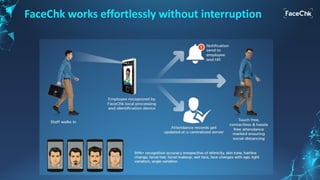
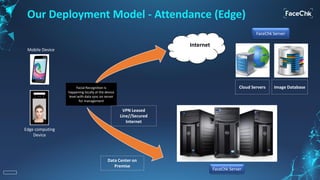
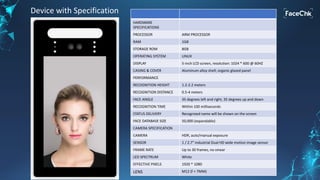
The document discusses an AI-enabled face recognition system called 'Facechk,' which is designed for identity and access management, particularly in the context of minimizing physical contact due to the COVID-19 pandemic. It highlights the advantages of facial recognition over traditional fingerprint systems, such as touch-free operation, speed, and ease of deployment across various devices. Additionally, Facechk offers features for attendance management, visitor management, and other applications while ensuring hygiene and facilitating social distancing.