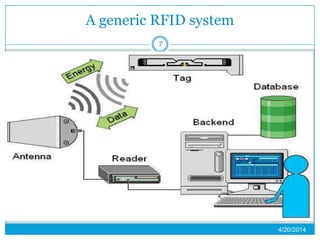
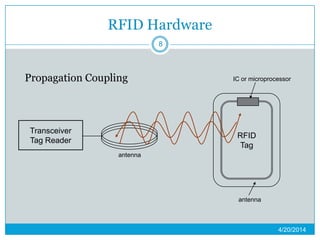
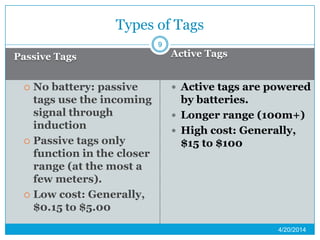
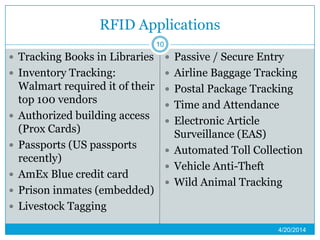
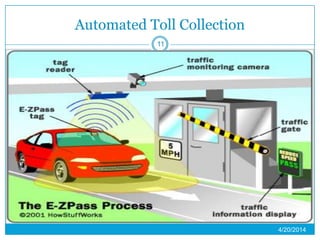
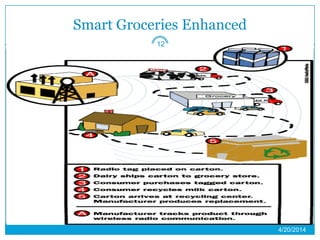
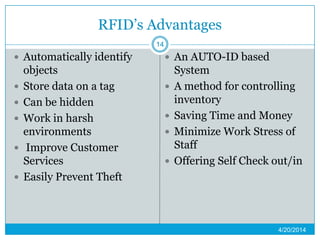
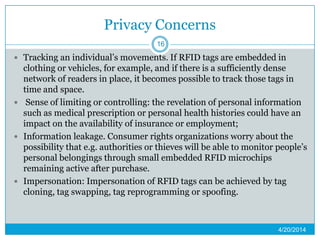
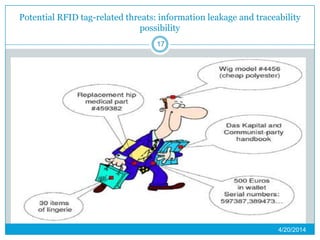
This presentation provides an overview of RFID (radio frequency identification) technology. It defines RFID as using radio frequency tags to identify objects via radio waves. The presentation describes the basic components of an RFID system including tags, readers, and antennas. It discusses the history of RFID and barcodes and provides examples of current RFID applications in areas like inventory tracking, building access, toll collection, and smart appliances. Both advantages like automatic identification and disadvantages like privacy concerns are outlined. Regulations surrounding RFID are also briefly addressed before concluding with predictions about the continued growth and standardization of RFID technology.