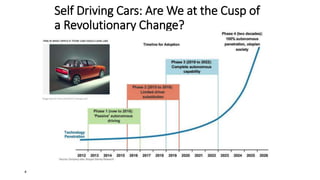
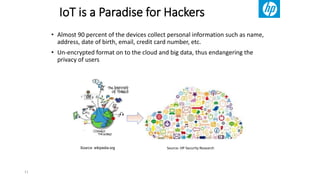
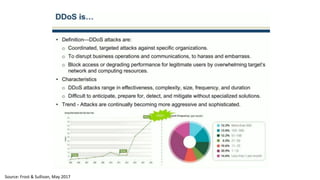
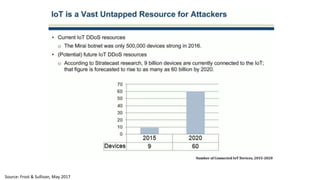
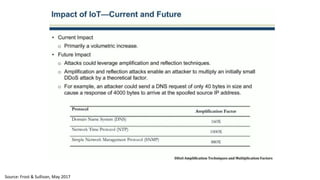
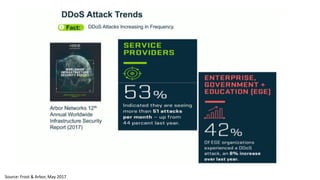
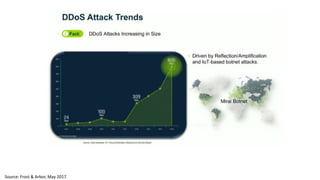
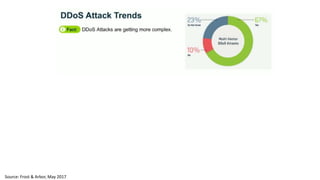
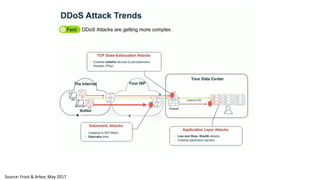
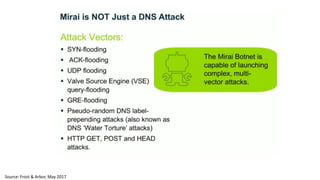
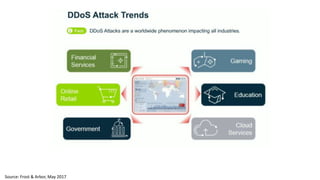
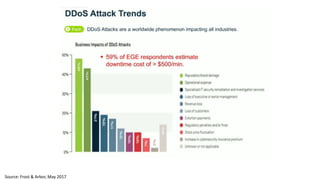
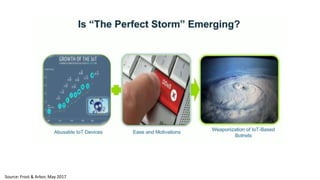
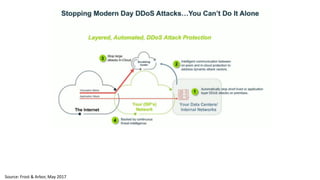
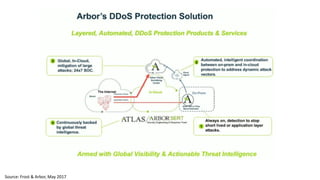
The document discusses the growth of the internet of things and connected devices. It notes that by 2018, digital business will require fewer workers but more digital jobs, and the cost of business operations will be reduced by 30% through automation. It also discusses new technologies like smart homes, wearables, and connected medical devices. However, the widespread connectivity of devices introduces new security threats, as many devices have poor security and collect personal data without encryption. The document calls for more robust security measures to protect the growing internet of things.