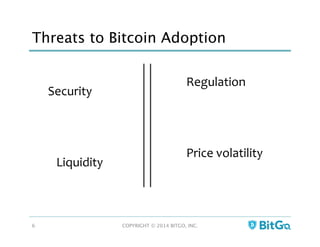
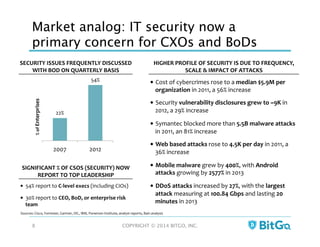
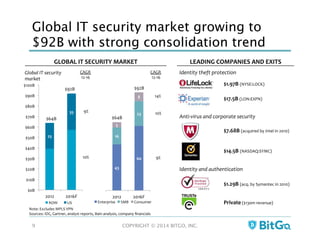
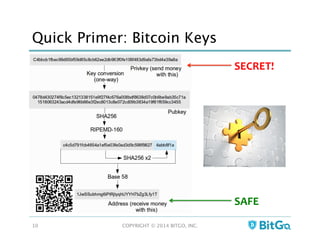
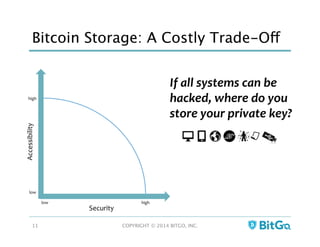
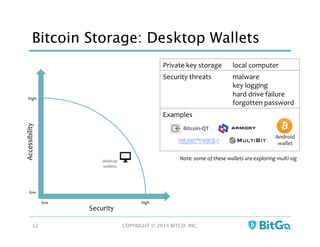
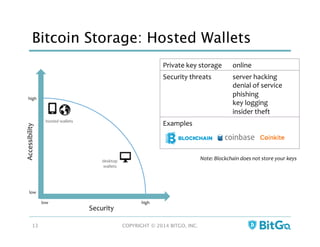
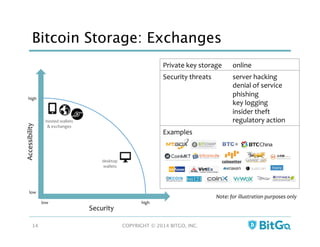
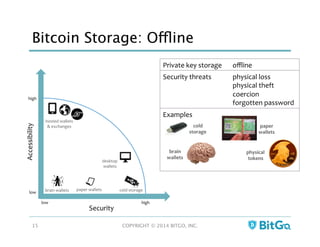
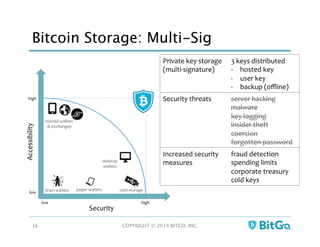
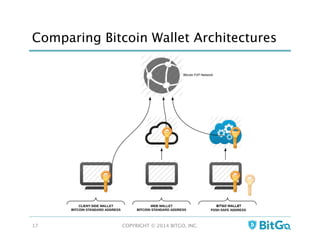
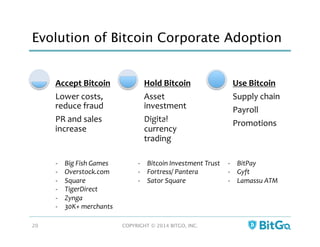
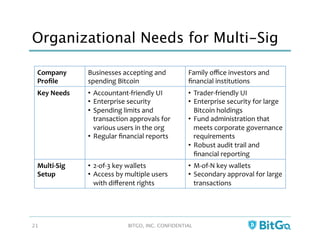
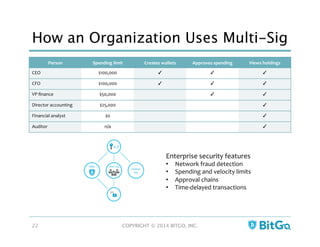
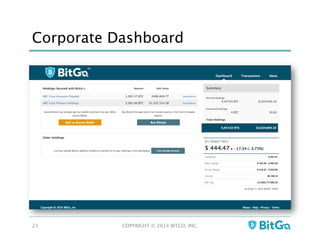
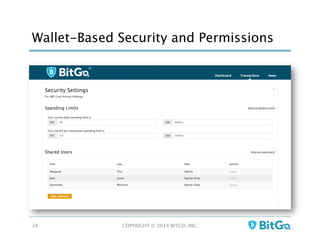
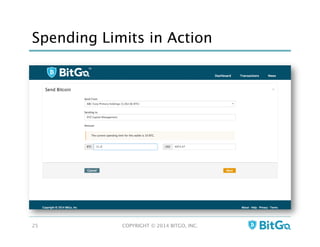
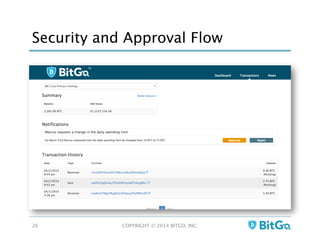
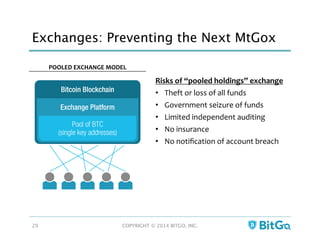
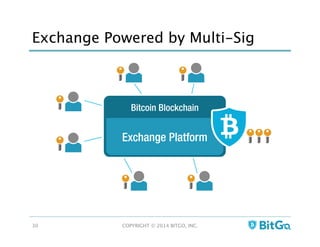
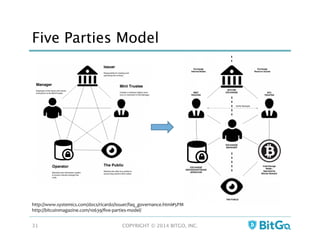
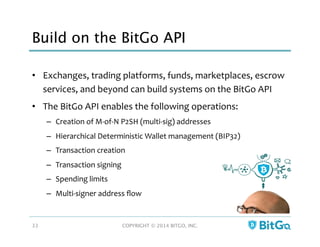
The document discusses how multi-signature (multi-sig) wallets can improve bitcoin security and enable its use in new industries. It begins with an overview of existing bitcoin storage methods and their security trade-offs. Desktop, online, offline and exchange storage are outlined. The document then introduces multi-sig wallets as a more secure solution that distributes control of funds across multiple private keys. It argues this approach makes bitcoin secure enough for enterprise and new applications.