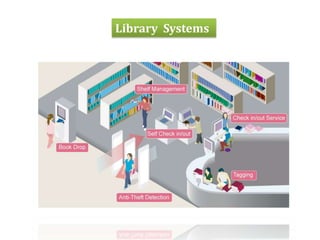
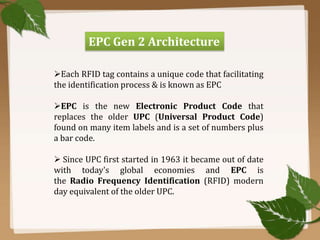
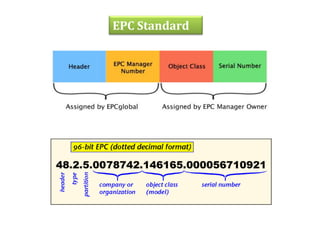
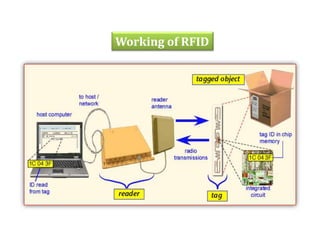
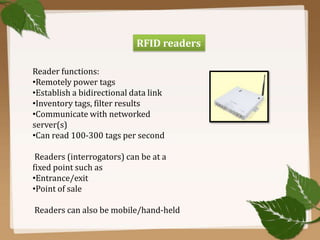
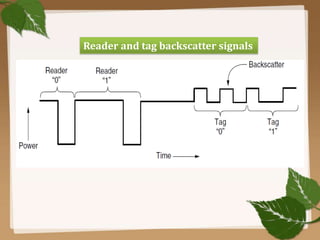
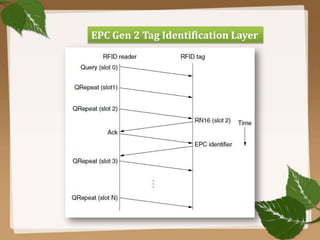
RFID uses radio waves to automatically identify objects. It consists of a tag attached to the object and a reader that detects and reads the tag. The tag contains an antenna and microchip that stores information. The reader emits radio waves to power the tag and read its data from a distance without contact. Common applications include inventory tracking, transportation payments, and access control like passports. RFID tags come in passive and active types. EPC Gen 2 is the standard protocol that defines the physical and logical specifications for UHF RFID systems, including tag and reader communication methods and message formats.