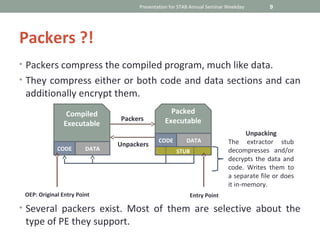
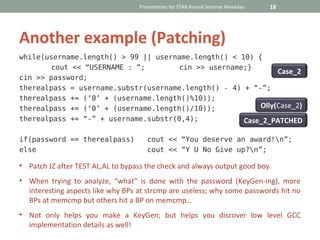
This document provides an introduction to reverse engineering and discusses cracking Windows applications. It begins with a disclaimer that reverse engineering copyrighted material is illegal. It then defines reverse engineering as analyzing a system to understand its structure and function in order to modify or reimplement parts of it. The document discusses reasons for learning reverse engineering like malware analysis, bug fixing, and customizations. It outlines some of the history of reverse engineering in software development. The remainder of the document focuses on tools and techniques for reverse engineering like PE identification, decompilers, disassemblers, debuggers, patching applications in OllyDbg, and analyzing key generation and phishing techniques.