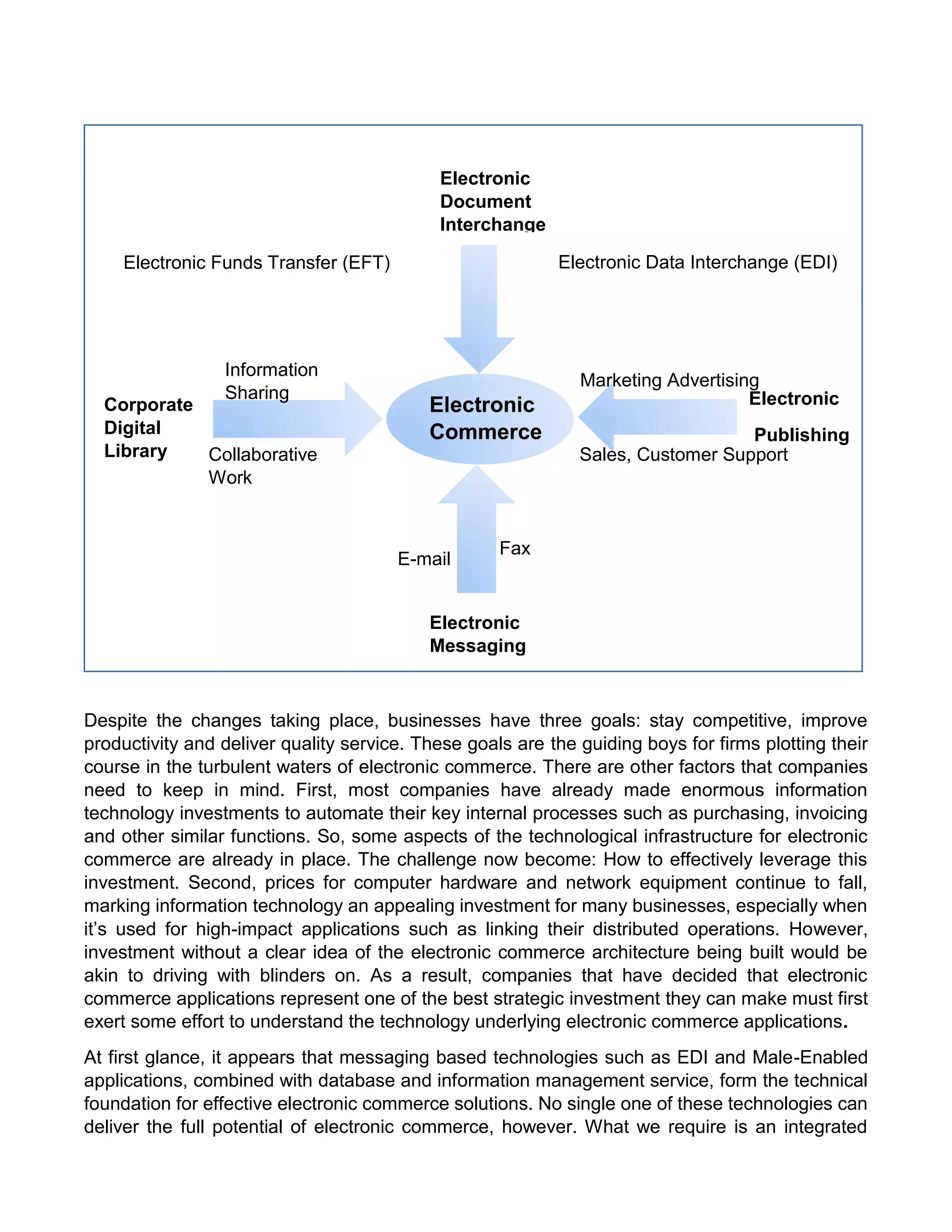
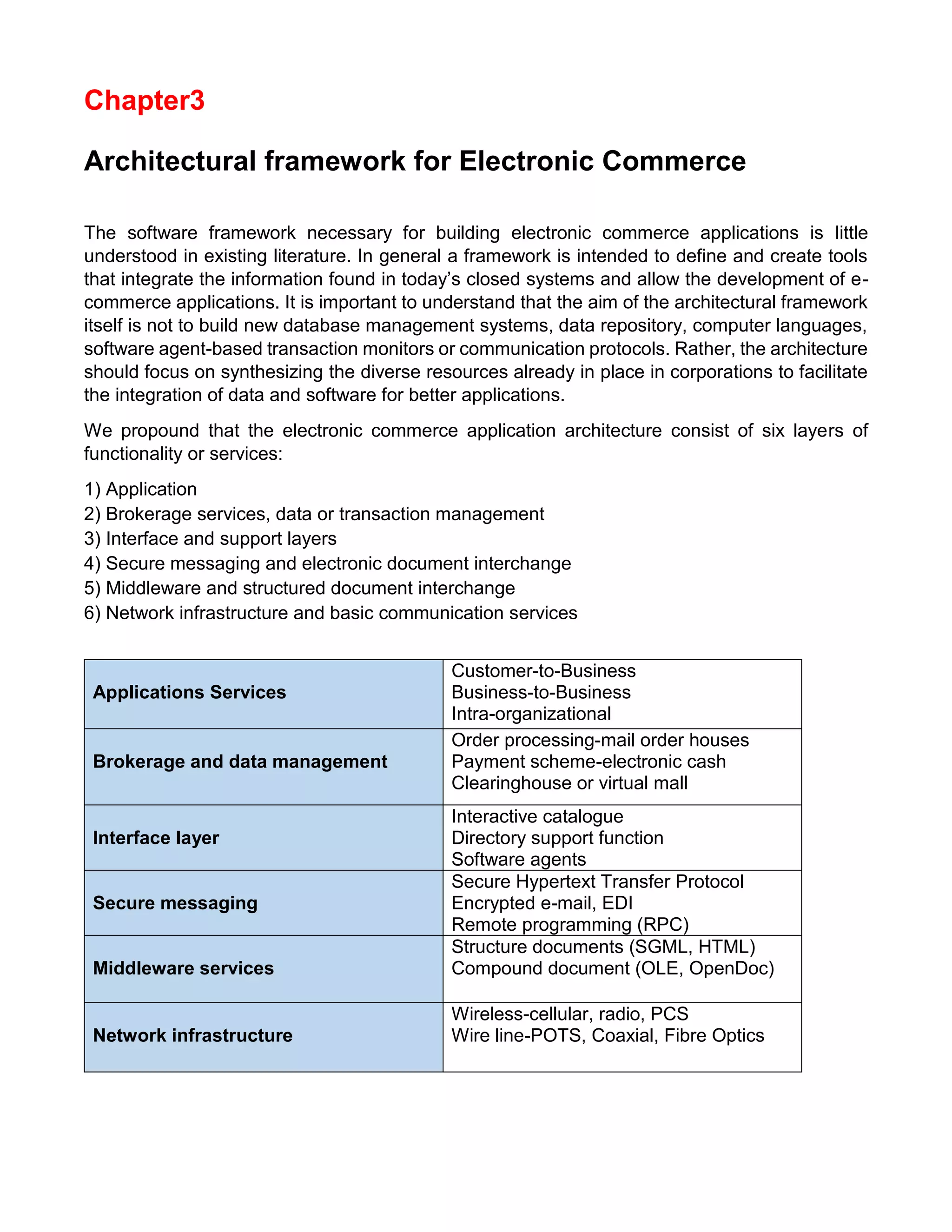
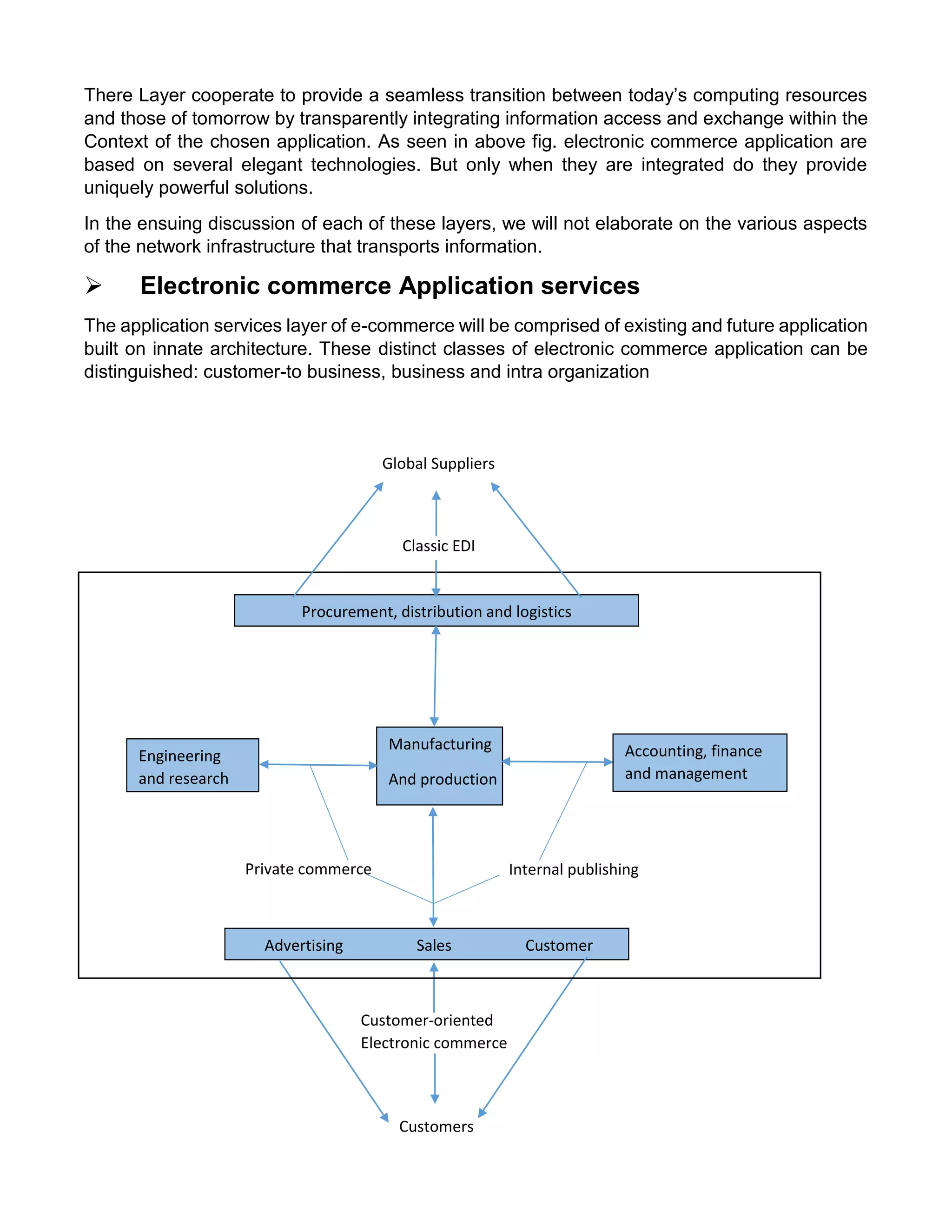
