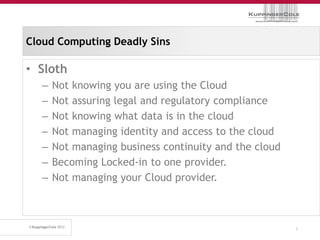
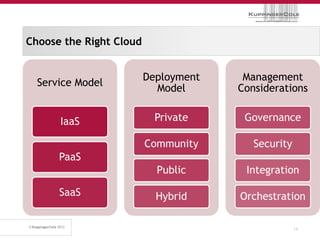
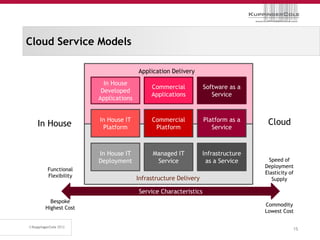
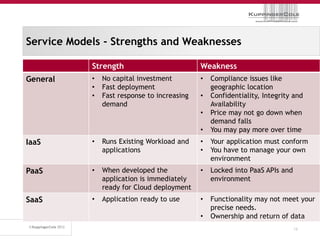
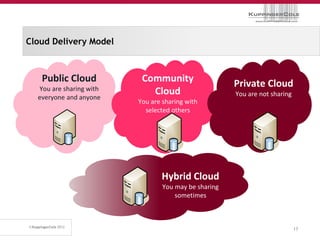
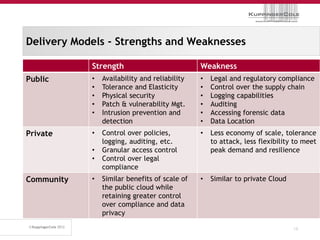
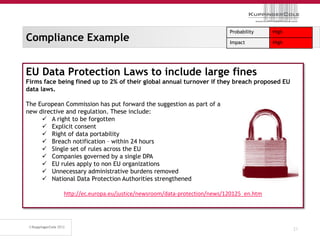
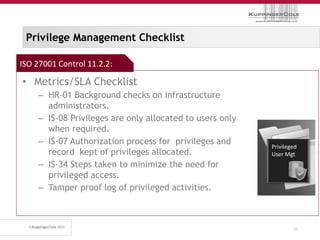
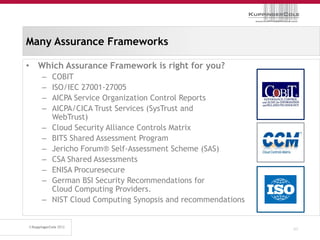
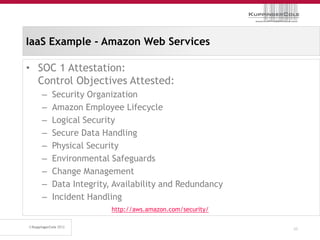
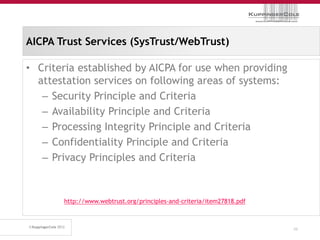
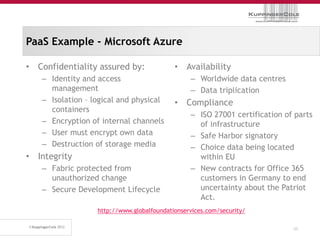
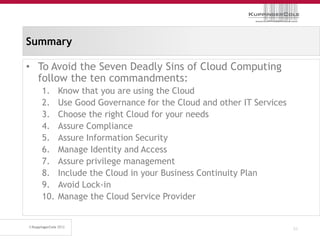
The document discusses the 'seven deadly sins' of cloud computing, highlighting the risks associated with not understanding cloud usage and compliance, as well as the management of cloud services. It provides ten key questions to consider for effective cloud governance and security, including selecting the right deployment model and ensuring business continuity. To avoid these pitfalls, it suggests implementing best practices, such as proper governance, compliance assurance, identity management, and managing potential provider lock-in.