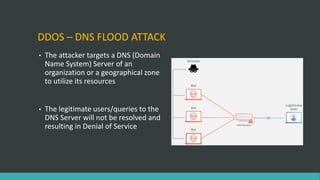
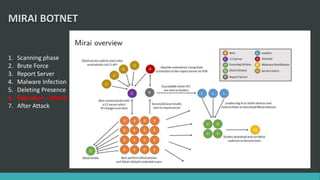
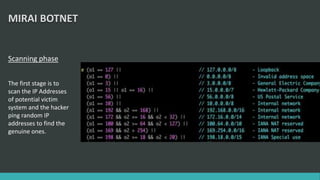
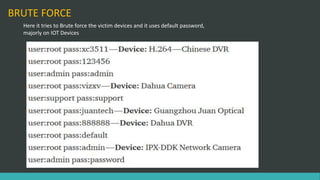
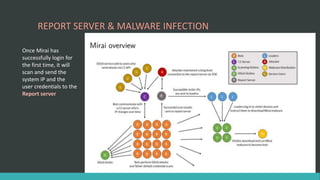
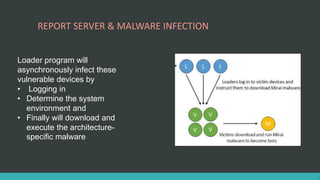
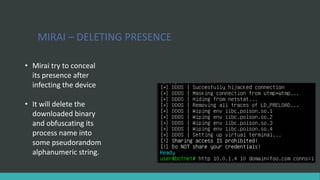
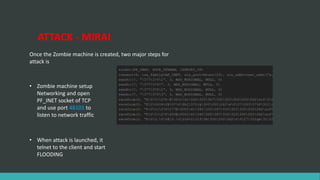
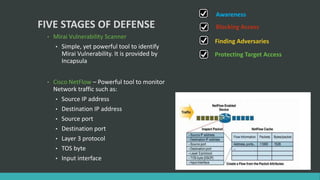
This document discusses DNS flood DDoS attacks and the Mirai botnet. It provides details on how Mirai infects devices, launches attacks, and then conceals its presence. It also outlines five stages of defense against Mirai: awareness, blocking access, finding adversaries, protecting target access, and mitigation plans like vulnerability scanning and traffic monitoring.