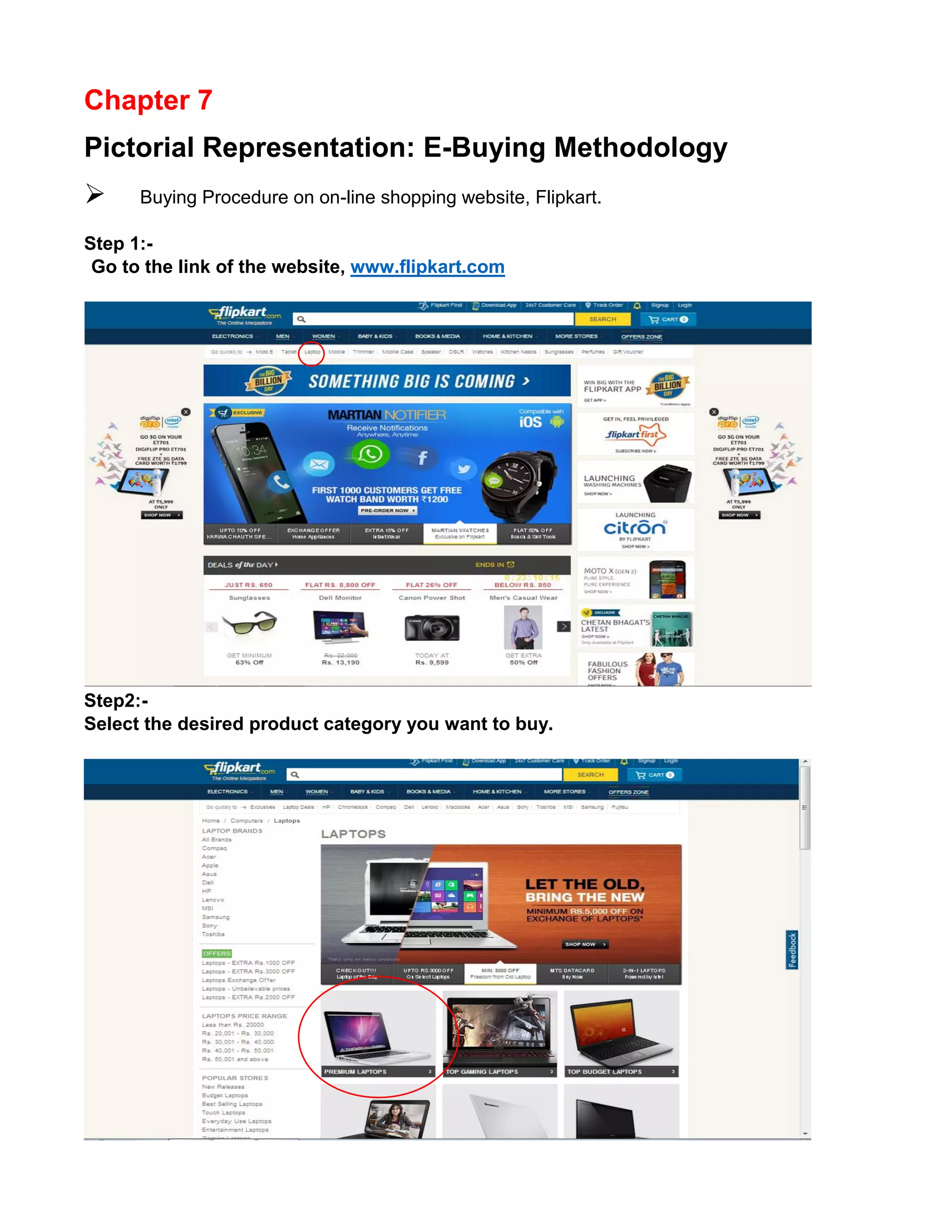
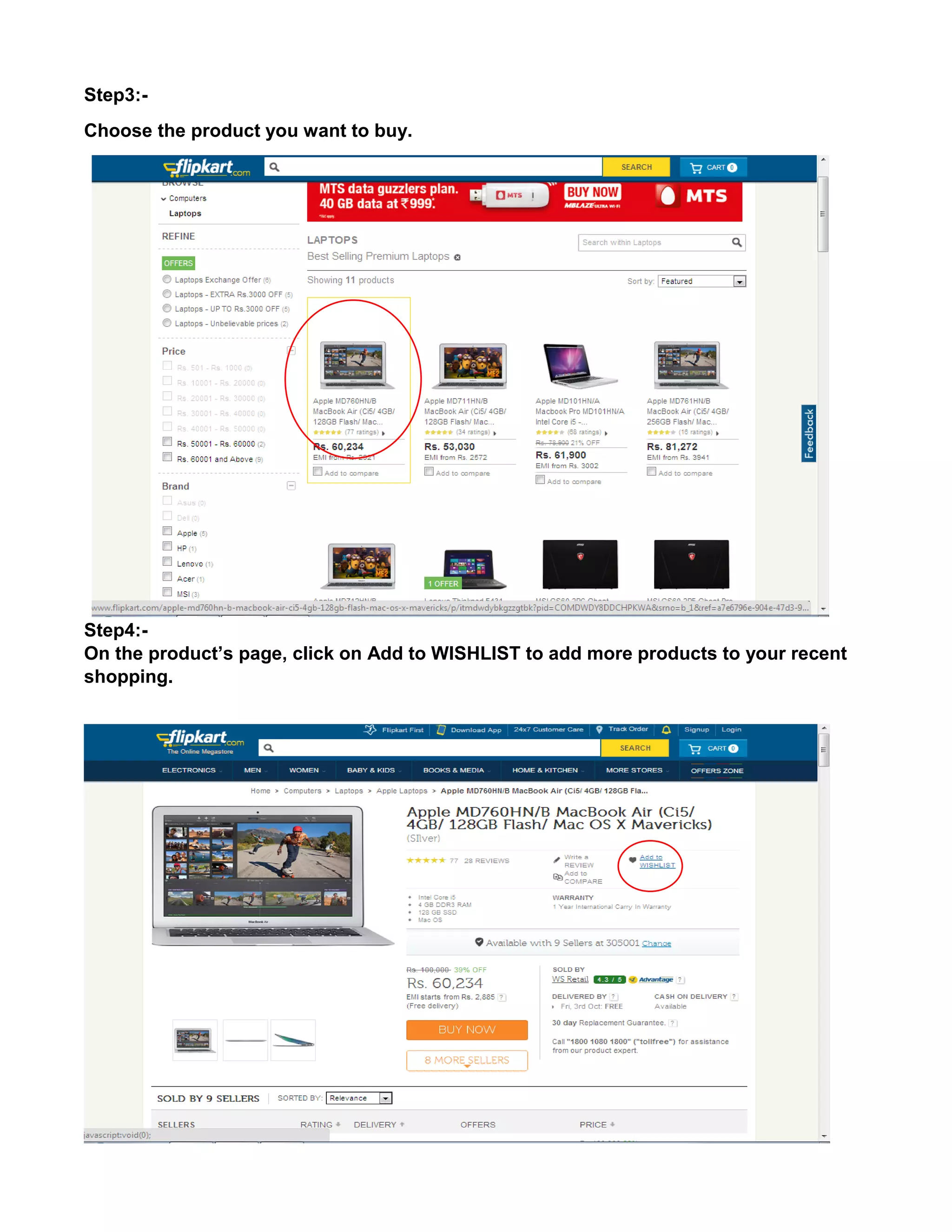
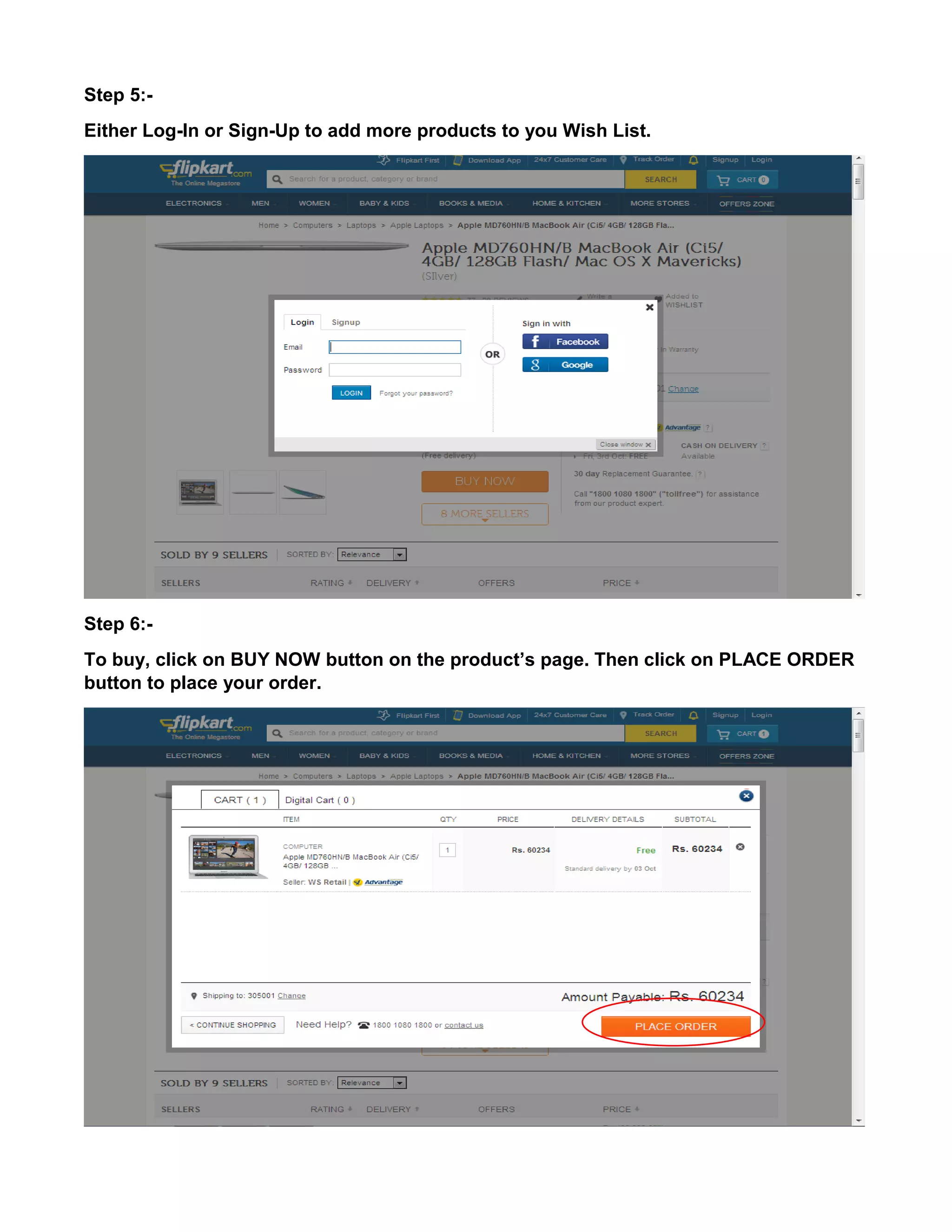
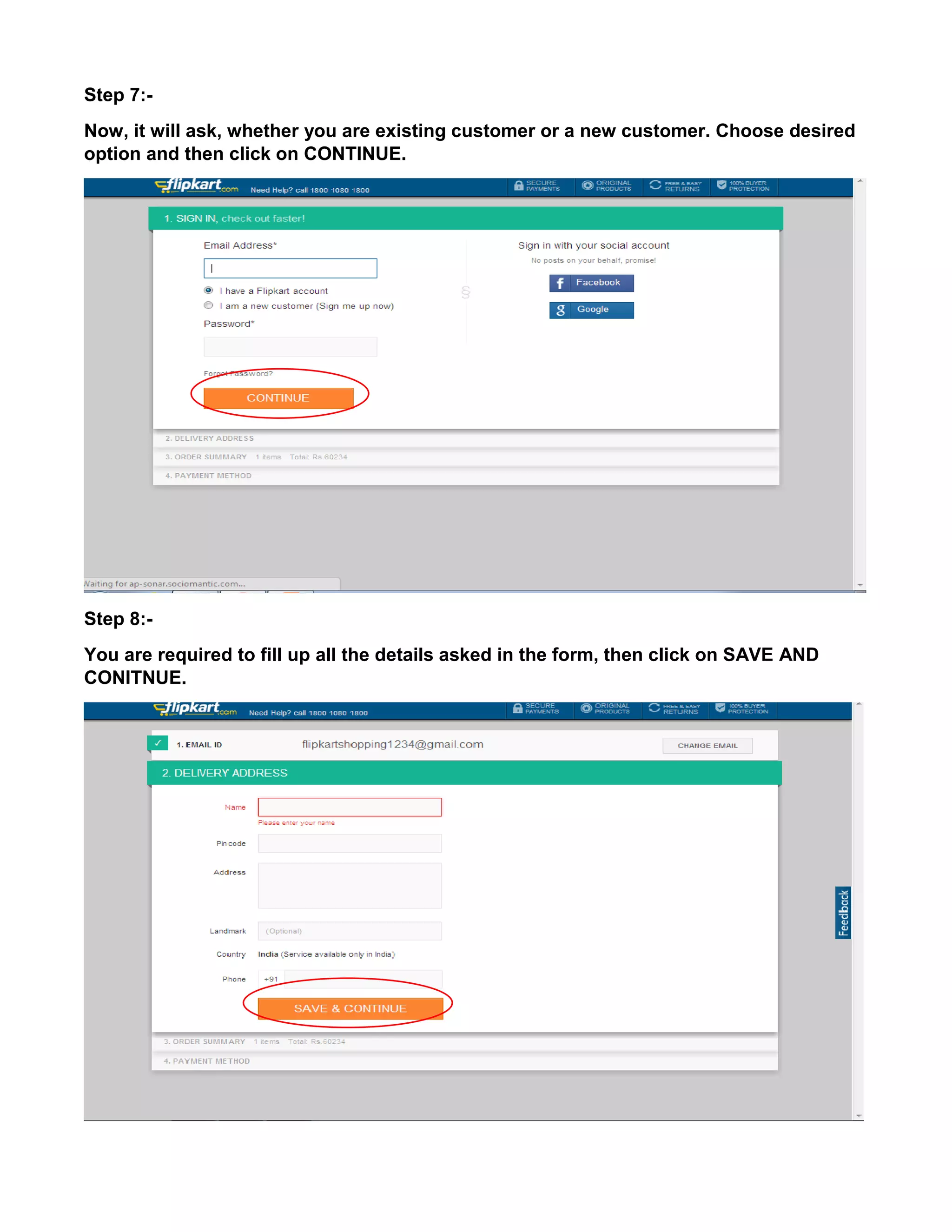
