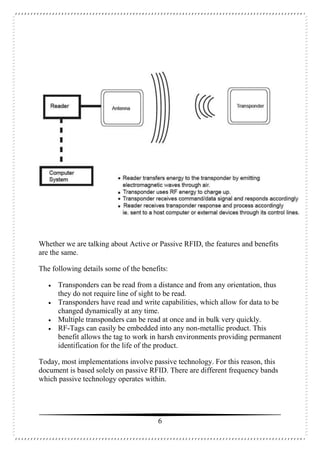
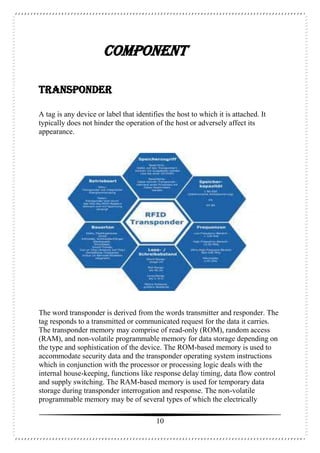
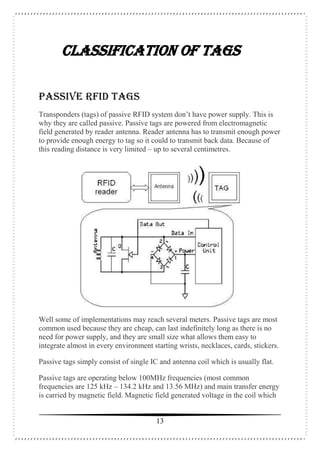
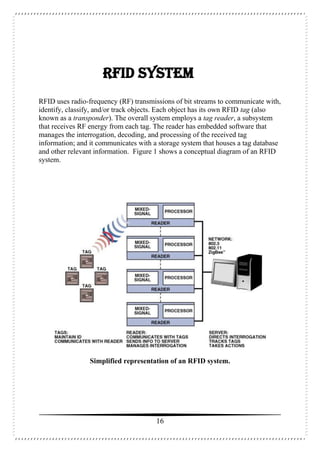
This document is a seminar report on radio frequency identification (RFID) technology submitted by Anjani Kumari for her Bachelor of Technology degree. The report includes an introduction to RFID technology, its components, types of tags, applications and advantages/disadvantages. It provides a high-level overview of the history and basic workings of RFID systems and discusses current and potential future uses in areas like supply chain management, manufacturing, and retail.