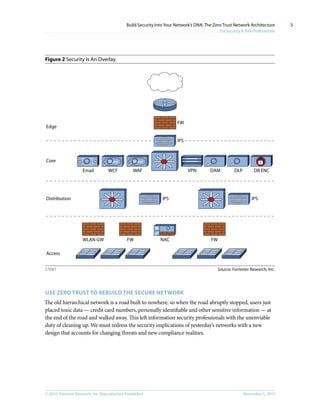
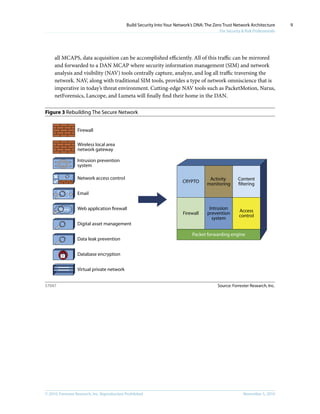
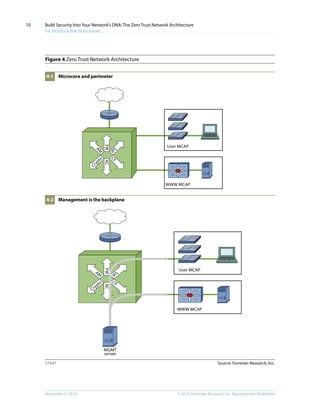
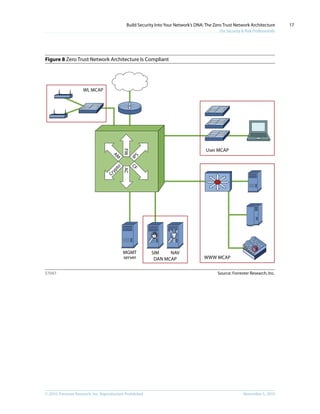
This document discusses the concept of a Zero Trust network architecture. It proposes building networks from the inside out by focusing first on protecting important data and systems, and then designing the network infrastructure around them. This approach treats all network traffic as untrusted and aims to eliminate the traditional distinction between trusted internal and untrusted external networks. The goal is to design more secure, efficient, and cost-effective networks better suited for today's threats and compliance needs.