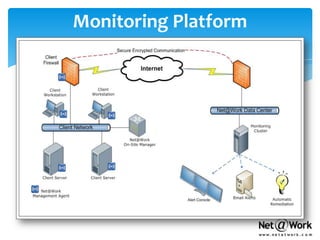
This document provides an overview of Net@Work, a technology integration company based in North America. Some key points:
- Net@Work was founded in 1996 and has over 200 employees serving over 4,500 clients.
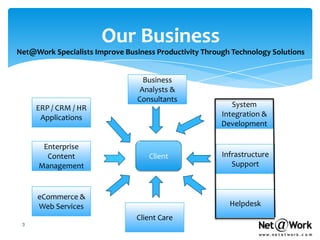
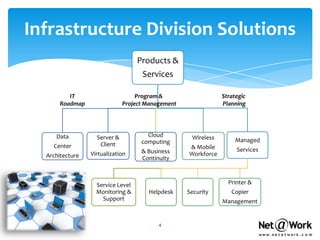
- They offer a wide range of IT services including consulting, infrastructure support, security services, and managed IT services.
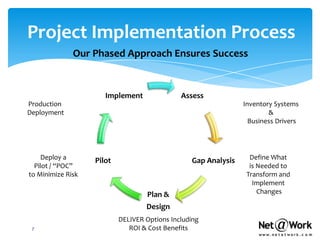
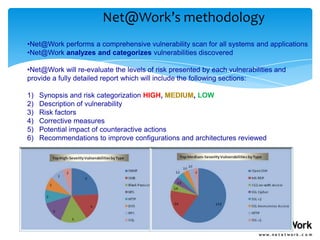
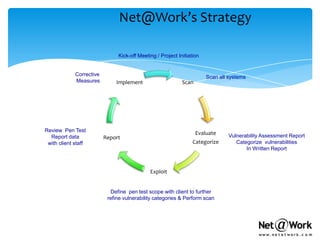
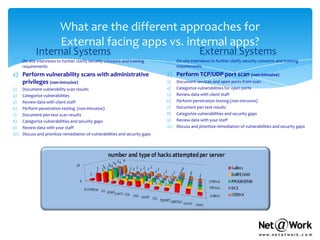
- For security assessments, Net@Work performs vulnerability scans, reviews security policies, analyzes third-party risks, and provides recommendations to improve security controls. They categorize risks as high, medium, or low.
- Net@Work recommends ongoing security assessments at least annually to ensure protections remain effective over time. Quarterly assessments are ideal.