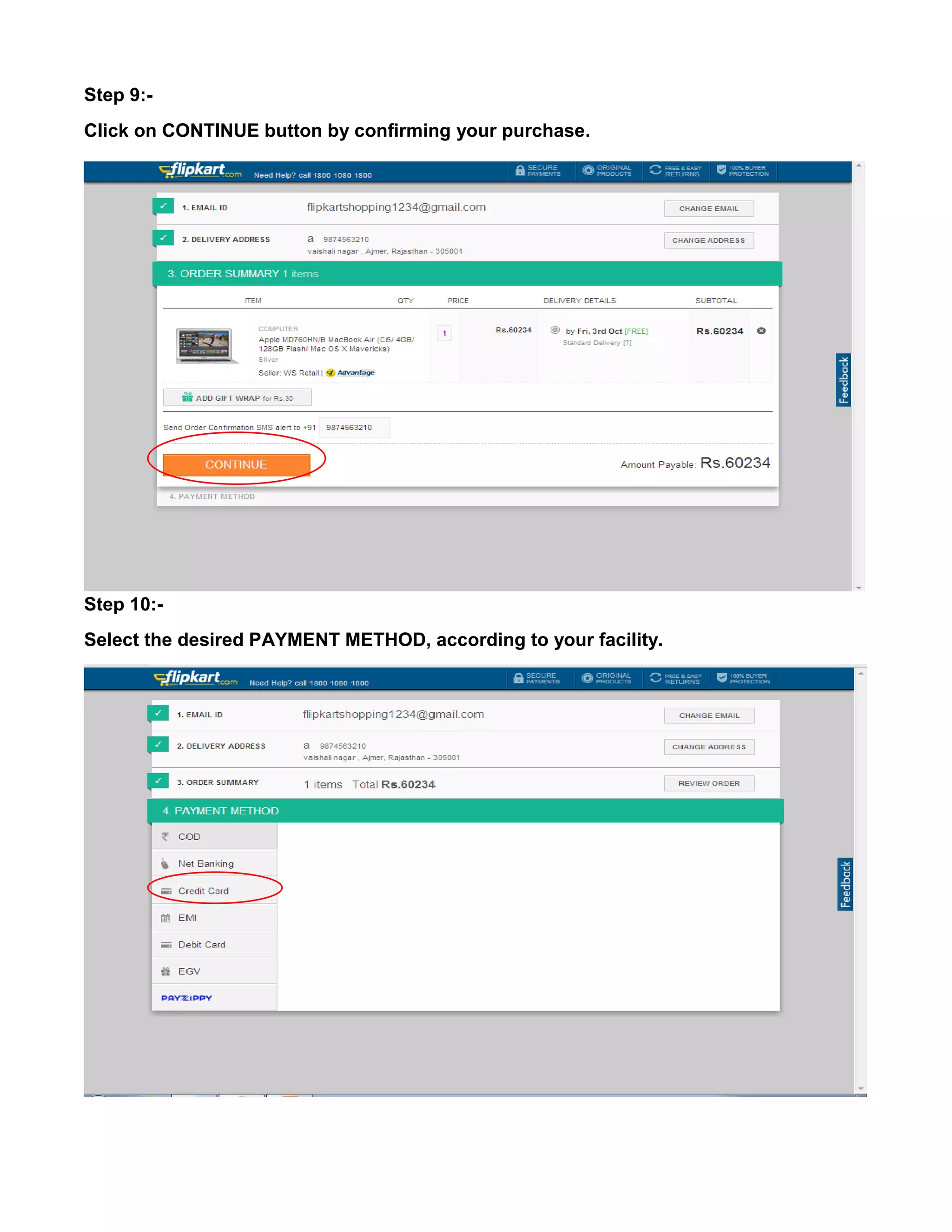
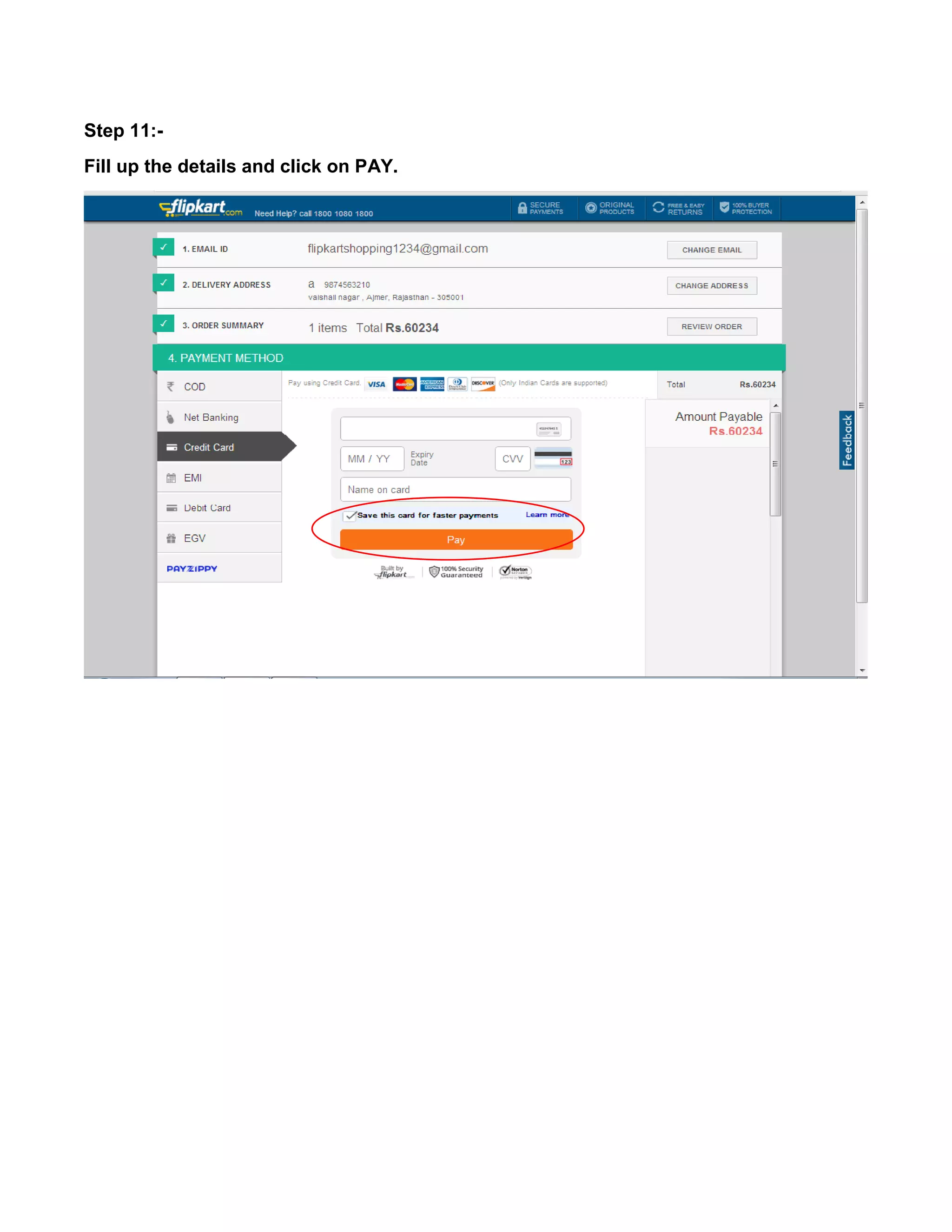
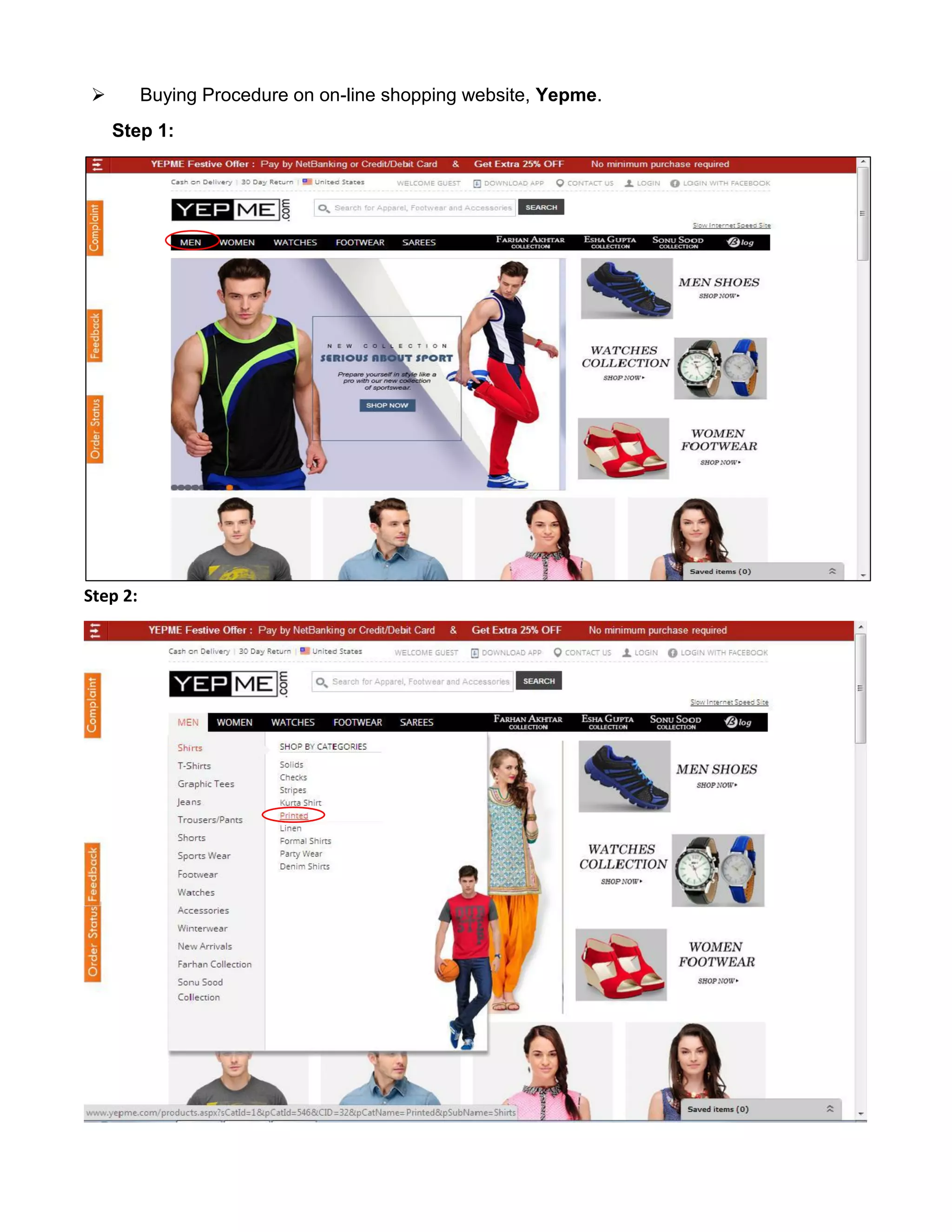
