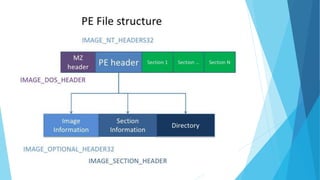
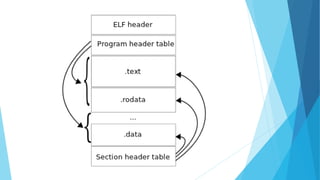
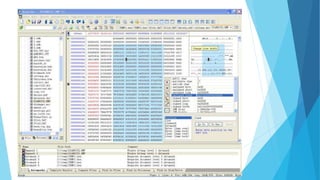
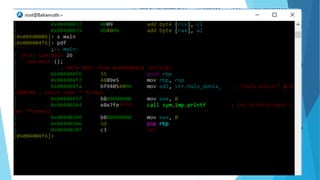
The document discusses reverse engineering in the context of software, outlining its fundamentals, principles, common practices, and tools. It covers the motivations behind reverse engineering, such as bug fixing and learning, and emphasizes the competition between developers and reverse engineers. The presentation warns against illegal activities and is intended solely for educational purposes.