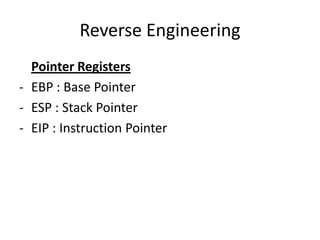
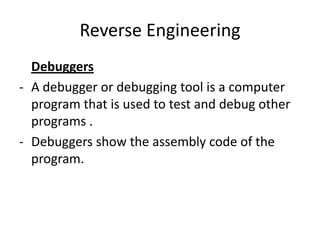
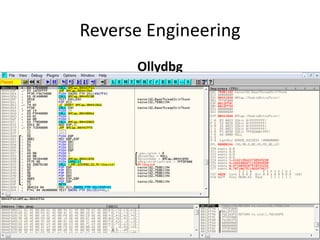
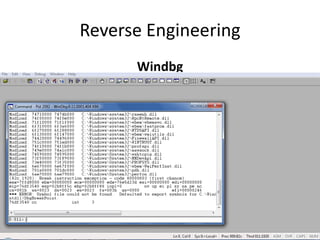
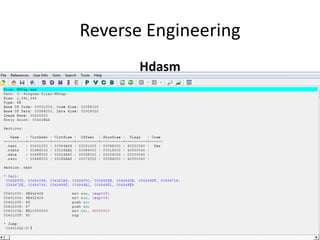
The document discusses reverse engineering, highlighting its goals of improving product functionality, reducing costs, and facilitating software updates through assembly language and debugging tools. It covers the basics of assembly language, registers, flags, jumps, packing, and unpacking methods, along with useful tools for each process. Reverse engineering is emphasized as a vital area in software maintenance, focusing on program understanding and system recovery.


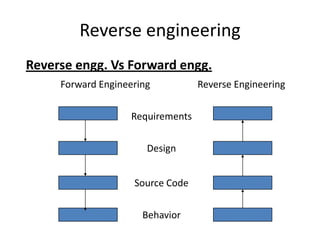


![Reverse engineering
Assembly Language basics
- Every code of a software converts in assembly
language whether it is written in java or c, or c++
or in any high level language.
- Assembly language contains mnimonics for
performing an operation like
MOV AX, 47104
MOV DS, AX
MOV [3998], 36
INT 32](https://image.slidesharecdn.com/reverseengineering-130402032939-phpapp02/85/Reverse-engineering-7-320.jpg)