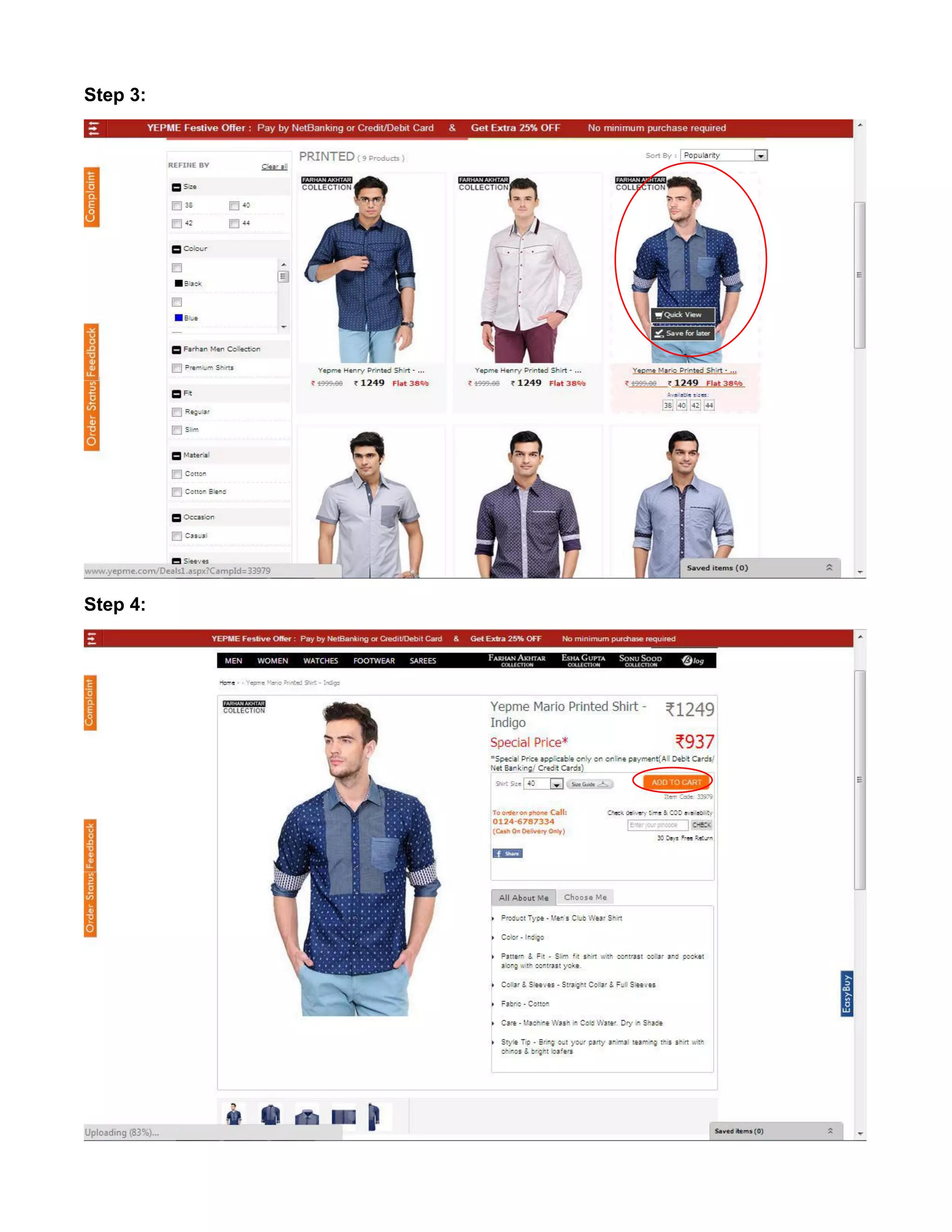
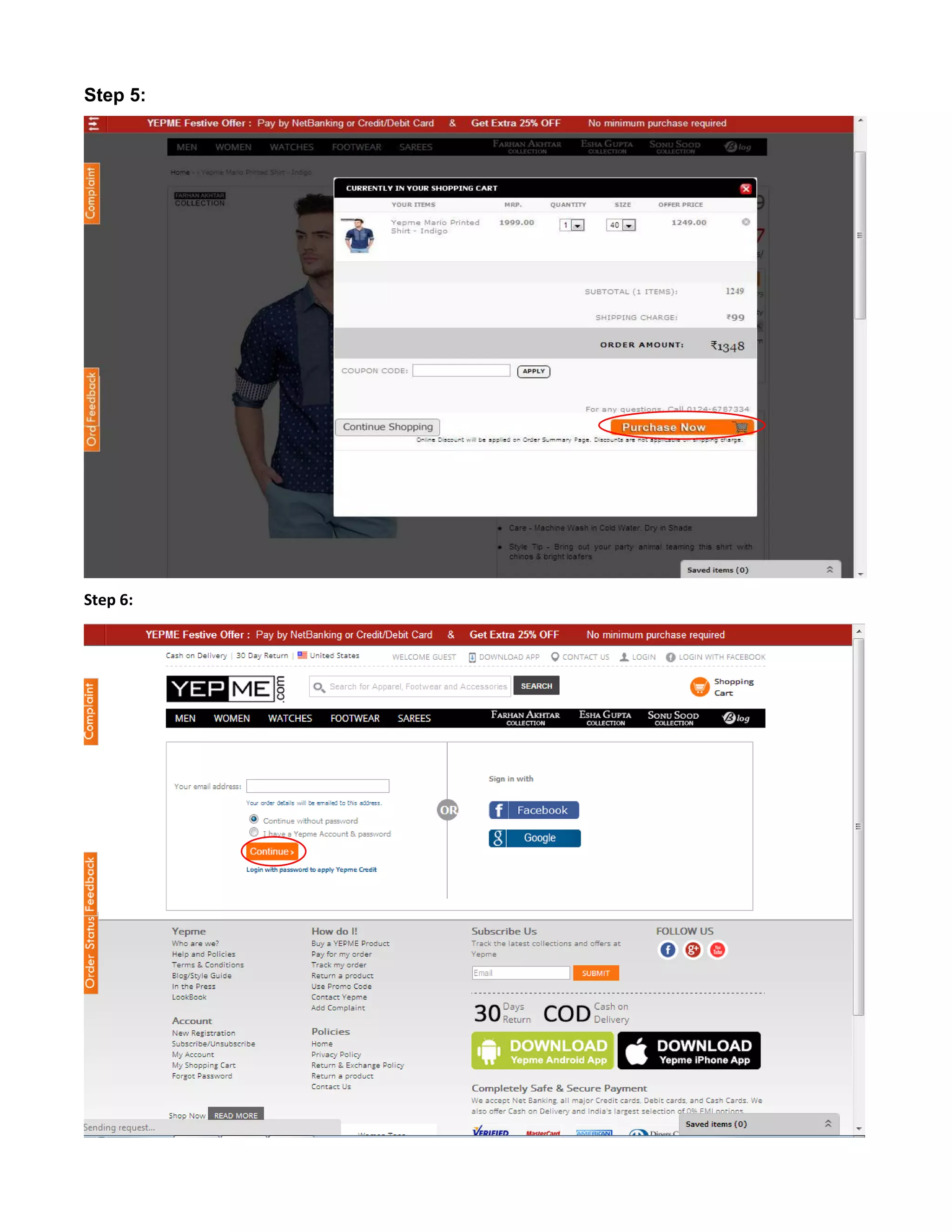
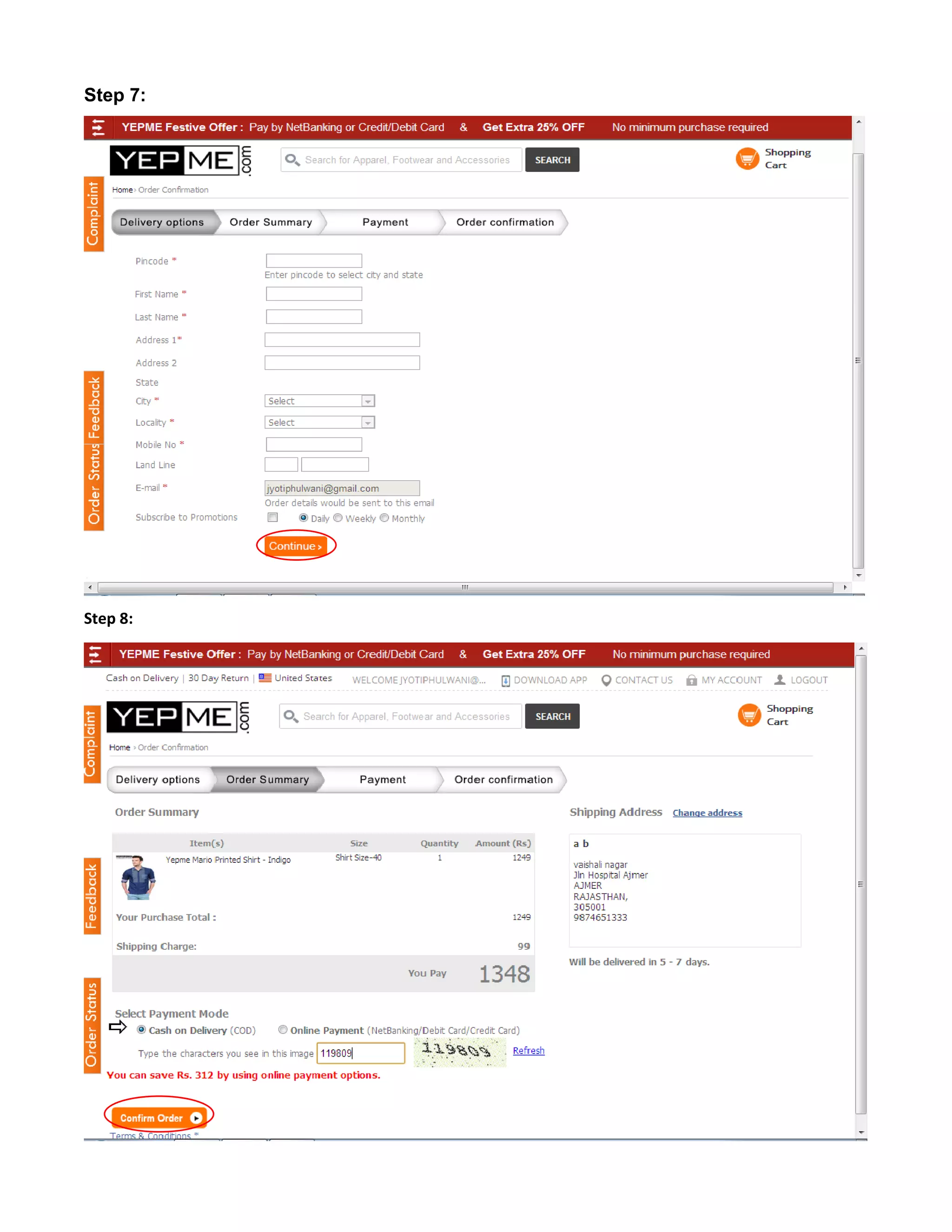
