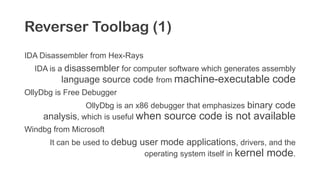
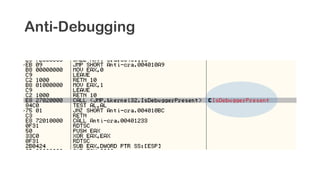
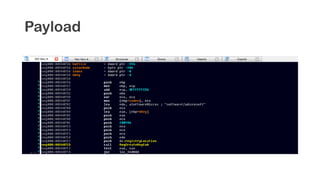
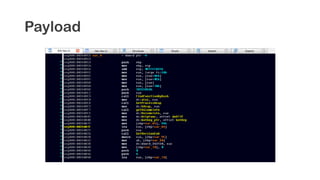
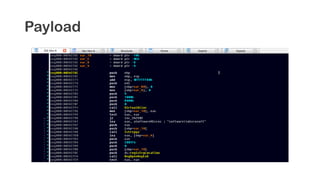
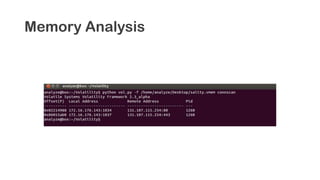
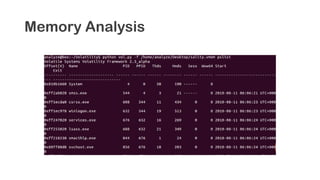
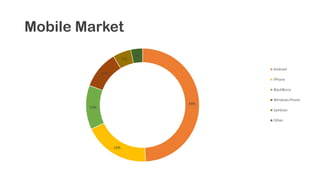
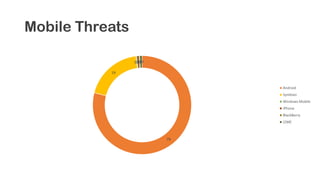
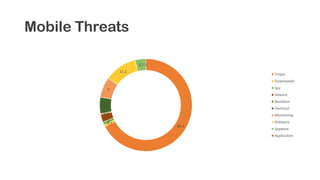
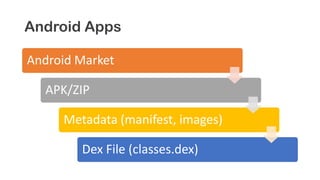
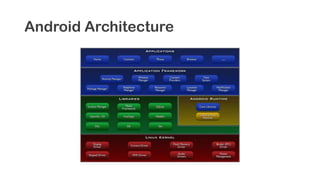
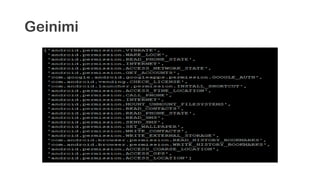
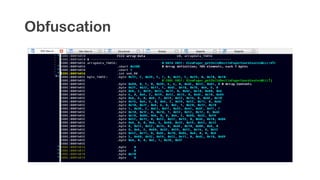
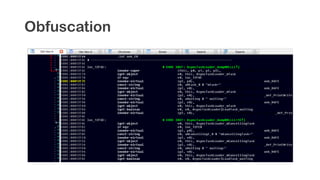
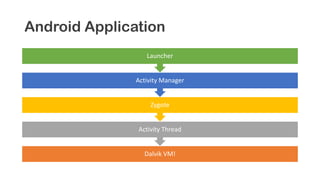
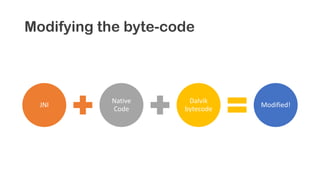
The document provides an overview of reverse engineering concepts and techniques. It discusses reverse engineering jargon like zero-day attacks and rootkits. It covers analyzing software from both an attacker and defensive perspective through static and dynamic analysis. Tools discussed include IDA Pro, OllyDbg, Windbg, and Sysinternals utilities. Techniques like anti-debugging, anti-dumping, and code obfuscation used to hinder reverse engineering are also summarized. Specific malware examples like FATMAL and analyzing packed executables and memory are examined. The document concludes with resources for analyzing mobile threats on Android.