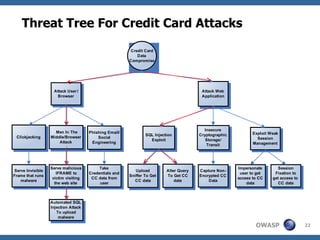
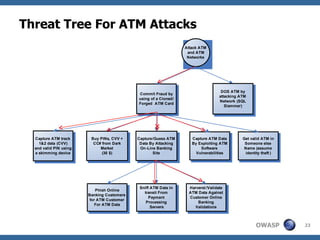
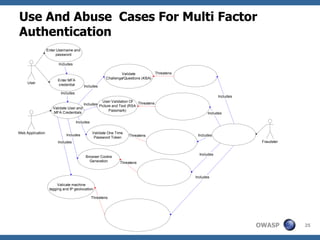
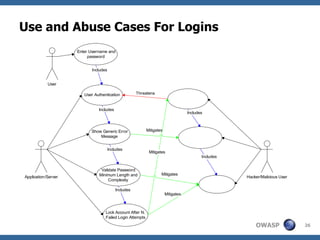
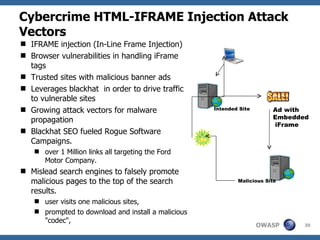
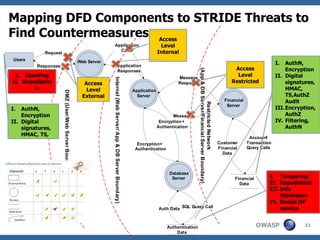
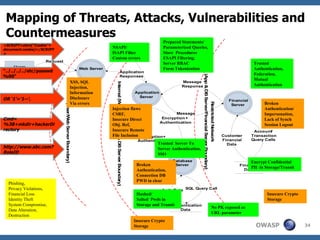
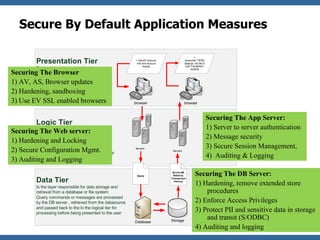
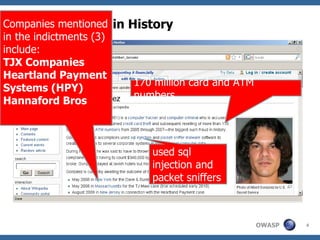
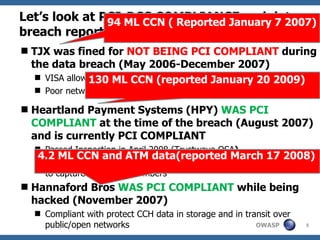
The document discusses the rise of threat analysis and fall of compliance in mitigating web application security risks. It argues that while regulatory compliance aims to improve security, many compliant organizations have still suffered major data breaches. The document advocates applying threat modeling techniques like attack tree analysis to understand likely cybercrime threats and how they could exploit vulnerabilities. This helps identify targeted security measures to implement in applications and architecture.
![The Rise of Threat Analysis and the Fall of Compliance in Mitigating Web Application Security Risks Marco Morana OWASP Cincinnati Chapter Lead [email_address] Tony Ucedavelez OWASP Atlanta Chapter Lead [email_address] LA and OC Chapters Sept 2009 Meetings](https://image.slidesharecdn.com/owaspocsept17presentationvs10reduced-091030221445-phpapp01/85/Security-Compliance-Web-Application-Risk-Management-1-320.jpg)



![PCI DSS: Protection of CCH and Sensitive Credit Card Authentication Data [PCI-DSS] 3.2 Do not store sensitive authentication data subsequent to authorization (even if encrypted) [PCI-DSS] 3.3 Mask PAN when displayed (the first six and last four digits are the maximum number of digits to be displayed). [PCI-DSS] 3.4 Render PAN , at minimum, unreadable anywhere it is stored (including on portable digital media, backup media, in logs)](https://image.slidesharecdn.com/owaspocsept17presentationvs10reduced-091030221445-phpapp01/85/Security-Compliance-Web-Application-Risk-Management-7-320.jpg)