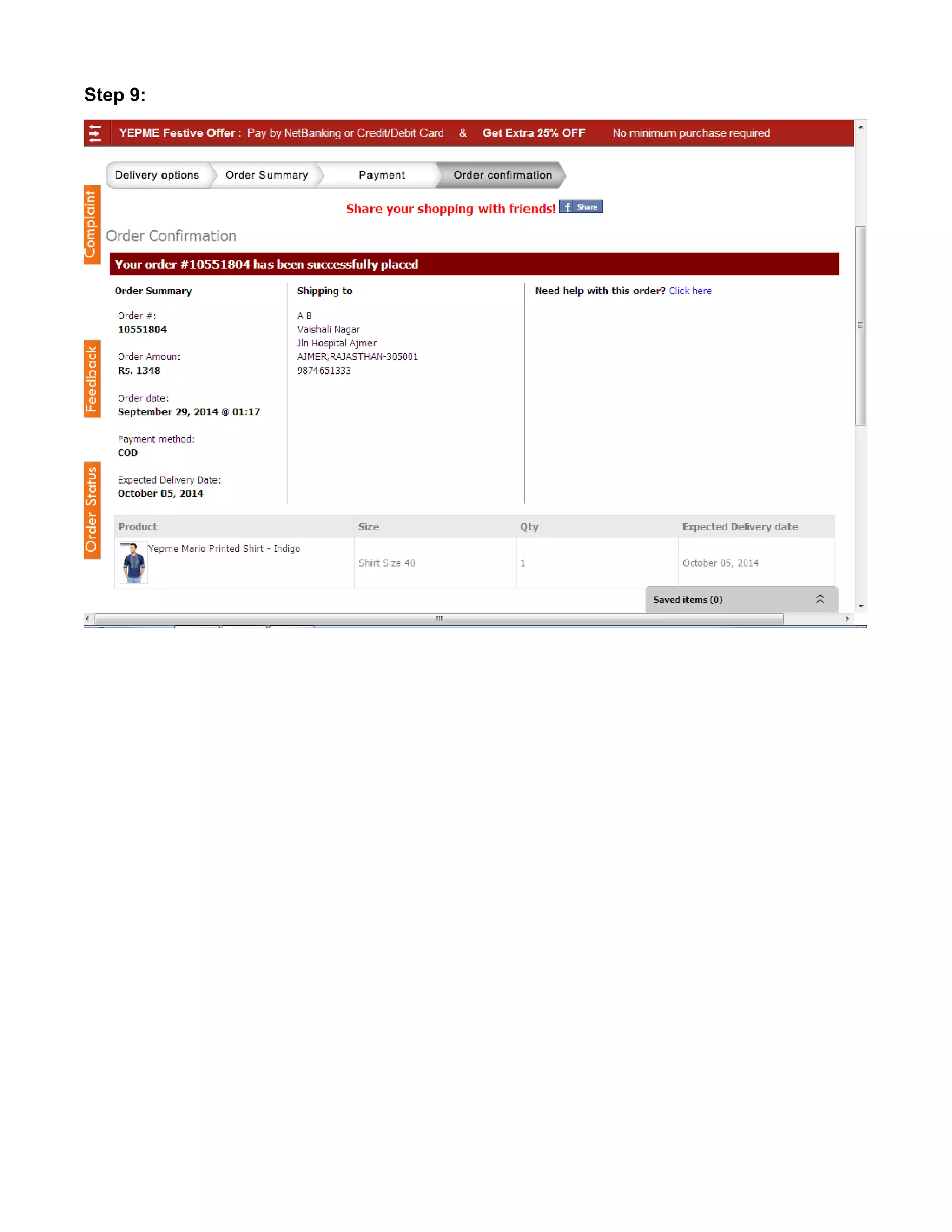
This document provides an overview of electronic commerce and discusses its various components. It describes the six layers that make up the architectural framework for electronic commerce: 1) applications services, 2) brokerage and data management, 3) interface and support layers, 4) secure messaging and document interchange, 5) middleware services, and 6) network infrastructure. Each layer is discussed in one to two paragraphs to explain its purpose and role in enabling electronic commerce.