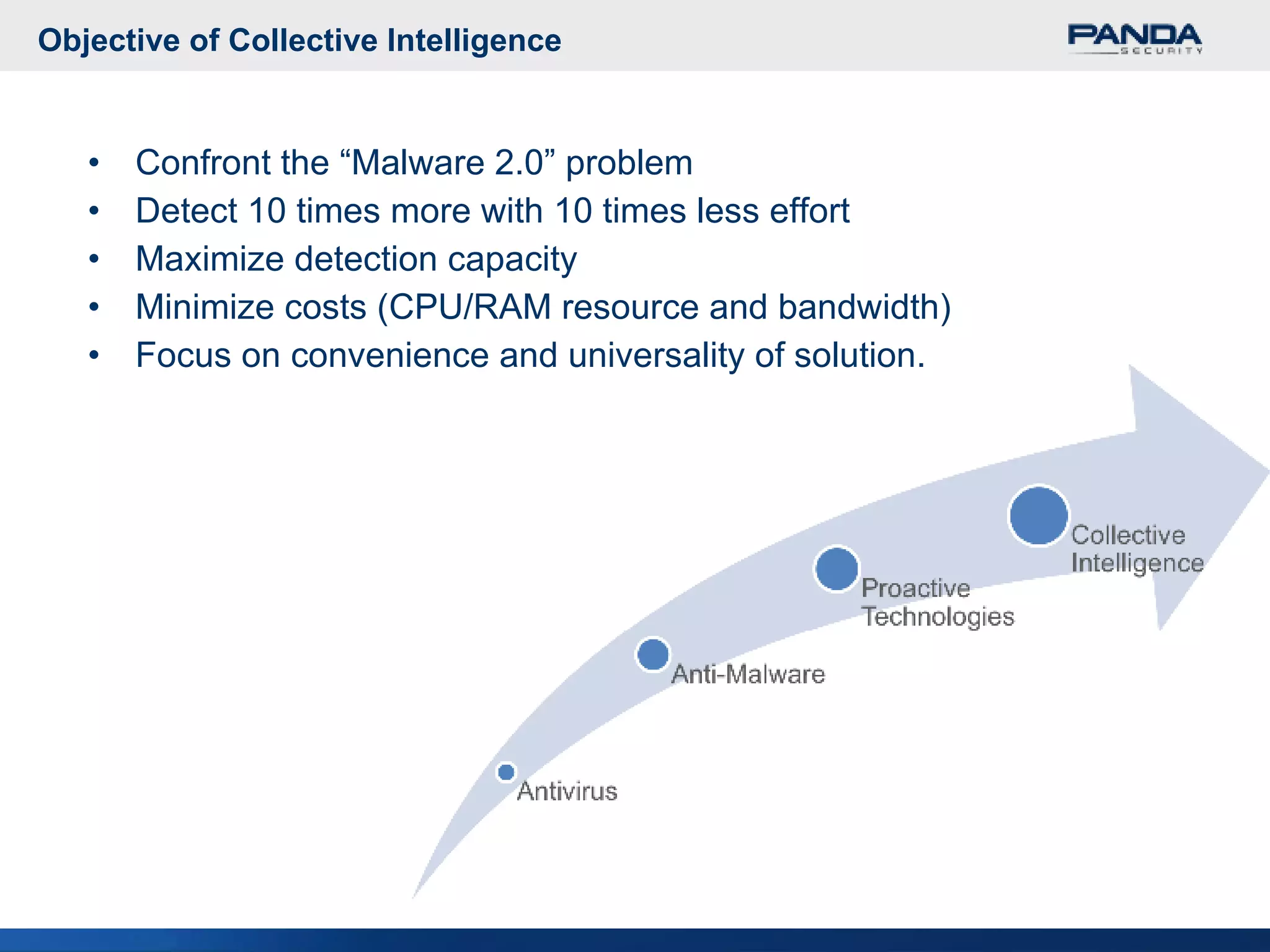
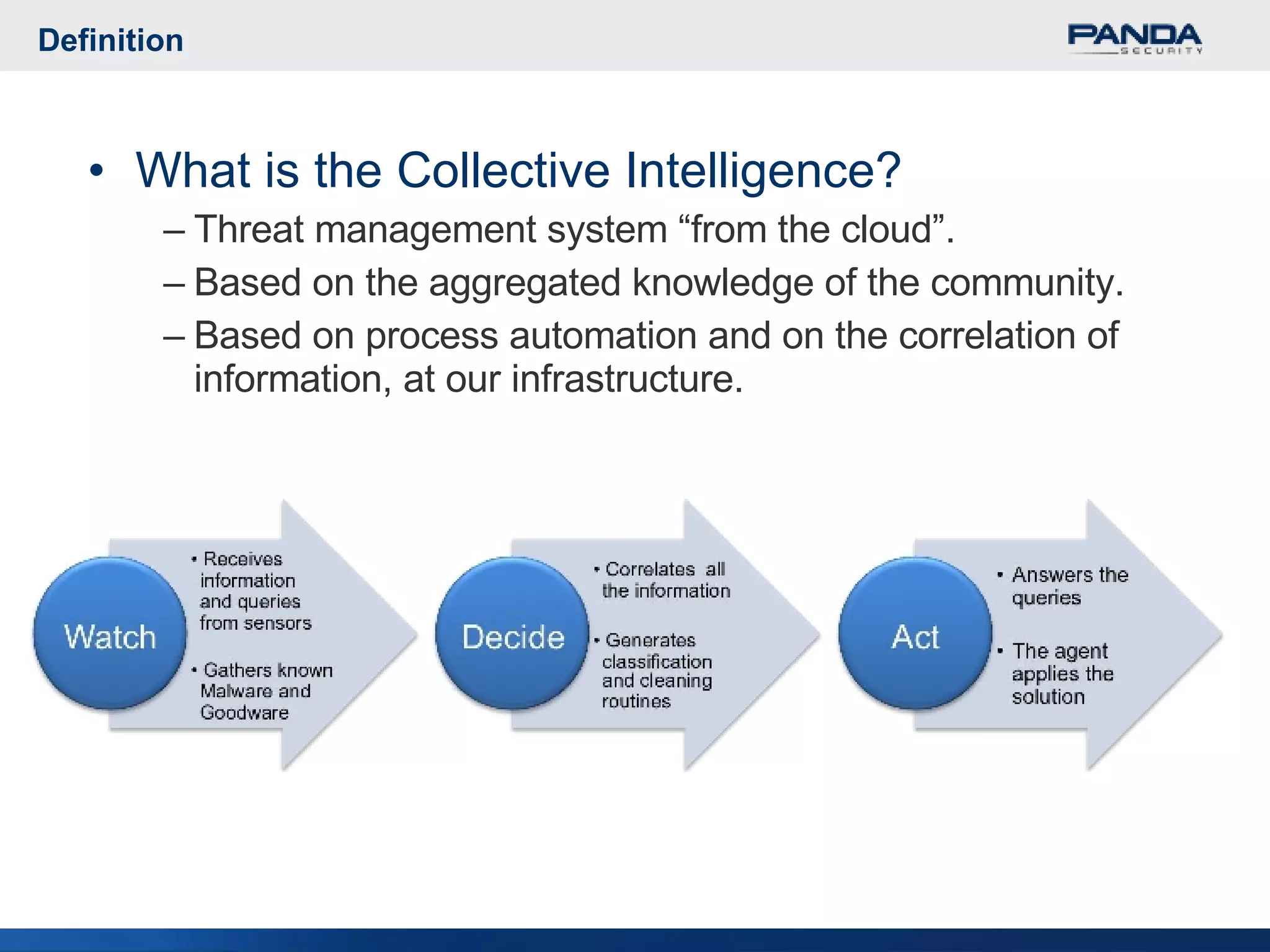
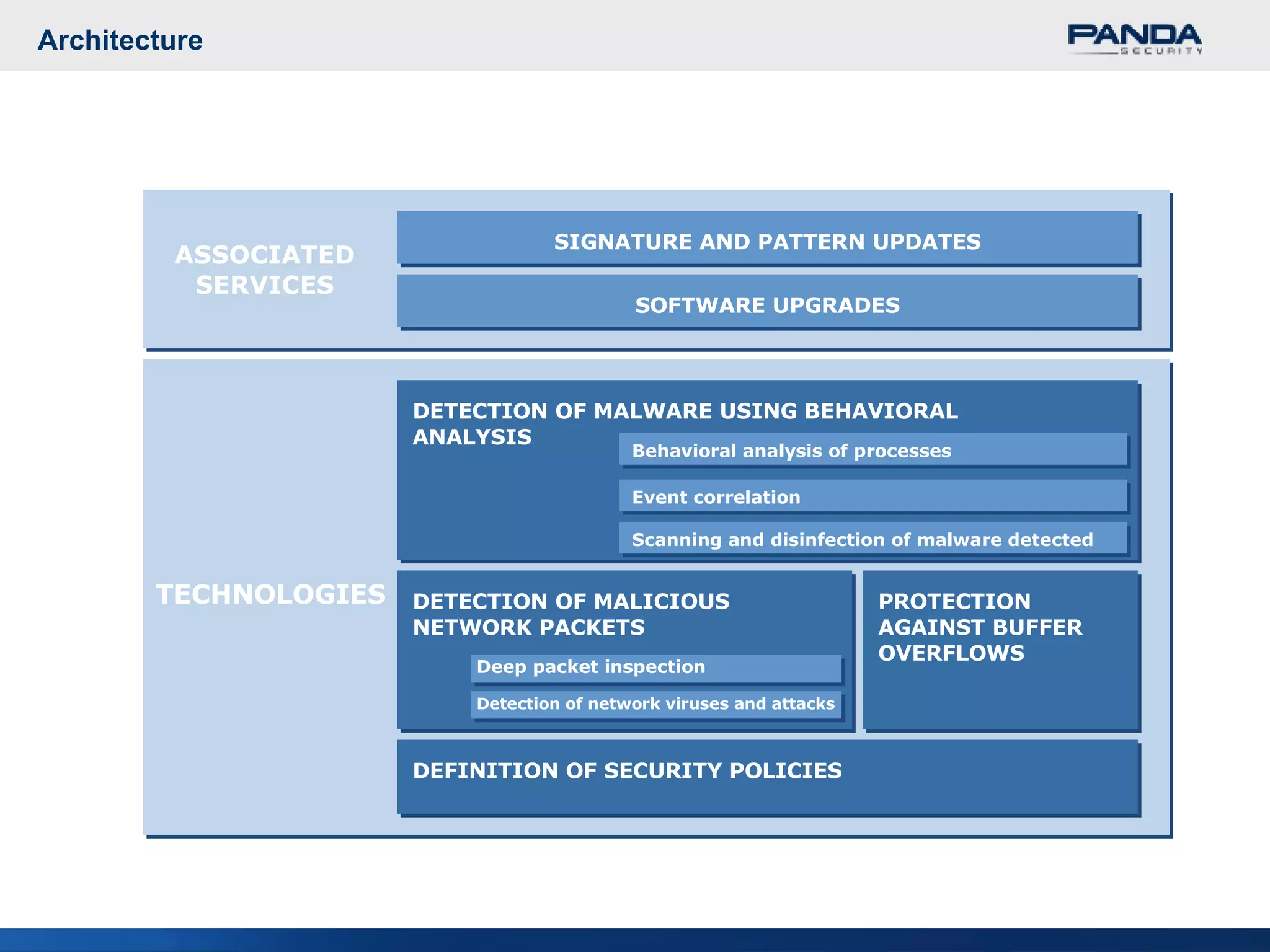
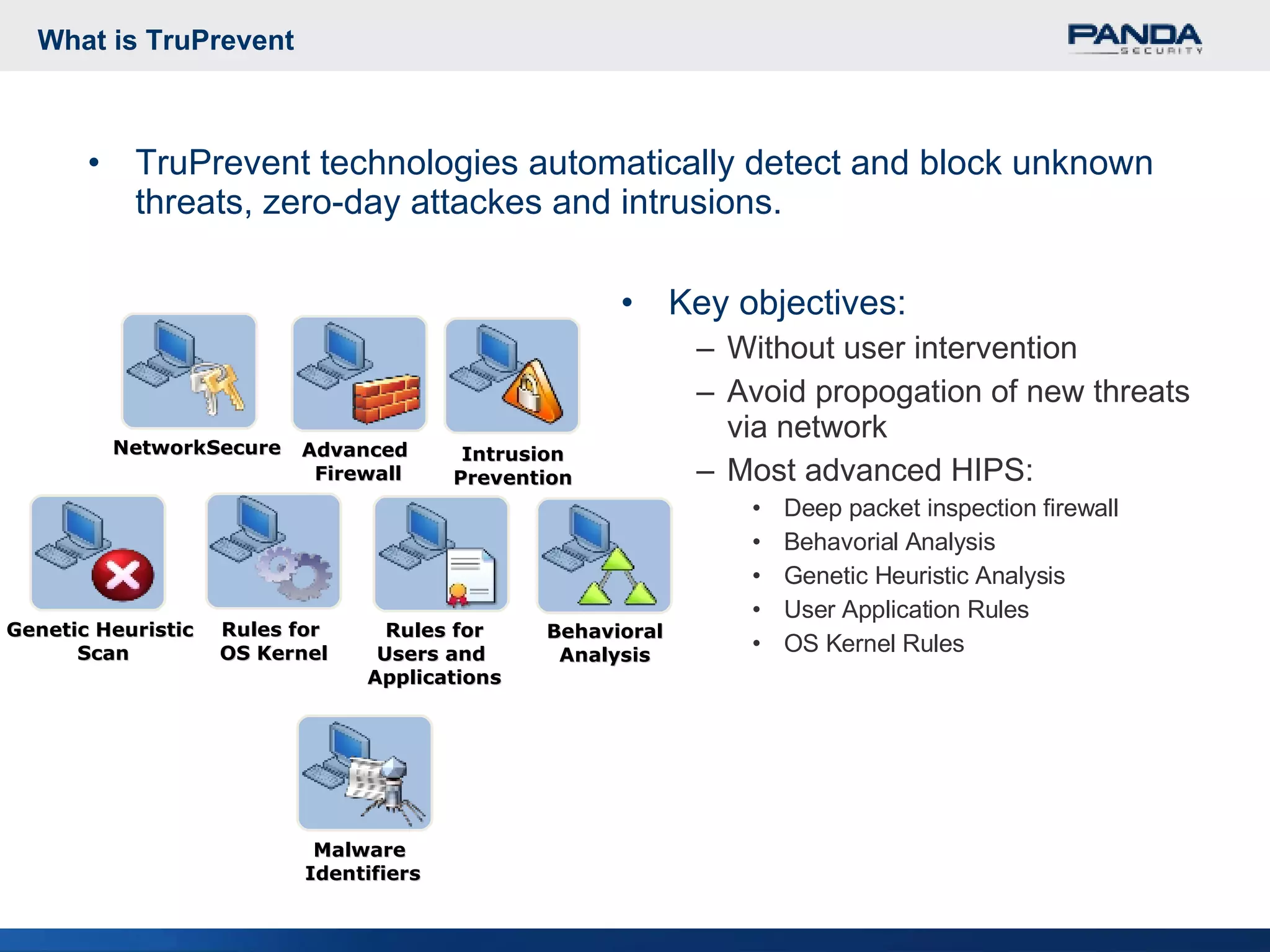
