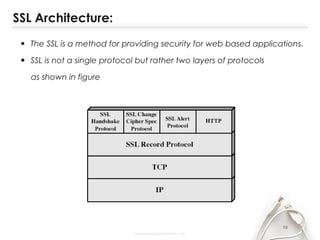
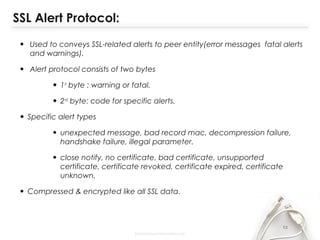
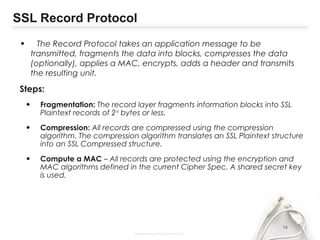
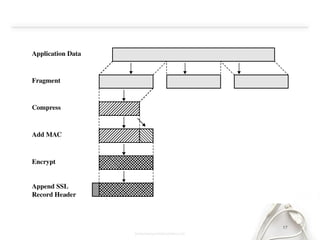
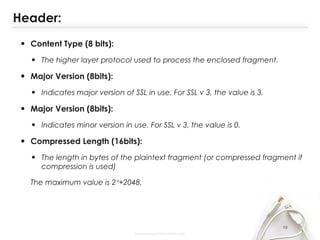
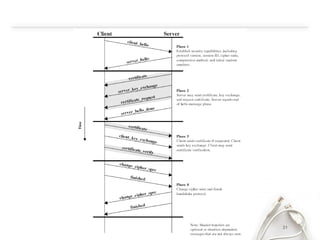
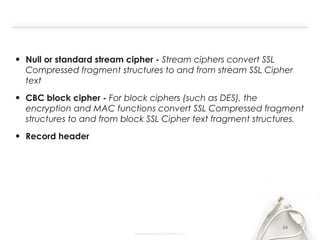
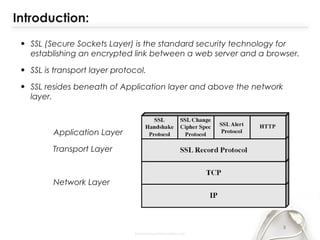
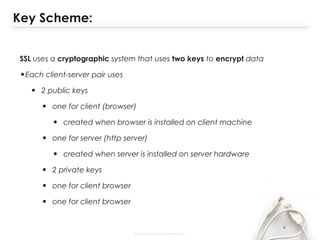
- The document discusses SSL (Secure Sockets Layer), which is a standard security technology for establishing an encrypted link between a web server and browser. It provides key details on SSL including its architecture, protocols (SSL Record and Handshake), certificates, encryption, and history/development. SSL uses public/private keys to encrypt data during transmission and provides authentication and security for web applications.



![6My Presentation
History and Development:
• TLS 1.0
• The Internet Engineering Task Force (IETF) began work to
develop a standard protocol that provided the same
functionality [as SSL]. They used SSL 3.0 as the basis for that
work, which became the TLS protocol in
• IETF develop TLS 1.0 in January 1999 was defined in RFC
2246.
• TLS 1.1 was defined in RFC 2346 in April 2006.
• TLS 1.2 was defined in RFC 5246 in August 2008.](https://image.slidesharecdn.com/securesocketlater-140611121732-phpapp02/85/Secure-socket-later-6-320.jpg)