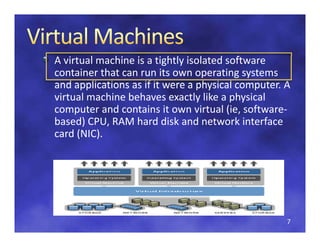
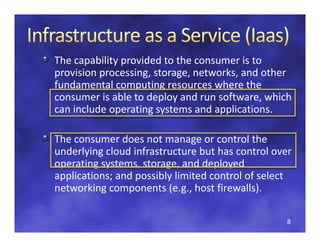
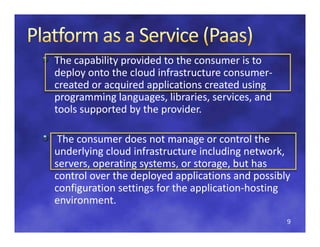
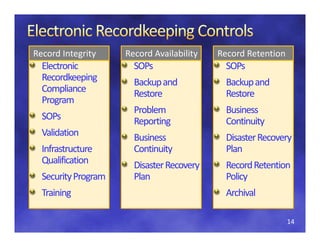
The document discusses regulatory considerations for cloud computing and SaaS environments, focusing on the qualification and validation of cloud infrastructures. It highlights key challenges, the importance of standards for security, interoperability, and portability, and the various types of cloud deployment models. Additionally, it emphasizes the necessity for clear agreements and compliance measures between service providers and consumers to ensure the effectiveness of cloud solutions.