This document outlines a 5-step approach to establishing a Software Security Assurance program:
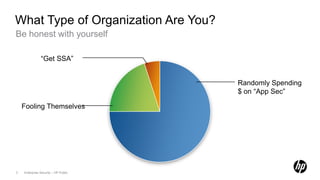
1) Conduct an assessment of capabilities, resources, assets, and organization.
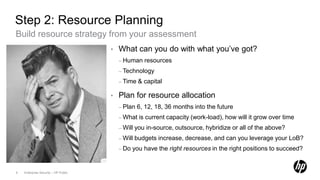
2) Develop a resource strategy and plan based on assessment.
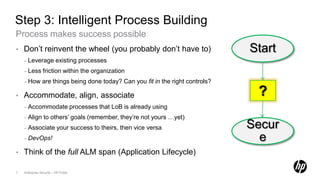
3) Build intelligent processes that leverage existing processes and accommodate business needs.
4) Implement processes strategically and augment with automation technologies.
5) Continuously measure business impact and reassess goals as business priorities change.