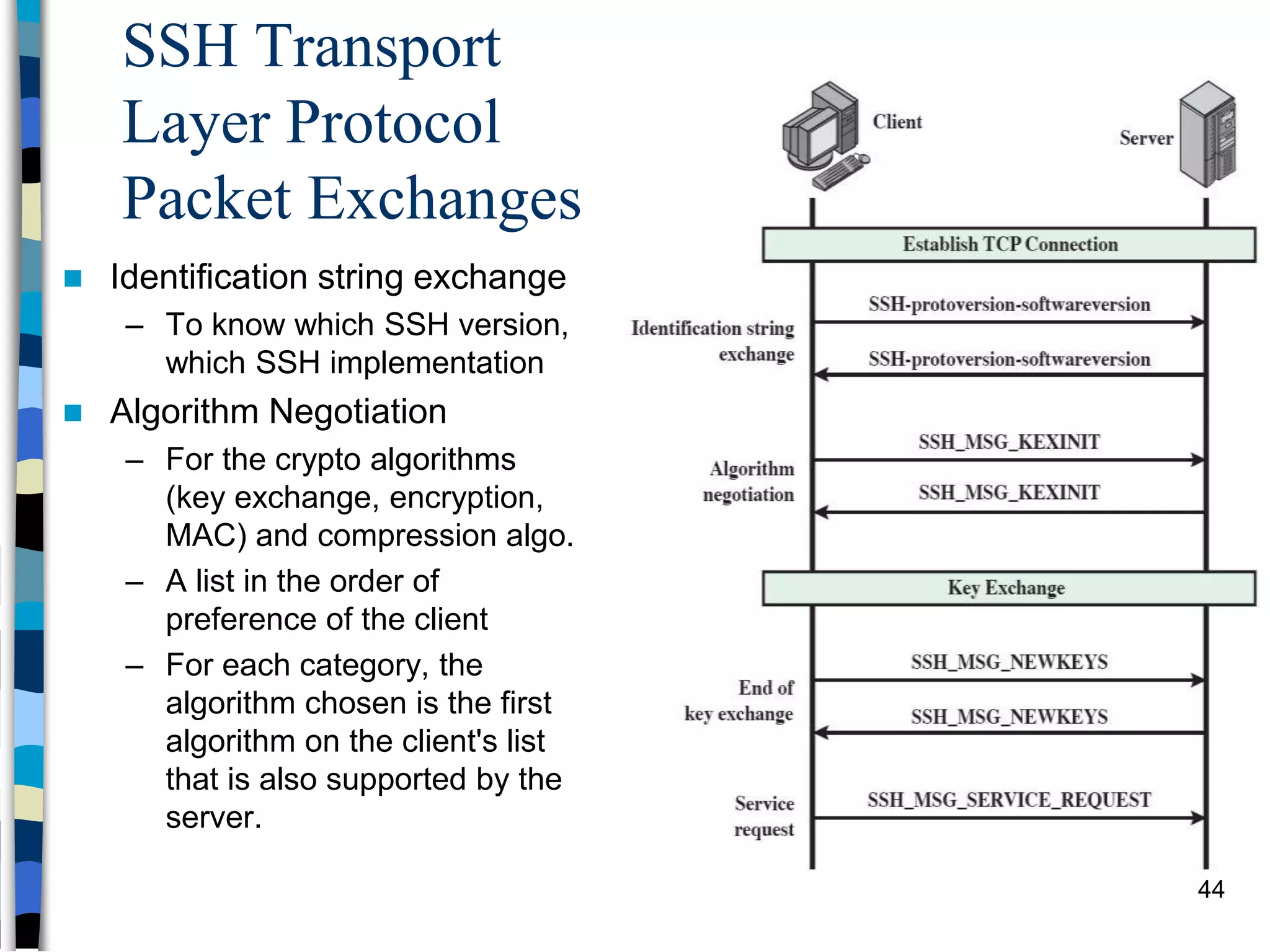
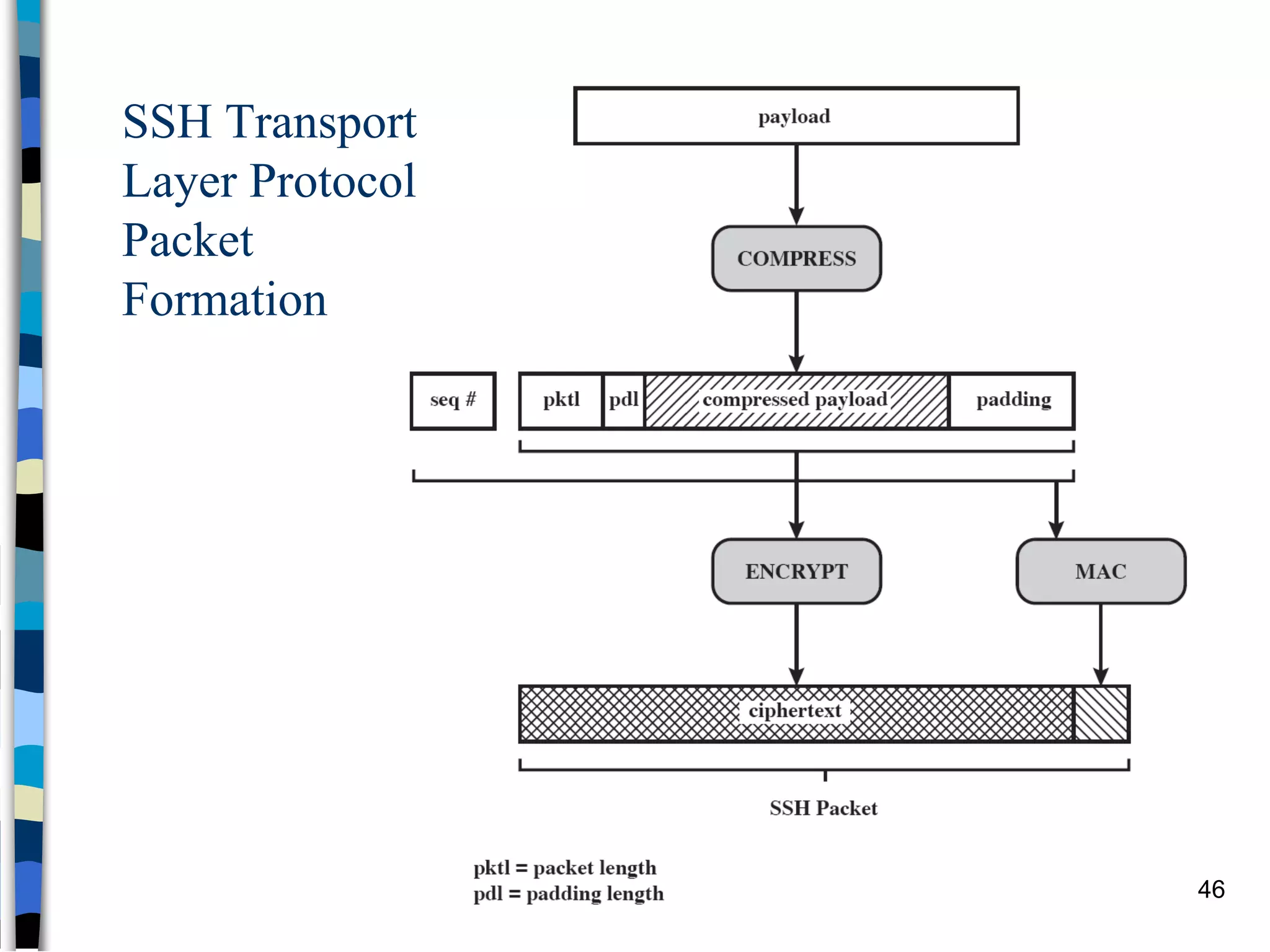
Transport-level and Web Security discusses SSL/TLS and SSH. It provides an overview of how SSL/TLS works to secure HTTP and other TCP/IP protocols. The document describes the TLS protocol stack and how TLS sessions and connections are established. It explains the TLS handshake protocol in detail, including the four phases to establish a secure session and connection. Key topics covered include cipher suites, certificates, and how cryptographic keys are derived. Common attacks on TLS/SSL implementations are also summarized.