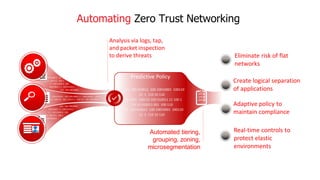
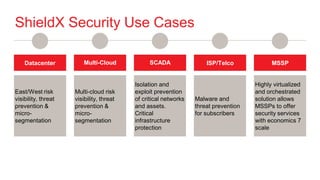
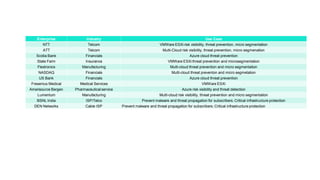
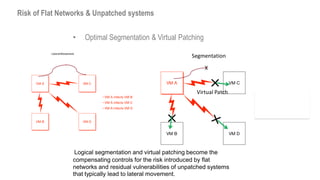
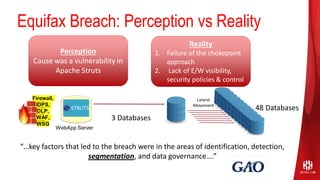
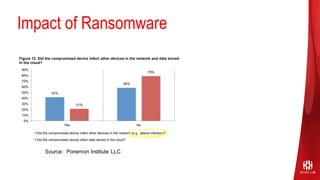
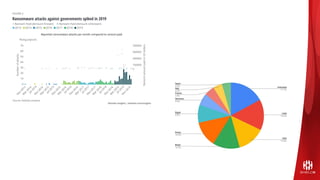
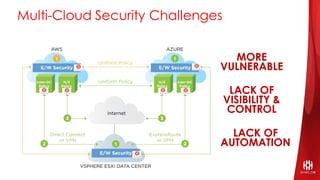
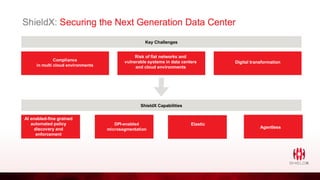
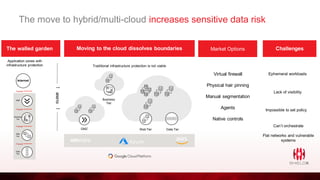
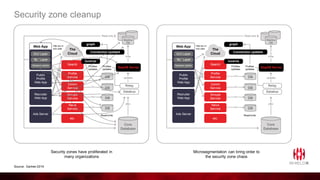
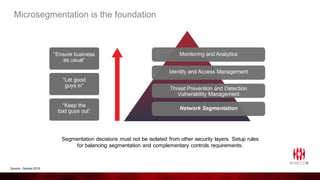
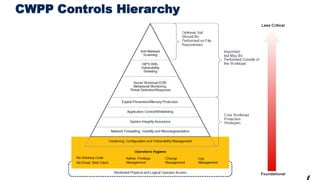
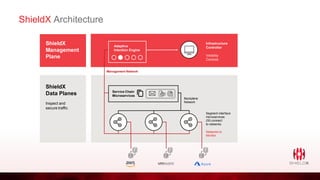
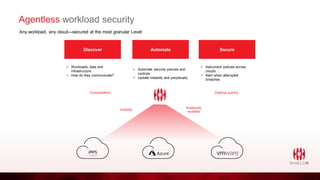
ShieldX Networks, founded in 2016, focuses on securing multi-cloud data centers by addressing risks such as lateral movement and ransomware through advanced microsegmentation and automated policy enforcement. The platform offers extensive visibility and threat prevention, which is critical for compliance across various regulations like PCI, HIPAA, and GDPR. By leveraging AI and automation, ShieldX helps organizations enhance their security posture while reducing costs associated with traditional firewall solutions.









![“[ShieldX] gives us a lower dollar-per-protected-megabyte than a traditional firewall...”
—Alaska Airlines
Life After
Deploying
ShieldX
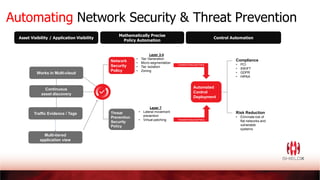
Lower Cost to
Deliver Security
Improved efficiency
Risk Reduction
• Reduce firewall footprint
• Consume fewer network resources
• Reduce maintenance costs
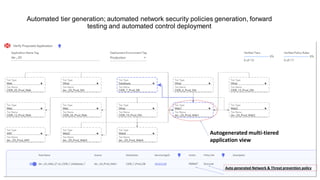
• Automated policy and control setup as well as ongoing management
• Accelerated network investigations while reducing spend on network
analytics, e.g., NextHop
• Real time policy and configuration updates
• Threat detection with DPI
• Automated fine grain control](https://image.slidesharecdn.com/crushcloudcomplexitysimplifysecurity-shieldx-200409145709/85/Crush-Cloud-Complexity-Simplify-Security-Shield-X-23-320.jpg)