1) REIL is a platform-independent intermediate language designed for reverse engineering. It has a small instruction set and simple operand types to simplify analysis.
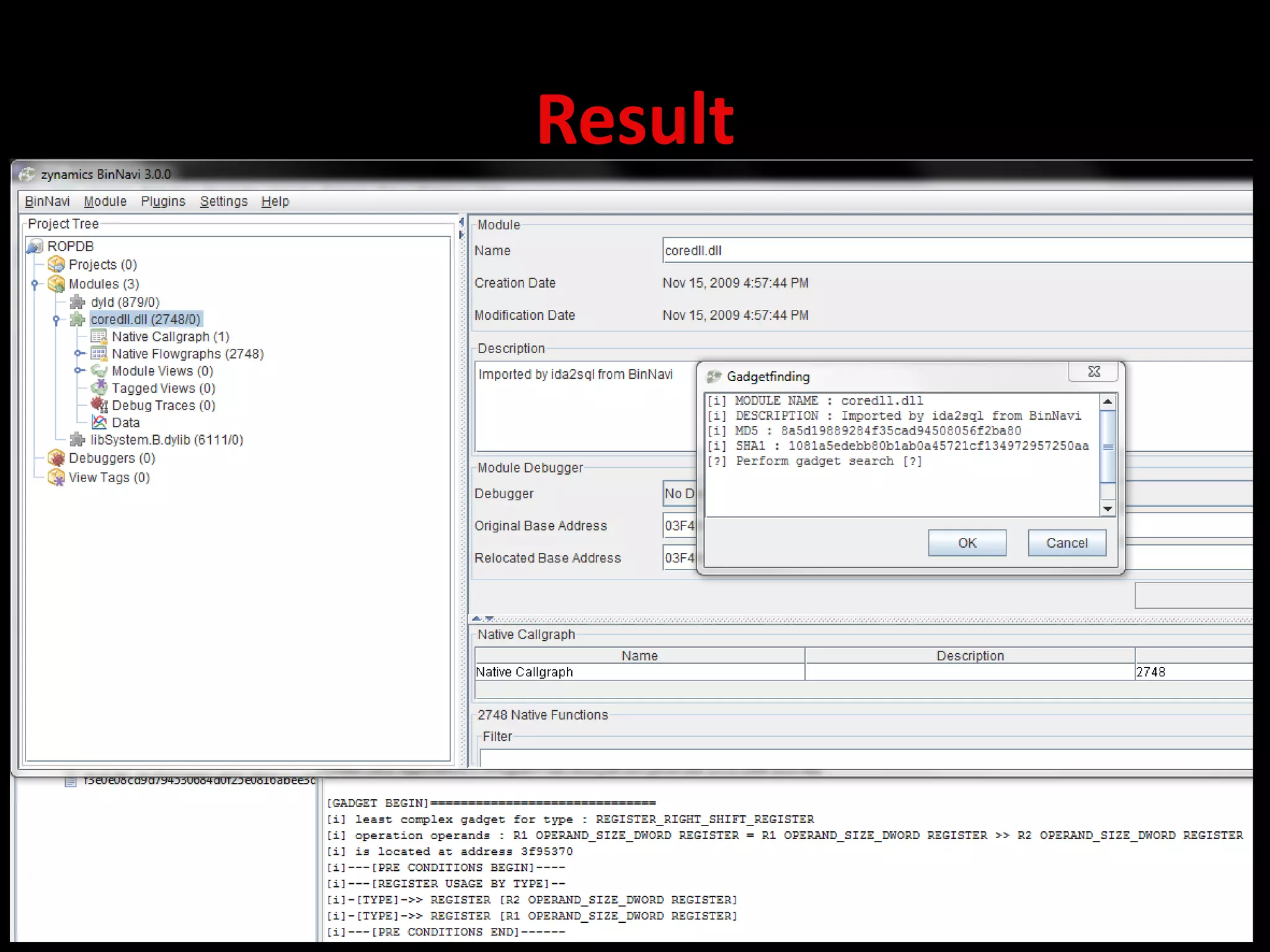
2) Applications of REIL include register tracking to follow data flow, index underflow detection to find bugs, automated deobfuscation to make code more readable, and ROP gadget generation to create return-oriented shellcode.
3) Future work includes developing BinAudit with more vulnerability research algorithms and type reconstruction to determine higher-level data types in registers.


























![Lattice
• Complicated to show in a picture
• Keep track of register values and
pointer dereferences as a list of
ranges
• eax [0 .. 4] [0 .. 10]
– Add a value between 0 and 10 to [eax], [eax + 1],
[eax + 2], [eax + 3], or [eax + 4]](https://image.slidesharecdn.com/slides-h2hc-100804062418-phpapp01/75/Applications-of-the-Reverse-Engineering-Language-REIL-27-2048.jpg)