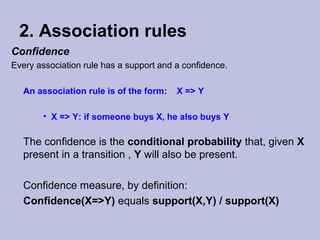
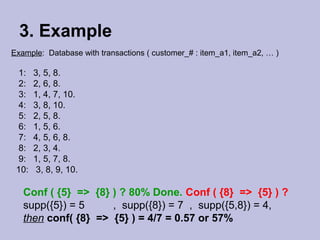
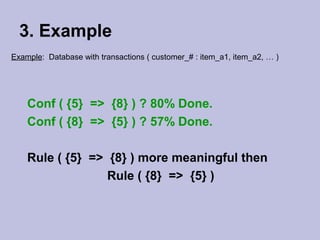
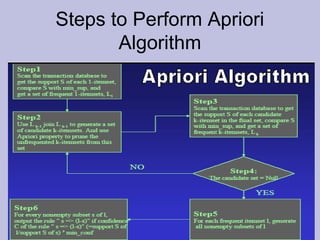
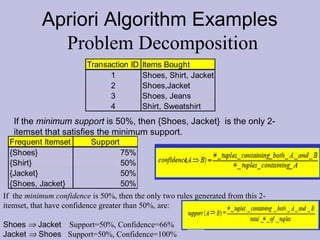
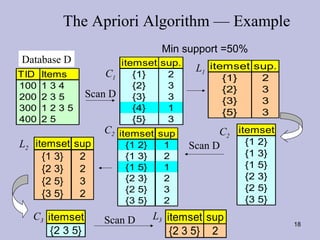
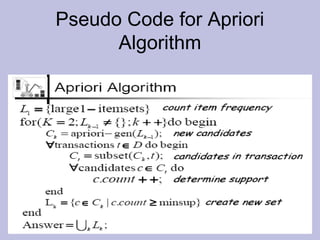
Data mining techniques like association rules aim to find frequent patterns and relationships in large datasets. Association rules use support and confidence metrics to identify rules that have a high probability of one item being purchased with another. The Apriori algorithm is designed to efficiently find these frequent itemsets in transaction data through multiple scans of the database and exploiting the property that subsets of frequent itemsets must also be frequent. An example shows calculating support and confidence for potential rules in a transactional dataset to determine meaningful relationships between items.
![Outline
1. Data Mining (DM) ~ KDD [Definition]
2. DM Technique
-> Association rules [support & confidence]
3. Example
(4. Apriori Algorithm)](https://image.slidesharecdn.com/rmining-131226022318-phpapp01/75/Rmining-1-2048.jpg)
![1. Data Mining ~ KDD [Definition]
- "Data mining (DM), also called KnowledgeDiscovery in Databases (KDD), is the process
of automatically searching large volumes of
data for patterns using specific DM
technique."
- [more formal definition] KDD ~ "the non-trivial
extraction of implicit, previously unknown
and potentially useful knowledge from data"](https://image.slidesharecdn.com/rmining-131226022318-phpapp01/85/Rmining-2-320.jpg)
![1. Data Mining ~ KDD [Definition]
Data Mining techniques
•
•
•
•
•
•
Information Visualization
k-nearest neighbor
decision trees
neural networks
association rules
…](https://image.slidesharecdn.com/rmining-131226022318-phpapp01/85/Rmining-3-320.jpg)