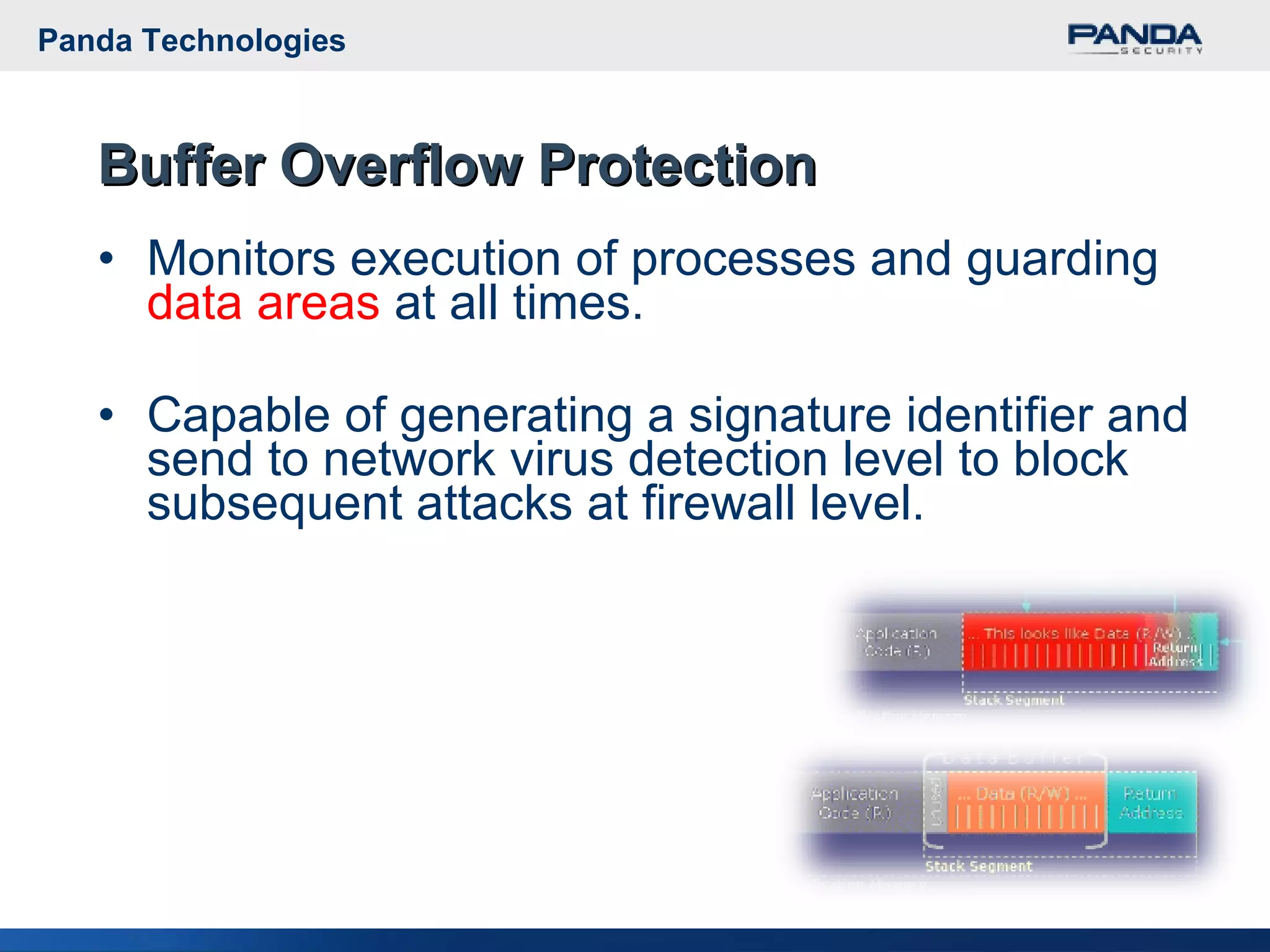
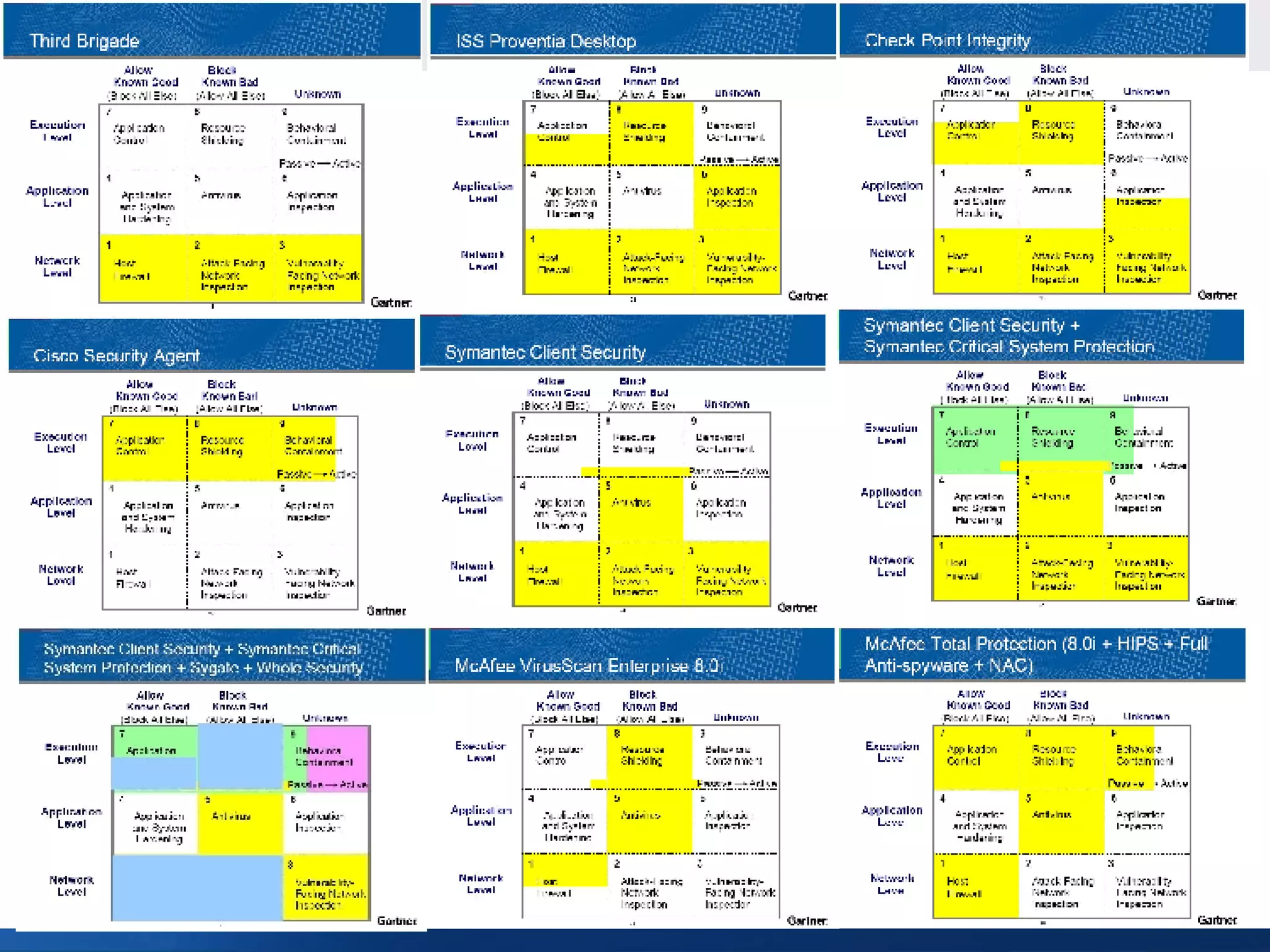
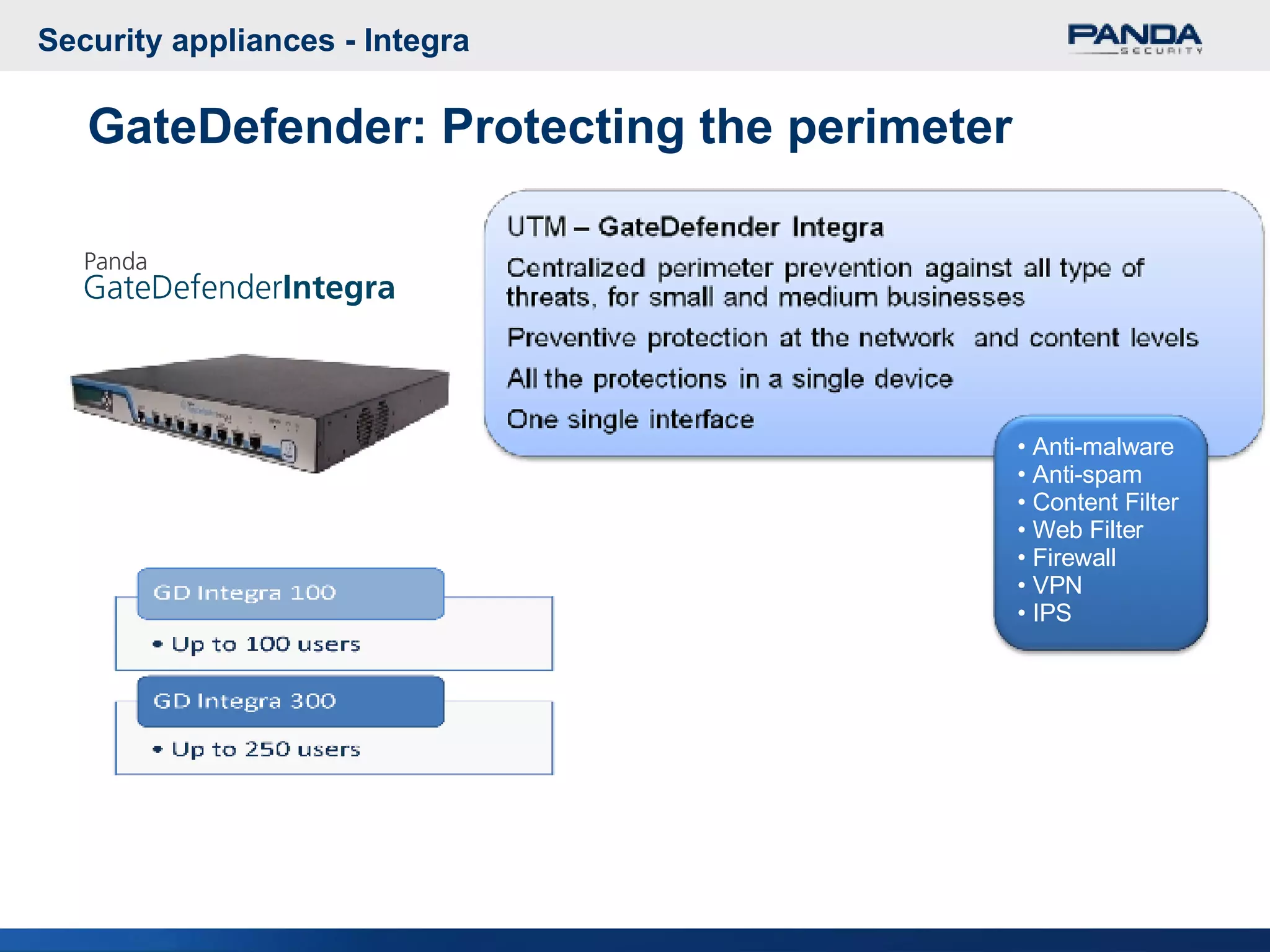
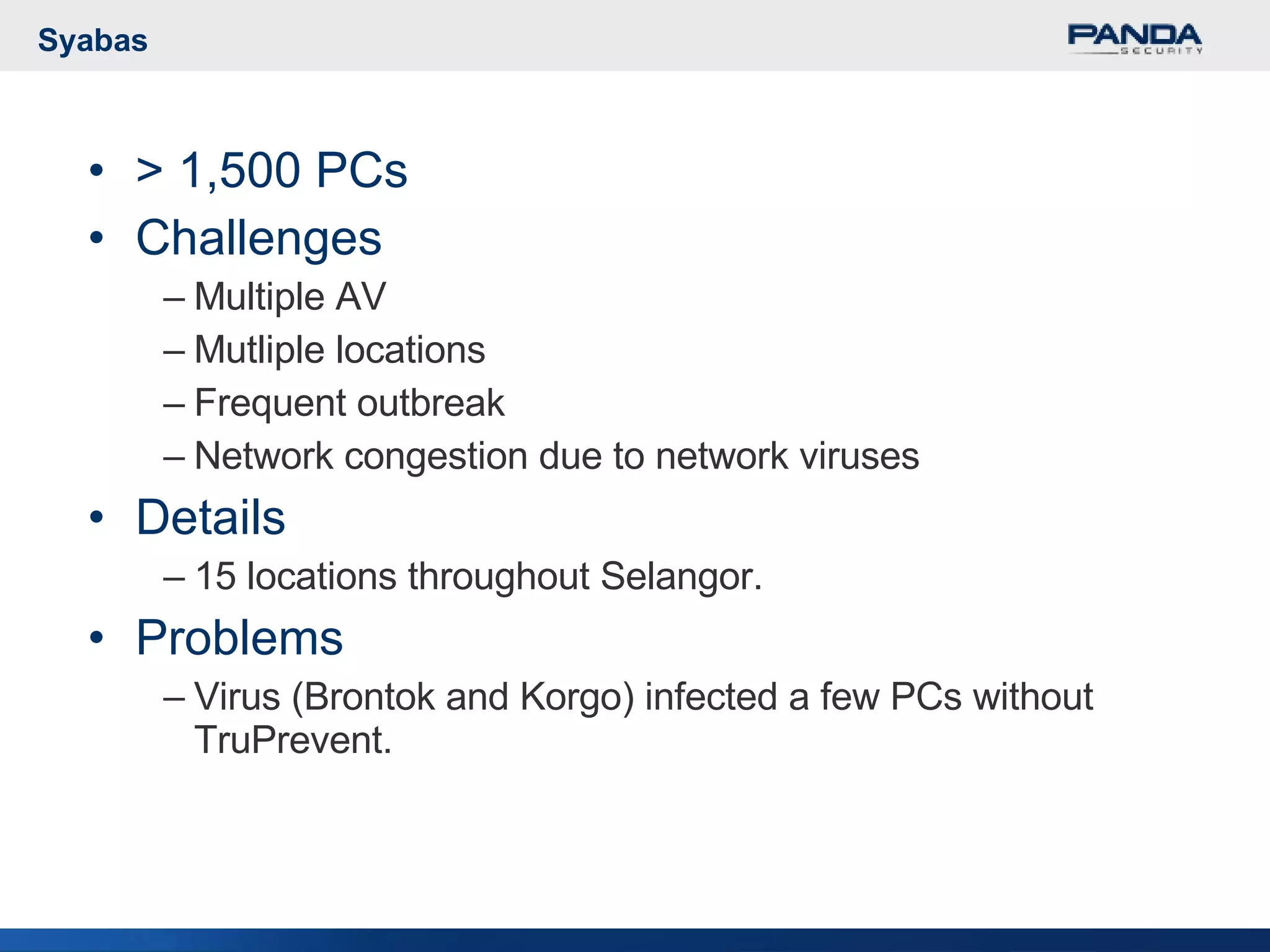
Panda Security provides unified malware protection technologies through products like TruPrevent host-based intrusion prevention system and Collective Intelligence. TruPrevent uses behavioral analysis and deep packet inspection to detect and block unknown threats while Collective Intelligence automates malware analysis through a global network of sensors to consistently deliver fast responses. Panda also offers security appliances and services like MalwareRadar, TrustLayer Mail, and solutions for mobile operators and enterprises to provide comprehensive protection.



![Who we are Founded in 1990 Leading European company in security, and the fourth worldwide company in the sector [Gartner] Solid financial situation with the participation of important private equity firms: 55% growth in 2004 Offices in more than 50 countries Product available in 23 languages Investing in R&D more than 25% of the annual revenue Leader in protection technologies against unknown threats [Gartner]](https://image.slidesharecdn.com/pandasecurity2008-1217382150294914-8/75/Panda-Security2008-4-2048.jpg)