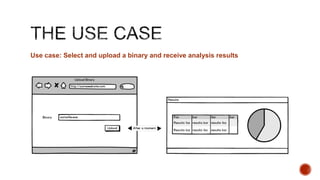
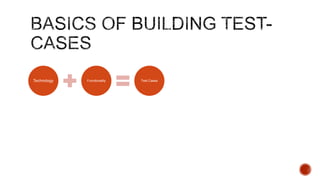
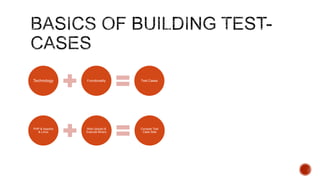
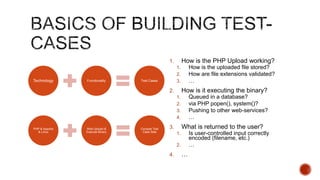
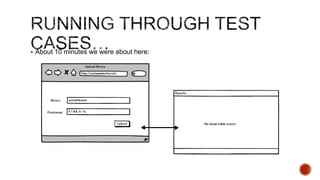
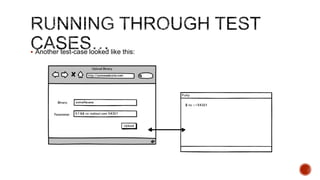
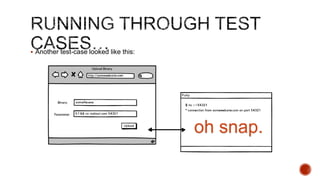
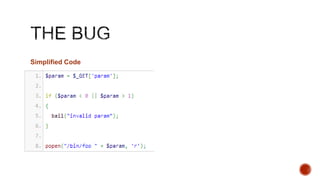
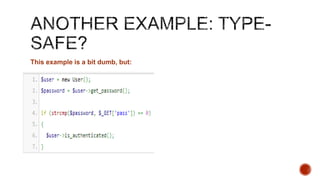
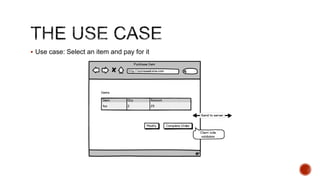
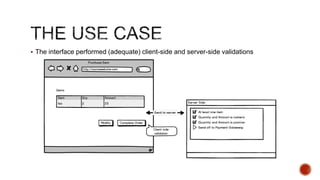
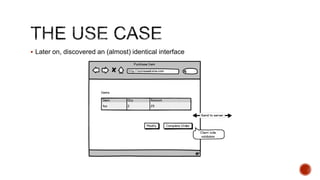
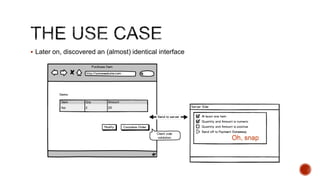
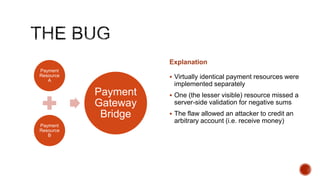
The document summarizes a talk focused on web application security at a Sydney meetup, highlighting the evolution of web development and common security vulnerabilities developers face today. It discusses the complexity of modern flaws compared to textbook examples and emphasizes the importance of defensive coding practices and thorough security assessments. The speaker shares insights on mitigating risks and stresses the need for continuous education and awareness in web security, supported by various resources and event participation.